- Related Products
- AD360
- Log360
- ADAudit Plus
- ADSelfService Plus
- EventLog Analyzer
- Exchange Reporter Plus
Identity Risk Assessment Report
The Identity Risk Assessment report in ADManager Plus identifies the potential identity risk indicators in your organization. It offers visibility into the health and risk posture of both your Active Directory (AD) and Microsoft 365 environments. ADManager Plus implements the guidelines of NIST SP 800-30 to assess the likelihood of occurrence and impact level of risk indicators to compute a risk score. It locates the plausible risk indicators in your organization, offers insights on why they could be a risk indicator, and what can be done to secure your organization from them. ADManager Plus also computes and displays a risk score to summarize the significance of the identified risks.
In a nutshell, ADManager Plus assesses your AD and Microsoft 365 environment, identifies the potential risk indicators, evaluates them, provides remediation measures, and helps you keep risks at bay with this report.
In this document, you will learn the following:
- Key terms
- How to generate the Identity Risk Assessment report
- How to view, export, and manage risks
- List of risk indicators identified by ADManager Plus in AD and Microsoft 365
- How to add Privileged Entities in Risk Assessment
Understand the key terms
The following are some terms that you will come across in this report, and it is imperative to know them:
| Term | Description |
|---|---|
| Risk Score | An indicator of your overall risk posture. It can be low, medium, high, or critical. It is recommended to have a low risk score to secure your organization. |
| Risk Exposure | It signifies the percentage of objects vulnerable to a particular risk. |
| Likelihood of occurrence | The possibility of an occurrence for the identified risk indicator along with insight on the potential damage that it could cause. |
| Remediation measures | Actions that can be taken to eliminate and avoid the identified risk indicator. |
| Dashboard view | A comprehensive one-stop view of all the identified risk indicators categorized based on the objects identified, along with a graphical risk score indicator. |
| Tile view | A tile-view of all the identified risk indicators categorized based on their severity along with graphical indicators. |
| Score Trend | Track how your overall risk score changes over time with visual graphs to monitor the effectiveness of remediation efforts and identify patterns in risk exposure. |
Steps to view a risk assessment report in ADManager Plus
- Log in to ADManager Plus.
- Navigate to the Governance tab.
- In the left pane, click Identity Risk Assessment report.
- Select the domain for which you would like to view the report under Risk Management.
- A dashboard will then display your risk score, along with the risks identified in your network.
- The Score Trend section displays how your risk score has changed over time through a visual graph, helping you track improvements and identify new vulnerabilities in your AD environment.
View, export and manage risks
- Export report: The report can be exported by clicking the Export As button. The overall risk assessment report and risky objects can be exported by clicking the appropriate buttons.
- View report: You can switch between the Tile View and Dashboard View by clicking the appropriate buttons.
- Filter risks: The risks in Dashboard view can be refined using the Filter drop-down menu based on their severity.
- Manage risks: Click on a risk to view the risky objects and remediate them using the management actions. The risk data can be refreshed by clicking the Refresh button.
Note: Only technicians delegated with the Identity Risk Assessment role can view this report and only in the delegated OUs. To delegate this role, Delegation > Help Desk Roles > Edit a help desk role/Create a new role > Administration > General > Check Identity Risk Assessment.
How is the risk score calculated?
ADManager Plus assesses active risks in your identity-environment. All risk indicators go through three phases of computation. This assessment blends qualitative and quantitative techniques, making it semi-quantitative. The ultimate output is to derive a risk score that represents the security posture of your AD.
What follows is an explanation of the risk scoring methodology, the factors used to calculate the risk score, and the rationale behind it.
Phase 1: Determining the severity
In the first phase, each risk indicator is assessed by following a three-step calculative process: Likelihood determination, Impact analysis, and Severity determination.
Step 1: Likelihood determination
Likelihood of occurrence is the probability or chance that a particular threat event or risk will happen or materialize. The overall likelihood is determined by correlating "Likelihood of Attack Initiation" and "Likelihood of Initiated Attack Succeeds."
Likelihood of Attack Initiation: The probability that a threat source initiates an threat event or vulnerability-exploit. Factors— pertinent to capability— considered under likelihood of attack initiation are:
- Skill level required
- Opportunity required
Likelihood of Initiated Attack Succeeds: The probability that an initiated attack or threat event will result in an adverse impact on the organization's assets, operations, or aims. The factors considered under Likelihood of Initiated Attack Succeeds are "Capability" and "Vulnerability Severity."
Capability: Alludes to the skills, resources, and opportunities at the disposal of potential attackers that they can leverage to exploit vulnerabilities, escalate privileges and orchestrate subsequent malicious activities within the AD or identity environment. Capability factors are mentioned under Likelihood of Attack Initiation.
Vulnerability Severity: The degree or level of harm that could result from the exploitation of a specific risk indicator. Factors considered in deriving the vulnerability severity are:
- Ease of Discoverability
- Ease of Exploitation
For every risk indicator, a numerical value is assigned to each capability and vulnerability severity factors. The average of all capability factors will result in overall capability while the average of all vulnerability severity factors will result in overall vulnerability severity.
Subsequently, the overall capability and vulnerability severity are averaged to derive the Likelihood of Attack Initiation.
Overall likelihood: An assessment output derived by correlating the results of Likelihood of Attack Initiation and Likelihood of Initiated Attack Succeeds for each risk indicator using a 4x4 correlation matrix.
Step 2: Impact analysis
This step assesses potential consequences of a risk or vulnerability-exploit. Potential consequences can include damage to a company's business operations, financial loss, reputational damage, or any other aspect deemed relevant by the organization. Factors considered under impact analysis are:
- Confidentiality
- Integrity
- Availability
Similar to the preceding step, for every risk indicator, a numerical value is assigned to each impact analysis factors and the average of all those factors will result in the overall impact.
Step 3: Determining severity
This step determines the severity of risks based on their likelihood and impact using a 4x4 correlation matrix.
Risk Matrix: Likelihood vs Impact
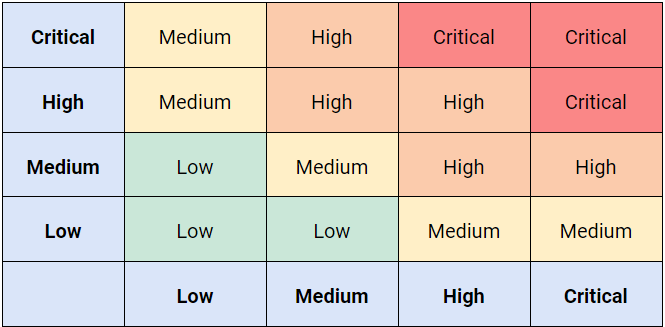
*Vertical scale is likelihood and Horizontal scale is impact
Phase 2: Assigning weightage and calculating risk exposure
In the second phase, each risk indicator is assigned a weightage based on their impact and risk severity. The weightage scale ranges from 1 to 10.
After the weightage has been assigned, the next step is to calculate the risk exposure for each risk indicator. This involves using the formula: number of risky objects related to a specific risk divided by the total number of objects within the scope of that risk in the environment.
Here are a few examples:
- Risk exposure for non-privileged disabled users = Number of non-privileged disabled users/Total number of non-privileged users
- Risk exposure for privileged inactive users = Number of privileged inactive users/Total number of privileged users
- Risk exposure for empty groups = Number of empty groups/Total number of groups
Phase 3: Determining the risk score
In the final phase, the overall risk score for your identity environment is calculated using a weighted average method that is comprised of weightage values and risk exposures as variables.
Note: The risk score and report become obsolete when a newer report is generated. Only risk indicators included in the assessment are scored, and failed to run indicators are not included in the final risk score. It's advisable to include all domains in the selected forest before assessing for an accurate analysis of your identity environment.
ADManager Plus identifies risks in Active Directory and Microsoft 365 environments by analyzing key risk indicators. These indicators reveal potential vulnerabilities, enabling organizations to categorize risks and take proactive measures to enhance security. The following categories are included:
| Risk indicators in AD | Risk indicators in Microsoft 365 |
|---|---|
Risk indicators in AD
Users:
| Privileged users | Non-privileged users | General |
|---|---|---|
|
|
Service Accounts
|
Computer
| Computer | Domain Controller |
|---|---|
|
|
Groups
|
|
GPOs
|
|
Security
|
|
Misconfigurations
|
|
Risk indicators in Microsoft 365
Users:
| Privileged users | Non-privileged users | General |
|---|---|---|
|
|
|
Groups
|
Note: When ADManager Plus accesses the domain objects' details for analyzing the risks through LDAP queries, it might trigger security alerts in your existing security systems.
