Setting up Two-Factor Authentication - RADIUS Authenticator
You can integrate RADIUS server or any RADIUS-compliant two-factor authentication system (like Vasco Digipass) with Password Manager Pro for the second factor authentication. Following is the sequence of events involved in using RADIUS-based authentication system as the second factor:
- Provide basic details about RADIUS server.
- Enable the RADIUS-based authentication system as the second factor.
Summary of Steps
- Configuring Two-Factor Authentication in Password Manager Pro
- Enforcing Two-Factor Authentication for Required Users
- Connecting to Password Manager Pro's Web Interface When TFA through RADIUS Authenticator is Enabled
1. Configuring Two-Factor Authentication in Password Manager Pro
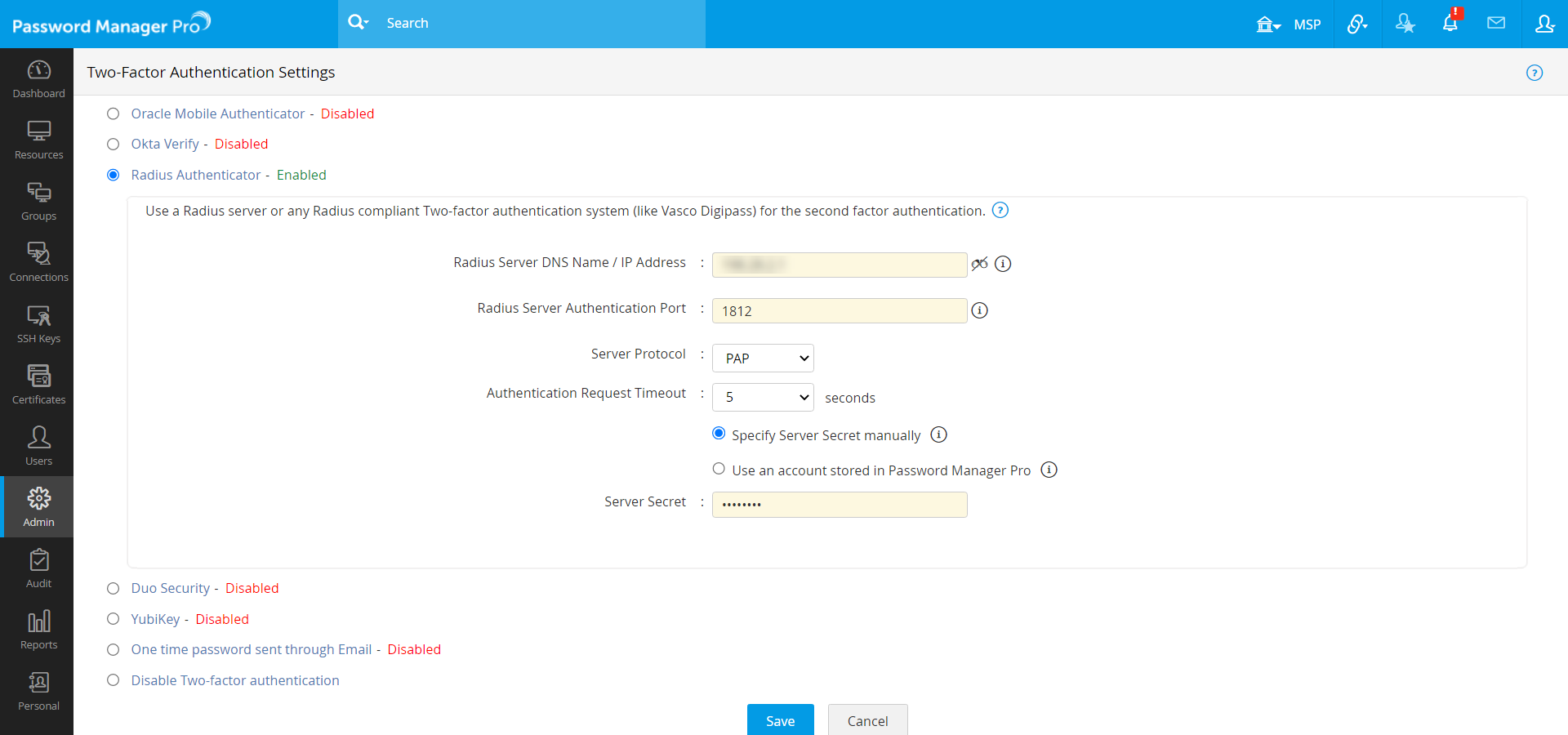
- Navigate to Admin >> Authentication >> Two-factor Authentication.
- Choose the option RADIUS Authenticator.
- In the new drop-down form that opens, provide the following details:
- Server Name/IP Address - Enter the host name or IP address of the host where RADIUS server is running.
- Server Authentication Port - Enter the port used for RADIUS server authentication. By default, RADIUS has been assigned the UDP port 1812 for RADIUS Authentication.
- Server Protocol - Select the protocol that is used to authenticate users. Choose from four protocols - Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), Microsoft Challenge-Handshake Authentication Protocol (MSCHAP), Version 2 of Microsoft Challenge-Handshake Authentication Protocol (MSCHAP2).
- Server Secret - You have the option to enter the RADIUS server secret either manually in the text box or you can direct Password Manager Pro to use the secret already stored in the product. In that case, you need to select the resource name and account name from the drop-down. The second option - storing the RADIUS password in Password Manager Pro and selecting it from drop-down is the recommended approach.
- Once you've entered the required details, click Save.
- Then, click on Confirm to enforce Radius Authenticator as the second factor of authentication.
2. Enforcing Two-Factor Authentication for Required Users
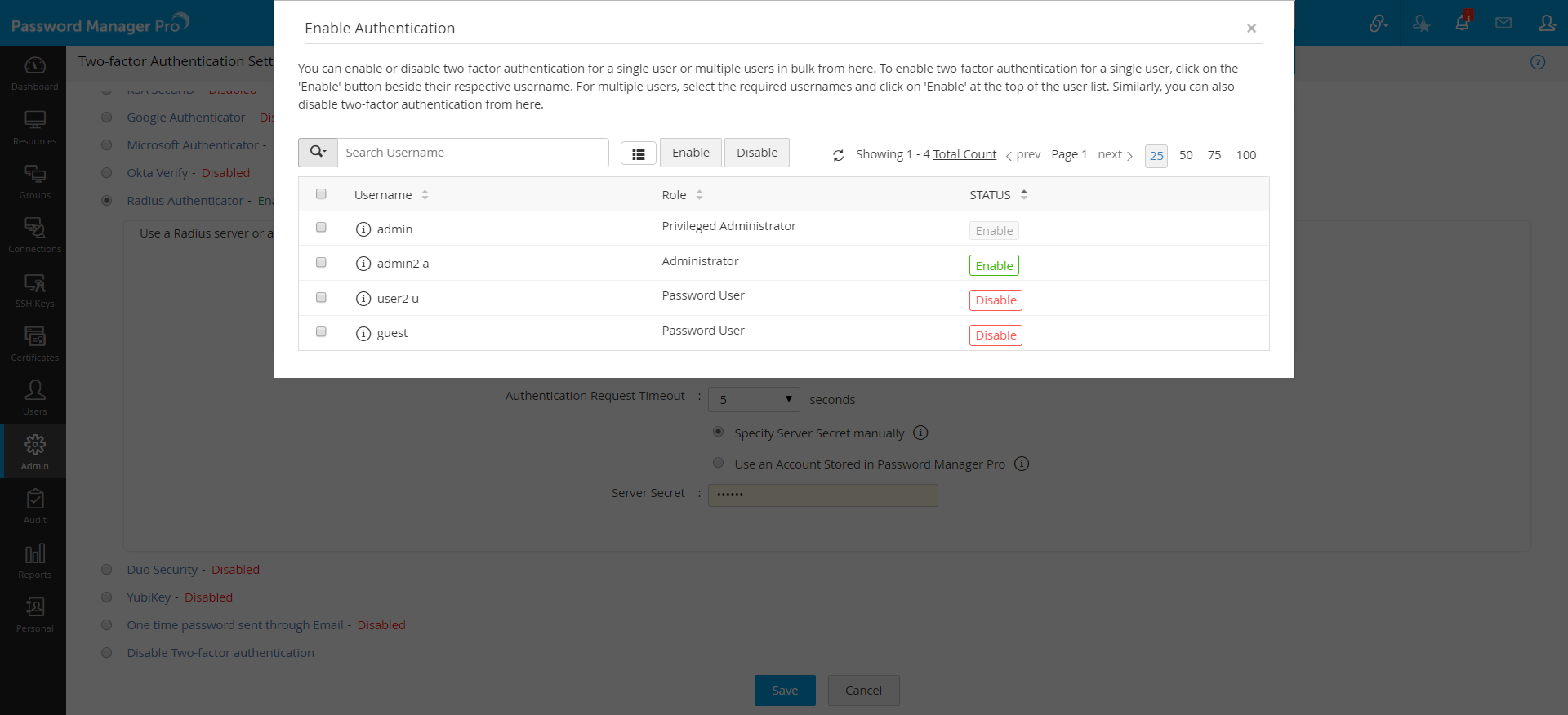
- Once you confirm Radius Authenticator as the second factor of authentication in the previous step, a new window will prompt you to select the users for whom two-factor authentication should be enforced.
- You can enable or disable two-factor authentication for a single user or multiple users in bulk from here. To enable two-factor authentication for a single user, click on the 'Enable' button beside their respective username. For multiple users, select the required usernames and click on 'Enable' at the top of the user list. Similarly, you can also 'Disable' Two-Factor Authentication from here.
- You can also select the users later by navigating to Users >> More Actions >> Two-factor Authentication.
3. Connecting to Password Manager Pro Web-Interface when TFA through RADIUS Authenticator is Enabled
The users for whom two-factor authentication is enabled, will have to authenticate twice successively. As explained above, the first level of authentication will be through the usual authentication. That is, the users have to authenticate through Password Manager Pro's local authentication or AD/LDAP authentication. If the administrator has chosen the TFA option "RADIUS Authenticator", the two-factor authentication will happen as detailed below:
- Upon launching the Password Manager Pro web-interface, the user has to enter the username and local authentication or AD/LDAP password to login to Password Manager Pro and click Login.
- Once the first level of authentication succeeds, you will be prompted to enter the RADIUS code.
If you have configured High Availability
Whenever you enable TFA or when you change the TFA type (RSA SecurID or One-time password or RADIUS or Duo), you need to restart the Password Manager Pro, secondary server once.