IAM authentication methods for managing identities and securing
your enterprise
April 11 · 7 mins read

Picture this: Your organization is preparing to recruit employees across various departments. HR plans to onboard 500 employees. As the admin of the enterprise, it is your responsibility to ensure each user is granted access to the applications needed for their role. With less than 24 hours on the clock, how do you get the job done?
Manually provisioning accounts for 500 employees is time-consuming and prone to human error. This is where identity and access management (IAM) comes into play. Automated user provisioning enables the creation of role-based user groups with predefined access controls and application permissions. When a recruit is added to their role, they can start using the relevant tools right away. Automated provisioning streamlines employee life cycle management, increases efficiency, and minimizes the risk of errors.
Enterprises today are rapidly moving towards digitalization. Companies are adopting cloud-based applications to enhance business agility, improve productivity, and drive growth. Enterprises with workplace flexibility allow employees and third-party vendors to access resources from any device and location. As a result, there is an increase in the number of identities, and the traditional security perimeter has become obsolete.
Cybercriminals are always on the lookout for loopholes to breach enterprise networks. In recent years, they have discovered sophisticated techniques to hack accounts through user identities. Therefore, depending solely on account credentials to defend enterprise resources is no longer a safe bet.
As shown in Figure 1, a 2022 survey conducted by the Identity Defined Security Alliance (IDSA) reveals that 84% of IT security and IAM decision-makers have experienced identity-based attacks. Yet almost all of the decision-makers believe that such identity-related attacks are preventable. The question is: how?

Organizations require a holistic approach to security. They must reinforce their cybersecurity infrastructure by implementing a robust IAM system. In this article, we will take a closer look at ManageEngine's IAM authentication methods.
Single sign-on (SSO)
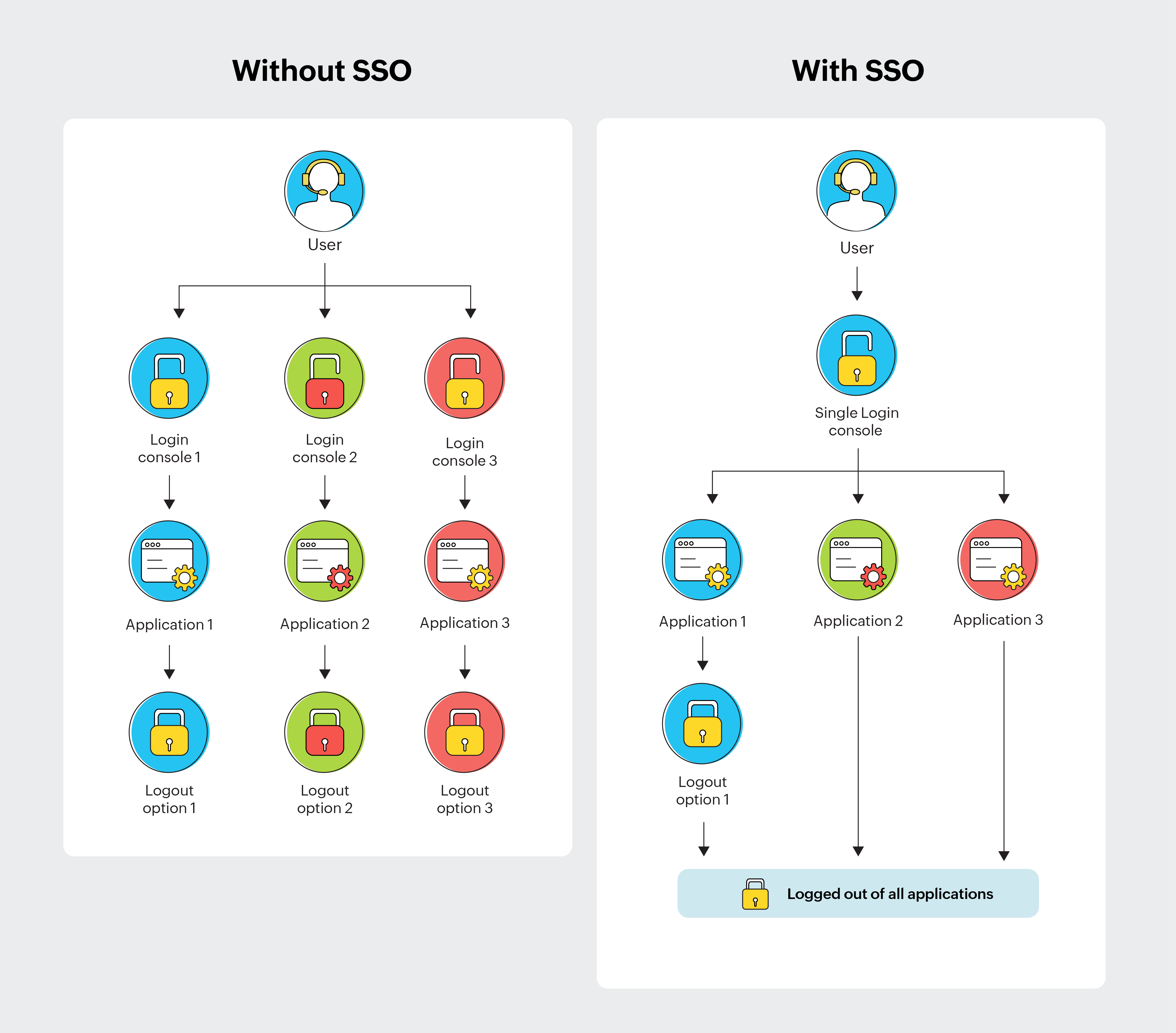
SSO is an authentication process that allows users to sign in to multiple applications with a single set of credentials, as opposed to having separate credentials for each app. When a user logs in to an application, they can automatically move between multiple applications with one set of valid credentials. Therefore, the need to remember multiple complex passwords is eliminated. Similarly, when a user logs out of one application, single logout ensures they are logged out of all the connected applications.
Zoho has implemented SSO organization-wide via our integrated IAM service. When our employees log in to their Zoho Corporation accounts, such as through their email, they gain one-click access to other Zoho services, such as chat, help desk, meeting, and presentation solutions. Likewise, when they log out of their email, they are automatically logged out of the other Zoho services (Fig. 2).
The login process through an identity provider (IdP) page
Zoho's applications are also utilized by other organizations to conduct their day-to-day affairs. They have the option to choose SSO as their authentication process. In certain use cases, Zoho acts as a service provider for third-party IdPs.
Let's look at an example where employees from a fictional third-party firm, Zylker, are using Microsoft solutions along with ManageEngine applications for their day-to-day
operations (Fig. 3).

During the configuration stage, the IT admin at Zylker configures SAML requirements (a standardized way to exchange authentication data), such as login and logout URLs. The user logs in to their Microsoft account using their credentials and selects a ManageEngine application from their dashboard. When the user selects the application, it creates a signed SAML assertion response. This data is sent to ManageEngine's URL, and the response is validated in the back end automatically. Upon successful validation, the user can access the selected
ManageEngine application.
Multi-factor authentication (MFA)
Usernames and passwords are susceptible to attacks and can be stolen. In the event of a security breach, passwords are likely the first thing to be compromised. These passwords become available on the dark web, publicly traded by attackers, for as little as $15. Organizations must not solely depend on passwords to protect their resources. Using features like fingerprints or OTPs acts as an additional layer of enhanced security.
At Zoho, we offer four MFA modes for our users: Zoho OneAuth, SMS-based OTPs, OTP authenticators, and security keys. OneAuth, an in-house MFA application, is the recommended mode for employees. OneAuth is designed to strengthen account safety and secure user accounts from password breaches. Users are required to identify themselves using a combination of factors commonly categorized as:
- Something you know (username and password)
- Something you have (a device or an access badge)
- Something you are (biometrics, like face ID or fingerprints)
OneAuth protects an organization's resources against unauthorized access. Users can set up all modes along with their credentials and opt for a preferred sign-in mode. If the preferred mode fails, users can authenticate via any of the alternate verification modes:
Sign-in mode |
Steps to sign in |
Push notification |
Password-based sign-in:
Passwordless sign-in:
|
OTP |
|
QR code |
|
What happens when an employee loses their registered device? In this situation, the user can:
- Authenticate and gain access to their accounts using a secondary device.
- Review the list of active sessions in OneAuth and remove the primary device.
- Restrict access by blocking all future sign-ins from the primary device.
Users are also provided with recovery options, including a passphrase, a backup mobile number, and backup verification codes. For organizations that use third-party two-factor authentication (2FA) apps, OneAuth offers an authenticator module. By enhancing the security of this module with updated encryption and decryption of 2FA account secrets, OneAuth has become more secure than ever. Plus, Zoho will continue to have zero knowledge of users' passphrases.
In the modern enterprise landscape, cyberattackers are always on the lookout for security vulnerabilities. Organizations can never fully prevent breaches. However, with IAM solutions and the right security policies and tools, they can minimize the risks and enhance their security posture. A strong IAM framework relieves IT teams of the burden of managing passwords while also enhancing productivity and the user experience. With IAM solutions in place, organizations will take a step closer towards implementing a Zero Trust strategy.
