
Recognized as a Representative Vendor in the Gartner® Market Guide for Identity Governance and Administration.
Recognized as a Notable Vendor in the The Forrester Wave™: Workforce Identity Platforms report.
Recognized as a Challenger in innovation, product, and market categories in the Leadership Compass: Access Management.
Recognized as a Leader in the Identity and Access Management category in the ISG Provider Lens™ Cybersecurity — Services and Solutions report.
Recognized in the Cybersecurity Solutions for Healthcare report.
Recognized in the Constellation ShortList™ for Access Management.
If you delay strengthening your identity security, you risk exposing your enterprise to evolving cyberthreats and rising costs to prevent a breach.
of cyberattacks involves identity-based methods*
is the average cost of a data breach**
of AI-related breaches stem from poor access controls**
of leaders say identity silos are the root cause of cybersecurity risk‡
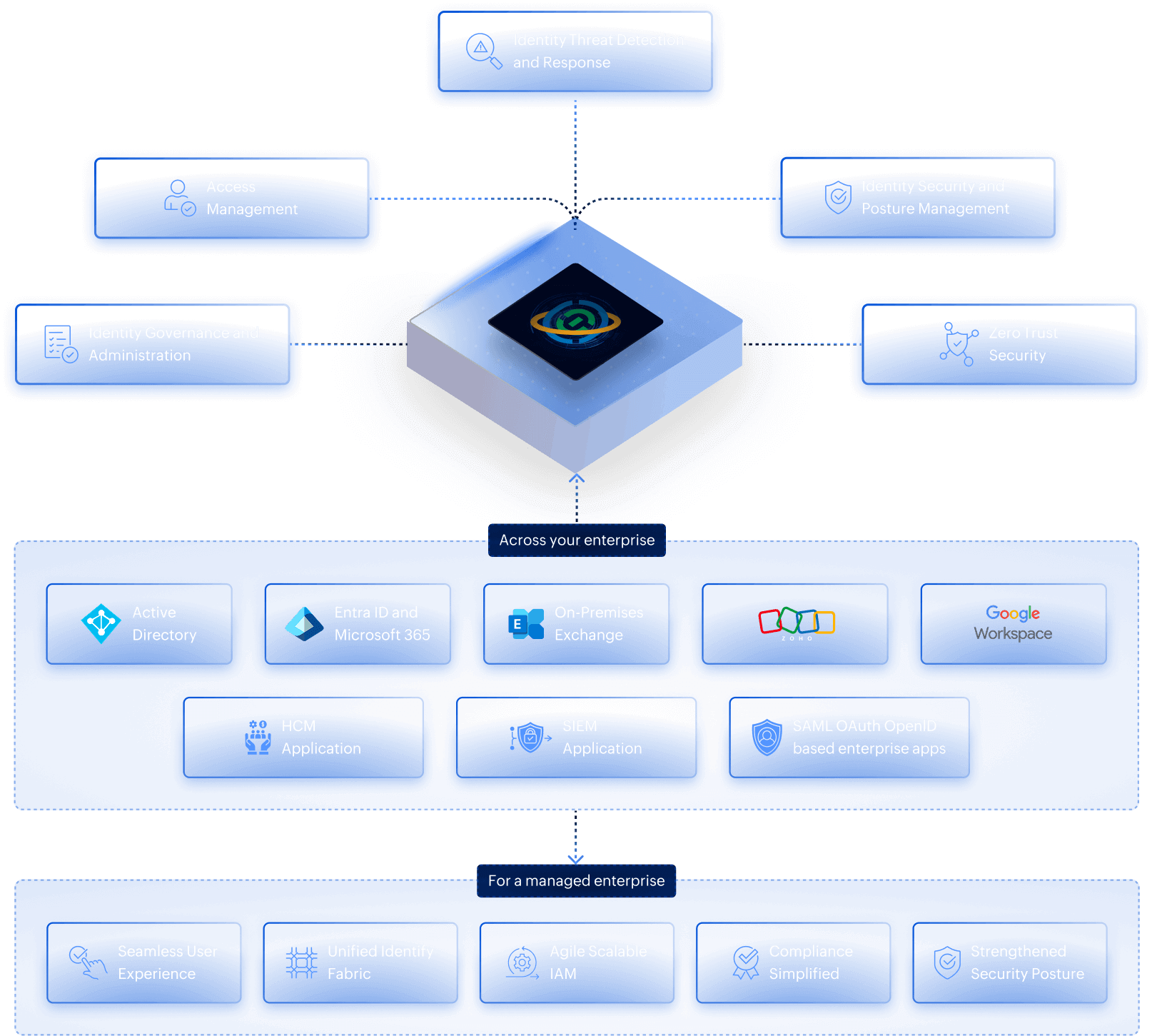
Gain complete control over the identity life cycle by automating provisioning and deprovisioning, enforcing role-based access, and simplifying access certifications. With self-service password management and approval workflows, it reduces IT overhead while ensuring compliance and stronger security.
I've noticed far fewer human errors and a faster turn around time for creating a user's account and email.
- Paul Jack, IT administrator, Science Museum
Deliver secure and convenient access with single sign-on, adaptive MFA, and conditional access policies. It balances productivity and protection, making it easier for users to access what they need while safeguarding sensitive data and applications.
"AD360 has been a game changer for us. Prior to AD360, we had no visibility into our AD infrastructure."
— Callixtus Muanya, administrator, Harvard Medical School
AD360 detects suspicious logins, privilege escalations, and lateral movement attempts in real time. With automated remediation and forensic insights, it helps enterprises contain threats quickly and reduce the impact of identity-based breaches.
"ADAudit Plus is absolutely perfect as an auditing solution. We've used the product for all types of auditing, and it is not limited in its purpose or scope."
— Michael Plourde, server architecture supervisor, Fortune Brands Home Innovations
Centralize and encrypt privileged credentials while discovering critical accounts to eliminate unmanaged access risks. Grant just-in-time privileges, enable secure remote access, and monitor sessions with zero-trust controls. Manage SSH keys and SSL certificates, analyze user behavior, and generate compliance-ready reports to safeguard enterprise systems.
"Control is the key benefit we’ve gained. Centralized privileged access management, session logs, and access workflows help us stay ahead of security risks."
— Mario, security leader at 5B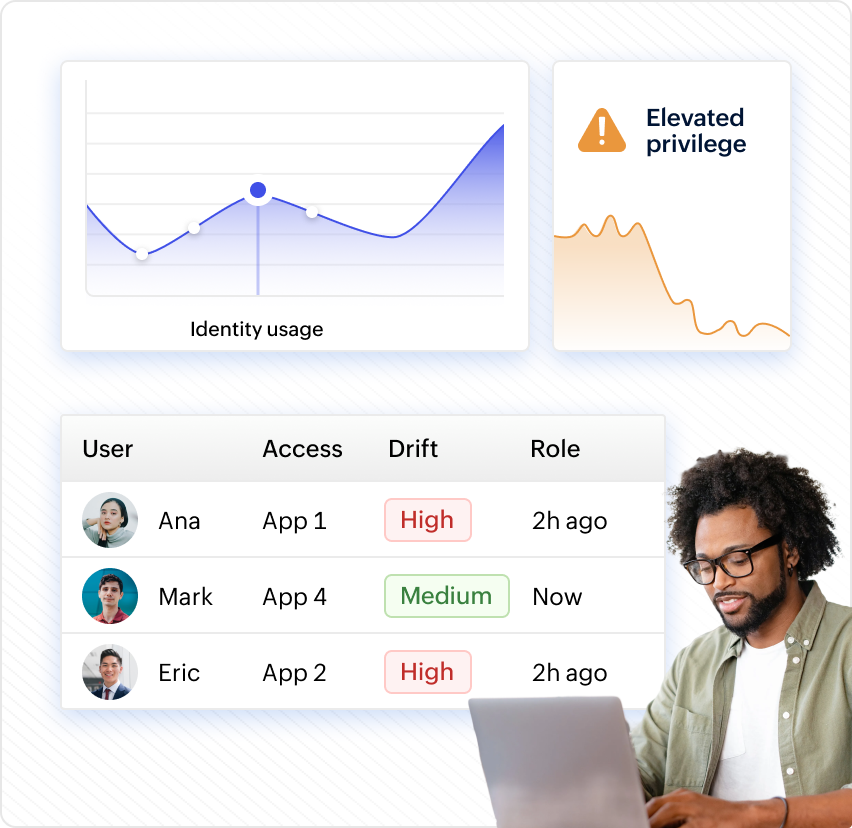
AD360 continuously monitors entitlements and configurations to uncover risks like privilege creep and excessive access. By providing clear insights and enforcing policies, it strengthens identity security posture and helps enterprises meet compliance standards without slowing operations.
"The ADAudit Plus console allows our resources to find and keep track of AD in a better way than we managed to in the past."
— Payam Alm, IAM lead, Inter Ikea Group
AD360 enables enterprises to apply zero trust principles with least privilege access, contextual authentication, and just-in-time access controls. Continuous verification ensures every identity is validated, reducing exposure and keeping critical resources secure.
"With ADManager Plus, the Service Desk staff can create and administer company staff AD accounts without needing a highly privileged admin account, so that meets our desire for Zero Trust."
— Darren Wiseman, group CTO, Toyota Financial Service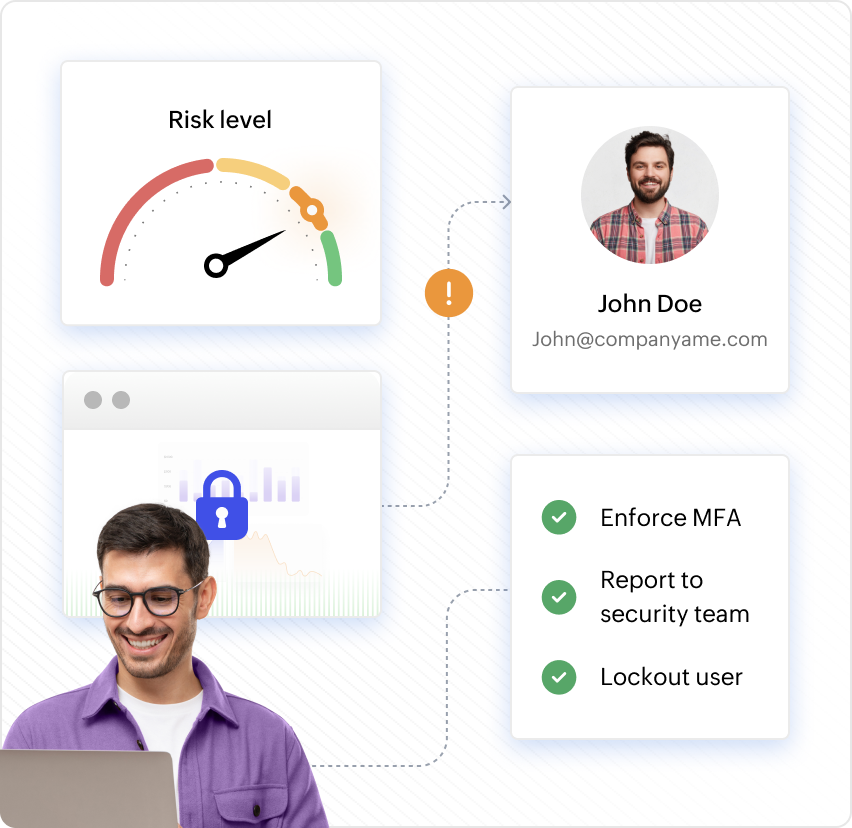
See how leading enterprises are driving efficiency and reducing costs with AD360.
saved annually for Centre for Addiction and Mental Health by eliminating password reset-related support calls through self-service.
reduction in daily support tickets at United Arab Emirates University by automating AD-related helpdesk tasks with self-service.
faster onboarding for Toyota Financial Services accelerated enterprise-wide user access and productivity.
faster account provisioning for Science Museum enabled same-day onboarding and improved operational efficiency.

Discover our enterprise-grade capabilities that power identity management at scale
Works seamlessly with your existing identity stack while extending security through more than 250 prebuilt integrations and flexible REST APIs across your on-premises, cloud, and hybrid systems.

Behind every successful deployment is a team that understands your world. Our trusted GSI partners work alongside you to design and deliver IAM solutions that fit your goals, reduce time to value, and scale confidently for the future.

Trust is built on transparency. We never run ads, sell data, or compromise user trust. We regularly test and certify our solutions against global privacy and security standards. Your data, your people, and your business stay protected at every step.

Our straightforward onboarding and smooth integration help you realize benefits quickly. Designed for efficiency, our solutions reduce delays so your team can focus on what matters—delivering results and growing your business.

Our transparent pricing model ensures no hidden fees, so your budgeting stays predictable. By streamlining operations and reducing maintenance overhead, our solutions help lower ongoing costs while delivering robust, scalable identity management. Get more value from your investment with a system built to grow efficiently alongside your business.

Effectively manage user identities and secure access to sensitive patient data. Automate identity lifecycle management, enforce adaptive MFA, and ensure compliance with industry standards such as HIPAA. AD360 also streamlines third-party access, allowing you to maintain control while fostering secure collaborations with external partners and vendors.
Ensure seamless security for both staff and student data, adhere to policies such as FERPA and COPPA, safeguard your institution's invaluable intellectual properties (IPs) from advanced security threats, and accelerate user onboarding and change management through automation — all from a single console.
Ensure robust security for client and company data, comply with financial regulations like the GDPR and the PCI DSS, protect valuable financial assets from cyberthreats, and streamline operations through a unified IAM system.
Centralize access management in your government organization to enhance security and compliance. Streamline provisioning, enforce policies, and manage authentication, boosting efficiency and safeguarding data.
Simplify user access control and improve security protocols by implementing a unified IAM system to reduce IT complexity and ensure compliance across all digital assets.
Secure login path for diverse user groups, from corporate employees managing business operations, factory workers handling production workflows, to external suppliers collaborating on supply chain processes
Our premium support ensures we are with you throughout your IAM journey. Access 24/7 expert guidance tailored to your unique enterprise environment.
Seamlessly deploy AD360 with personalized onboarding and configuration support. Our experts ensure smooth implementation aligned with your enterprise infrastructure.
Empower your teams with our self-paced learning platform. We provide curated courses by product experts that accelerate adoption, build expertise, and enable confident, independent identity operations.
We make every decision with our customers in mind, delivering solutions that solve real problems and create lasting value.
At ManageEngine, our commitment to doing what's right drives every decision, helping enterprises stay secure, agile, and future-ready.
Your trust comes first. We safeguard your data as if it were our own, never monetizing or compromising it.
We invest heavily in research and development, ensuring our technology stays ahead of enterprise challenges.
Security is built into every layer. Our solutions are tested for scale, built for uptime, and trusted worldwide.
From concept to code, every feature is built in-house. Our independence keeps us focused on customer needs, not investor demands.
One thing we've really liked about ManageEngine is that they’ve always been ahead of us. When we wanted something, we took a quick look around the product, and it was already in there.
Donna Milner | ITSM Manager | West Yorkshire Combined AuthorityWhenever we've had issues with ManageEngine products, the support has been really good. We've received feedback, fixes, and in-person demos, which has been really beneficial.
Chris Wallace | Head of IT | N3i LimitedAD360 has significantly reduced the number of tickets for minor changes like contact updates and distribution group adjustments. It allows our teams to handle these tasks independently while maintaining targeted security, resulting in improved responsiveness and efficiency.
James Carlisle | IT helpdesk lead |DIRTT Environmental SolutionsAll of the users in the entire company can change the password from a web browser or right when they log into the computer. Works really simple. Everything that we’ve used, we’ve been very impressed with. It’s really easy to use, easy to administer and implement. It’s a great product.
Mark Thompson | Kubota Canada Ltd. Environmental SolutionsEnable secure, compliant, and scalable access across your global workforce with ManageEngine AD360. Let's align your identity strategy with your business goals.
A practical guide to help you choose the right IAM solution for your enterprise.
Read moreDiscover how our solution helped a leading enterprise achieve their IAM objectives and reduce risk.
Read moreConnect with our experts and explore how AD360 can help your organization to manage, protect, and empower workforce identities — from a single centralised identity platform.