Chapters
- Introduction: Why NIST matters for enterprise Cybersecurity
- How the NIST Cybersecurity Framework acts as a shield for your organization
- Understanding the NIST cybersecurity framework
- The role of identity and access management in risk governance
- Integrating cybersecurity risk into enterprise risk management
- Best practices for cybersecurity risk governance
- Enhancing your AD security with AD360
Introduction: Why NIST matters for enterprise Cybersecurity
Companies worldwide are continuing to transition to complex ecosystems that include cloud platforms, mobile devices, IoT networks, and intricate supply chains. While these advancements drive innovation and efficiency, they also expose organizations to a wider array of cyber risks.
In this context, the National Institute of Standards and Technology (NIST) and Cybersecurity Framework(CSF) emerges as a vital resource. It goes beyond a simple checklist by offering a flexible and adaptable framework that aligns cybersecurity practices to the strategic objectives of the organization. This structured approach helps businesses effectively manage their cybersecurity risks while ensuring that their security measures support their overall goals.
How the NIST Cybersecurity Framework acts as a shield for your organization
Effective risk governance ensures that an enterprise’s cybersecurity posture isn’t reactive or fragmented— it is anticipatory and integrated. Cyberthreats are no longer isolated incidents; they are systemic challenges that demand cohesive responses. In this area, the NIST CSF delivers a structured approach to cybersecurity risk management by integrating existing standards, guidelines, and best practices.
It provides organizations with a scalable, adaptable roadmap to identify, assess, and mitigate cyber risks. Its universal applicability means that enterprises of all sizes and sectors can benefit from its structure while tailoring it to their unique needs. But why is this framework so important?
- Strategic alignment: The CSF bridges the gap between technical cybersecurity measures and business objectives, ensuring that decisions are both operationally sound and strategically aligned.
- Regulatory compliance: With regulatory landscapes becoming more stringent, the CSF helps organizations demonstrate adherence to global, regional, and industry-specific compliance mandates.
- Operational resilience: By nurturing a proactive approach, the framework helps organizations recover swiftly from disruptions, minimizing downtime and reputational impact.
Understanding the NIST cybersecurity framework
At the core of the NIST CSF are five interrelated functions that offer a comprehensive approach to managing cybersecurity risks. Each function represents a key aspect of effective risk governance:
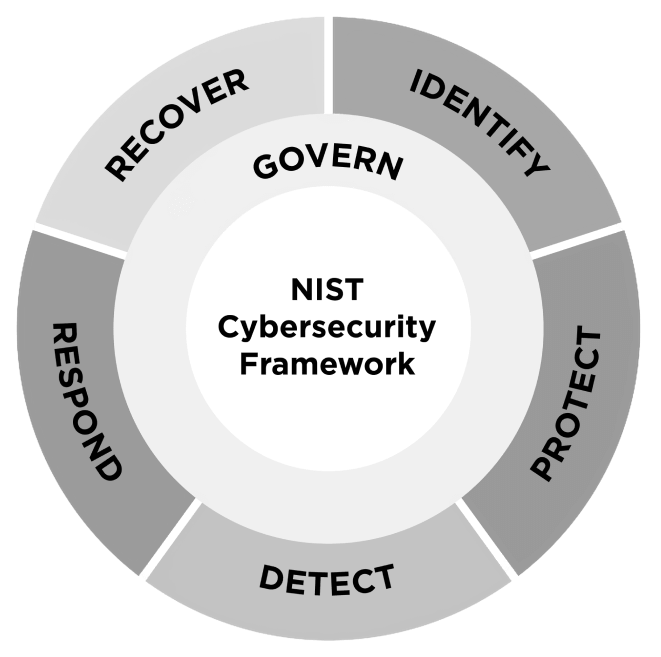
Identify
Understanding cybersecurity starts with a clear grasp of what’s at risk. The Identify function lays the groundwork by cataloging all assets, assessing vulnerabilities, and establishing a baseline for understanding the risk landscape of the organization. Think of it as the blueprint that guides every subsequent security effort. This step ensures you know exactly what needs protection and which vulnerabilities demand immediate attention.
Metrics like the percentage of assets inventoried and risk assessment coverage are instrumental here. The former helps confirm that all critical systems are accounted for, while the latter measures how effectively risks are being assessed and prioritized. With these insights, organizations can confidently address risks, focusing on what matters most.
Protect
Once you’ve identified the stakes, it’s time to put protective measures in place. The Protect function centers on reducing the likelihood of a breach by implementing safeguards such as access controls, employee training, and incident response planning. It’s the stage where proactive defenses are built to shield critical systems and data.
Monitoring the number of critical systems with updated safeguards ensures that essential systems are secured with the latest updates and configurations, effectively minimizing vulnerabilities. Similarly, the user training success rate gauges the effectiveness of cybersecurity awareness programs. Employees who can spot phishing attempts, or follow secure password practices become a key line of defense, reinforcing the organization’s security posture.
Detect
Even with strong defenses, no system is entirely immune to threats, which is where the Detect function comes into play. This stage focuses on early identification of anomalies and potential breaches through effective monitoring and alerting mechanisms.
Metrics such as mean time to detect (MTTD) and incident detection rate are crucial here. MTTD measures the speed at which the system identifies unusual activity—shorter detection times mean faster responses, reducing the window for damage. Meanwhile, a high detection rate ensures fewer threats slip through unnoticed. By catching issues early, organizations can limit the scope of an incident before it evolves into a larger problem.
Respond
When an incident does occur, the Respond function becomes critical. This phase is about taking swift and effective action to contain and mitigate the damage. Metrics like mean time to respond (MTTR) measure how quickly your team reacts, with faster response times minimizing operational disruption.
Another vital measure is recovery costs, which provides insights into the financial impact of incidents and highlights areas where investments in preparedness might yield better outcomes. Effective response isn’t just about damage control—it’s about preserving trust, maintaining continuity, and learning from the event to establish future readiness.
Recover
The final phase is Recover, where the focus shifts to restoring normal operations and addressing root causes to prevent recurrence. The efficiency of recovery efforts is reflected in metrics like business downtime post-incident and recovery time objective (RTO).
Shorter downtimes mean reduced disruption to business operations, while an established RTO ensures realistic goals for bouncing back after an incident. Recovery isn’t merely about restoring what was lost—it’s an opportunity to improve resilience and build stronger defenses for the future.
Together, these functions form a comprehensive, cyclical approach to cybersecurity. By integrating continuous improvement and tracking meaningful metrics, organizations can align their security efforts with broader business goals, ensuring they are not only mitigating risks but also preparing for an evolving threat landscape. Cybersecurity becomes less about reacting to crises and more about maintaining confidence, resilience, and control in the face of uncertainty.
The role of identity and access management in risk governance
Identity and access management (IAM) has come a long way from its early role as a basic gatekeeper, simply verifying usernames and passwords to grant system access. Today, as cyberthreats grow in complexity and the digital ecosystem expands, IAM has transformed into a sophisticated risk management solution that plays a pivotal role in an organization’s cybersecurity strategy.
Modern IAM solutions do much more than authenticate users. They serve as intelligent gatekeepers, not only controlling who can access systems but also evaluating the context, behavior, and risks associated with every digital interaction. This evolution has enabled IAM to become an essential component of comprehensive cybersecurity risk governance frameworks.
IAM solutions enhance governance by:
- Enforcing least privilege access, ensuring users only access what’s necessary.
- Automating periodic access reviews to maintain compliance.
- Detecting and responding to anomalous behavior, mitigating insider threats.
Integrating cybersecurity risk into enterprise risk management
Integrating cybersecurity risk into broader enterprise risk management (ERM) frameworks is no longer just an option—it’s a necessity. Cyber risks don’t exist in isolation; they ripple across the organization, affecting operations, finances, reputation, and even regulatory standing. To manage these risks effectively, organizations should align their cybersecurity strategies with their overall risk management practices, ensuring a unified, cohesive approach that brings every stakeholder on board.
One effective strategy is adopting a unified risk taxonomy—a common language that bridges the gap between technical teams and business leaders. For example, rather than describing risks in purely technical terms like “phishing attacks” or “vulnerability exploitation,” they can be categorized as “operational disruption risks” or “data confidentiality risks.” This reframing ensures that cybersecurity issues are understood in a context familiar to leadership and aligns them with broader organizational priorities.
Another crucial component is cross-functional collaboration. Imagine a scenario where the IT team discovers a vulnerability that could disrupt supply chain software. By involving representatives from the Legal, Finance, and Operations departments in the risk assessment process, the organization can assess the potential legal ramifications, calculate the financial impact, and prepare contingency plans to minimize supply chain disruptions. This collaborative approach ensures that every angle of the risk is addressed, avoiding siloed decision-making and fostering shared accountability.
Centralized reporting is the third pillar of integration. When risk data is scattered across departments, leadership struggles to see the full picture. Centralizing cybersecurity metrics alongside financial and operational risk reports provides decision-makers with a comprehensive view of the organization’s vulnerabilities. For instance, an enterprise might consolidate data on failed login attempts (cyber risk), delayed project timelines (operational risk), and unexpected compliance fines (regulatory risk) into a single dashboard. This bird’s-eye view empowers leaders to prioritize mitigation efforts where they’ll have the greatest impact.
By weaving cybersecurity risk seamlessly into ERM frameworks, organizations can break down silos, uphold collaboration, and advance cybersecurity from a technical concern to a strategic business priority. This unified approach not only strengthens the organization’s risk posture but also builds resilience, ensuring risks are managed proactively and holistically.
Best practices for cybersecurity risk governance
Executive leadership is where it all begins. Strong governance starts at the top, with clear directives from leadership. When executives prioritize cybersecurity, it sets the tone for the entire organization. Research indicates that organizations with strong leadership support for cybersecurity initiatives are significantly more likely to achieve successful security outcomes. For instance, Accenture’s Cyber-Resilient CEO report found that cyber-resilient CEOs—those who actively engage in cybersecurity—outperform their peers in managing cyberthreats effectively, leading to lower breach costs and better overall performance.
Next up is having defined policies. Establishing strong policies clarifies roles, responsibilities, and escalation paths. This structured approach improves accountability and simplifies response efforts when threats arise.
Another essential element is continuous training. Building a culture of cybersecurity awareness through ongoing education helps employees recognize potential threats and respond appropriately.
Measurable metrics are also crucial. Using data-driven insights empowers organizations to track progress and identify areas for improvement. For example, by monitoring metrics like the number of attempted breaches or employee compliance rates with security protocols, organizations can pinpoint weaknesses and adjust their strategies accordingly.
Failing to incorporate these best practices could leave your organization vulnerable to devastating security breaches, operational inefficiencies, and compliance failures. Without strong governance, defined policies, continuous training, and measurable metrics, you risk falling behind the constantly changing risks and challenges in cybersecurity, exposing your organization to unnecessary risks.
However, addressing these challenges is entirely within reach. Our advanced AD management solution enables you to adopt these best practices with ease—enabling reliable policy enforcement, efficient workflows, and insightful reporting. It’s time to ensure your organization stays strong and secure.
Enhancing your AD security with AD360
Having a solution that stays committed to your journey in safeguarding your AD is not just an advantage—it’s a necessity. Risk identification is only the beginning; effective risk management is about proactively addressing vulnerabilities before they become liabilities.
This is where ManageEngine AD360 comes in. It not only provides the solutions to identify risks but also the means to act on them effectively.
Our governance, risk, and compliance (GRC) features ensure your AD management aligns with organizational policies and regulatory requirements. By automating access certification campaigns, you can regularly review user privileges and prevent privilege abuse, a common cause of insider threats.
Compliance isn’t just about audits; it’s about creating accountability. With detailed reports on access patterns and security events, you’ll have the clarity to demonstrate both your compliance posture and your proactive approach to risk governance.
You can also stay ahead of potential threats with custom alerts for unusual activities, like unauthorized privilege escalations or access attempts outside regular hours. This ensures that you’re not just reacting to incidents but actively preventing them from escalating.
By embedding best practices into your AD management strategy, our solution empowers your organization to maintain an environment that is both secure and agile. It’s about more than risk—it’s about building resilience.
