- Features
- Benefits
- FAQs
- Next step
Features
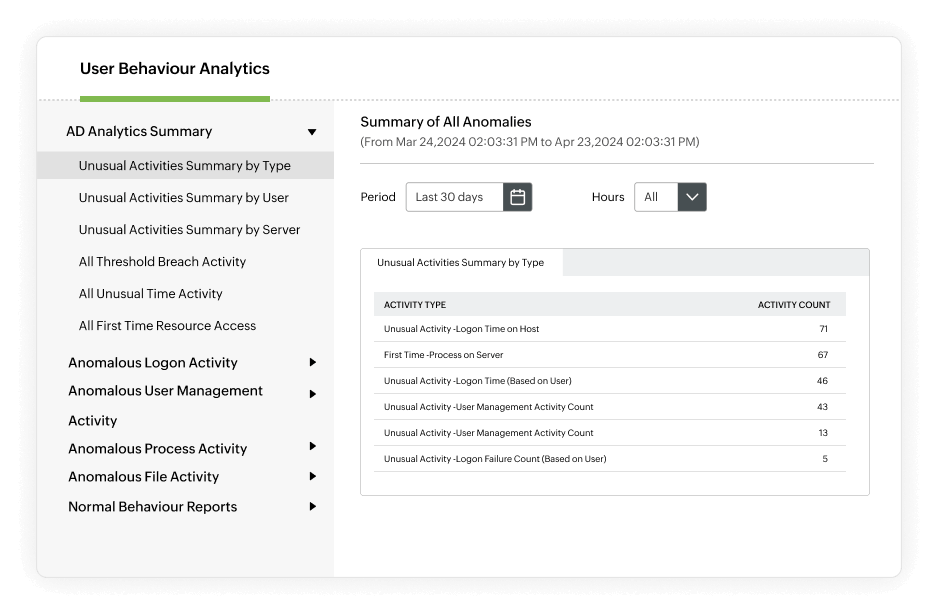
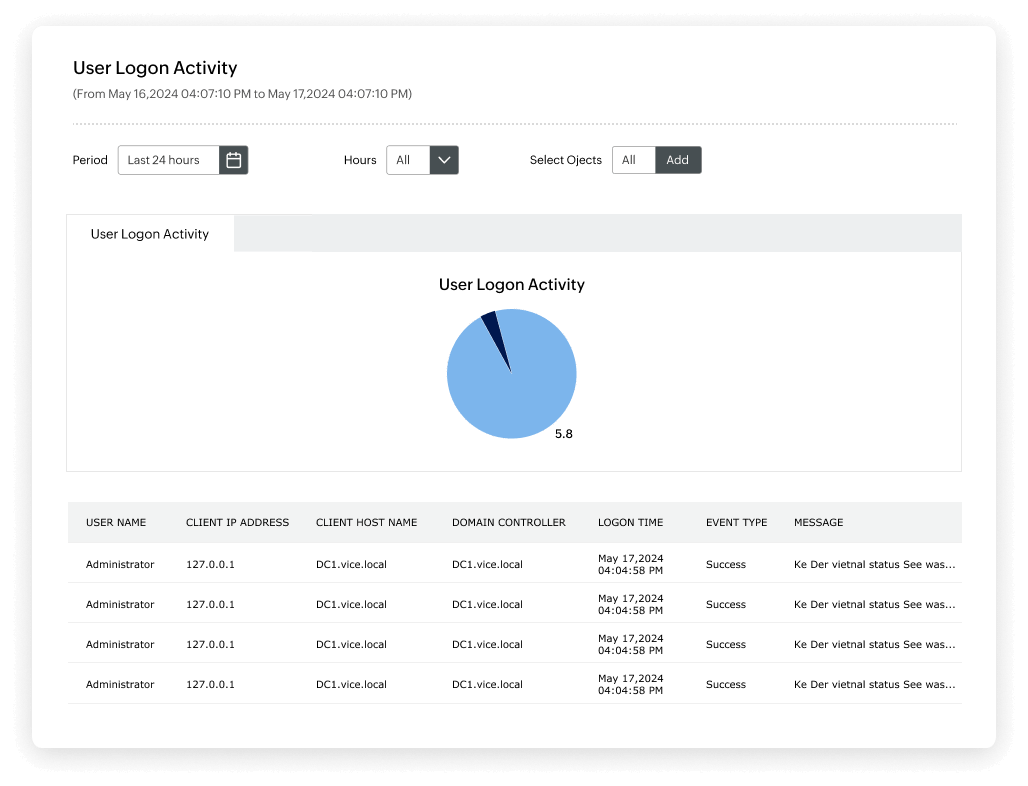
Utilize User Behavior Analytics (UBA)
- Identify suspicious user activities such as an unusually high volume of events and file activities carried out at unusual times.
- Identify the source and reason behind every failed logon attempt, and find user accounts with the highest percentages of logon failures.
- Audit privilege use, and report on critical events like password resets, user management, and privilege escalations.
Leverage Attack Surface Analyzer (ASA)
- Detect 25+ AD attacks, including credential access (e.g., Kerberoasting, Golden Ticket, DCSync), lateral movement (e.g., pass-the-hash, pass-the-ticket, ransomware), and privilege escalation (e.g., RID hijacking).
- Spot 15+ network attacks and 20+ process attacks like Indirect Command Execution by leveraging the MITRE ATT&CK framework.
- Identify risky Azure, AWS, or GCP configurations, like allowing public access to a virtual machine, which exposes it to attacks like brute-force.
Monitor file and folder changes
- Continuously track the who, what, when, and where behind every file change along with failed attempts to change a file.
- Track changes across Windows, NetApp, EMC, Synology, Huawei, Hitachi, and Amazon FSx for Windows file servers.
- Receive email and SMS alerts for critical file and folder changes, with customizable thresholds to detect mass changes.
- Keep a comprehensive audit trail of every change and meet SOX, HIPAA, PCI DSS, GDPR, FISMA, and GLBA requirements.
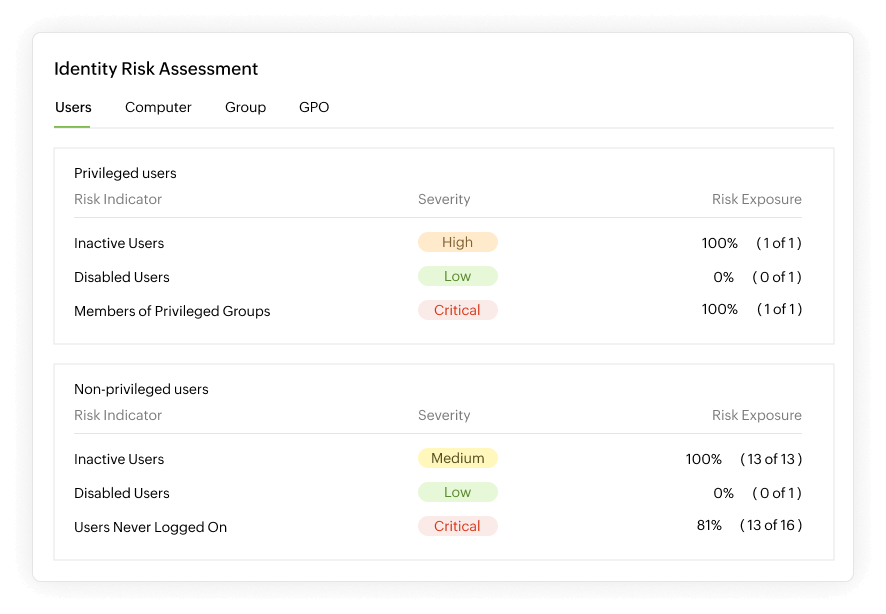
Benefits of identity analytics
Early threat detection
Uncover and remediate unusual user behavior using UEBA, enabling timely alerts for dormant accounts and anomalies, preventing potential security threats using AD360
Context-aware access
AD360 enables risk-based contextual authentication to enhance access control by considering factors like IP address, geolocation, device type, and access time, contributing to a more secure authentication process
Agile response to user activities
With AD360, you can track and monitor identities across platforms with the provision of real-time notifications for remote host access, offering deeper insights into users' work patterns and facilitating agile responses to user activities
Secure remote workforce
Systematic schedules for remote work enhance employee productivity, ensuring a well-organized approach to managing identities across various platforms during remote work scenarios
FAQs
How does AD360 use UBA to uncover and remediate unusual user behavior?
AD360 leverages User and Entity Behavior Analytics (UEBA) to detect unusual user behavior, receive alerts for dormant account activations, and circumvent excessive privileges through risk-based access certifications.
How can AD360's risk-based contextual authentication enhance security?
AD360's risk-based contextual authentication configures access control based on factors like IP address, geolocation, device type, and access time, allowing you to measure potential vulnerabilities and derive risk scores.
How does AD360 track and monitor identities across all platforms?
AD360 provides real-time notifications for remote host access and offers insights into users' work patterns It also allows you to create systematic schedules for enhanced employee productivity during remote work.
What benefits can I expect from AD360's identity analytics solution?
AD360's identity analytics solution helps uncover and remediate unusual user behavior, enhances security through risk-based authentication, and provides tools for real-time monitoring and productivity improvement.
How does AD360 contribute to circumventing the review of excessive privileges?
AD360's "Identity Analytics" allows you to circumvent the review of excessive privileges through risk-based access certifications, providing insights into potential vulnerabilities.