Application Allowlisting
Over 30 percent of all critical security issues are made up by application-related vulnerabilities. With this number rising rapidly, if you're depending on your antivirus software to save you, it's very unlikely that your enterprise will withstand the next major exploit. An application allowlisting software is a must to achieve a well-rounded and secure application environment.
Preventing threats with application allowlisting.
Ongoing technological advancement has led users to depend on applications for even the smallest tasks, aided by big and small vendors alike creating new applications by the minute. Due to the increase in demand and lack of time, vendors often rely on open source code to build their applications. Attackers have started to leverage this trend by inserting their own backdoors into open source code so they can easily launch malware or steal data.
Enterprises must take caution to ensure that applications allowed into their network can't be exploited in an attack. By creating application allowlists, you can exercise total control. ManageEngine Application Control Plus, a comprehensive application allowlisting solution, simplifies the allowlisting process into just a handful of steps. Refer here to learn more about allowlisting and blocklisting.
How to allowlist applications using Application Control Plus?
Traditional application allowlisting comes with the hassle of list management, which is why enterprises usually shy away from it and opt for antivirus solutions to prevent malware intrusions through applications. Application Control Plus breaks all such norms with its self-updating Application allowlisting feature. Unlike your typical antivirus software, our application allowlisting takes on a proactive approach when it comes to dealing with these vulnerabilities, giving you the best chance of withstanding an attack. Here's how Application Control Plus helps you create an application allowlist:
Application discovery
The first step in any application control process is discovering which applications are installed in the network. Application Control Plus' agents scan every endpoint and provide a list of the applications installed in them, along with details of all their executables.
Application grouping
Application Control Plus' application allowlisting software builds and updates the allowlist automatically based on the discovered applications’ compliance with your selected policies. The following policies can be configured:
Trusted vendors
Trusting software vendors without valid certificates can cause backdoor attacks if those vendors are using open source code. Hence, only authorized vendors of the installed software will be displayed to you. From this, only applications that belong to the vendors you choose will be added to the allowlist.
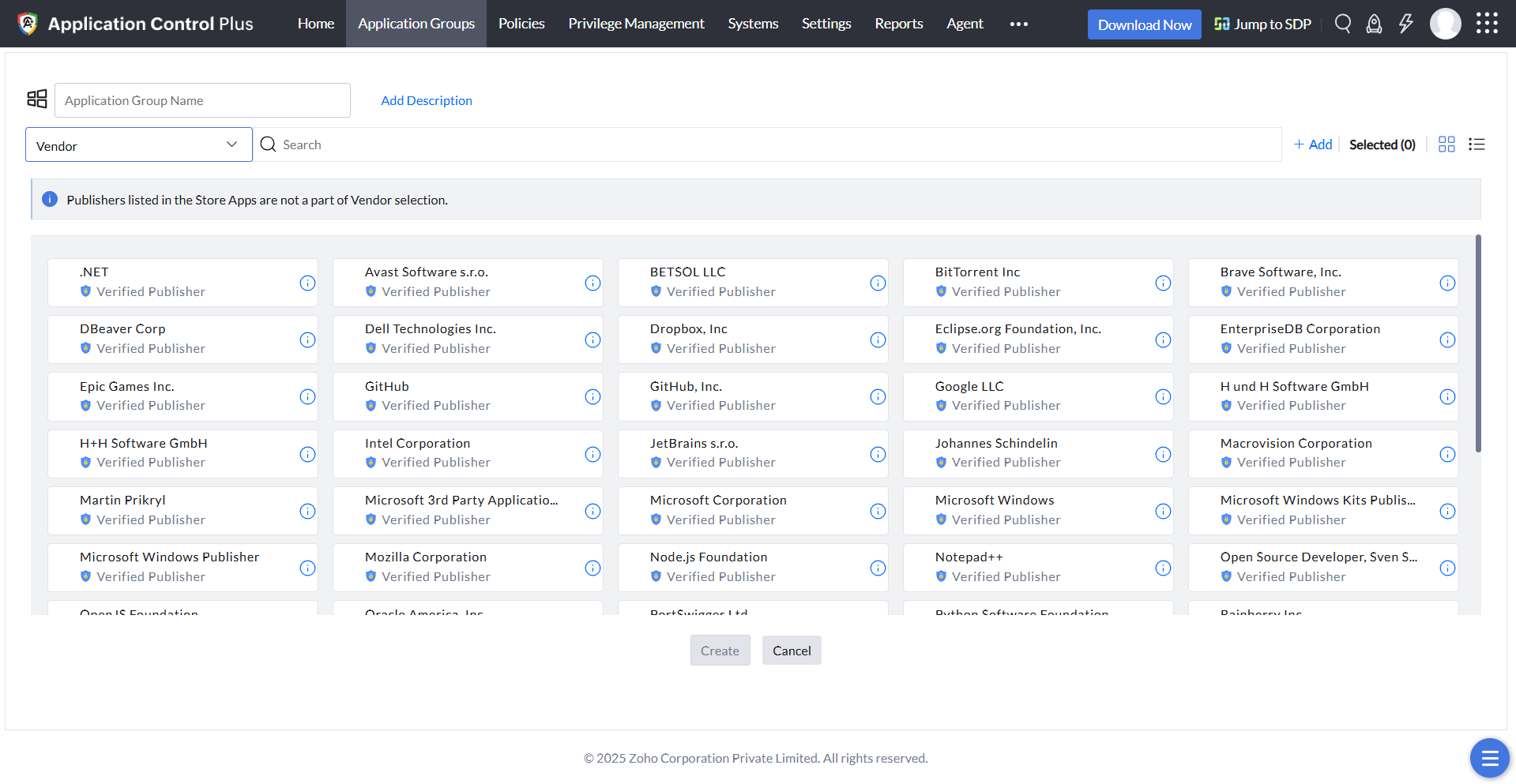
Product name
If you want to allowlist certain products from the same vendor, this type of policy can be opted for instead of the trusted vendor rule.
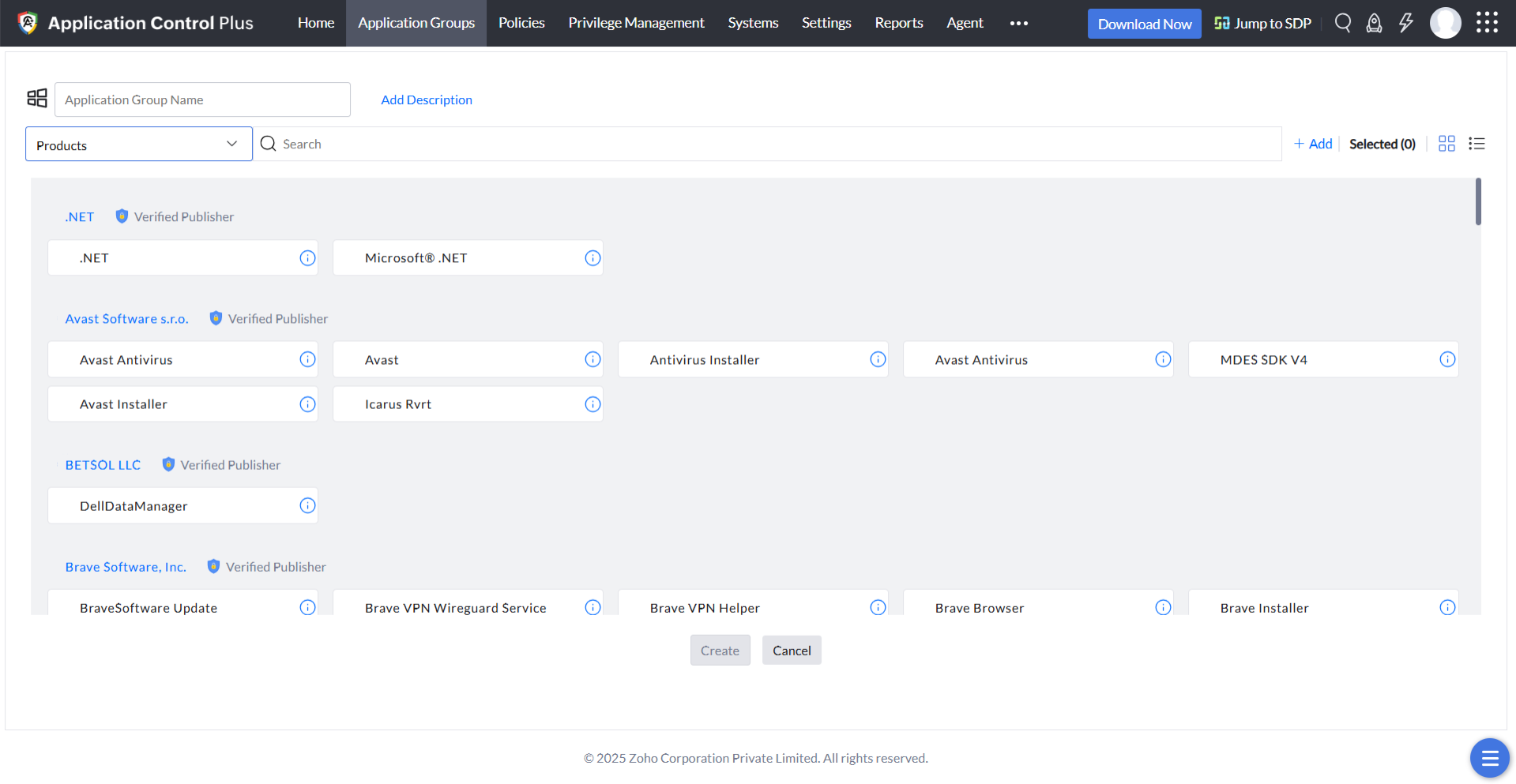
Verified executables
Applications are made of multiple executable files, with vendors assigning a digital certificate to each executable to vouch for its authenticity. Application Control Plus displays these verified executable files to you, from which you can select the EXE files to be allowlisted. This policy is critical when it comes to maintaining a secure network, as a file will not be allowed to execute if its digital certificate has been tampered with. Even EXEs added to applications in the form of updates will not be allowed to run if they aren't allowlisted.
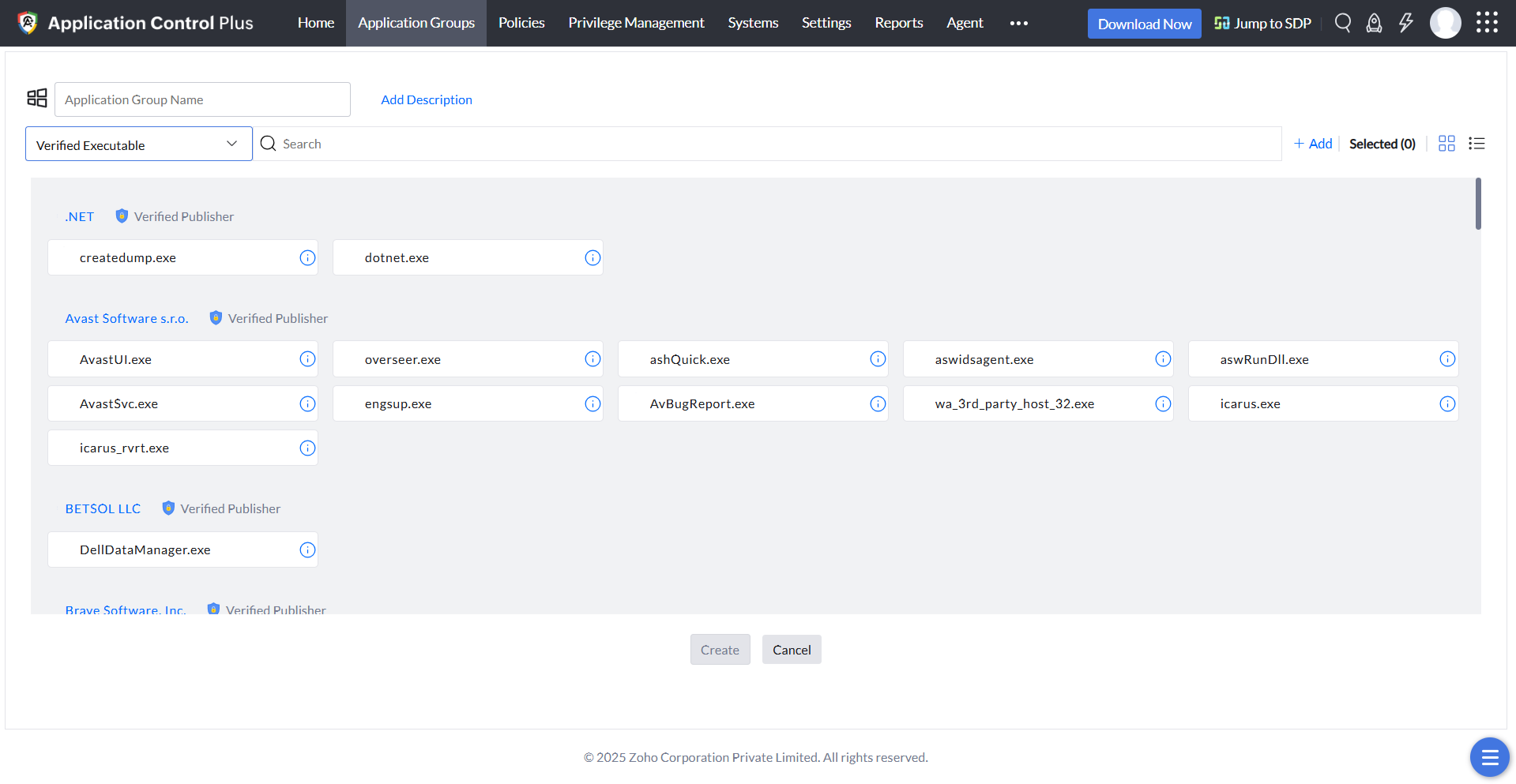
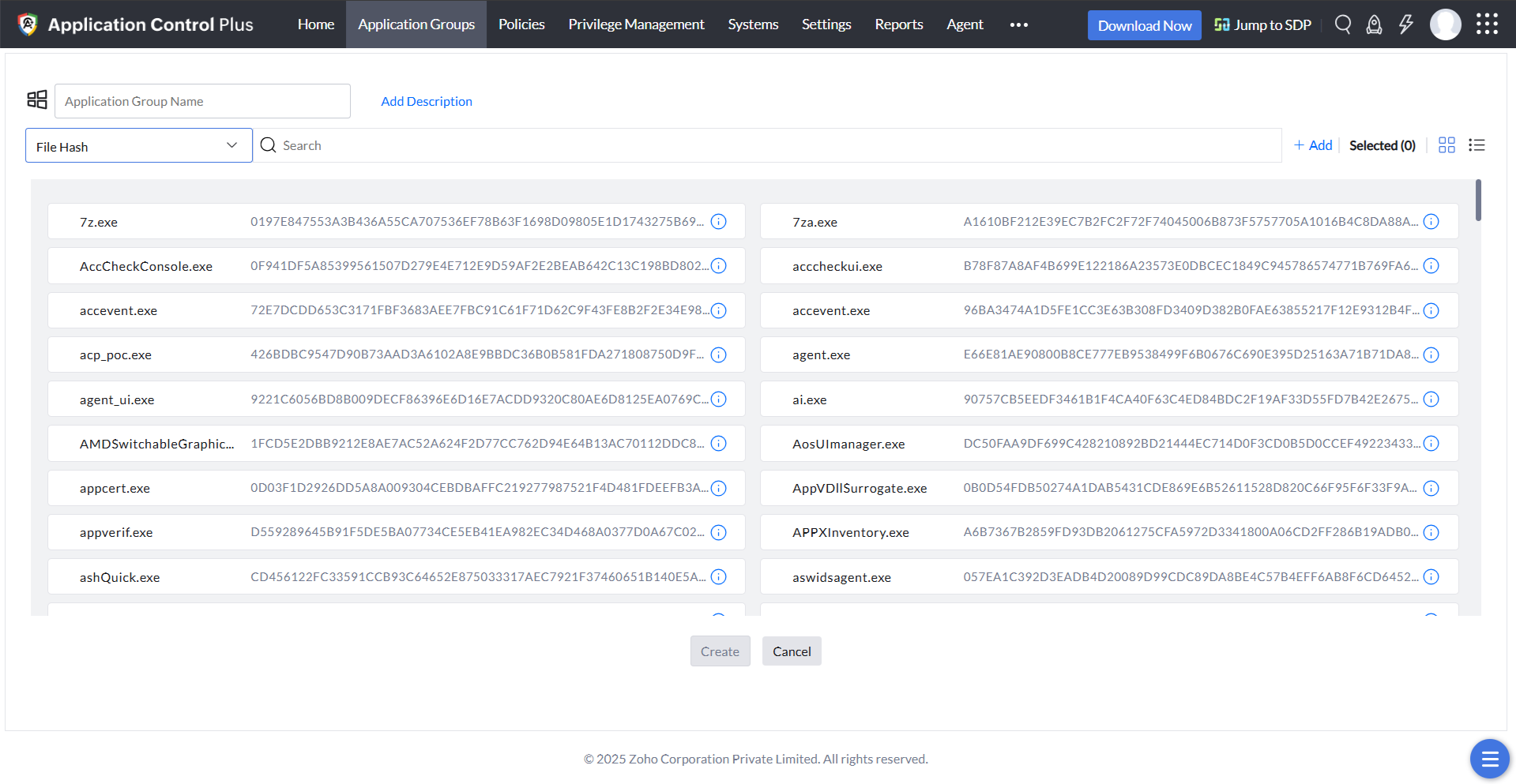
File hash
This is the most secure policy, as it's based on the hash value of the executable file. All executable files of the running processes, including those that don't have a valid digital certificate, will be displayed to you. You can choose all the files that you wish to allowlist; after that, even the smallest change to the file, such as a revision of the file's version, will change its hash value, meaning the file will be removed instantly from the application allowlist. This policy is perfect if you want to run only extremely specific executables.
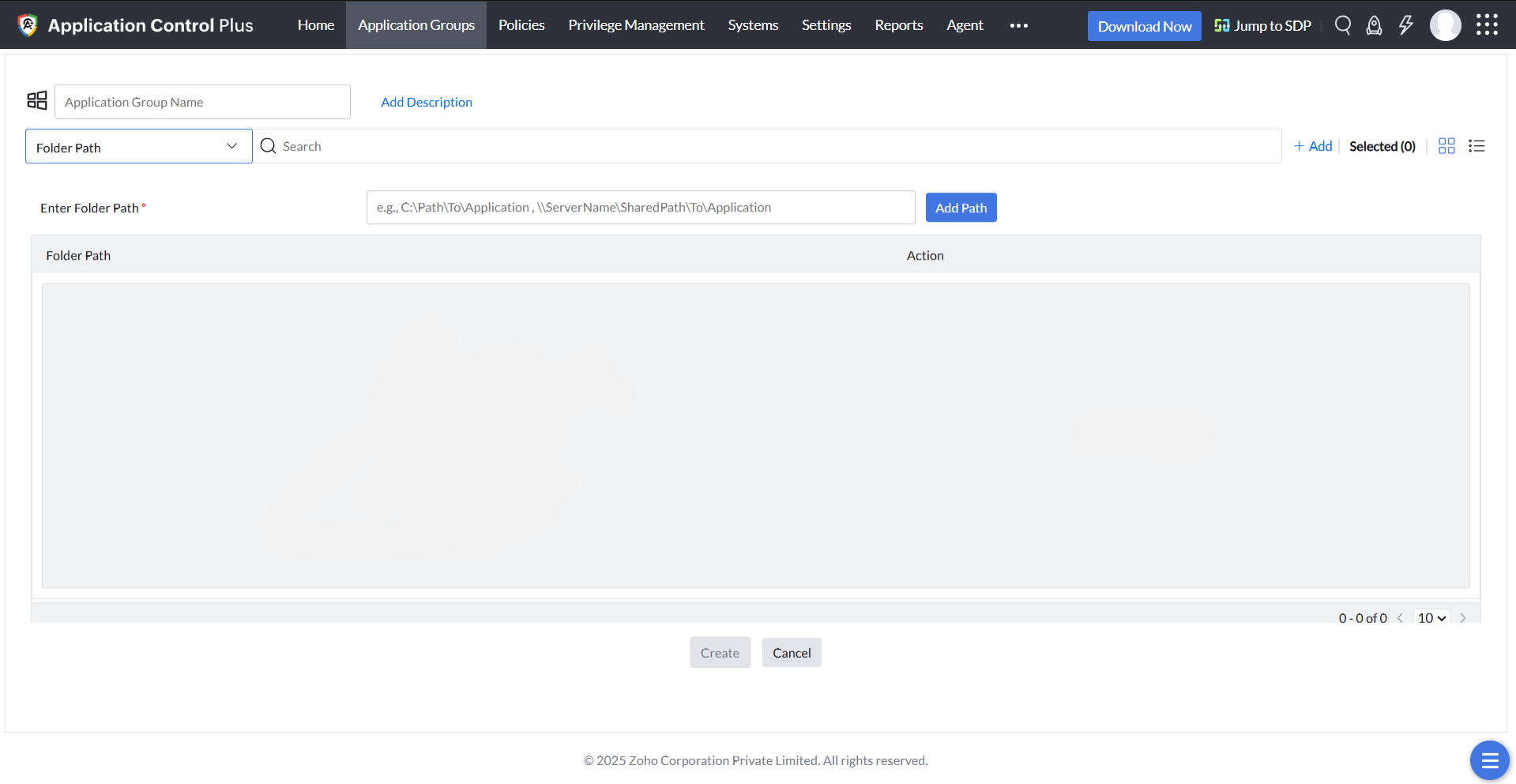
Folder Path
This policy makes application allowlisting very simple for you. You can put all the applications that you trust into a folder to allowlist those apps in one go.
StoreApps Rule
Along with facilitating the allowlisting of legacy applications, Application Control Plus also provides support for Windows 10 and 11 Store Apps. This rule discovers all the StoreApps that run in the managed endpoints and lets you instantly allowlist the applications of your choice.
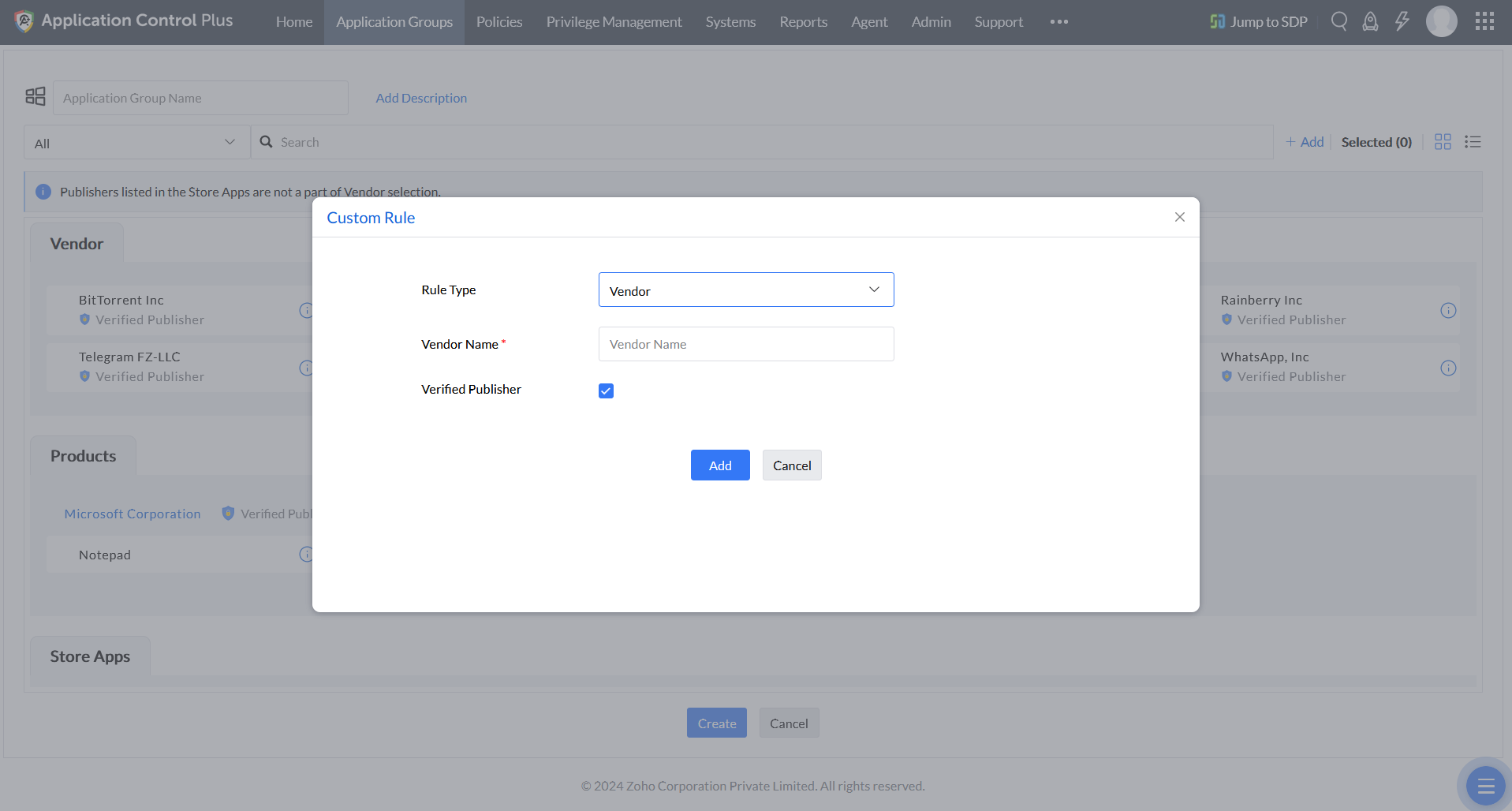
Custom Rule
This feature lets you define specific criteria such as the vendor, product name, verified executable, or file hash to create application rules that are not detected in your network.
The application allowlist will be created automatically according to the policies chosen, and will be updated whenever new applications are discovered.
Associating applications
Users with the same role generally require similar applications. You can assign applications to individual users based on their requirements, or create custom groups of users and associate those groups with application allowlists specifically built to satisfy their needs using relevant policies. Application Control Plus' application allowlisting feature allows you to associate multiple application allowlists with the same custom group, and vice versa.
Application Allowlisting - FAQs
What is Application Allowlisting?
Application allowlisting is the process of creating a list of trusted applications and allowing only those apps to run on managed devices. The concept of allowing only what you trust cannot be taken lightly, considering applications tend to be the route through which cyberattacks occur, leading to either major financial losses or massive data leakage.
Why is application allowlisting important?
The scope of application allowlisting doesn't just end with malware protection. Creating application allowlists also streamlines inventory management. Enterprises usually grant all users access to most applications, even if they're irrelevant to a user's role. In such cases, users end up having several unused applications running on their devices. Not only do these applications consume storage space, but you waste time managing the licenses and patches associated with these unnecessary apps.
Application allowlisting solves all these issues in that it allows users to use only specific applications based on their role and job requirements.
Supported OS Versions
Application Control Plus facilitates application allowlisting in versions of the OS such as Windows 7 and above, Windows server 2008 R2 and above, and Mac OS 11 Big Sur and above.
Packed with other cutting-edge and essential features like Application Blocklisting, Endpoint privilege management, and Just-in-time Access our endpoint application allowlisting software takes a comprehensive approach to application control with options to handle privilege elevation. Try Application Control Plus free for 30 days and see all the features for yourself!
