In order to build a strong and secure IT environment, it's essential to establish a foundation built on basic security principles. According to Forrester, 80 percent of security breaches involve the credentials of privileged accounts. With the stakes set so high, a security principle to prevent these attacks has become the need of the hour. The principle of least privilege (POLP) is one such concept that, when properly implemented, can minimize the attack surface considerably.
The principle of least privilege refers to the concept of lowering enterprise-wide privileges to the bare minimum required to perform an entity's job. It not only pertains to users, but also to systems, processes, applications, services, and other devices.
Normally, privileges are assigned to users based on their role, department, hierarchical position, etc. Even though this is common practice, it may be doing more harm than we realize. According to a study, 99 percent of user privileges are unused and post a potential risk to the network. Along with being stringent about handing out privileges, authorities need to have a thorough understanding of the enterprise, the employees, and their job requirements before they assign privilege access.
After quantifying and qualifying every employee's needs, the POLP recommends making most user accounts "standard" or "least privileged user" accounts.These least privileged user accounts will only have the privileges required to do every day business-critical activities, with no access to administer other network resources. Here is how an organization can implement the POLP:
Local User accounts created and added to the Administrator Group in a computer are considered as local administrator accounts. They can stripped of these privileges either by manually shifting them to the standard User group or by deploying scripts for the same.
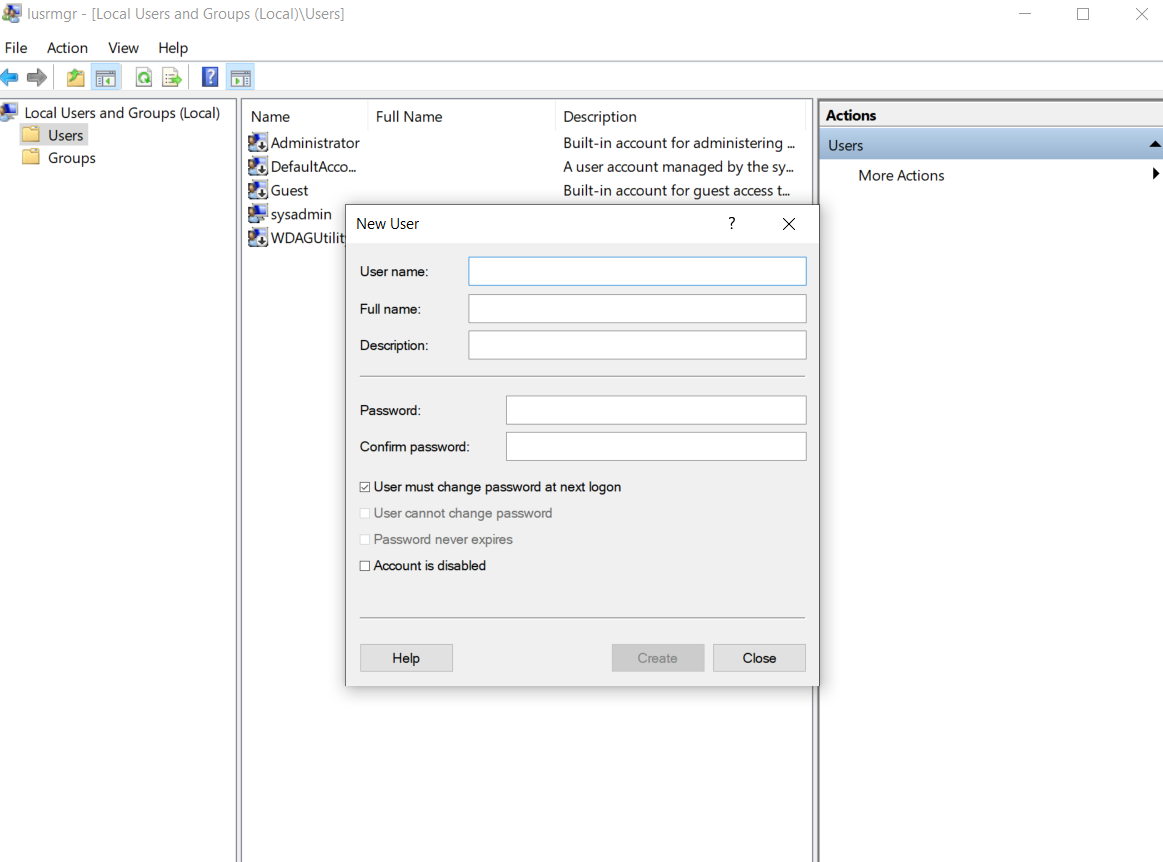
Identify and remove unnecessary accounts from the Administrator group and add them to the standard Users group instead.
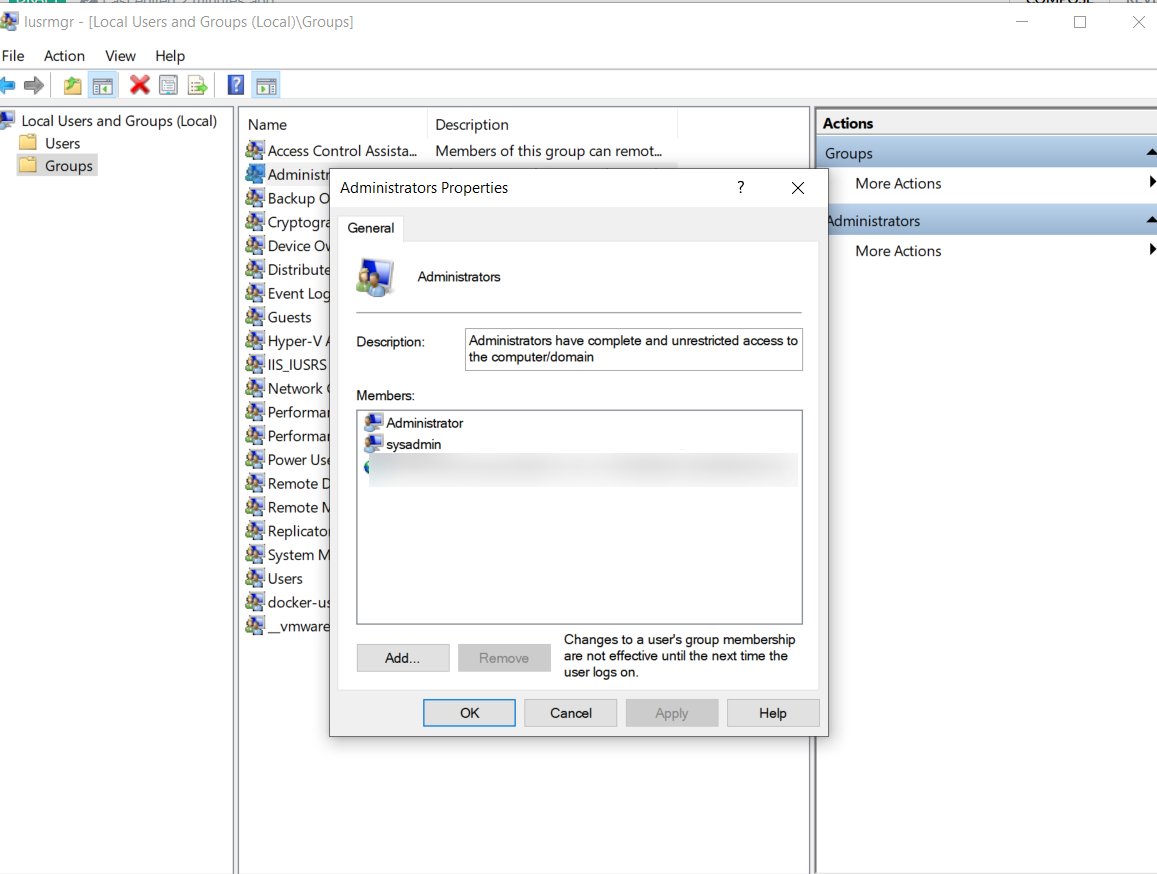
By removing these admin accounts, all employees will be left with only the bare minimum privileges required by them to execute their functions. However, it is not that simple. While being highly advantageous for an organization's security posture, the Principle of Least Privilege comes with its set backs.
Many enterprises struggle with establishing POLP because of the consequences it can have on productivity. Having only limited admin accounts can improve security, but what happens when standard users accounts require administrator-level privileges for last-minute critical tasks? They either need to be provided with privileged admin credentials, or they needed to be added back into the Administrator group.
Along with being inconvenient and time-consuming, these re-elevated privileged accounts can pose major security threats as they are seldom revoked once those requirements are fulfilled. In order to ensure productivity without compromising on security, the POLP can be established with privilege bracketing enabled.
In this approach, instead of elevating the entire user's account, standard users will be given only the elevated privileges they require, on demand. The privileges given and the associated user behavior must be properly monitored. Once the requirement is fulfilled, the privileges would be automatically lifted.
If privileges are not revoked once the demand is satisfied, users could stock up on privileges unnecessary for their daily activities. This accumulation of unnecessary privileges is known as privilege creep, and must be completely eliminated, as malware attacks targeting these accounts can bring down the entire enterprise.
Application Control Plus does an essential part of privilege bracketing with respect to applications and their privileged access, which enables enterprises to establish the POLP without worrying about productivity drops.
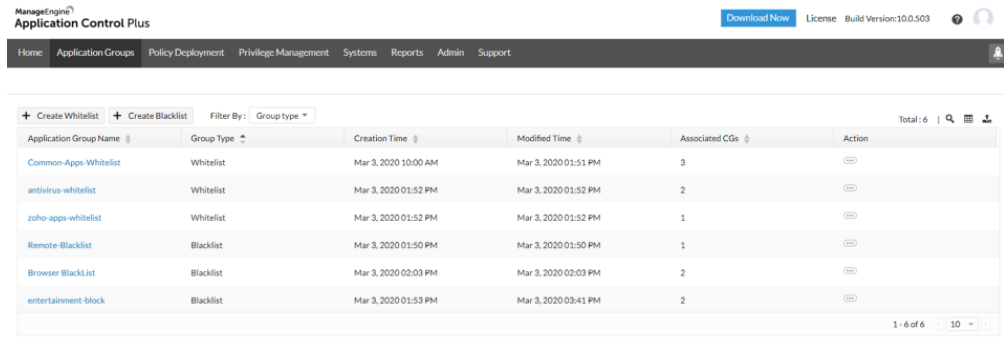
Application allowlisting and blocklisting features can also be leveraged to create trust-oriented lists, which govern who has the privilege to run which application.
Once the POLP has been established by moving all the employees to the standard User Groups, Application Control Plus assures that none of the business critical advancements are hindered. Using the Endpoint Privilege Management, instead of elevating the users, privileges specific to applications can be elevated when required. This enables authorized users to run essential applications as administrators from their standard user accounts. With Application Control Plus you can:
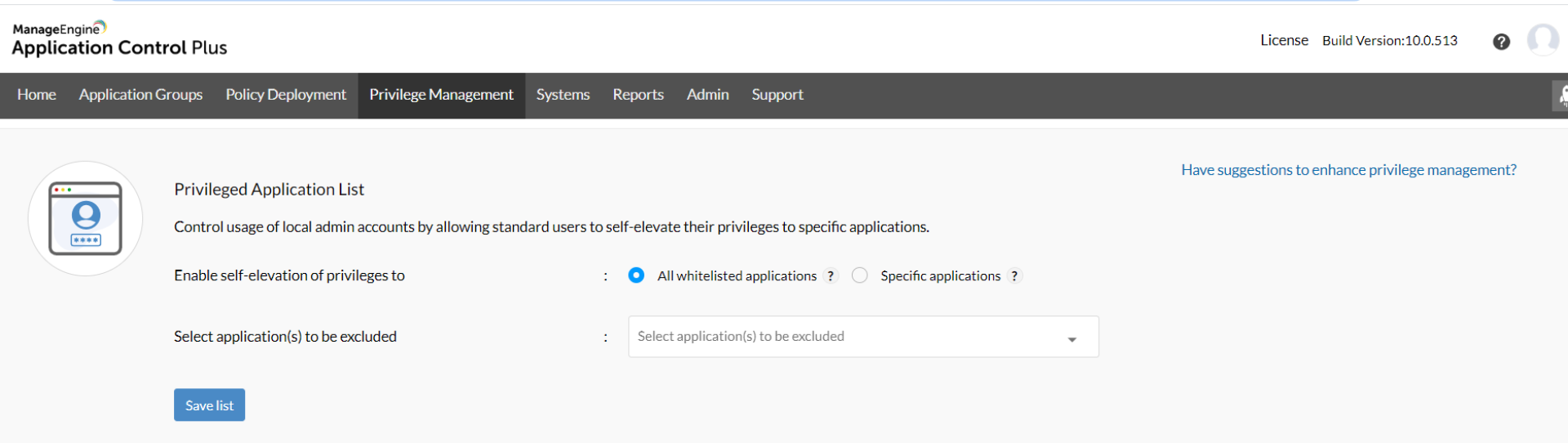
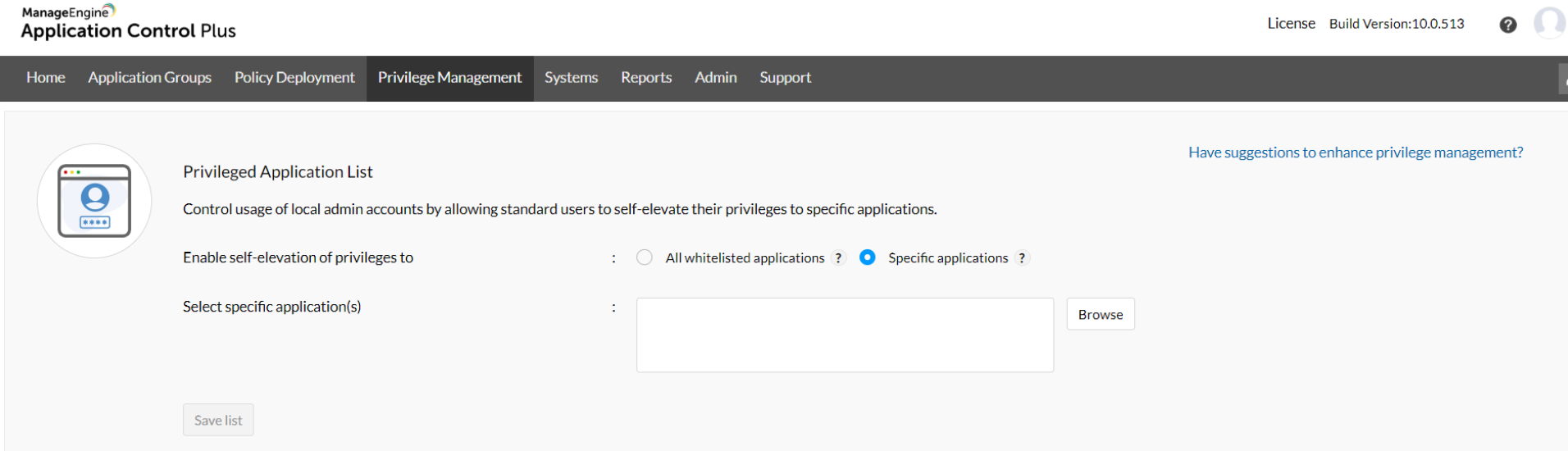
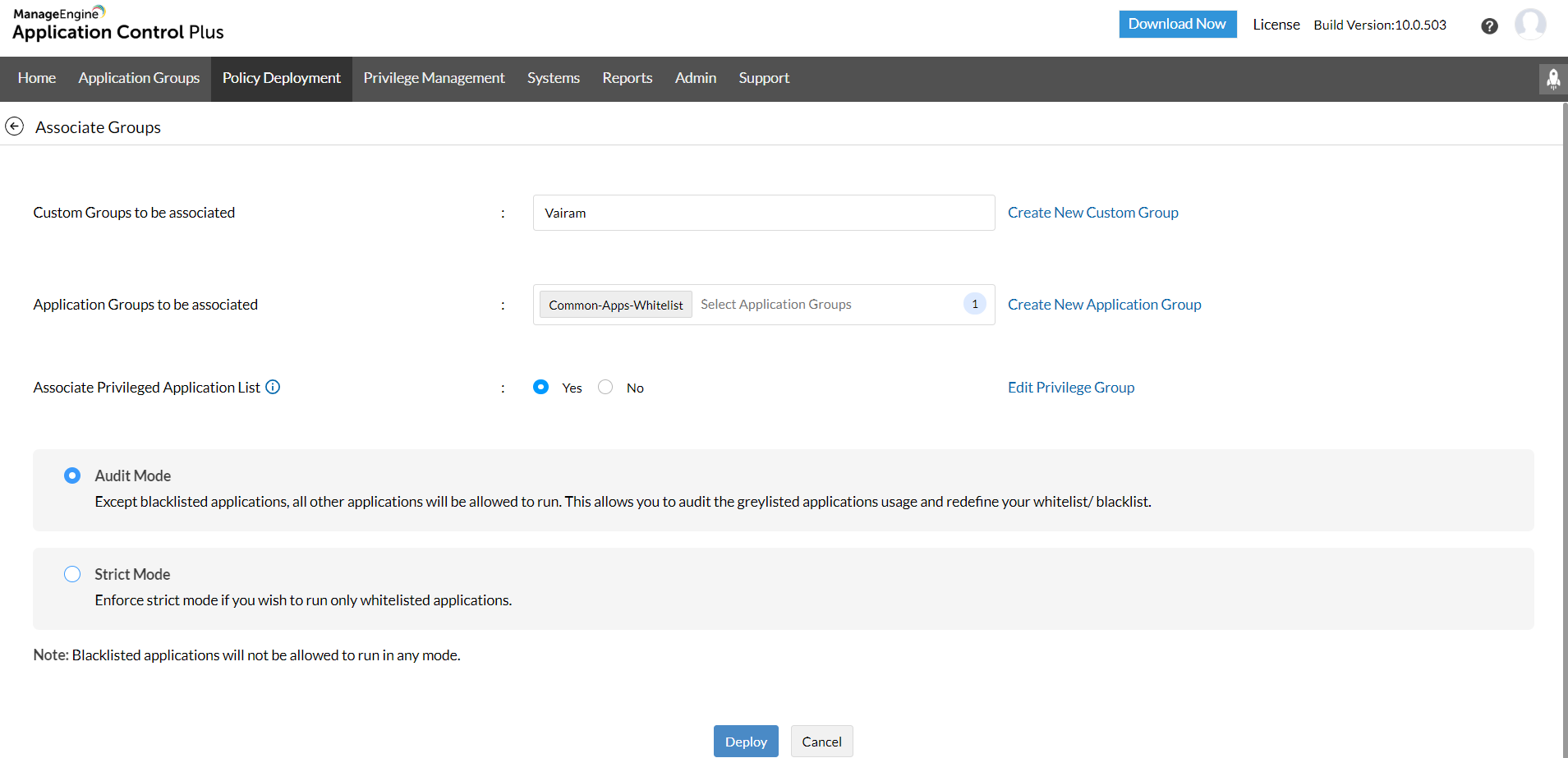
Deleting the policies created after fulfilling the requirements can prevent the existence of privilege creep.
Try Application Control Plus free for a trial period of 30 days, and protect your network!