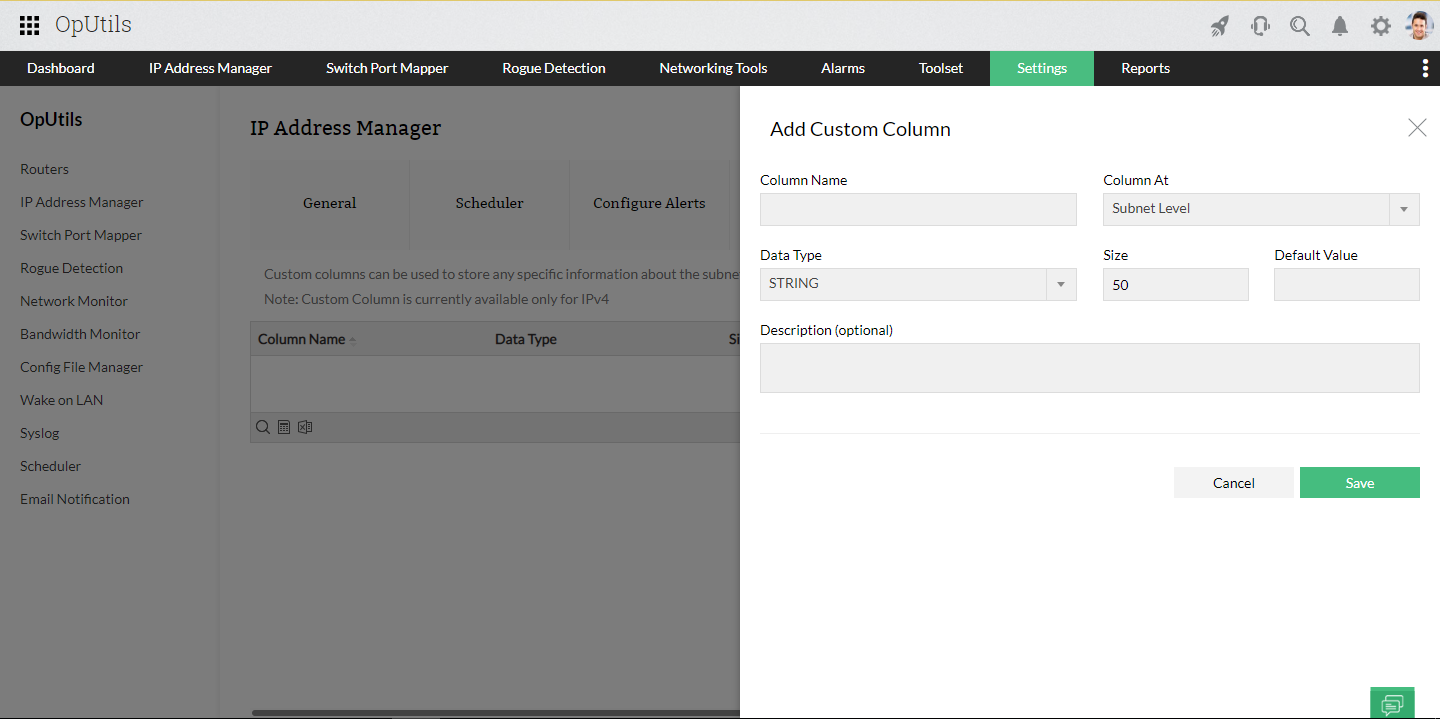
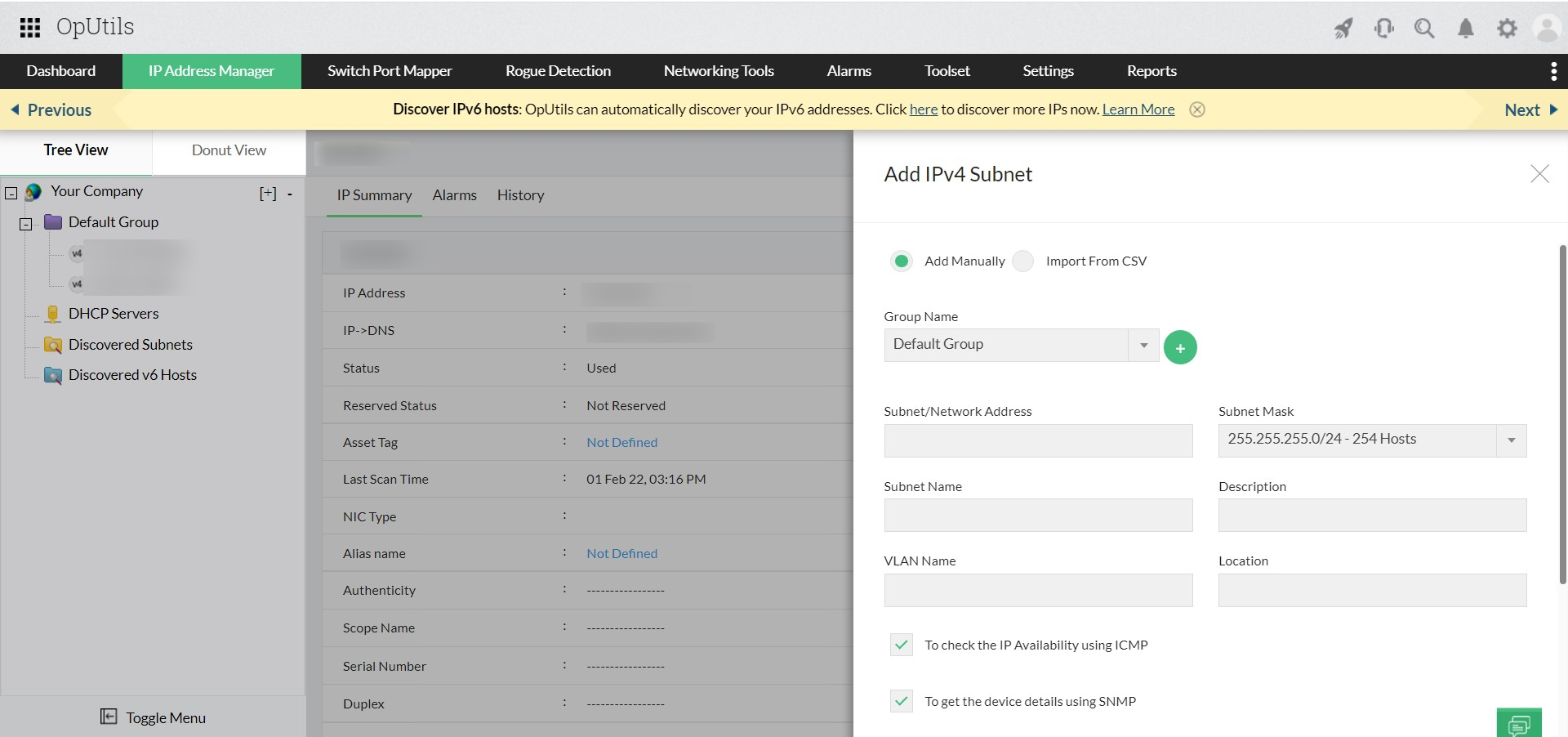
Scan IP addresses in seconds for real-time IP availability monitoring
IP availability plays a critical role in managing and diagnosing enterprise networks. Relying on spreadsheets or manual tracking often leads to inefficiencies, making IP scanning a time-consuming task for IT admins.
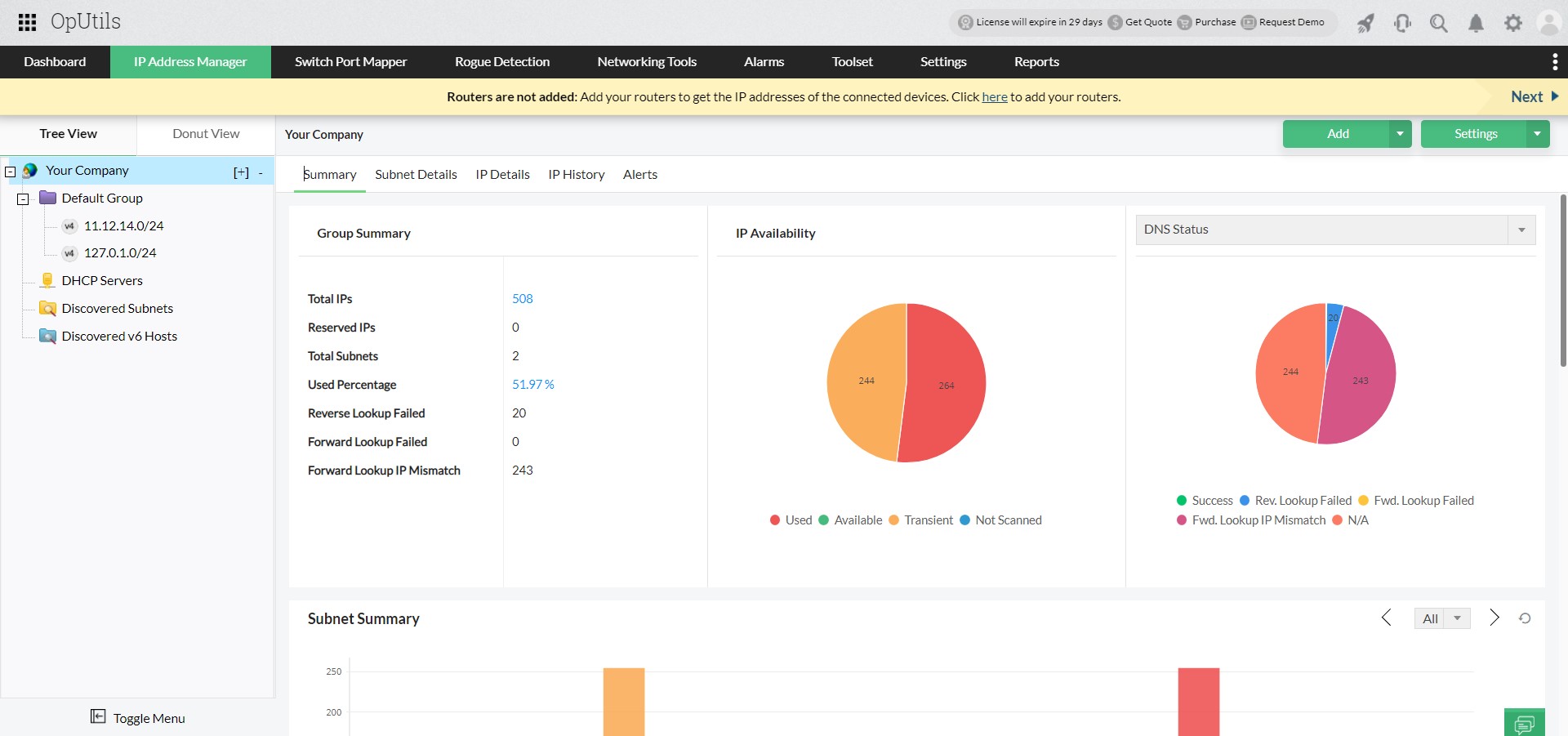
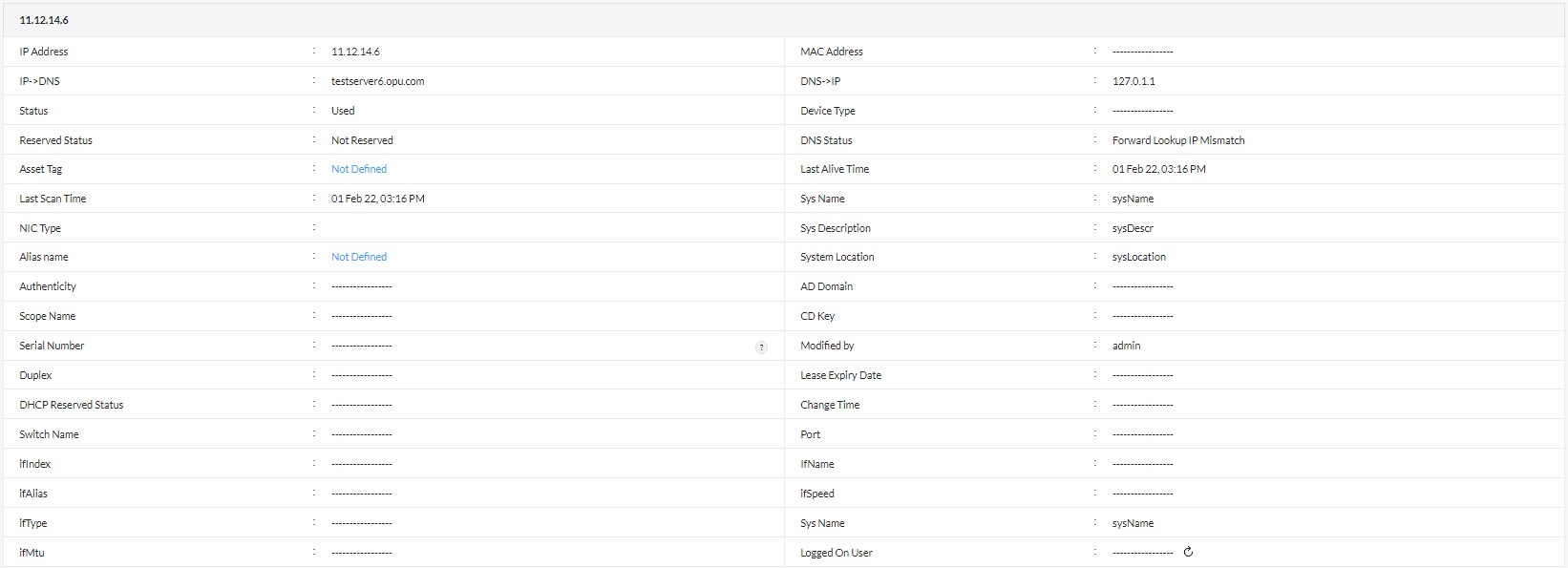
OpUtils’ advanced IP scanner eliminates this complexity by scanning your entire IP address space in seconds. Integrated with Active Directory, it provides real-time availability insights across IPv4 and IPv6 subnets. These insights help network teams plan capacity, avoid address conflicts, and ensure efficient IP utilization.
The scanner continuously monitors your network and classifies each IP address into one of three availability states:
- Available – IP addresses that are unassigned and ready for allocation.
- Transient – IPs linked to devices that temporarily connect to the network, such as mobile or roaming endpoints.
- Used – IP addresses currently in use and unavailable for reassignment.
With support for multi-subnet scanning and AD integration, the advanced IP scanner simplifies IP address tracking and provides full visibility into address utilization across your network.