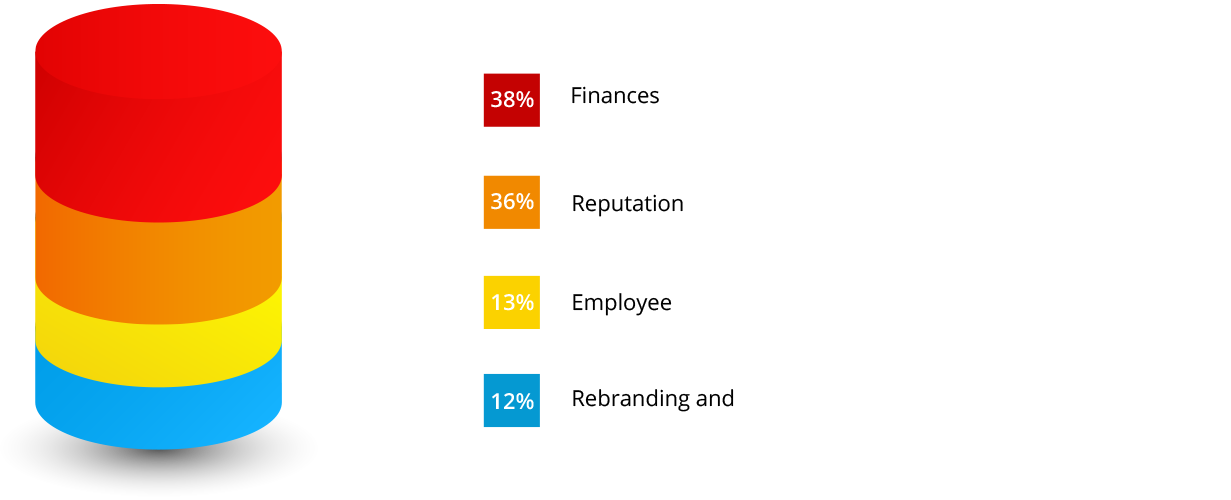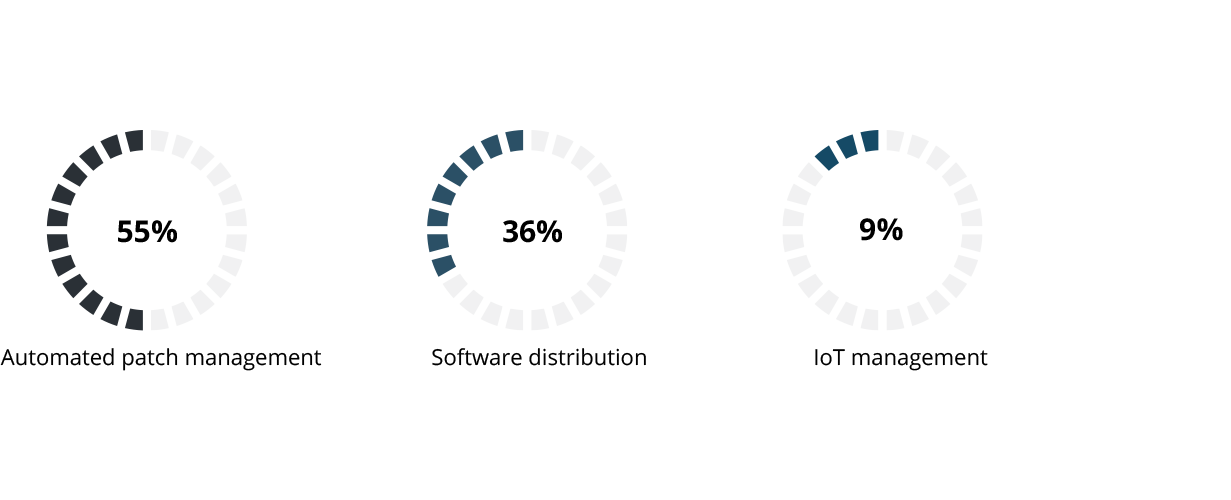Veja o infográfico completo
The recent increase in cyberattacks
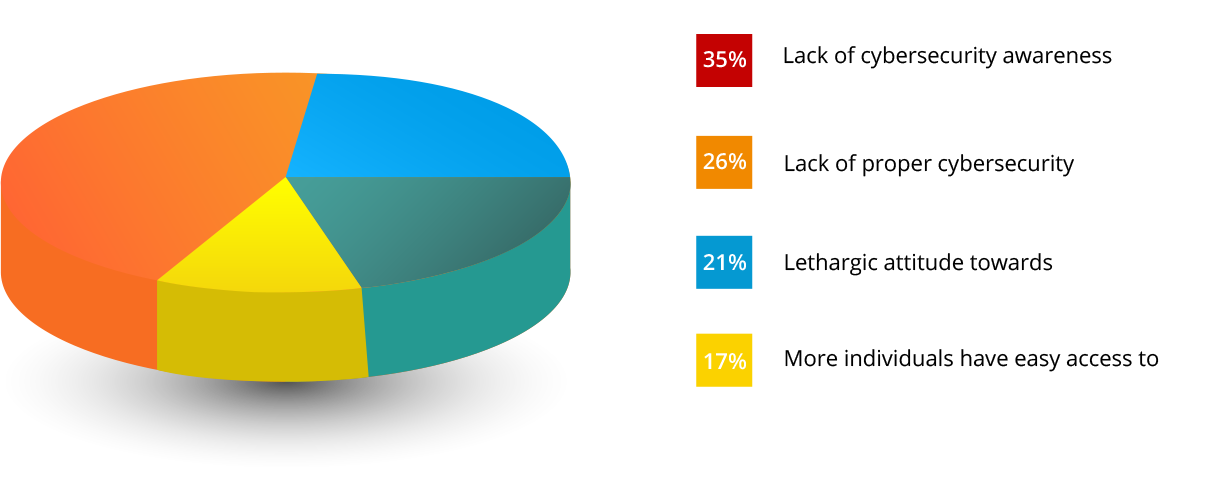
Digital transformation and easy access to the internet have greatly benefited our society, but they've also contributed towards the evolution of cyberattacks. In our survey, 35 percent of professionals showed a lack of cybersecurity awareness, and 26 percent lack proper cybersecurity controls.
Business impact
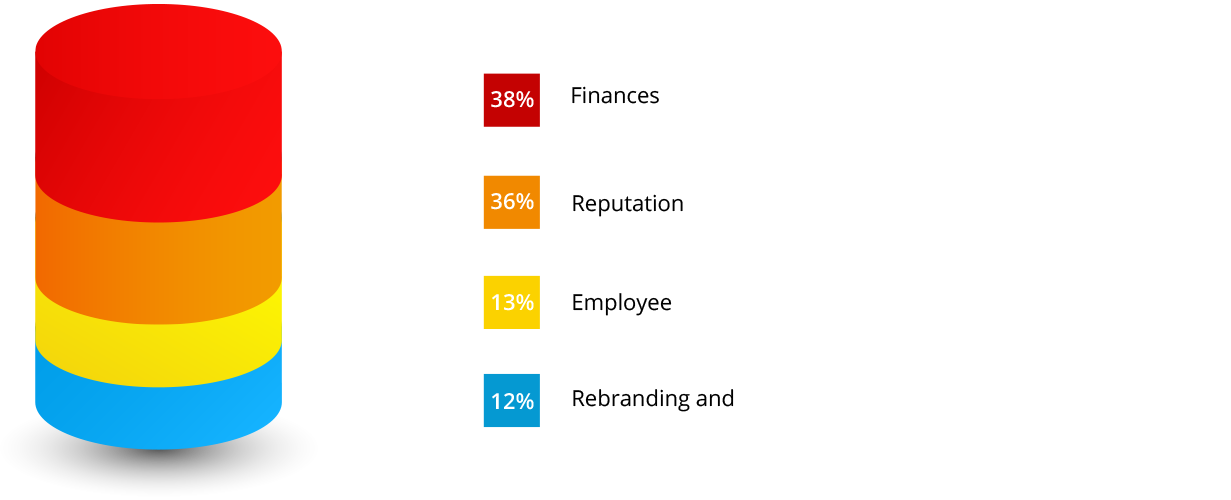
Attack methods vary based on the attacker and the security of the target network, businesses can be affected in different ways by cyberattacks; they could suffer productivity loss, financial loss, damage to brand name or reputation, and more.
Source of cyberattacks
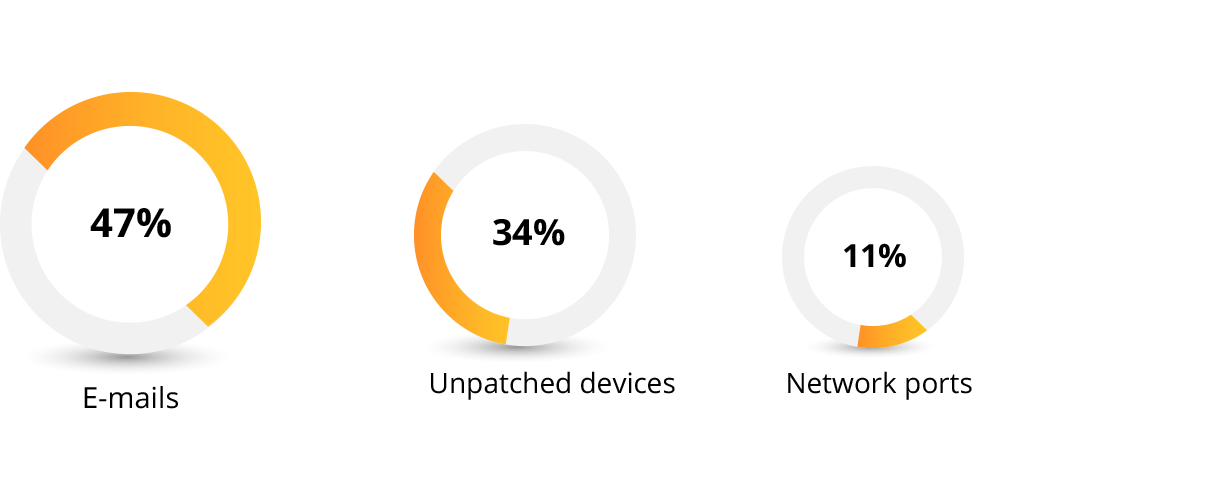
The scope and source of cyberattacks is quite vast due to widespread internet access and constantly evolving techinology. However, during our study, we were able to identify a few prominent areas where cyberattacks typically penetrate corporate networks. Emails are the top source of cyberattacks, followed by distributed devices.
Vulnerable devices in a corporate environment
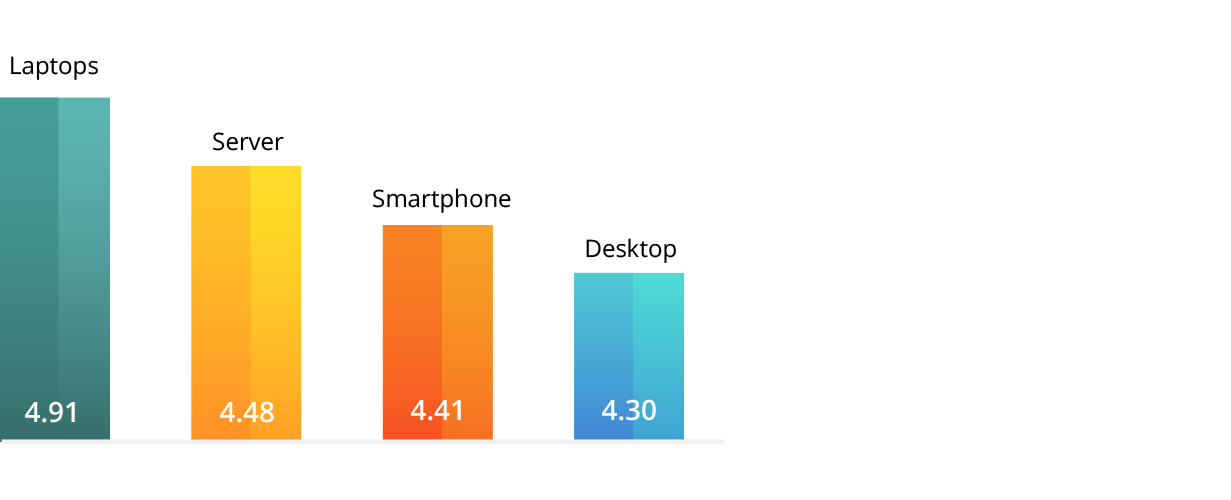
Organizations utilize many different types of devices, and securing all of them from external threats can be demanding, but cybersecurity professionals should focus on securing the most critical and the most vulnerable resources first. Based on our cybersecurity research, servers, smartphones and laptops are the most vulnerable devices in a business environment.
Frequent cyberattacks
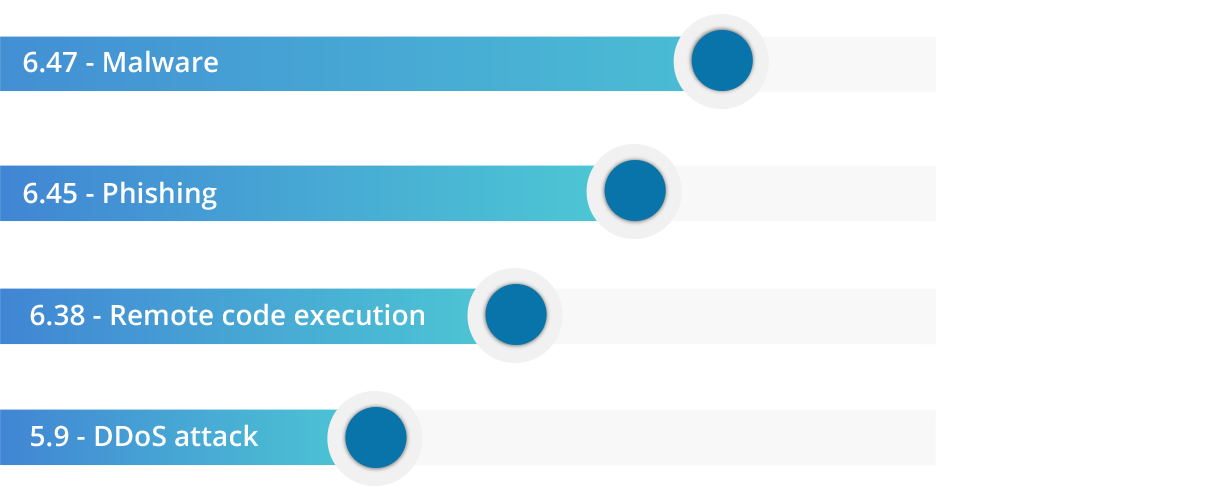
There are number of ways an organization's devices can be breached. Based on our study, malware and phishing are the most common cyberattacks occurring in the market. These types of attacks wreak havoc, affect productivity, and bring in unnecessary expenditure to a business.
Malware in a corporate environment
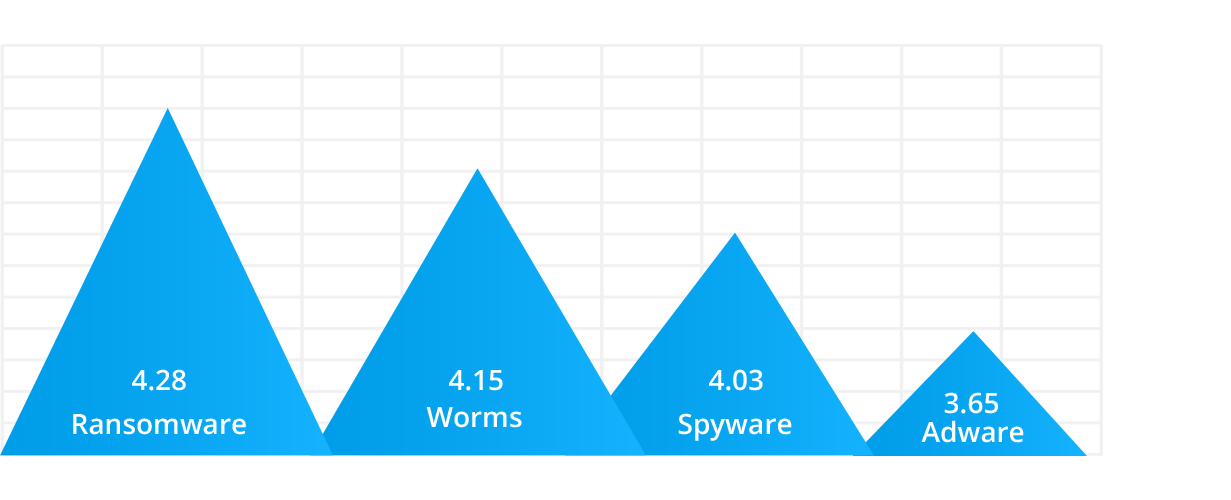
Since malware is a top concern for businesses in 2020, we wanted to identify the different types and their impacts on industries. We handpicked common types of malware like ransomware, trojans, worms, spyware, and adware to study their impact on businesses. Based on the results, we found that ransomware is the primary source of cyberattacks, followed by worms.
Ciritical security controls
Basic Security Controls
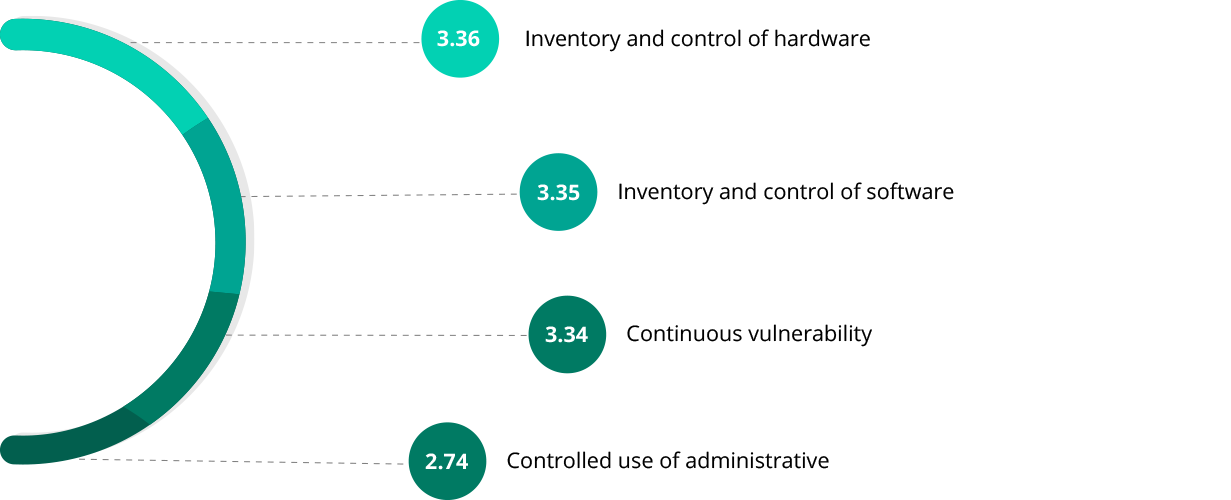
Businesses can overcome these cyber-challenges by establishing a few basic security controls for their business. To do that, they must understand their critical touch points and deploy the right controls to nullify cyberattacks. These security controls are based on the Center for Internet Security (CIS) framework, and, in our research, we identified inventory and control of hardware assets as the primary concern for a business, followed by inventory and control of software.
Foundational Security Controls
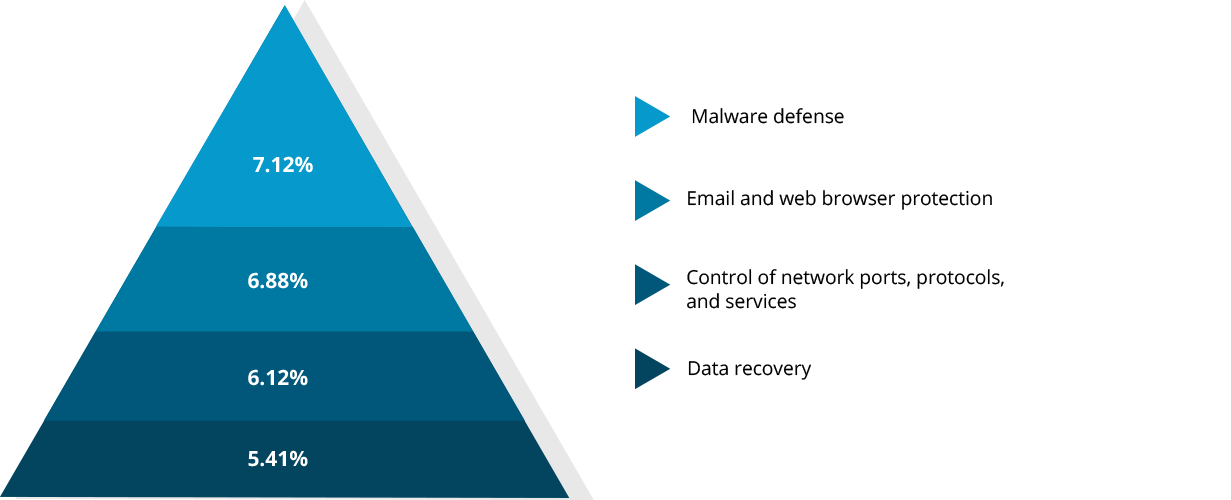
Understanding the importance of basic security controls, we also asked respondents about their current security needs. The results show that browser security is a priority for many businesses, as malware defense tops the list, followed by email and web browser protection.
Organizational Security Controls
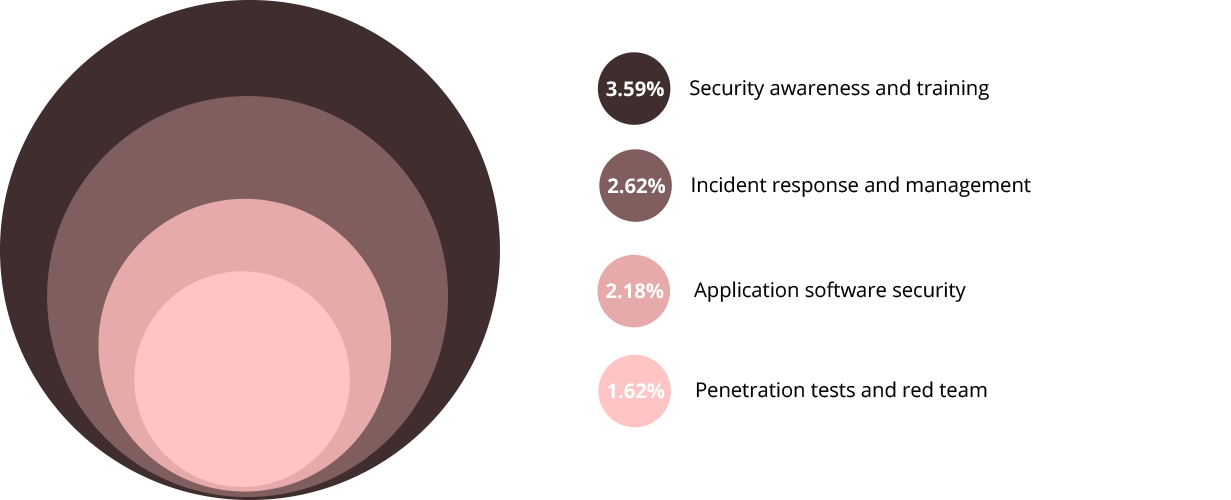
That being said, organizational security controls play a critical role compared to basic and foundational controls; these other two levels of cybersecurity strategies aren't successful unless your C-level executives contribute to them equally. Below are our findings on organizational security controls and their expectations in the market.
Responsible Individual
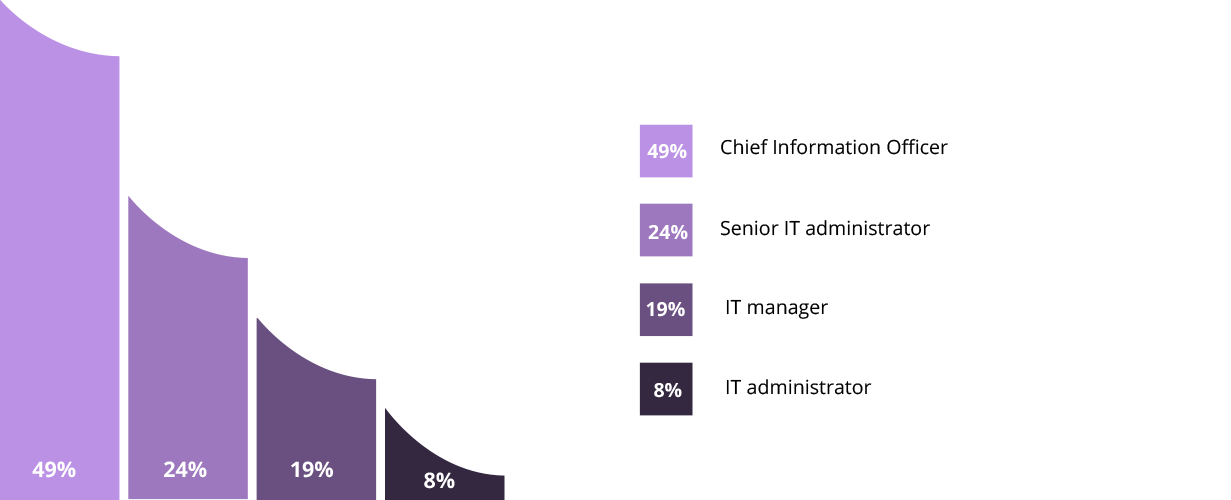
After understanding cybersecurity challenges and procedures, it's time for implementation, which can be a demanding task. Typically, the Chief Information Officer (CIO) will develop and implement a cybersecurity strategy, while the senior IT administrator will help facilitate it.
Strategy
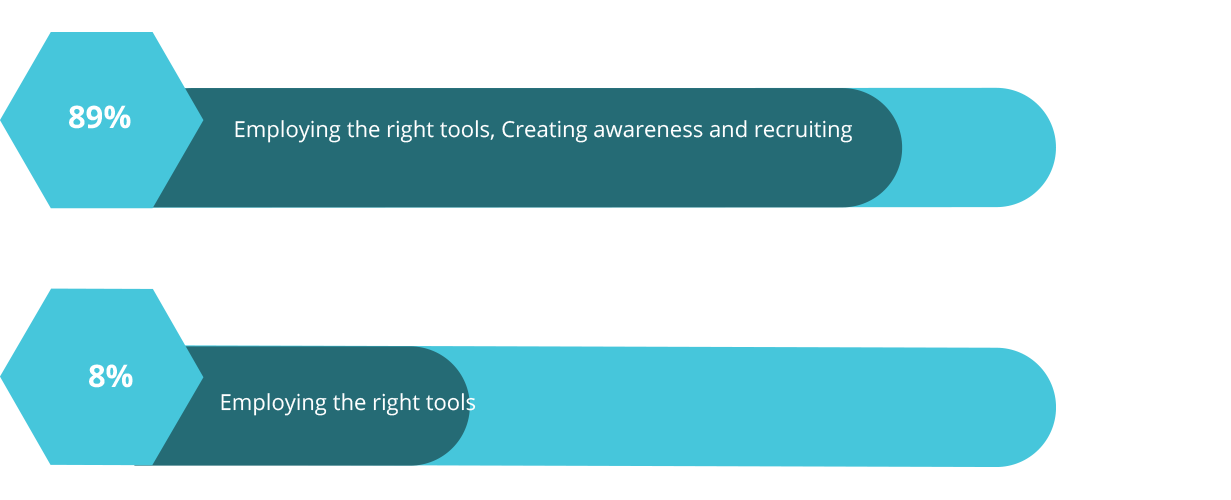
Once these security controls are ready to be implemented, the next step is to understand what factors to consider for improving the enterprise's overall security. According to our research, it's a cumulative decision that depends on employing the right tools, creating awareness, and recruiting skilled cybersecurity professionals.
Implementation
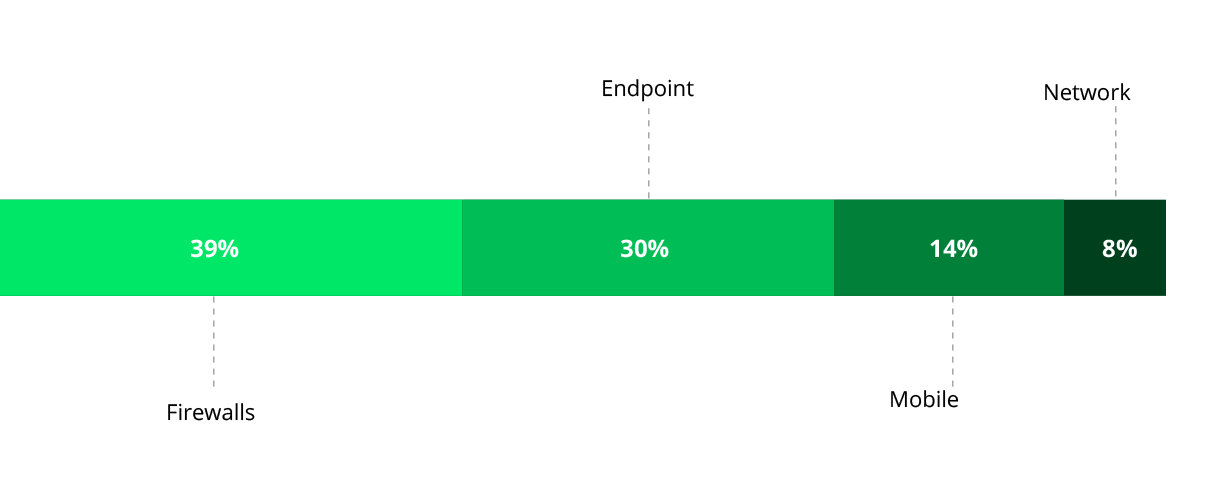
Corporate networks consist of servers, desktops, laptops, and mobile devices, all of which can fall victim to cyberattacks if targeted. Based on our study, we identified the best place to start implementing controls are firewalls, followed by endpoints.
Mobile Security
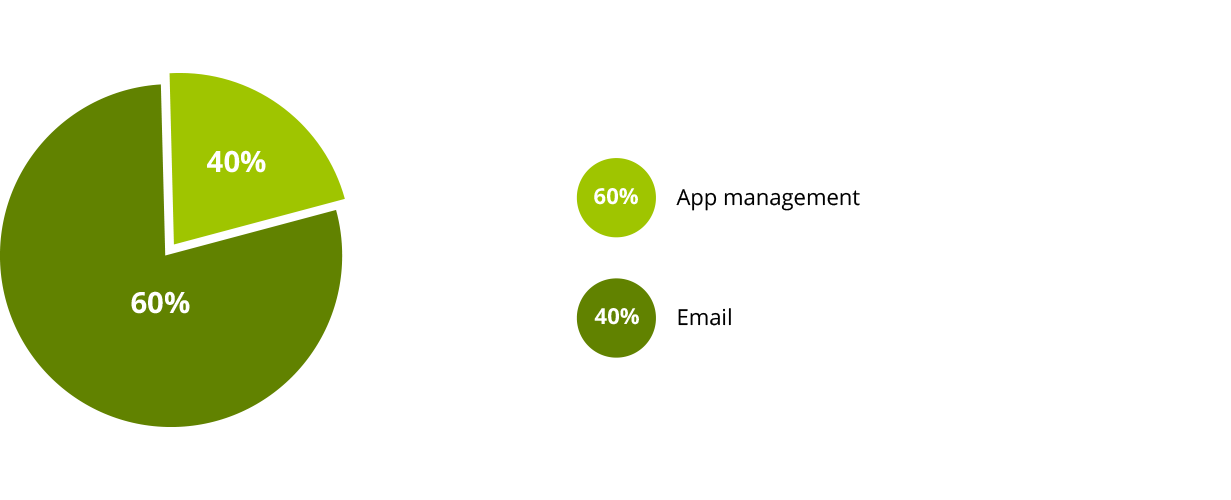
When it comes to mobile device security, the primary concern is email security management, followed by app management.
Server Security

Moreover, when it comes to server security management, virtual server management is a primary concern for cybersecurity.
Implementation
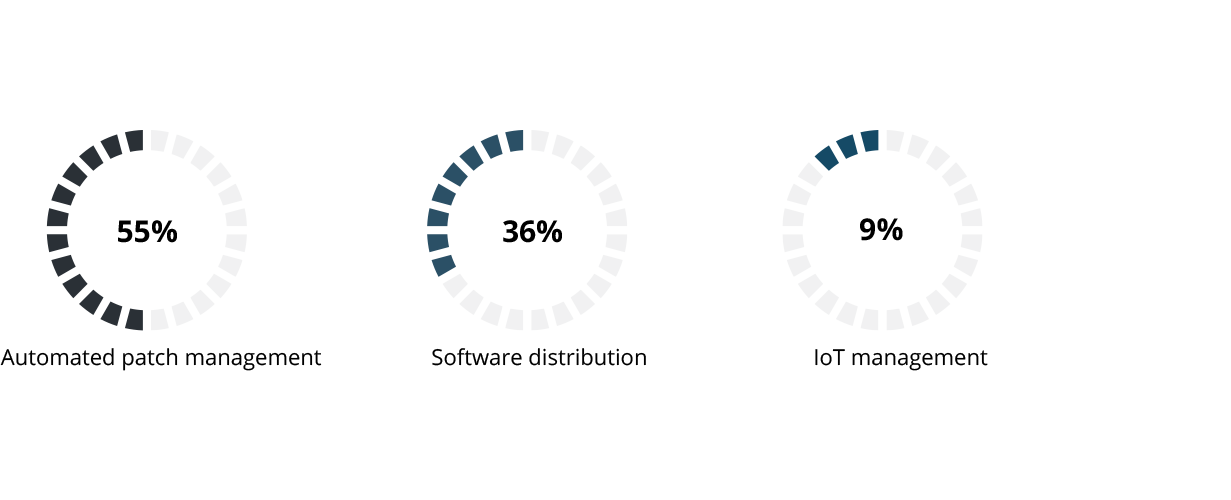
Unified endpoint management is another interesting field of research; almost all types of devices are included, but the primary concern for security professionals regarding endpoints is automated patch management, followed by software distribution, then Internet of things (IoT) management.
Cybersecurity
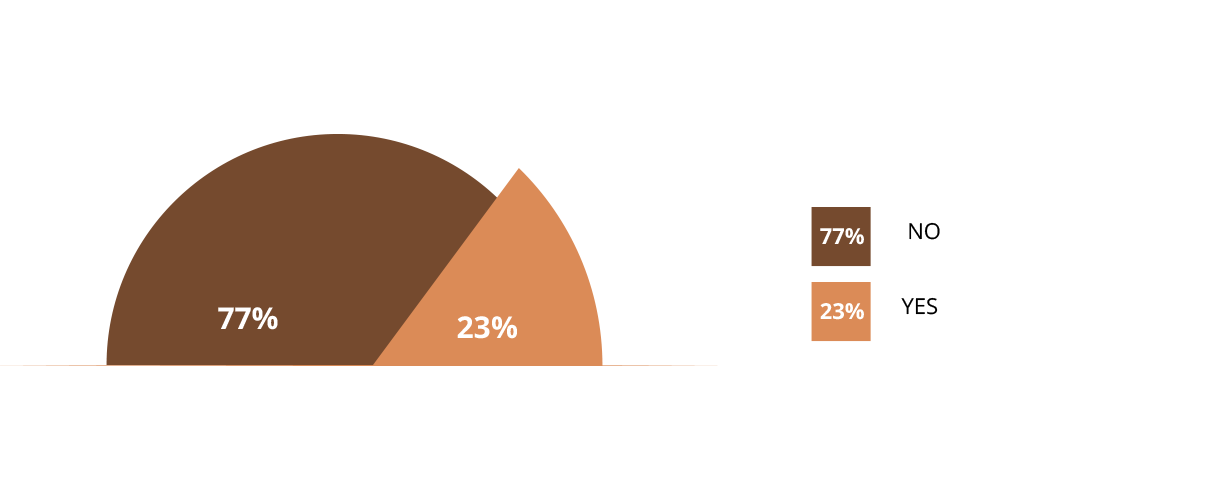
Above all else, the research and data we obtained showed that only 27 percent of businesses have the above mentioned critical security controls in place, and 73 percent of them have yet to deploy and implement them.
Only a few enterprises have employed critical security controls like ISO 27001 cybersecurity frameworks, developing massive open online courses (MOOC) on cybersecurity paradigms for mobile ecosystems, advanced threat prevention systems (ATP), security information and event management (SIEM), endpoint protection, identity access management (IAM), and vulnerability management.
Inference
The results of our study show that businesses are aware of critical touch points, procedures, and individuals responsible for reinforcing enterprise cybersecurity, but many enterprises are still a long way from implementing the right security controls for their corporate ecosystem.
Businesses can now combine several cybersecurity approaches dealing with servers, desktops, laptops, smartphones, tablets, IoT devices, and kiosk devices, along with the scopes for automated patch management, email security management, app management, and virtual server management into one optimal cybersecurity strategy: unified endpoint management (UEM).
Suggestion
ManageEngine offers a comprehensive UEM solution that's free to use for up to 50 endpoints, making it a good start for your business to reinforce cybersecurity. With ManageEngine's UEM solution, you can accomplish different IT management routines all from one single console.
With ManageEngine's UEM solution, you can take care of:
- Patch management
- Software deployment
- IT asset management
- Remote desktop management
- Mobile device management
- OS imaging and deployment
- Browser and firewall management
- USB security management
- Self-service portal management