Active Directory Federation Services (AD FS) is a capability developed by Microsoft that provides users with claims-based single sign-on (SSO), allowing them to log on to several applications across organizational boundaries.
SSO authentication lets users log in and gain access to all integrated systems and applications using a single set of credentials (ID and password). It works on a claims-based authentication model, which is a mechanism of identifying and authenticating a user by a set of claims that are related to their identity.
The identity provider here is the service that is responsible for storing and managing the digital identities of the user based on which it performs the functions of authentication and authorization. These claims are then bundled into tokens by the identity provider, which are further used to authenticate users across multiple applications.
AD FS is generally installed as a role in a domain controller running a Windows Server operating system.
Primarily AD FS plays two key essential roles:
SSO: AD FS lets users access applications or resources located in different networks or organizations using SSO.
Identity federation: Generally, when a user wants to access a resource or application in a different network, they are required to prove their identity again by providing some secondary credentials. These secondary credentials would be used to represent the user's identity in the network where the requested application or resource is present.
But with AD FS, users can avoid having to remember a second set of credentials. Organizations can build and use federation trust to authenticate the user and provide access to all the trusted partners who are part of the federation (a collection of domains that have established trust for shared access of resources and applications).
For instance, if an external user (a vendor or a partner) from organization A wants to access a resource in organization B, they can easily access it with a single authentication. The admins of organization B need not support any password management activities for such users nor are the external users required to remember new credentials.
The AD FS architecture is made up of following basic components:
User Account: Users utilize these to access resources or web applications. A user account is also known as a partner account in a federation.
Federation server: This server authenticates the user and generates a security token containing claims. A user's authentication request to any external site needs to go through the federation server. The AD FS server can be installed as a role in a Windows Server machine that is joined to the domain.
Target application: This is the web or cloud resource or application server that the user wants to access. It is also called a relying party and will have a federated trust relationship with AD FS to facilitate SSO through AD FS.
Let's consider a user, Harvey, from ABC Corp., who wants to access an application or resource in another network.
Harvey belongs to an account organization (network A), and the organization in which the target application or resource resides is the resource organization (network B).
Here's how Harvey will be authenticated using AD FS to access the application:
From his account organization, Harvey attempts to log in to a target application residing in the resource organization.
He is then redirected to the login page of the resource AD FS server. Here, he will enter his credentials (username and password).
The AD FS server will verify the credentials submitted by Harvey in Active Directory (AD).
If successful, AD will issue an authentication claim that is packaged inside security tokens. The claims are used to determine the unique identity of the user and decide if they can access the requested application or not.
Harvey will then be redirected to the login page of target application.
The target application will perform a claims check, and if it's accepted, Harvey can successfully log in and access the resource.
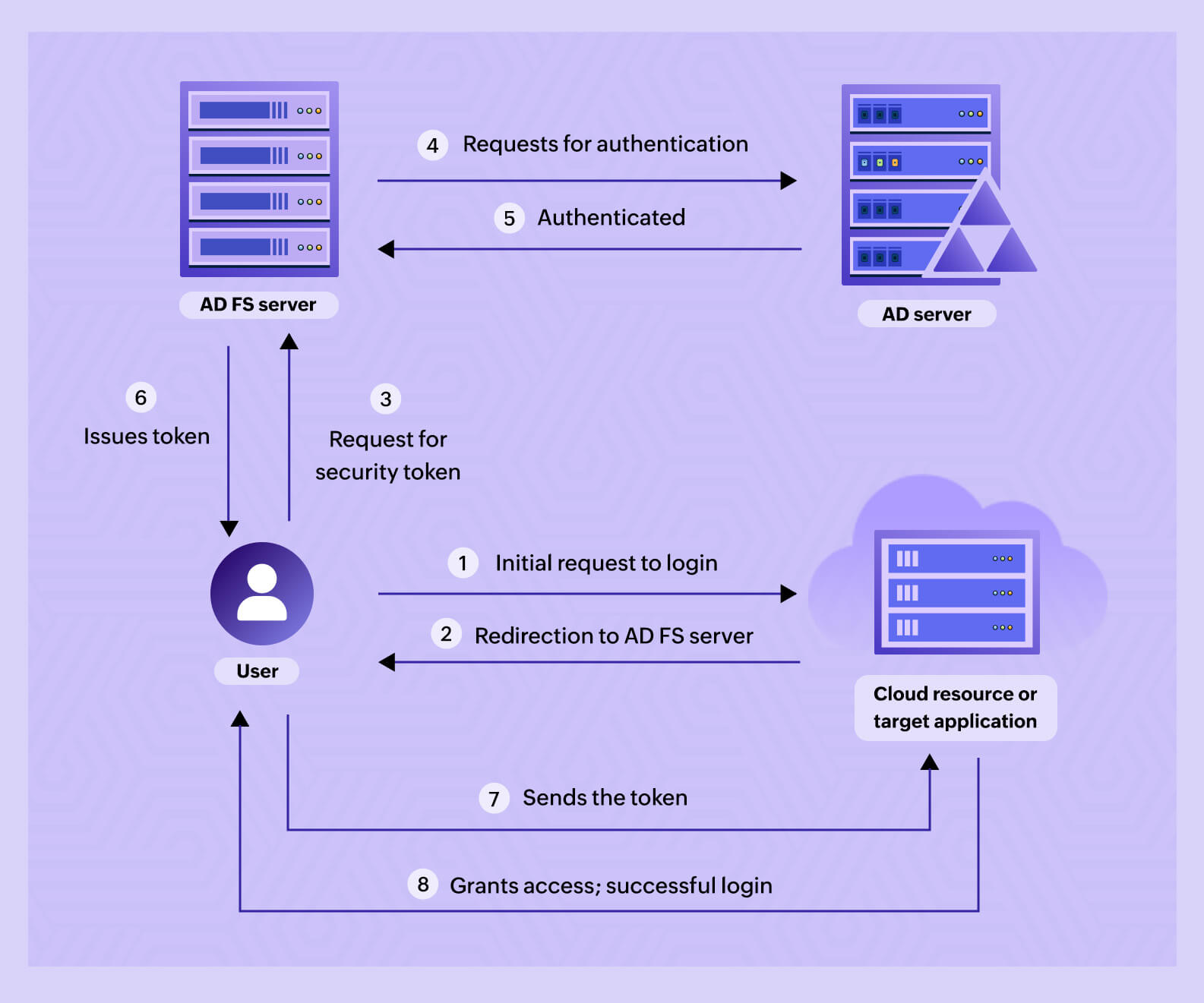 Figure 1. AD FS authentication process
Figure 1. AD FS authentication process
Here are few of the advantages AD FS has to offer to organizations and their users:
Simplified SSO for users: Users only have to remember one set of credentials to access various applications or resources. This ensures users do not experience password fatigue, which results from the excessive number of passwords users often have to maintain.
Improved security: Since access to multiple applications or resources is amalgamated into one single login, it reduces the attack surface exponentially, thus strengthening the cybersecurity posture of organizations.
Simplified account management: Adding or removing a user account can be managed easily within the network or across third-party applications.
Efficient credentials management: AD FS eliminates the requirement of storing and maintaining multiple user credentials in the database.
Hope this blog helped you in understanding the nuances of the AD FS authentication model. Stay tuned for future reads!
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.