Ransomware actors have recently exploited a nearly two-year-old vulnerability in the ESXi hypervisor developed by VMware to carry out a massive ransomware campaign dubbed ESXiArgs. They appear to be exploiting CVE-2021-21974, a heap-overflow vulnerability in the OpenSLP service run by ESXi. According to Italy’s National Cybersecurity Agency, while Europe has been hit the hardest, North America has also suffered greatly.
While France was the first to report the attack, Italy, Finland, the United States, and Canada soon joined the bandwagon. On Feb. 3, 2023, French cloud provider OVHcloud and the French Computer Emergency Response Team (CERT-FR) became aware of and investigated attacks against ESXi hypervisors, which are being targeted by threat actors for the express purpose of deploying ESXiArgs ransomware on them.
The attackers appear to be leveraging CVE-2021-21974 as this allows them to run exploit codes remotely. Though the patches for this vulnerability have been available since February 2021, this attack has demonstrated just how many servers have remained unpatched with the OpenSLP port 427 still exposed.
As the Austrian CERT has noted, Censys data indicates that at least 3,276 systems have been affected. The Austrian CERT also reported that CVE-2019-5544 and CVE-2020-3992 could be possible attack vectors. On Feb. 8, 2023, the US' Cybersecurity and Infrastructure Security Agency (CISA) and FBI released a joint advisory revealing that over 3,800 servers have been compromised globally. The advisory adds that the ransomware encrypts only the configuration files that are associated with the VM files and not the flat files. In some cases, these unencrypted flat files can help organizations reconstruct their encrypted VM files.
According to CERT-FR, the VMware ESXi versions that are vulnerable to the new ransomware variant, ESXiArgs, are:
CISA has reported that attackers are taking advantage of unpatched, out-of-service, or out-of-date versions of the ESXi hypervisors to deploy the Args ransomware.
The attack pattern, as identified by OVHcloud, is as follows:
An OpenSLP vulnerability, possibly CVE-2021-21974, and the user dcui (as depicted in the logs) have been identified as part of the compromise process.
The ransomware uses a public key deployed in /tmp/public.pem to encrypt data.
The encryption targets VM files with the extensions VMDK, VMX, VMXF, VMSD, VMSN, VSWP, VMSS, NVRAM, and VMEM.
To unlock the files, the malware then attempts to shut down VMs by killing the VMX process.
The ESXiArgs ransomware then creates args files (by adding the .args extension) that contain the metadata (the number of megabytes to skip, the number of megabytes in the encryption block, and the file size) for each encrypted VM file.
No evidence of exfiltration has been found before file encryption. In some cases, encryption seems to fail partially, which allows for data recovery.
Threat intelligence provider DarkFeed shared a copy of a ransom note in which the attackers demand 2.064921 bitcoins. But in each of the notes, the ransom and wallet address are different, as shown in Figure 1 and 2 below.
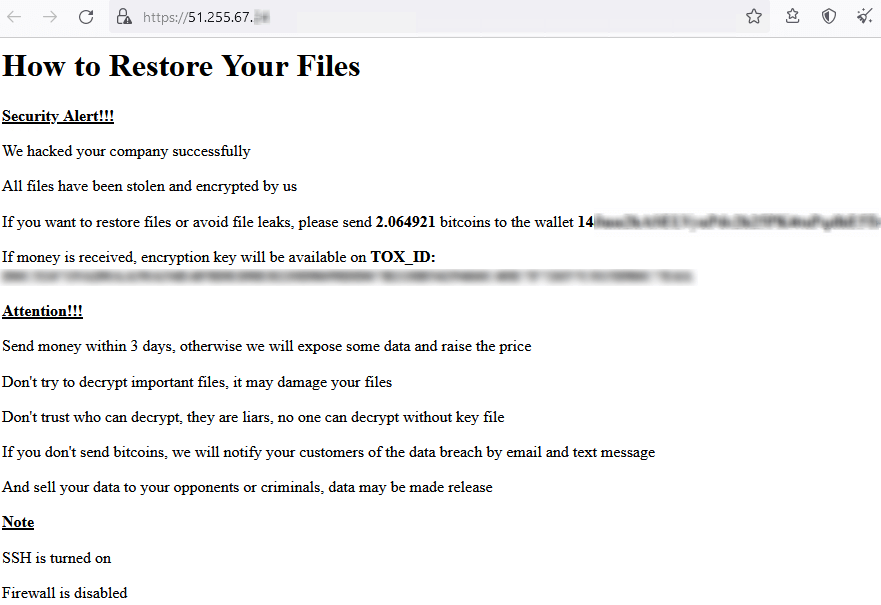 Figure 1. A ransom note demanding that 2.064921 bitcoins be sent to a wallet address..
Figure 1. A ransom note demanding that 2.064921 bitcoins be sent to a wallet address..
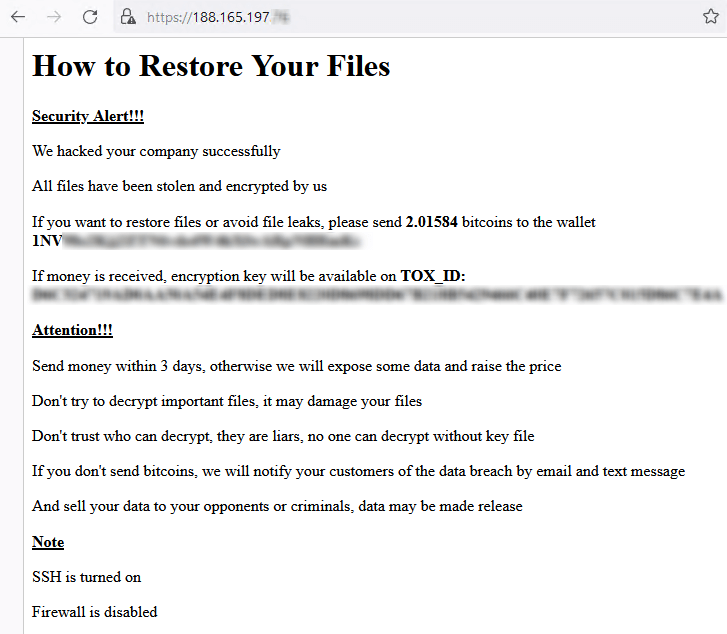 Figure 2. A ransom note demanding that 2.01584 bitcoins be sent to a different wallet address..
Figure 2. A ransom note demanding that 2.01584 bitcoins be sent to a different wallet address..
Julien Levrard, CISO of OVHcloud, recommends the recovery procedure for VMDK files documented by Turkish security researcher Enes Sönmez as many researchers have found the success rate for Sönmez's procedure to be good. Moreover, CISA has released a script to help organizations recover their encrypted files, which you can find here.
CERT-FR recommends the following measures after the ransomware infection:
Isolate the affected server.
As attackers may have already deposited the malcode, implementing the patches alone might be insufficient. Analyze your systems for any sign of compromise.
Reinstall your hypervisor, preferably ESXi versions 7.x or 8.x.
Apply all the necessary security patches and follow vendor security advisories to remain up to date.
Disable unnecessary services, such as the SLP service, on hypervisors.
Block access to administration services as required (either through a dedicated firewall or through the firewall integrated into the hypervisor) and implement a local administration network and a remote administration capability if required (via VPN or filtering trusted IP addresses).
CISA also recommends maintaining offline backups of your data, ensuring they're encrypted and immutable, and regularly testing your backup and restoration capabilities. CISA further advises organizations to have an incident response plan to combat ransomware attacks.
ManageEngine Log360 is a unified SIEM solution with integrated UEBA, SOAR, DLP, and CASB capabilities that can help you identify, detect, and mitigate various cyberattacks, including ransomware. With Log360, you can:
To learn more about how Log360 can help your organization defend against cyberattacks, sign up for a personalized demo.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.