On this page
The global identity threat detection and response (ITDR) market is projected to surge from USD 12.8 billion in 2024 to USD 68.92 billion by 2032, growing at a remarkable CAGR of 22.6%. This rapid growth reflects the increasing enterprise focus on combating identity-driven cyberattacks that target credentials, privileged accounts, and cloud identities. To keep pace, enterprises should start strengthening ITDR strategies with SIEM and IAM, ensuring faster detection, richer identity context, and automated response.
Why is identity the new targeted attack surface?
The following are the few reasons for identity to be the prime target:
- Credentials are the easiest entry point: Attackers can now log in using tokens, session cookies, or stolen passwords instead of having to "break in." Identity theft is frequently the easiest target due to the prevalence of credential leaks, phishing kits, and MFA fatigue assaults.
- Hybrid and cloud environments expand identity exposure: Enterprises now rely on AD, Azure AD, SaaS platforms, and cloud IAM systems. Each creates more identity silos, increasing the attack surface. A single compromised identity can provide access across multiple environments.
- Privileged accounts = High-value targets: Admin accounts, service accounts, and machine identities offer attackers a shortcut to lateral movement and privilege escalation, making them a favorite target for ransomware groups and APTs.
- Insider and supply chain risks: Employees, contractors, and third-party vendors all have identities within enterprise systems. Attackers exploit this expanded trust boundary, making identity compromise more damaging than endpoint compromise alone.
What are the challenges in identity security?
The following are the key challenges:
- Credential theft and abuse: Attackers increasingly exploit stolen passwords, tokens, and MFA fatigue attacks to gain unauthorized access.
- Excessive and orphaned privileges: Privilege creep and abandoned accounts create hidden entry points for attackers to move laterally.
- Hybrid and multi-cloud complexity: Enterprises struggle to monitor identities consistently across AD, Azure AD, SaaS, and cloud platforms.
- Insider threats and supply chain identities: Employees, contractors, and vendors with legitimate access can misuse it without immediate detection.
- Lack of real-time detection: Most organizations struggle to identify when compromised accounts are actively being misused, as existing tools often generate alerts without sufficient identity context.
- Machine and service identities: APIs, bots, and service accounts with long-lived credentials often go unmonitored, making them attractive targets.
- Regulatory and audit pressure: Enterprises face compliance challenges if they cannot prove who accessed what, when, and how.
- Advanced attack techniques: Techniques like Golden Ticket and Pass-the-Hash specifically exploit weaknesses in identity infrastructure.
What are the limitations in traditional enterprise defenses against identity?
- Perimeter-centric security models: Traditional defenses mainly focus on firewalls and network perimeters, but with cloud and remote work, attackers now target identities directly, bypassing these controls.
- Preventive-only access controls: Conventional identity management solutions enforce authentication and authorization but lack the ability to detect post-compromise misuse of legitimate credentials.
- Siloed identity systems: Identities are scattered across Active Directory, cloud platforms, SaaS apps, and third-party systems, making centralized monitoring and response difficult.
- Alert overload without context: Security monitoring tools often produce large volumes of alerts that lack identity-specific context, leaving SOC teams unable to distinguish real identity threats from noise.
- Blind spots in privileged and non-human accounts: Traditional defenses often overlook privileged accounts, service accounts, and machine identities, which attackers can exploit to gain elevated or persistent access.
- Limited insider threat detection: Employees, contractors, or partners with valid access can misuse identities without triggering conventional security controls.
- Inadequate response mechanisms: Even when threats are detected, most legacy defenses rely on manual intervention, slowing down containment of identity-driven attacks.
What are the core ITDR capabilities?
ITDR combines visibility, detection, analytics, response, and forensics to close the critical gap that traditional IAM and monitoring tools leave open. The following are the capabilities:
- Comprehensive identity visibility: Creates a unified inventory of all identities, including human, privileged, machine, and service accounts; across on-premises, cloud, and hybrid environments.
- Anomaly and behavior detection: Uses baselines of normal user and entity activity to detect unusual behaviors like impossible travel, privilege escalation, or suspicious access patterns.
- Threat correlation and analytics: Correlates identity signals with broader security events and maps them to frameworks like MITRE ATT&CK to identify sophisticated attack techniques.
- Automated and adaptive response: Enables real-time remediation such as enforcing step-up authentication, terminating sessions, or disabling compromised accounts to contain threats quickly.
- Forensic traceability: Maintains detailed identity activity trails, supporting investigations, incident reconstruction, and regulatory compliance audits.
- Privileged identity protection: Continuously monitors and safeguards privileged accounts and entitlements, reducing the risk of lateral movement or privilege abuse.
Which capabilities in a comprehensive security platform drive ITDR?
The following are the features that help in enhancing ITDR:
| Feature | How it helps | Benefit for ITDR |
|---|---|---|
| Identity-focused log correlation | Correlates login anomalies, privilege escalations, and directory changes with security events across endpoints, networks, and cloud apps. | Detects complex, multi-vector identity-driven attacks, like credential theft, that are followed by lateral movement. |
| UEBA-powered anomaly detection | Uses ML to baseline normal user/entity behavior and flags deviations, such as impossible travel or unusual access times. | Identifies compromised accounts early, even when attackers use valid credentials. |
| Privileged account activity monitoring | Tracks all privileged and service account activities, from group membership changes to sensitive file access. | Protects high-value accounts that attackers target for escalation. |
| Granular access governance | Enforces role-based and attribute-based access controls, ensuring users only have the permissions they need. | Reduces privilege creep and shrinks the attack surface for identity exploitation. |
| Just-in-time access provisioning | Grants time-bound, approval-based access for sensitive accounts instead of persistent privileges. | Limits attacker opportunities, even if credentials are stolen. |
| Adaptive MFA | Applies context-aware authentication based on login location, device, and user behavior. | Provides dynamic protection against credential theft and brute-force attempts. |
| Automated lifecycle management | Streamlines onboarding, role changes, and deprovisioning across on-premises and cloud apps. | Eliminates orphaned and dormant accounts that attackers commonly exploit. |
| Automated threat response | Executes remediation such as disabling compromised accounts, blocking malicious IPs, or triggering MFA. | Minimizes attacker dwell time and accelerates incident containment. |
| Threat hunting for identity attacks | Provides built-in queries to uncover advanced AD threats like Kerberoasting, golden ticket, and pass-the-hash. | Moves defense from reactive alert handling to proactive threat hunting. |
| Self-service with security controls | Enables secure self-service password resets and account unlocks with added authentication checks. | Reduces help desk dependency while preventing social engineering–driven compromises. |
How SIEM and IAM together powers ITDR?
The following is how SIEM and IAM (refer to Fig.1) work together in a chain to improve ITDR:
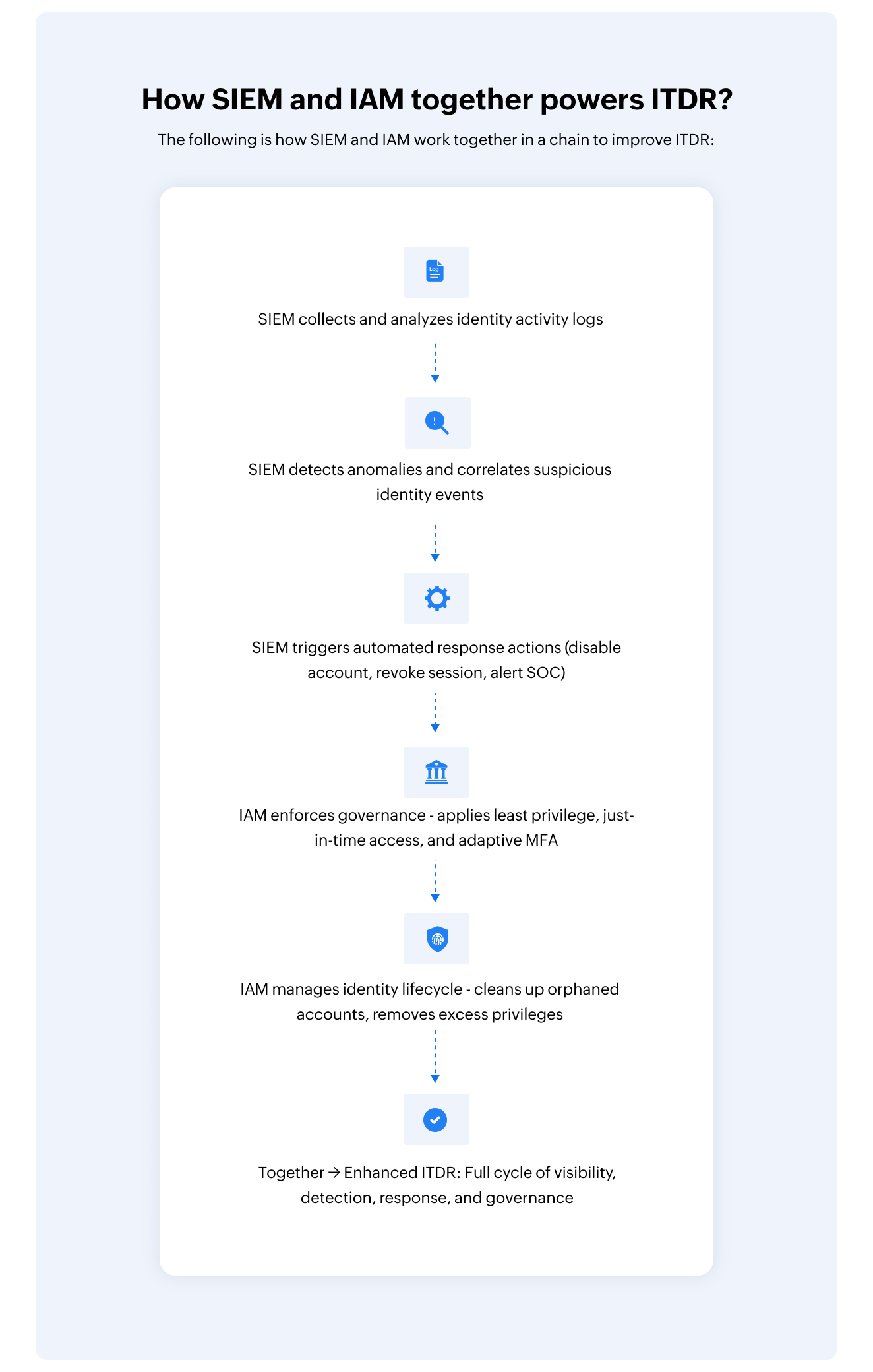
Figure 1: How SIEM and IAM enhance ITDR
What are the strategic benefits for CISOs integrating SIEM and IAM for ITDR?
The following are the benefits for CISOs:
- Unified identity risk posture: CISOs gain a holistic view of all identity risks across cloud, on-premises, and hybrid environments by combining SIEM's real-time detection with IAM's governance and control.
- Faster threat containment: When SIEM detects anomalous activity and IAM enforces adaptive controls instantly, enterprises reduce dwell time and limit blast radius of identity-based attacks.
- Regulatory and audit readiness: Integrating SIEM and IAM provides provides forensic traceability of identity events, access approvals, and incident responses; simplifying compliance with SOX, GDPR, HIPAA, PCI DSS and more.
- Reduced business disruption: Automated detection (SIEM) plus proactive access governance (IAM) prevents attackers from misusing accounts, helping maintain service continuity and protect customer trust.
- Optimized security investments: Instead of siloed tools, an integrated approach maximizes ROI by leveraging existing investments while aligning identity security with enterprise risk management.
- Board-level assurance: CISOs can confidently report to the board that the enterprise has identity-centric detection, protection, and compliance built into its defenses strengthening trust in security strategy.
Which metrics should CISOs track when aligning SIEM and IAM with ITDR?
Uncover the critical metrics CISOs need to track when integrating SIEM and IAM with ITDR strategies.
What are the best practices to enhance ITDR with a security solution?
Here are the best practices to be followed:
- Integrate IAM logs into SIEM for unified identity and threat visibility.
- Monitor privileged accounts closely and enforce least-privilege access.
- Automate responses by linking SIEM alerts with IAM workflows.
- Implement risk-based MFA and track suspicious MFA bypass attempts.
- Detect and remove dormant or orphaned accounts continuously.
- Conduct proactive threat hunting with identity context for faster investigations.
- Use IAM and SIEM reporting together to meet compliance and audit needs.
Conclusion
Today, CISOs face an environment where identities are the new attack surface, making ITDR a strategic priority rather than an optional layer of defense. Traditional tools alone cannot keep up with the sophistication of identity-based threats, leaving critical blind spots. By combining SIEM’s deep visibility and advanced detection with IAM’s strong access enforcement, enterprises gain a holistic ITDR framework that ensures threats are identified, contained, and remediated in real time. This unified approach not only strengthens security posture but also enables CISOs to confidently protect business-critical systems and data.
Related solutions
ManageEngine Log360 is a SIEM solution that combines DLP, CASB, machine learning, and MITRE ATT&CK® mapping to deliver real-time threat detection, automated response, streamlined incident management, and compliance across hybrid IT environments.
Sign up for a personalized demoManageEngine AD360 is a unified IAM solution that simplifies identity, access, and security management across on-premises and cloud platforms with features like user provisioning, SSO, self-service password management, and auditing.
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
