What are anomalies?
Anomalies, also known as outliers, are rare or unexpected data points that differ significantly from the majority of observations. In cybersecurity, anomalies often signal malicious behavior such as insider threats, lateral movement, or unauthorized access. Detecting anomalies early is essential for preventing data breaches and enhancing network security.
Anomaly detection meaning
Anomaly detection, meaning the identification of abnormal events or behavior in a dataset, is a cornerstone of modern threat detection systems. Whether in time series data, logs, or user activity, anomaly detection software flags deviations that might indicate a security anomaly or system failure. Unlike rule-based systems, anomaly detection algorithms can uncover unknown threats and zero-day attacks.
Types of anomalies
Understanding the types of anomalies is vital for designing effective anomaly detection techniques. These include:
- Point anomalies: Single data points that are significantly different from the rest. Example: A sudden spike in login failures.
- Contextual anomalies: Data points that are anomalous in a specific context. Example: High network traffic at midnight.
- Collective anomalies: A sequence of data points that, together, deviate from expected behavior. Example: A sequence of logins from different countries in a short span.
These types guide the implementation of different anomaly detection methods and improve the accuracy of detecting threats in dynamic environments.
Anomaly detection algorithms
Anomaly detection algorithms form the computational backbone of any modern security anomaly detection system. These algorithms help identify deviations from normal patterns in user behavior, system logs, network traffic, and access events, enabling early detection of threats that evade traditional signature-based tools.
Key anomaly detection algorithms used in cybersecurity include:
- Isolation forest: Highly effective in identifying outliers in large datasets, this algorithm isolates anomalies based on how easily they can be separated from the rest of the data. It’s commonly used for detecting rare attack patterns such as privilege misuse or unusual file access.
- One-class support vector machine (SVM): Ideal for high-dimensional data like logs and user activity records, one-class SVM creates a boundary around normal data and flags deviations as anomalies, which is useful for spotting unknown attack vectors or credential misuse.
- Autoencoders: These are deep-learning-based models trained to reconstruct input data. In cybersecurity, they’re used to model normal log sequences or network traffic. When reconstruction errors spike, it indicates potential anomalies such as unauthorized actions or system compromise.
- k-means clustering: This unsupervised algorithm groups similar data points and highlights outliers, making it useful for grouping typical user actions and detecting anomalous behavior like brute-force attacks or internal reconnaissance.
- Density-based spatial clustering of applications with noise (DBSCAN): DBSCAN identifies dense clusters and flags points in sparse regions as anomalies. In SIEM environments, this can highlight rare logon behaviors or low-frequency communication attempts from dormant malware.
- Principal component analysis (PCA): Often used to reduce the dimensionality of log or telemetry data, PCA-based anomaly detection helps identify unexpected variance in system behavior or application usage.
Machine learning in anomaly detection
Machine learning (ML) in anomaly detection empowers cybersecurity teams to identify threats that don't match known attack signatures. Traditional detection methods struggle with novel threats and noisy environments. ML-based anomaly detection software adapts to evolving patterns and reduces false positives by learning what "normal" means in your unique environment.
There are three primary types of ML used for anomaly detection in cybersecurity:
- Supervised learning: Requires labeled data for both normal and anomalous behavior. In cybersecurity, this is useful for training models on known attacks (e.g., phishing or ransomware activity). However, its applicability is limited by the availability of quality labeled data.
- Unsupervised learning: Most common in security anomaly detection, unsupervised models like clustering and autoencoders learn normal behavior patterns without needing labeled anomalies. These models are ideal for environments like SIEM platforms, where most data is unlabeled and attackers constantly evolve their tactics.
- Semi-supervised learning: Trains on abundant "normal" data and flags deviations without requiring labeled attack data. This approach is effective in UEBA systems, where understanding baseline user behavior is key to detecting insider threats or compromised accounts.
Common cybersecurity applications of ML-based anomaly detection include:
- UEBA: ML models analyze time series data, log sequences, and access patterns to detect anomalies such as impossible travel, credential misuse, and data hoarding.
- Network anomaly detection: ML identifies abnormal protocol usage, data exfiltration attempts, and command-and-control traffic, even when encrypted or obfuscated.
- Endpoint security: Behavior-based models detect anomalous process execution, file modifications, and registry changes indicative of malware activity.
- SIEM correlation and alerting: ML augments rule-based correlation by flagging rare or emerging attack patterns across logs, events, and telemetry data.
Anomaly detection in cybersecurity
As discussed, anomaly detection involves identifying deviations in user activity, network behavior, or system events that indicate potential threats.
Types of anomalies may include:
- Unusual login patterns: A user logging in at an odd time (e.g., 3am), from a foreign IP address, or from multiple geographic locations within a short time frame are all strong indicators of credential compromise.
- Privilege escalation: A standard user suddenly executing commands or accessing resources reserved for administrators can be flagged as an anomaly based on behavioral baselining.
- Lateral movement: When an account or process accesses systems that it typically never interacts with, such behavior is considered a network anomaly. Detecting lateral movement is a key use case for network anomaly detection.
- Data exfiltration behavior: A sudden surge in outbound traffic, especially involving sensitive data or unrecognized destinations, is a classic data anomaly detection scenario.
- Unusual process behavior: Processes spawning unexpectedly, executing from non-standard directories, or making unauthorized registry changes can be flagged by endpoint anomaly detection systems.
- Application misuse: Users performing actions outside their normal application usage pattern—like downloading reports in bulk or exporting dashboards—can signal insider threats.
- Unexpected service activity: New ports being opened, services restarting frequently, or protocols being used in unexpected ways are all examples of network behavior anomaly detection.
- Time-based anomalies: Time series anomaly detection is useful for spotting deviations in metrics like CPU usage, memory spikes, authentication attempts, or failed logins over a period of time.
Anomaly detection use cases
To understand anomaly detection in cybersecurity better, it helps to look at practical scenarios where security anomalies signal real threats. These examples show how anomaly detection algorithms, ML, and anomaly detection techniques work together to identify unusual activity that may bypass traditional detection tools.
1. Unusual login location (impossible travel detection)
- Scenario: A user logs in from New York at 9am EST and then from Singapore at 9:15am EST. The organization uses SSO and geo-based access controls.
- Detection: A time series anomaly detection algorithm backed by user behavior baselining flags this as an impossible travel event. It detects that such geographic switching within a short time span is statistically implausible.
- Significance: This security anomaly may point to stolen credentials being used from a different region or a session hijack attempt, both common in phishing-based compromises.
2. Massive outbound traffic at odd hours
- Scenario: A desktop endpoint that usually transmits a few megabytes per hour during work hours suddenly uploads 3.5GB of encrypted data to an unknown IP address at 2:45am.
- Detection: A data anomaly detection technique, paired with an outlier detection algorithm like isolation forest, flags this as a volume spike and unusual time-of-day activity.
- Significance: This could be a case of data exfiltration by a compromised system, a botnet, or an insider threat. It’s a classic use case for anomaly detection software in detecting stealthy breaches.
3. Dormant account suddenly active across multiple systems
- Scenario: A rarely used admin account, inactive for over 90 days, is suddenly used to authenticate into domain controllers, a VPN, and cloud consoles, all within 10 minutes.
- Detection: Anomaly detection techniques involving UEBA identify this burst of activity as abnormal for that account and privilege level.
- Significance: This is often indicative of a credential compromise. The attack could be an insider threat or external actor exploiting a forgotten high-privilege account.
4. Device profile mismatch on access attempt
- Scenario: A user account that typically logs in from a corporate-issued Windows 11 machine attempts to access the network using an Android device over an unrecognized IP.
- Detection: Anomaly detection algorithms powered by ML analyze device fingerprinting, session metadata, and access history to flag the mismatch.
- Significance: This behavior deviates from the user’s known profile and may represent session hijacking, mobile malware, or a rogue device breach attempt.
ManageEngine Log360: A unified security platform for modern SOCs
Log360 is an enterprise-grade SIEM designed for modern security teams. It helps SOCs scale their operations and detect threats faster. The platform brings log management, real-time security analytics, and behavior-based anomaly detection together in one place. Security data from cloud and on-premise environments can be monitored in real time.
Log360's architecture is built for both depth and performance. It uses distributed event processing, enriched context modeling, and an advanced alert pipeline to ensure accurate detection without slowing operations. All detection rules and IOCs are continuously updated from the cloud, so your SOC is always prepared for the latest threats.
Capabilities that set Log360 apart
1) Anomaly detection library
Advanced behavioral analytics and contextual correlation highlight subtle deviations that indicate early-stage compromise. Examples include:
- Windows and AD anomalies: excessive update attempts, registry tampering, high-volume file edits, unauthorized Group Policy changes, and DSRM password resets.
- Microsoft 365 anomalies: password reset bypasses, unusual login failures, suspicious mailbox activity, excessive file deletions, and off-hours policy changes.
- Database & server anomalies: SQL Server suspicious password changes, IIS FTP privileged execution attempts.
- Firewall anomalies: off-hour or unauthorized policy modifications across Fortinet, Netscreen, WatchGuard, SonicWall, and Sophos.
- Cloud/SaaS anomalies: Salesforce abnormal data transfers, unauthorized connector activity, admin setting modifications.
- Unix anomalies: irregular password activity, anomalous privileged command execution.
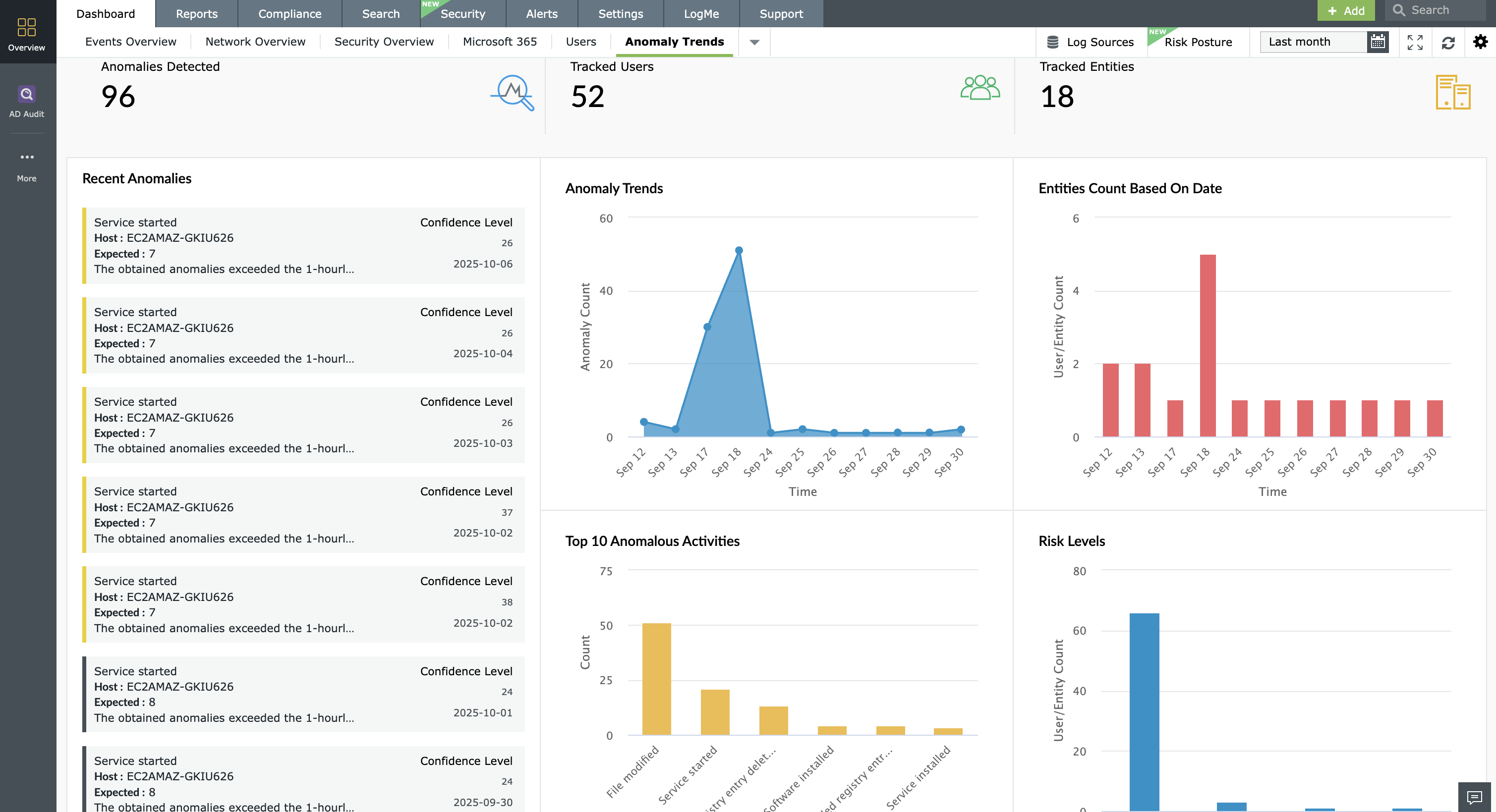
2) Next-gen threat detection:
- Rule optimization with object level filtering: Rules operate at a granular object level (users, applications, endpoints), filtering alert criteria by context, significantly cutting false positives and focusing analyst time on the high risk events.

- Cloud-delivered detection library: Log360 provides instant coverage with a cloud-curated repository of 2,000+ detections, spanning correlation rules, anomaly models, and threat intelligence matches. All detections are mapped to the MITRE ATT&CK® framework, giving SOC teams visibility into defensive posture against real-world adversary tactics. The library enables multi-layered defense by:
- Correlation rules - detect known attack patterns by linking activity across endpoints, servers, SaaS, and cloud environments.
- Anomaly rules - baseline normal behavior and surface insider threats, compromised accounts, or policy abuses.
- Threat intelligence matches - enrich detections with real-time feeds (Webroot, STIX/TAXII), flagging connections to known malicious IPs, domains, and URLs.
New rules are continuously released to cover emerging TTPs, ensuring resilience against evolving threats.
3) Behavioral analysis with UEBA
Log360 includes a dedicated UEBA module. This feature uses ML algorithms to establish a behavioral baseline for every user and entity (e.g., endpoints, servers, and applications) in the network.
- Risk scoring: Each user and entity is assigned a dynamic risk score based on the severity and frequency of their activities.
- Dynamic grouping: Users and entities are automatically grouped based on similar behaviors, making it easier to spot anomalies in context.
- Contextual alerts: When activity significantly deviates from the norm, the system triggers alerts, flagging them as low, medium, or high-risk incidents.
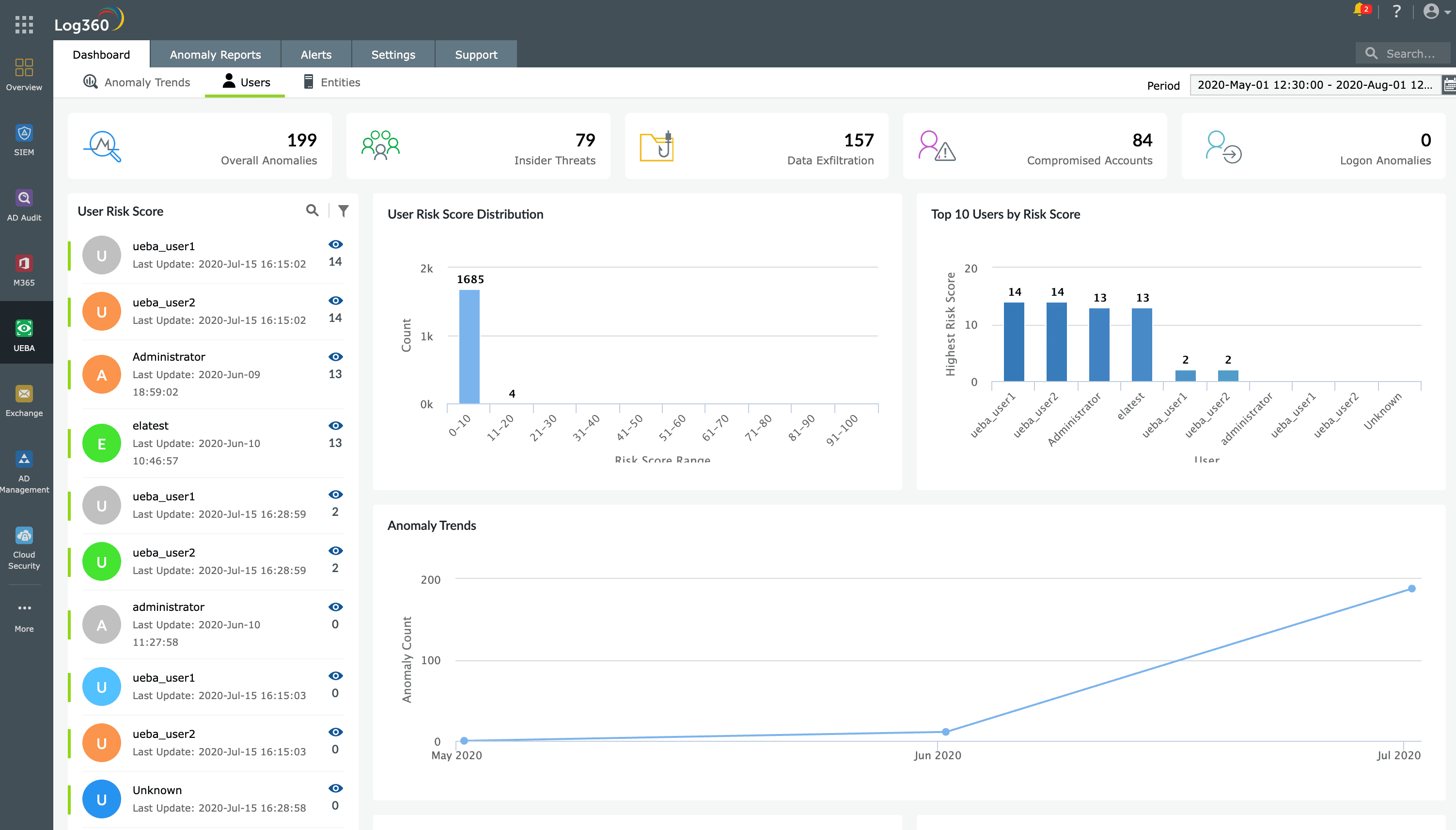
The solution provides smart thresholds that leverage contextual information and real-time data to continuously reassess and readjust their values. Unlike static thresholds, which are fixed values set based on predefined standards, smart thresholds have the capability to adjust dynamically in response to changes in the IT environment.
Who is Log360 for?
Log360 is built for organizations with complex, hybrid environments seeking to centralize security, threat detection, and streamline compliance. It is ideal for:
- SOC teams needing contextual, low-noise threat visibility with minimal manual tuning.
- Enterprises with heterogeneous IT stacks
- Regulated industries required to generate audit quality reports
- Managed Security Service Providers (MSSPs) delivering multi tenant SOC services at scale
Existing content (Excepting the product pitching section)
What's next?
Learn how you can implement anomaly detection in your organization's network with Log360's capabilities
- What are anomalies?
- Anomaly detection meaning
- Types of anomalies
- Anomaly detection algorithms
- Machine learning in anomaly detection
- Anomaly detection in cybersecurity
- Anomaly detection use cases
- ManageEngine Log360: A unified security platform for modern SOCs
- Who is Log360 for?