What is OSINT?
Open-source intelligence (OSINT) refers to the collection and analysis of data from publicly available sources to produce actionable intelligence. This intelligence is utilized in various fields such as national security, law enforcement, and business intelligence. OSINT distinguishes itself from traditional research by applying a structured intelligence process to create tailored knowledge that supports specific decisions.
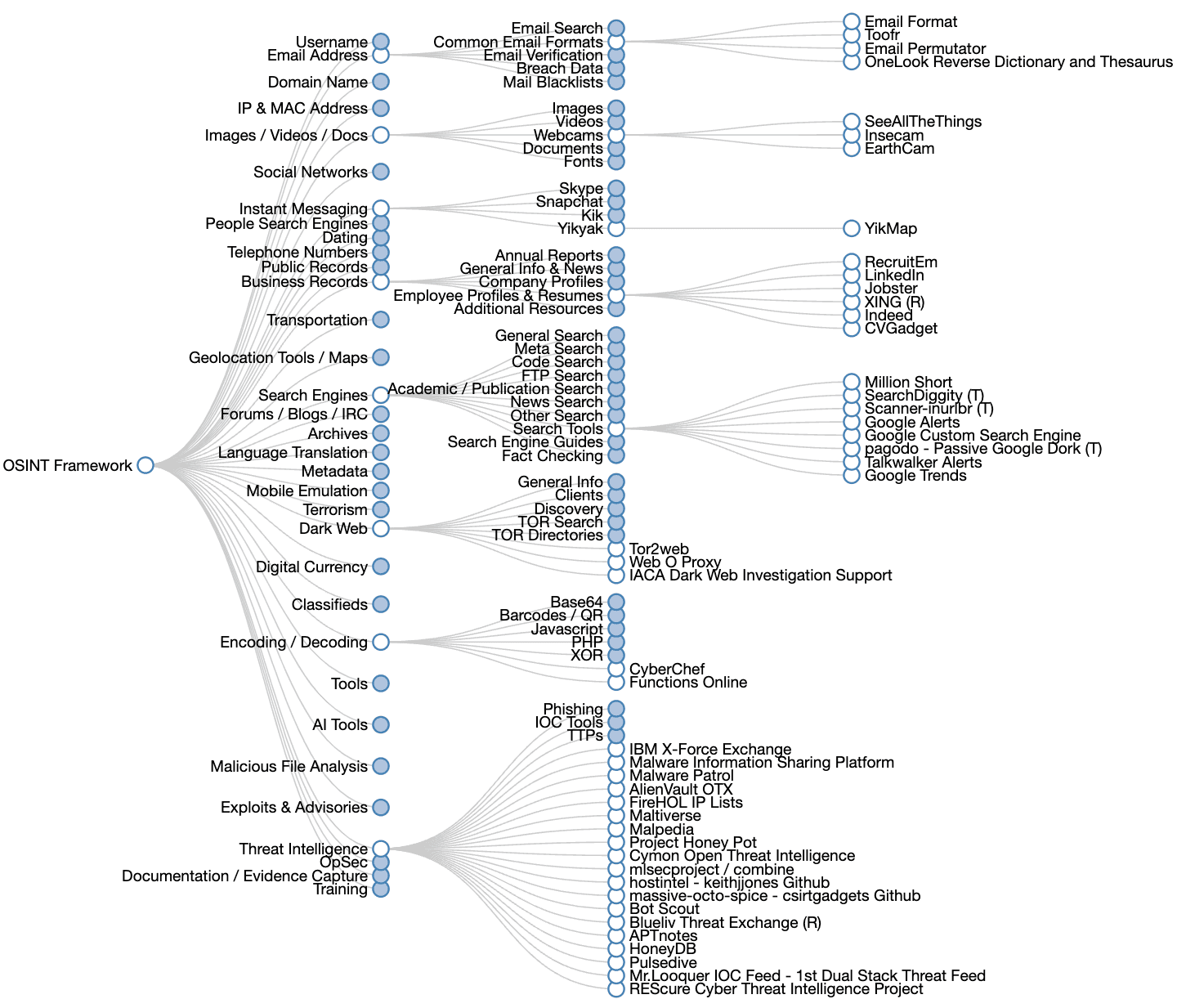
What is OSINT framework?
The primary function of the OSINT framework is to compile and categorize publicly available information, allowing users to navigate through different categories related to their specific intelligence needs. This framework simplifies the process of gathering data by offering direct access to various tools that can be employed for different types of investigations, such as:
- Username searches: Tools for finding information related to specific usernames.
- Email address investigations: Resources for gathering data linked to email addresses.
- Domain name analysis: Tools for examining domain registrations and associated information.
The OSINT Framework enhances intelligence gathering efficiency by organizing these tools into categories based on source, relevance, type, and context.
Types of OSINT
OSINT can be categorized based on the sources of information and the methods used for collection. Here are the primary types:
- Internet sources: This includes social media platforms, forums, blogs, video-sharing sites, search engines, and metadata from digital files. Information from the dark web is also included.
- Traditional media: Newspapers, television, radio broadcasts, magazines, and academic publications. These sources provide valuable insights into public sentiment, trends, and events.
- Grey literature: This encompasses non-commercial publications such as reports from NGOs (non-governmental organization), government documents, academic research papers, and other materials that are not easily accessible through traditional publishing channels.
- Public records: Data from government databases, court records, business registrations, and other official documents can be analyzed for various intelligence purposes.
- Geolocation data: Using information from GPS data or location-based services to gather insights about specific areas or individuals.
Methods of OSINT collection
OSINT collection methods can be classified into three main categories:
- Passive collection: This involves gathering information without actively engaging with the source. For example, monitoring social media profiles or reading news articles without direct interaction.
- Semi-passive collection: This method may involve some level of engagement with the source but does not directly reveal the collector's intent. For instance, subscribing to newsletters or following certain online forums.
- Active collection: This entails direct interaction with the source or target to obtain specific information. Examples include conducting interviews or participating in discussions where information can be gathered.
Who can use OSINT?
OSINT is utilized by a diverse range of users across various sectors. Here are some key groups that leverage OSINT:
- Government agencies: Intelligence agencies and law enforcement use OSINT to gather information on national security threats, criminal activities, and foreign governments.
- Military organizations: The military employs OSINT for strategic planning and situational awareness in operations.
- Journalists and investigative reporters: Journalists use OSINT to uncover stories, verify facts, and gather background information on subjects they are reporting on.
- Businesses: Companies use OSINT for competitive analysis, market research, and understanding consumer behavior. It helps them identify trends and make informed decisions.
- Cybersecurity professionals: Security analysts and penetration testers use OSINT to identify vulnerabilities in systems and gather intelligence on potential threats or attackers.
- Private investigators: They often rely on OSINT to gather information about individuals or entities for legal cases or personal investigations.
- Human rights organizations: These groups utilize OSINT to document abuses and gather evidence in conflict zones or oppressive regimes.
- Academic researchers: Scholars use OSINT to collect data for studies across various disciplines, including sociology, political science, and environmental studies.
- Individuals concerned about privacy: People may use OSINT techniques to assess their own digital footprint or understand how much of their personal information is publicly accessible.
The dark side of open-source intelligence
OSINT is increasingly utilized by criminals to gather information for malicious purposes, posing significant risks to organizations. Here are some of the known risks associated with bad actors leveraging OSINT:
Target profiling: Criminals leverage OSINT to conduct extensive research on potential victims, including individuals and organizations. They can gather personal details, such as names, addresses, and social media activity, which helps in crafting personalized phishing attacks or social engineering schemes.
Data breach exploitation: Attackers often use OSINT to find leaked credentials from previous data breaches. They execute credential stuffing attacks by cross-referencing usernames and emails with compromised databases and gain unauthorized access to accounts.
Dark web engagement: Criminals exploit OSINT tools to navigate the dark web, where they can buy and sell stolen data, share hacking techniques, or communicate with other criminals. This environment provides a lot of information that can be used to plan and execute cybercrime.
Identity theft and fraud: By gathering personal information from various public sources, criminals can impersonate individuals or organizations. This can lead to identity theft, financial fraud, or unauthorized access to sensitive systems.
How ManageEngine Log360 and open-source threat feeds work in tandem to create proactive cybersecurity strategy for your organization
ManageEngine Log360 is a comprehensive security information and event management (SIEM) solution designed to enhance network security and streamline log management processes for organizations of all sizes.
Open-source threat feeds provide a wealth of information about emerging threats, vulnerabilities, and attack vectors. Log360 can incorporate data available from such open-source threat intelligence feeds like STIX/TAXII, AlienVault, etc., enabling real-time updates on potential threats. This allows for proactive threat detection and response by correlating technical feeds with internal logs.
Organizations gain better visibility into their security landscape by leveraging open-source threat feeds alongside Log360's extensive SIEM capabilities.
Log360’s security orchestration, automation, and response (SOAR) capabilities can be augmented with insights from intelligence feeds derived from OSINT sources. When a threat is detected, automated workflows can be triggered based on the context provided by the data. For example, if an attack vector correlates with a known vulnerability reported in threat feeds, Log360 can automatically initiate incident response protocols to mitigate the threat.
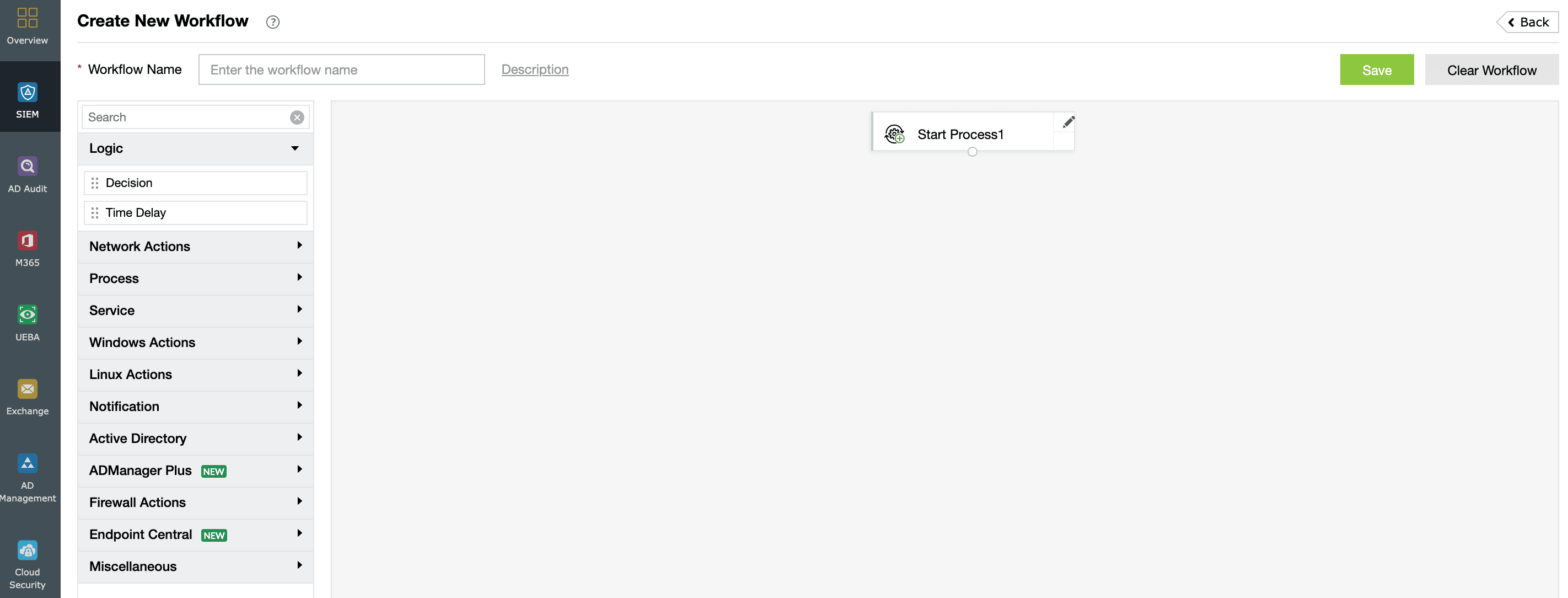
The integration aids in maintaining compliance with regulatory requirements by ensuring that organizations are aware of the latest threats and vulnerabilities that could impact their security posture. Log360’s reporting capabilities can be enhanced with insights gained from threat feeds for comprehensive audit trails.
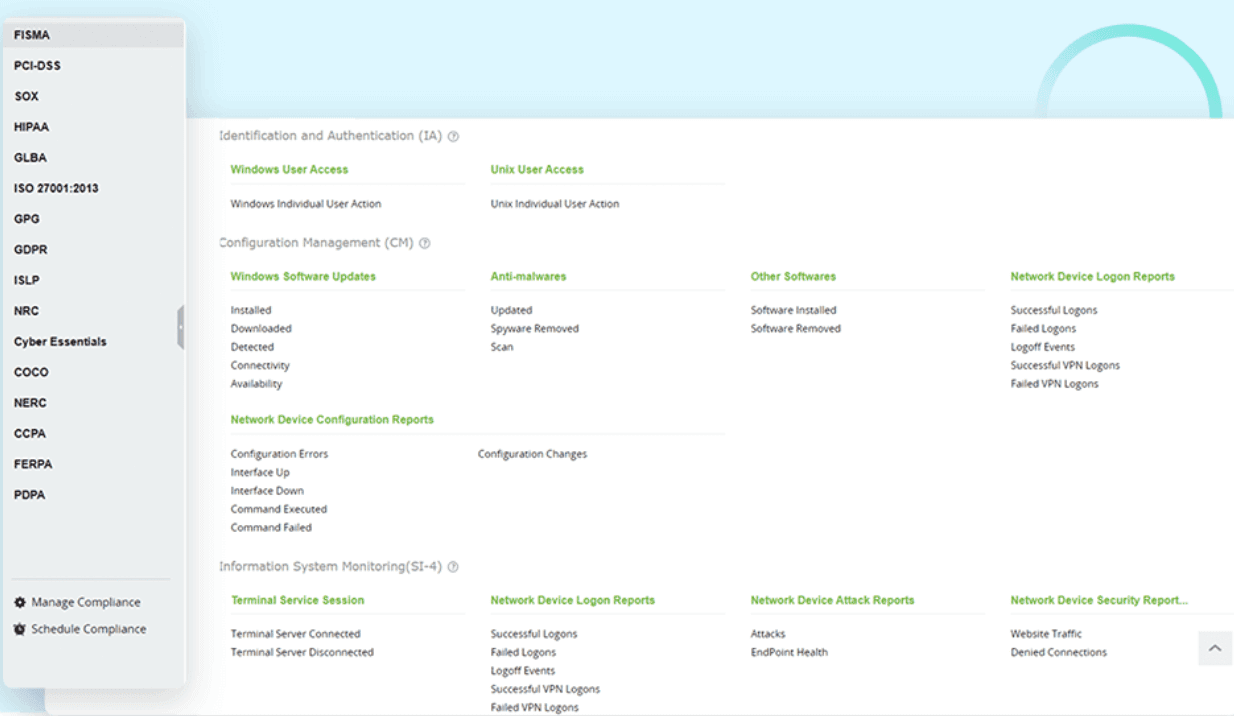
Log360—through its integration with Constella Intelligence—continuously scans the dark web for leaked credentials and sensitive information related to the organization, its employees, and third-party vendors. This proactive approach allows organizations to identify potential threats before they can be exploited by attackers.

What's next?
Bolster your business' cybersecurity efforts with Log360's SOAR capabilities.
- What is OSINT?
- What is OSINT framework?
- Types of OSINT
- Methods of OSINT collection
- Who can use OSINT?
- The dark side of open-source intelligence
- How ManageEngine Log360 and OSINT work in tandem to create proactive cybersecurity strategy for your business