In the age of interconnected healthcare systems, protecting sensitive information from data breaches has become paramount.
The cyberattacks target sensitive patient data, disrupt medical services, and can result in significant financial losses and regulatory penalties. Log360's security solution specifically tailored for healthcare organizations ensures data security across IoT devices, protects patient privacy with cutting-edge monitoring capabilities, and helps comply with HIPAA standards by integrating with EHRs to secure PHI. This will provide healthcare providers with peace of mind and patients with trust in their privacy, resulting in high quality healthcare and improved operational efficiency.
Healthcare agencies that trust Log360
8 Game-changing ways Log360 secures and simplifies your healthcare management
- Secure against a range of cyberattacks
- Simplify service management
- Safeguard PHI
- Improve compliance management
- Device and network management made simpler
- Combat APTs
- Preserve data privacy
- Stop recurring threats
Secure against a range of cyberattacks
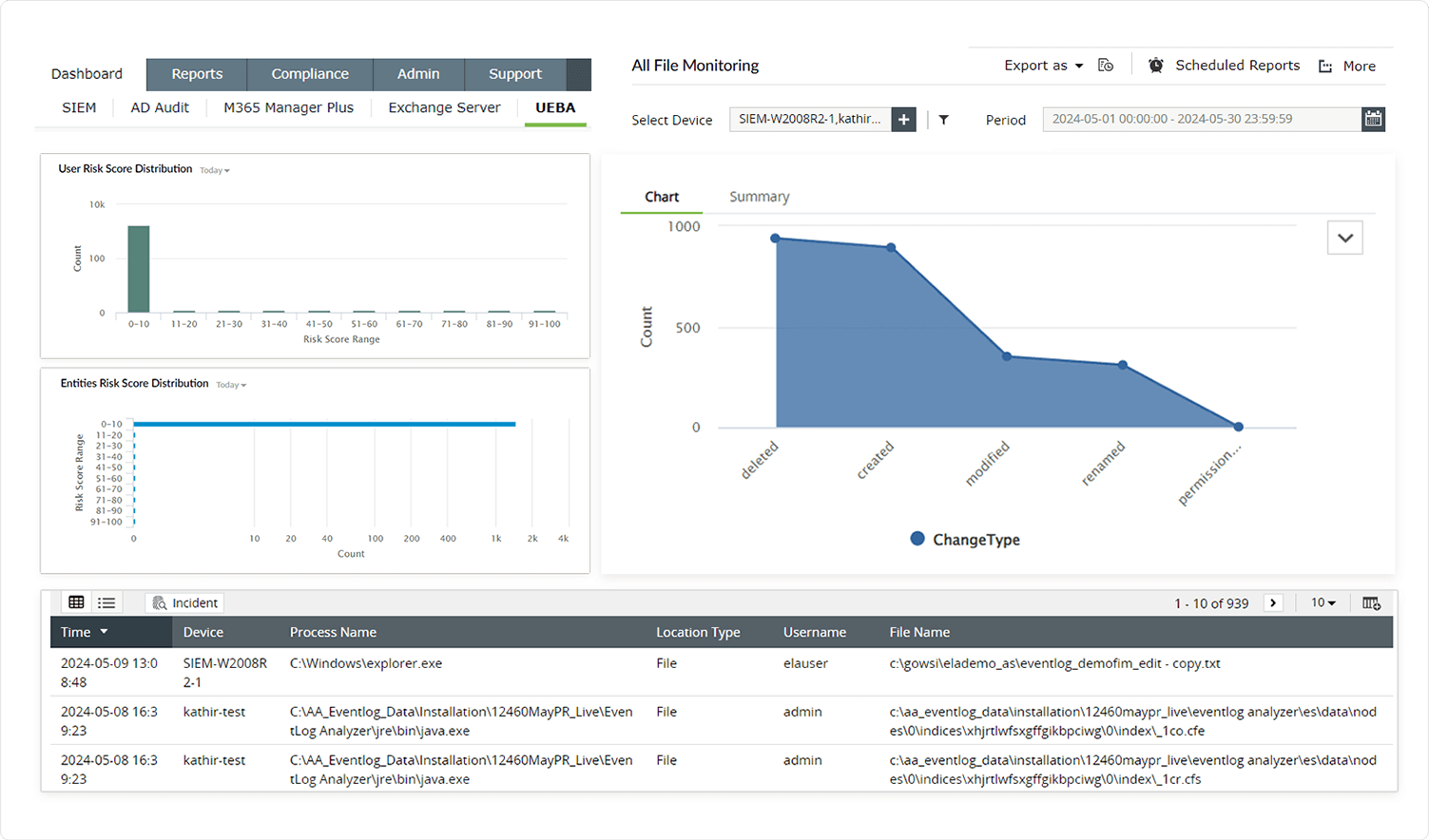
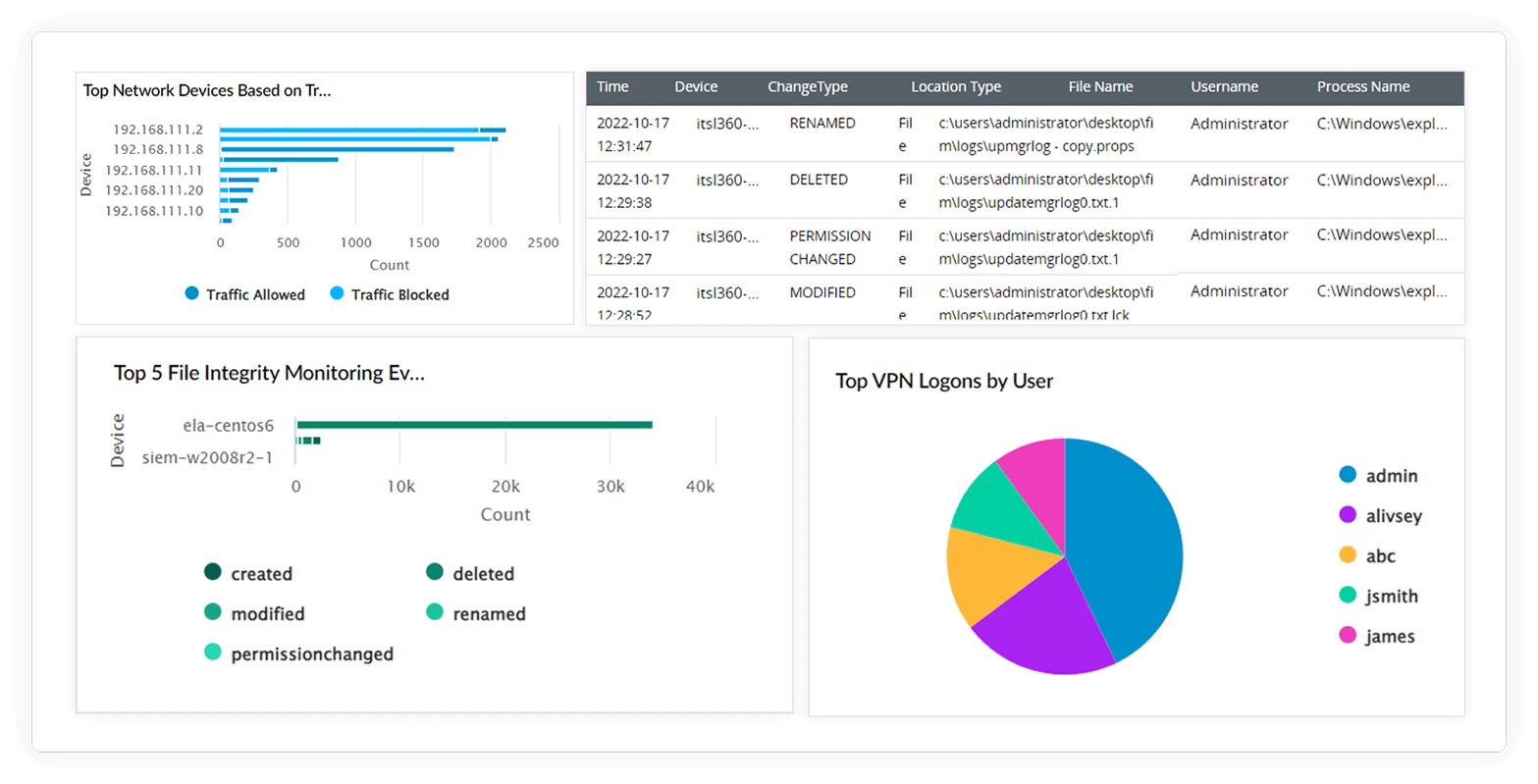
Protect your digital assets from every angleMalicious actors target healthcare organizations worldwide for the vast amount of sensitive patient information they contain. Log360's file integrity monitoring (FIM) assists administrators in managing user privileges and file permissions, which further supports access control mechanisms. By ensuring that only those with the proper authorization can interact with sensitive data, FIM improves overall healthcare data security posture.
Additionally—to preempt possible attacks by malicious actors inside the organization—Log360's user and entity behavior analytics (UEBA) add-on is equipped with machine learning algorithms that can detect anomalies in the behavior of all users and entities in a network. Any deviation from the baseline will be logged as an anomaly, and a risk score will be assigned. Any user with a high risk score will be flagged by the system and placed on a watch list.
Simplify service management
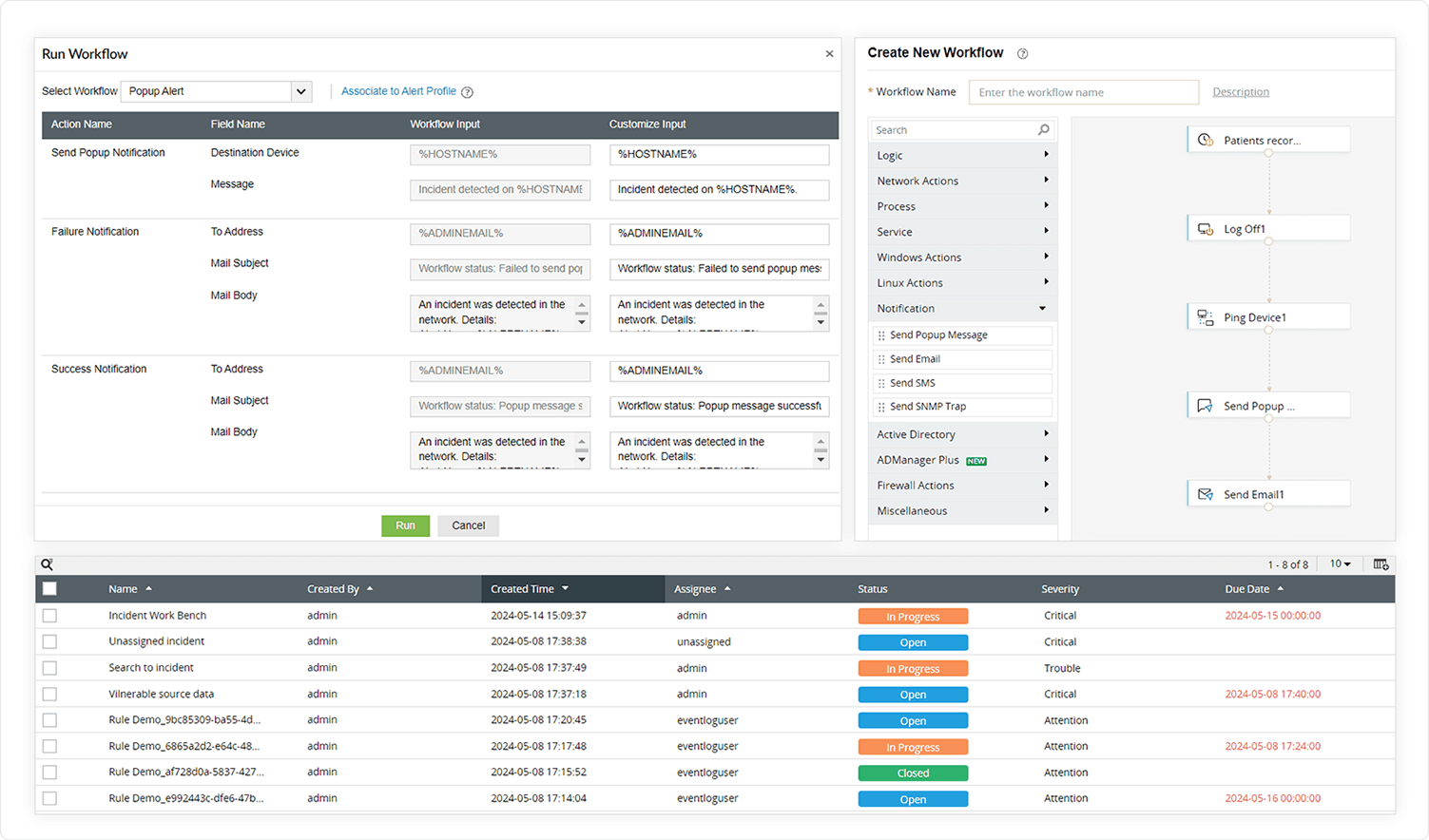
Streamline service management for enhanced efficiencyPlanning, organizing, and supervising health services are all part of service management in the healthcare sector, which is necessary to deliver efficient, high-quality patient care. It involves managing resources, improving patient experiences, ensuring legal compliance, and using appropriate healthcare IT security tools.
Log360's workflow automation can help enable effective service request management connected to healthcare. It can manage critical incidents with proactive incident detection, impact assessment, and resolution. An integrated ticketing module—part of Log360's end-to-end incident management system—assists in allocating tickets to security administrators, monitoring their progress, and ensuring accountability throughout the incident resolution process. It also includes an automatic remediation framework that can associate workflows with alert profiles. These workflows get executed automatically when a correlation alert is triggered to remediate the incident.
Safeguard PHI
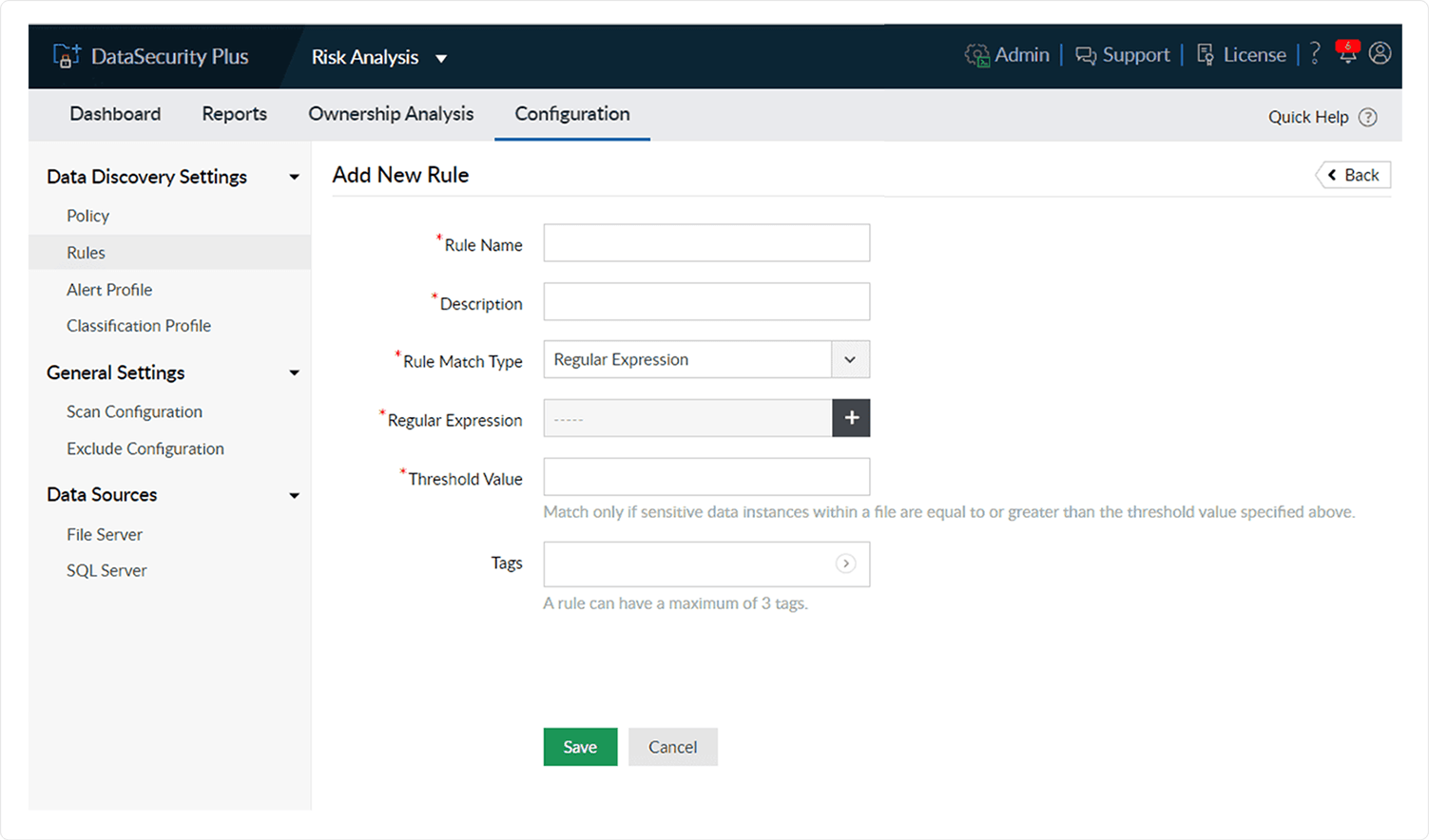
Unlock unbreachable privacy by safeguarding PHIIdentifying every instance of protected health information (PHI) on every device in your network is crucial for protecting sensitive health records. The security posture of the entire organization may be at risk if a user inadvertently downloads this data on a workstation with lesser security controls. It's therefore crucial to discover all instances of sensitive data across every single device in your network and ensure that unnecessary copies are duly eliminated.
Log360 can help you do this with its predefined rules to discover sensitive data like personally identifiable information. If the data you want to scan for isn't defined in the existing rules, you can set the required parameters and create your own rules. Based on this, Log360 will start looking for the information right away.
Improve compliance management
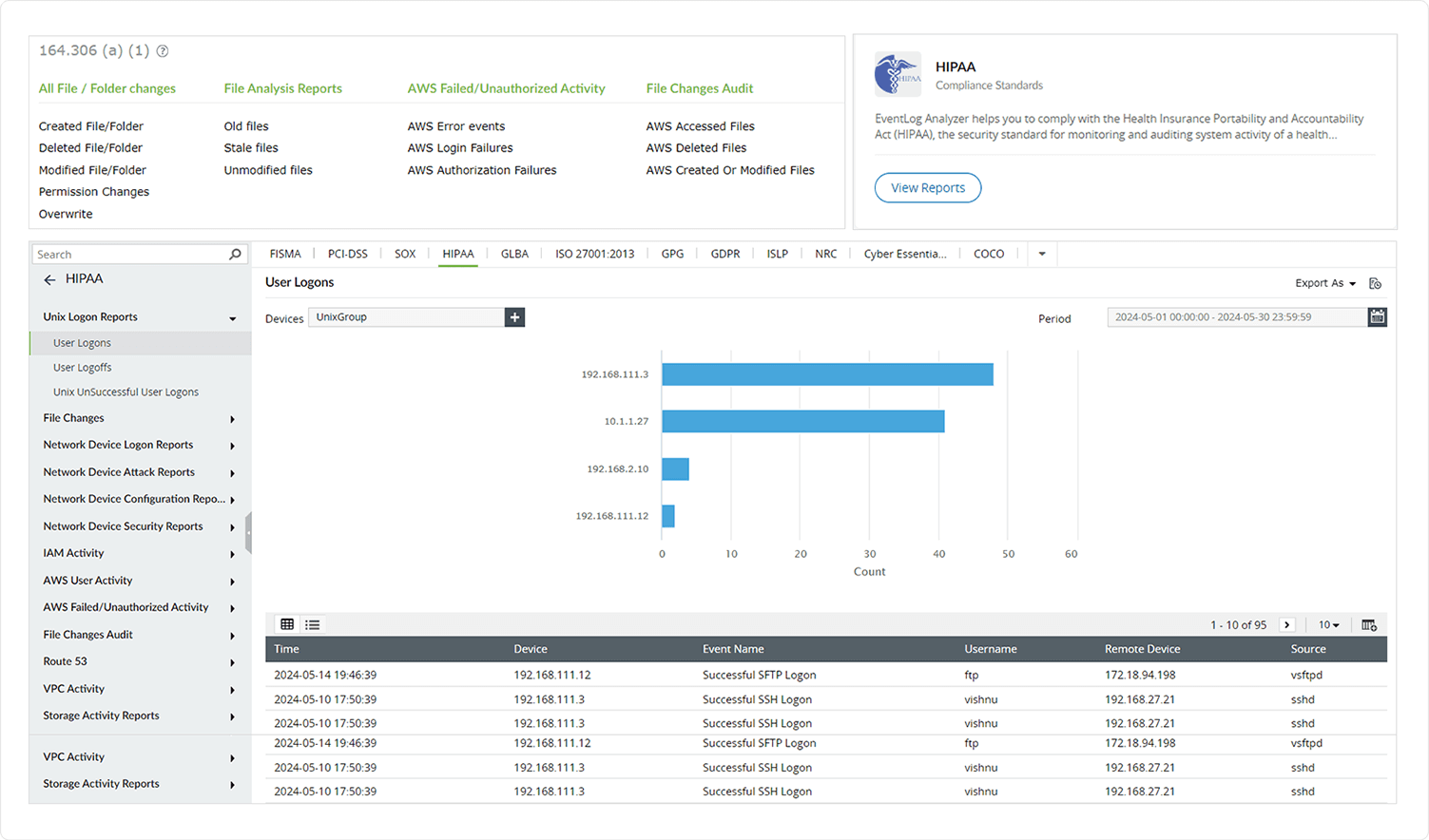
Navigate the compliance maze with easeHIPAA mandates the security of a patient's health information from any unauthorized use or access. A security management strategy must be in place for all healthcare organizations handling sensitive patient data in order to comply with HIPAA regulations and safeguard patient information from attempts of unauthorized access, use, disclosure, or interference.
Section 164.308(a)(5)(ii)(C), for instance, requires organizations to establish a process for monitoring login attempts and reporting inconsistencies. Log360 helps organizations fulfill HIPAA requirements with its compliance reports. These reports contain all of the details of the files created, modified, deleted, and renamed; files that had permissions changed; and granular details of what, when, where, and how the file activities occurred. The information regarding all the activities related to users, IAM, or endpoints can also be obtained from these reports. Also, if a compliance violation is detected, the security admin will be alerted immediately via email or SMS.
Device and network management made simpler
Gain seamless control by simplifying your network and device managementIn the healthcare sector, device and network management is crucial for maintaining patient safety, data protection, and operational effectiveness. Ensure that you audit the IT resources and networks associated with critical medical equipment.
Remotely manage app installations and protect medical devices by implementing strict access control to malicious websites, untrusted IP addresses, and unnecessary ports or protocols. Proactively monitor everything in your network, including VPNs, routers and switches, firewalls, and IDSs and IPSs.
Also, Log360 accomplishes real-time monitoring (overall file and folder monitoring) by tracking the changes made to executable files, folders, system configuration files, content files, zipped files, zipped folders, and more. The dashboards provide in-depth graphical representations of all the activities performed on files and folders, including the device name, location, and username.
Combat APTs
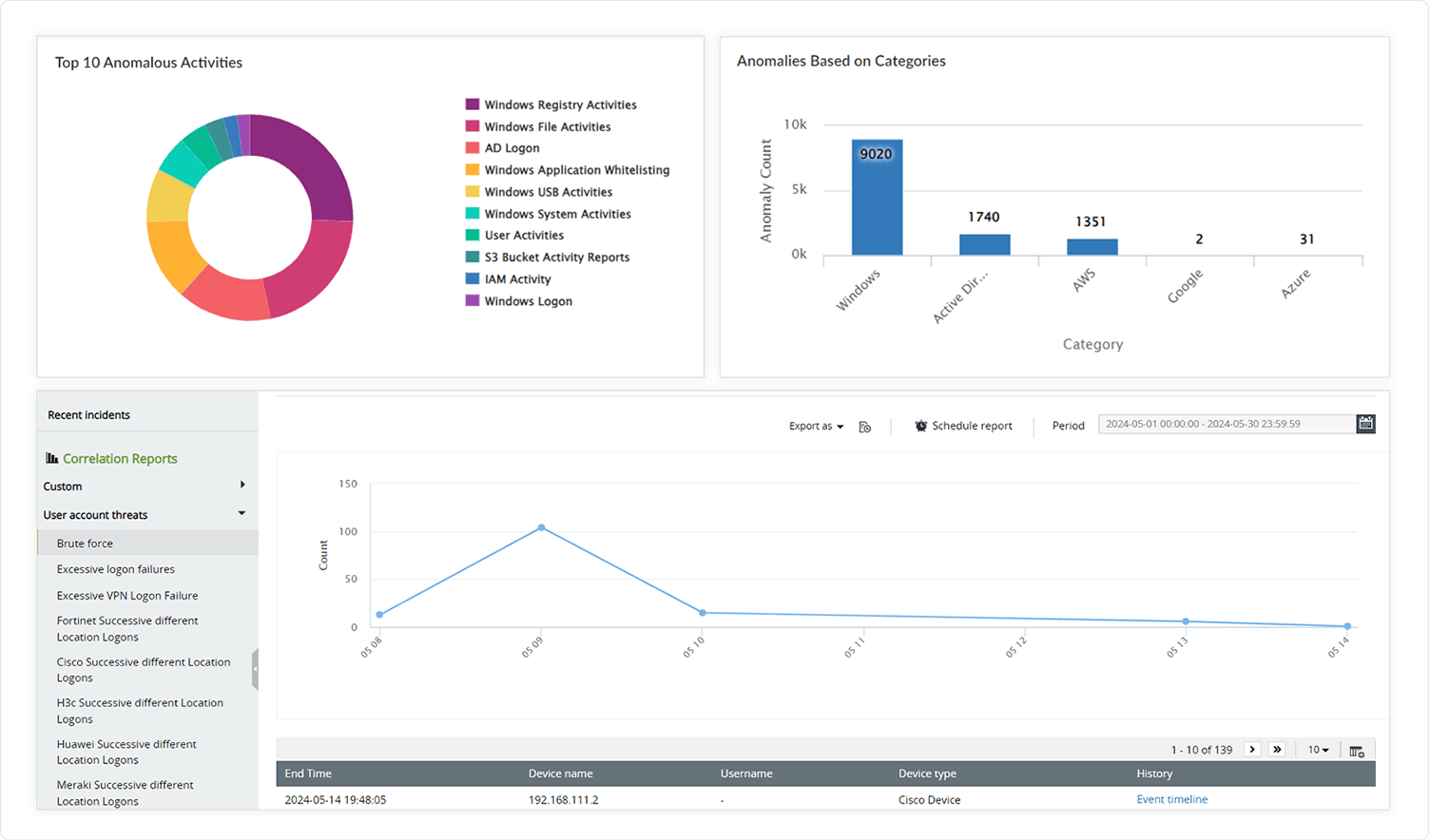
Combat APTs and fortify your frontlineThe goal of an advanced persistent threat (APT) is to retrieve valuable data while avoiding discovery for as long as possible. By evaluating and removing user privileges, using UEBA, upgrading firewalls and antivirus software, and other measures, an APT attack can be avoided.
Log360 keeps track of modifications to user privileges, which aids in spotting possible insider threats. A strong UEBA component in the solution can be used to find abnormalities and attack patterns. Additionally, this one-stop solution monitors endpoints and instantly notifies admins of any anomalies.
Also, Log360 correlates events to ensure file integrity. Users can specify a sequence of events that are indicative of an anomaly or a security loophole. A deeper understanding of the incident can be obtained by correlating the events occurring within your network, which may have been overlooked while examining the situation at the individual level.
Preserve data privacy
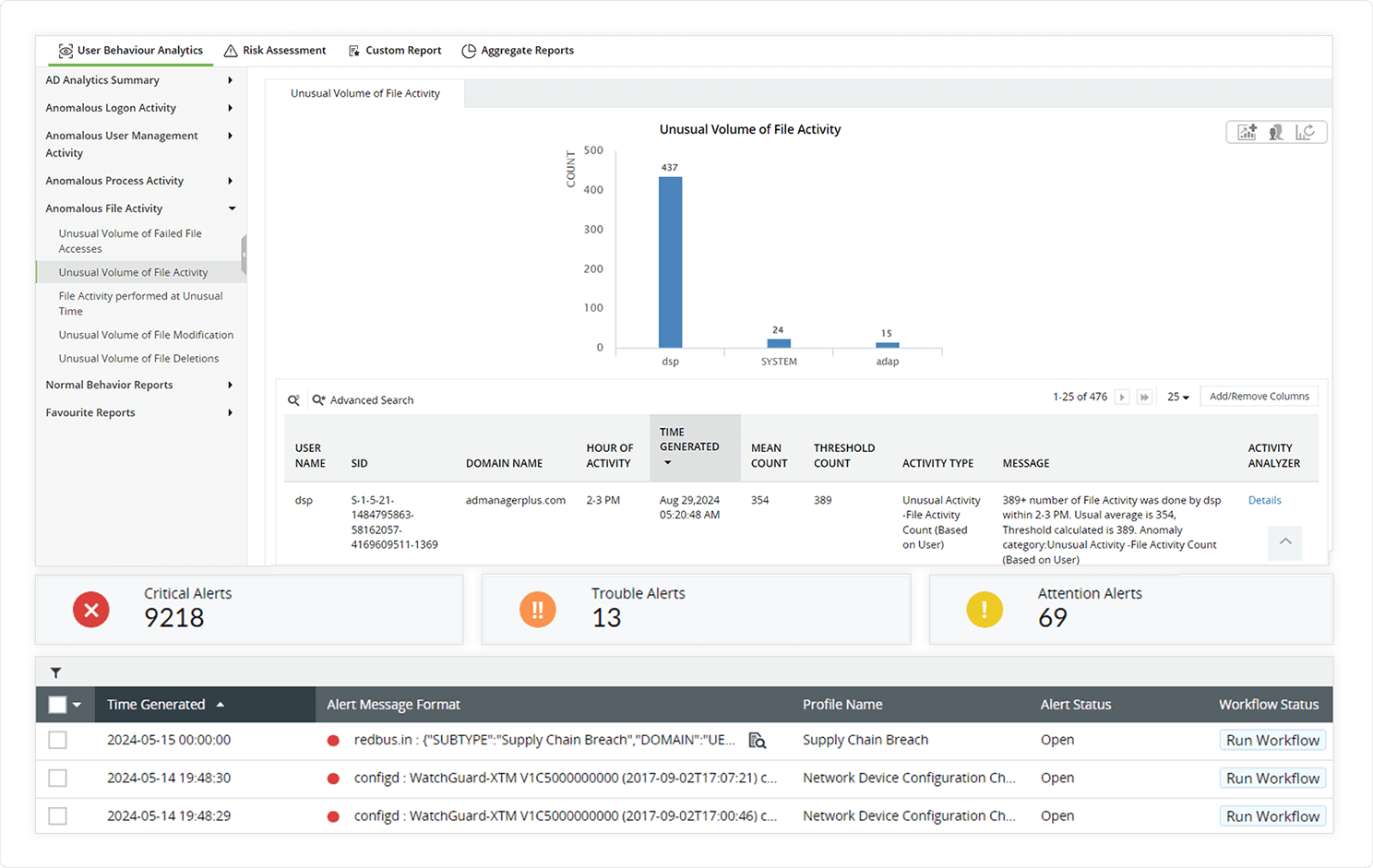
Protect and preserve data privacy for a safer tomorrowData privacy and security in healthcare are essential in the healthcare industry in order to protect patient confidentiality, ensure trust in the healthcare system, assure compliance, and prevent unwanted access to sensitive health information. Log360 will help you enhance data privacy by:
- Monitoring Exchange servers and Active Directory in real time.
- Implementing alerts and blocking unauthorized ePHI transfers via email.
- Stopping ransomware attacks and data breaches in your hybrid environment by gathering network device logs and using machine learning to detect anomalies.
- Preventing unauthorized access to safeguard patient privacy.
Stop recurring threats
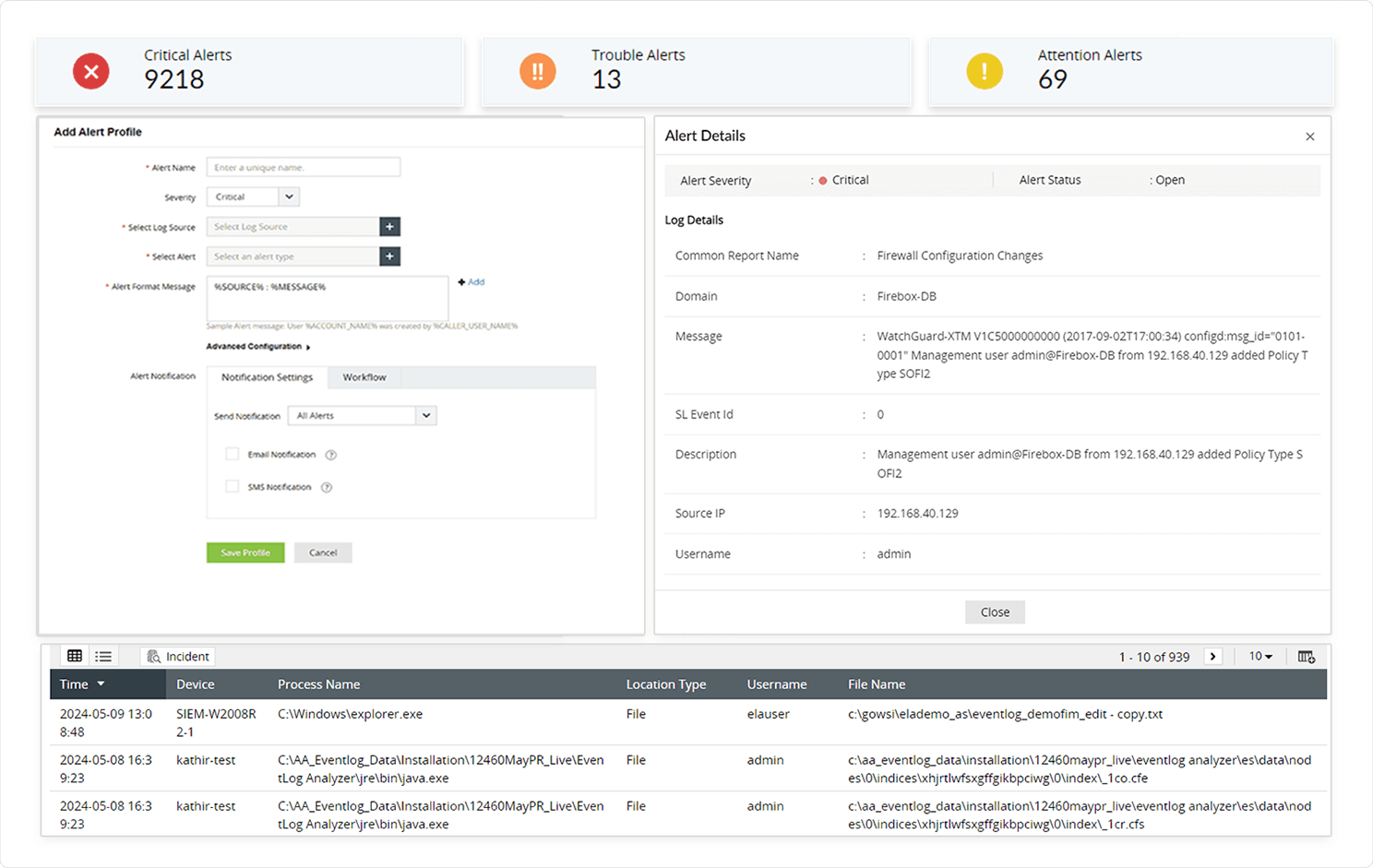
Put an end to repeat threats: Stop the recurrenceAs soon as we become aware of an attack within an organization, we must move quickly to counter it. This will ensure that the organization won't experience a similar threat in the future. Upon identifying the vulnerability and the specific threat's cause, create an incident workflow. Ensure that unwanted modifications are tracked down and stopped by setting up alerts with a predefined threshold based on the vulnerability discovered.
Log360 provides real-time event alerts for important updates, including changes in rules or access policies for database-stored files and folders. You can do this while configuring the alert criteria as per your needs. Alert criteria can also be created based on custom thresholds and user actions.
Essential health watch: 5 critical focus areas and how Log360 empowers your monitoring strategy
| Key areas that need to be secured | Log360's capabilities |
|---|---|
| Patient records and health information |
|
| Medical devices |
|
| Network security |
|
| Access control and authentication |
|
| Compliance and regulatory requirements |
|
Hear what our customers say
Log360 is an all-in-one SIEM solution that provides exceptional bang for your buck.
I like that we can do GDPR reporting and audit anyone accessing sensitive patient information. It helps with compliance and reporting, which is heavily relied on by the NHS.
Your organization is one of a kind. Discover how Log360 can seamlessly address your unique requirements
Awards
Log360 won the 2023 Cybersecurity Excellence Award for IAM and identity governance (Asia)
Log360 won the 2022 Fortress Cyber Security Award for Authentication and Identity.
Why choose Log360?
Log360 is a unified SIEM solution with integrated DLP and CASB capabilities that detects, prioritizes, investigates, and responds to security threats. It combines threat intelligence, machine learning-based anomaly detection, and rule-based attack detection techniques to detect sophisticated attacks and offers an incident management console for effectively remediating detected threats. Log360 provides holistic security visibility across on-premises, cloud, and hybrid networks with its intuitive and advanced security.
Book a personalized demo




