Enterprise network systems are vulnerable to a wide variety of risks in the cybersecurity landscape. Without a proper setup to manage such risks, organizations can face losses amounting to millions of dollars, making integrated risk management a crucial aspect in your security strategy.
Gartner defines integrated risk management as "a set of practices and processes supported by a risk-aware culture and enabling technologies, that improves decision making and performance through an integrated view of how well an organization manages its unique set of risks."
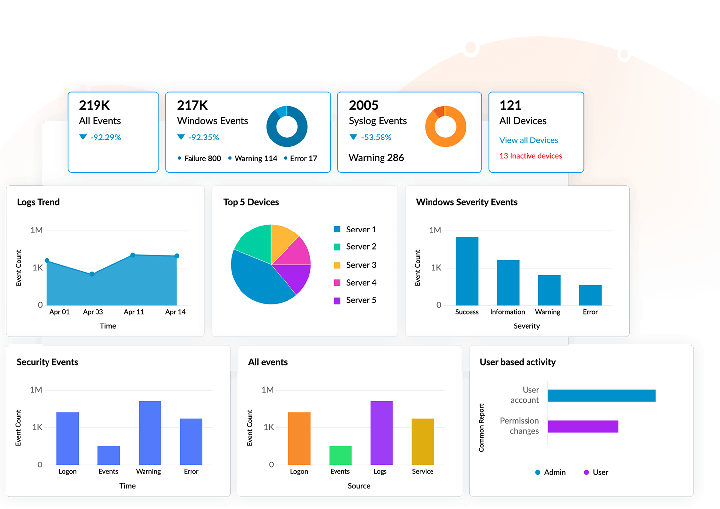
Log360 collects and analyzes log data from more than 700 log sources, including firewalls, endpoint devices, and servers. This helps Log360 keep tabs on your entire network. With Log360, you can identify risks, analyze them, configure alerts, and take necessary remedial action, helping you manage your enterprise's network risks effectively.
Log360 helps you identify threats by correlating seemingly unrelated events occurring in your network. With advanced threat analytics, Log360 takes risk identification one step further by regularly retrieving the latest information from multiple reliable threat feeds and monitors your network for signs of possible threats.
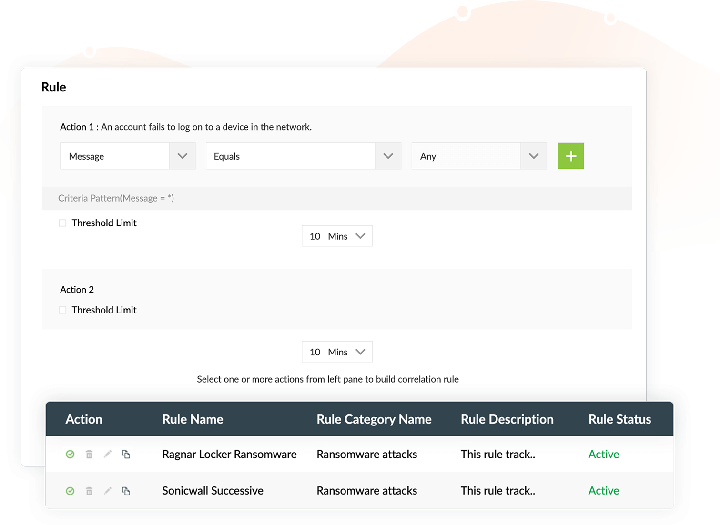
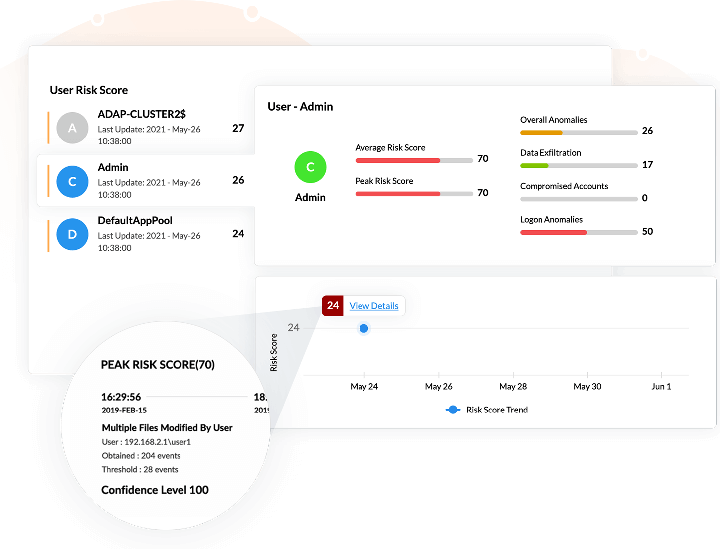
Log360 analyzes risks based on the severity associated with them. There are five categories of risk, based on which Log360 calculates a risk score:
Any time a user or entity's observed activity deviates from its baseline of expected activities, the risk score of the user or entity associated with one or more of the above threat categories will be increased.
Log360 enables you to respond to critical security events promptly with its real-time event response system. You can also assign incidents to admins and track their progress from a single console. The automated workflow management console allows you to mitigate security incidents in your network before they result in a breach by automating response workflows when alerts are triggered.
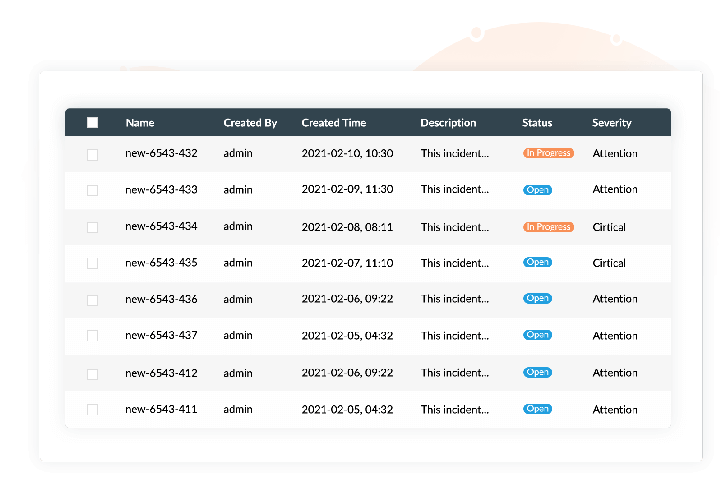
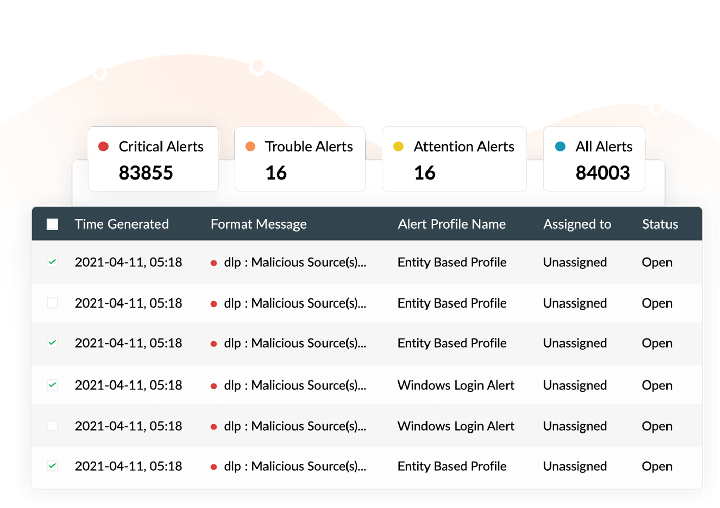
Log360 provides you with an intuitive reporting console that delivers insightful reports and trend graphs that help you conduct effective investigation into events and respond to anomalies effectively. Configure alert profiles for the risks that get detected by Log360, so that your security team is always up to date and can take necessary measures immediately.
Log360 collects logs from over 700 log sources and monitors them to ensure no threat goes undetected. This helps in spotting indicators of compromise (IoC) and eliminating such threats promptly.