Log360 helps you detect and stop phishing attacks with:
Log360's threat intelligence module holds access to threat information from international threat feeds like STIX, TAXII, and AlienVault OTX. Receive a prompt alert if a malicious IP source interacts with your network, and automatically assign it to your organization's security team. The solution provides better visibility into security data to help you swiftly resolve critical events, thereby thwarting security breaches.
Log360's rule-based correlation engine identifies suspicious event patterns in your network logs, like suspicious software installations, by correlating various events to address threats. Log360 triggers an alert based on the workflow related to event logs and automatically assigns a ticket to a security admin.
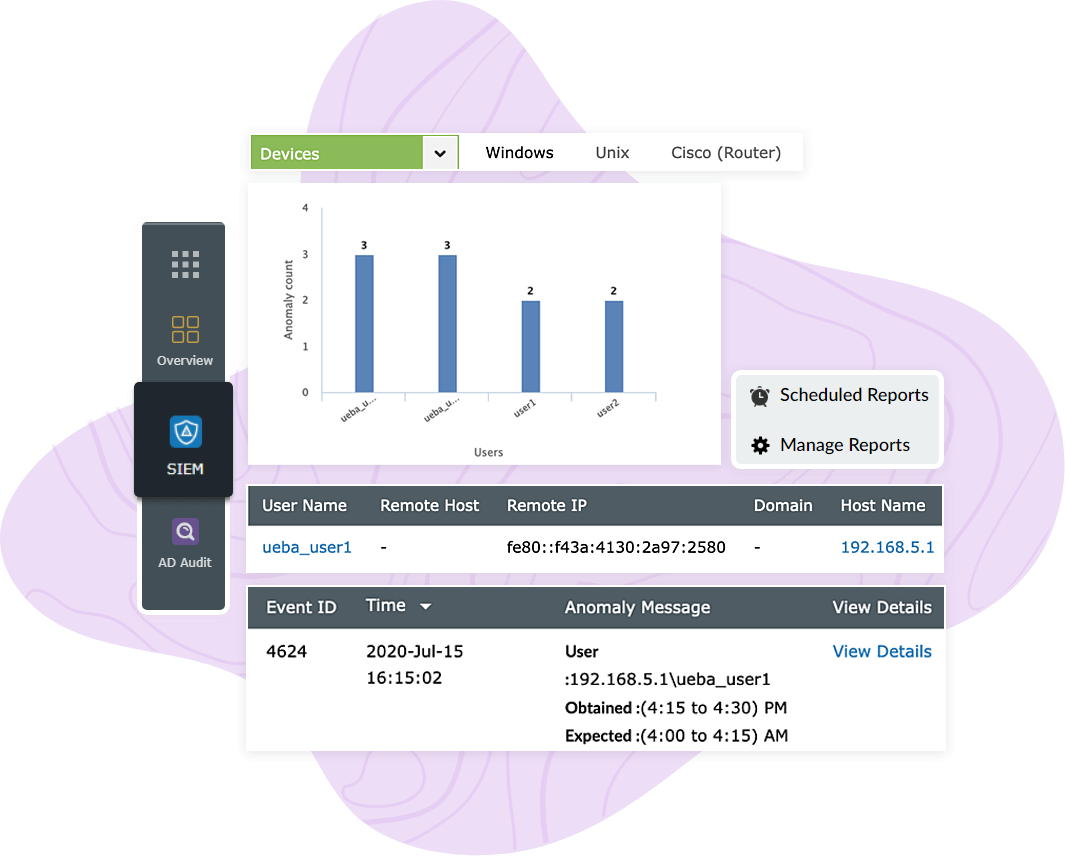
Leverage ML-based user entity and behavior analytics (UEBA) to spot malicious intruders. Log360 performs user behavior profiling based on time, event pattern, and number of events triggered to accurately spot anomalies. Instant alerts are sent to the security team for further investigation.
Log360's automated incident response helps you alleviate phishing attacks with:
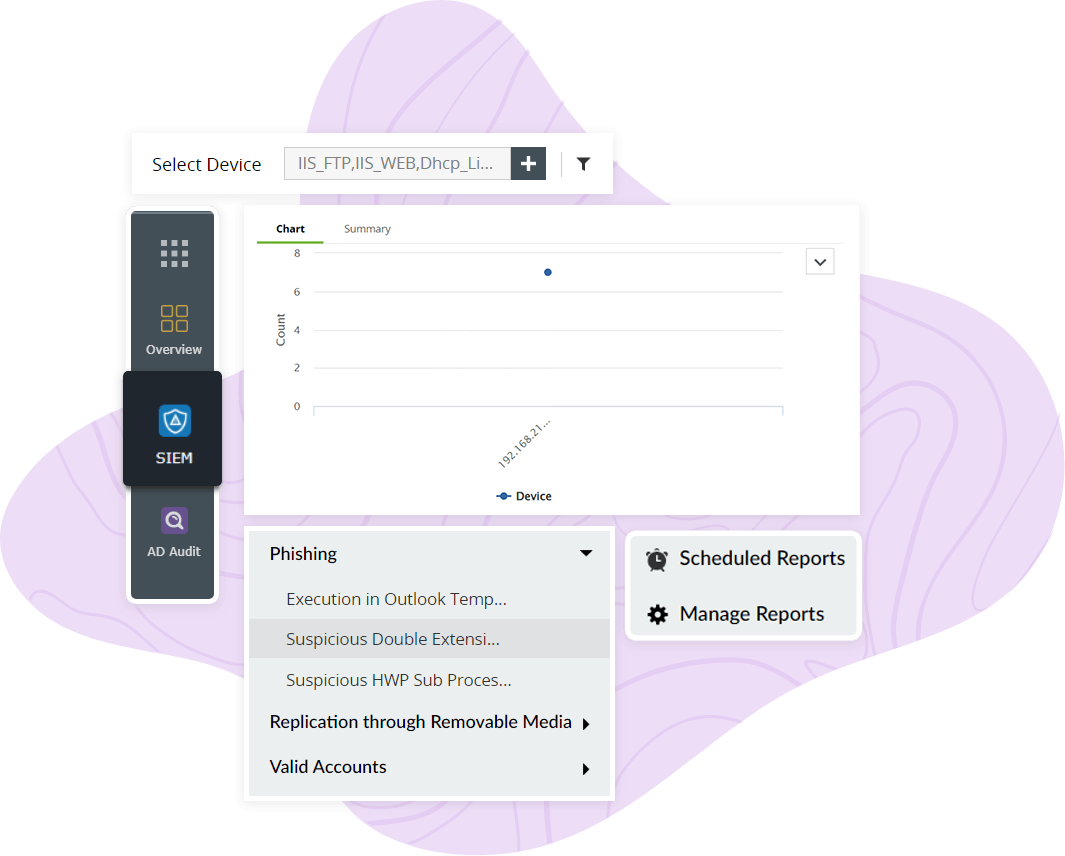
Log360 monitors all incoming traffic based on IP address, source, destination, and port to detect a compromised system. When suspicious activity is detected, the solution's SOAR capability automatically executes workflow profiles and assigns tickets to security admins to quickly remediate a phishing attack.
Log360's threat intelligence console has threat feeds that are constantly updated with all the blocklisted, malicious IPs and URLs around the globe. Log360 categorizes alerts based on the severity as Attention, Trouble, or Critical. Once the alert is triggered, a detailed correlation report is sent to the IT admin so they can investigate an issue promptly.
Log360 provides an intuitive incident management console to help you prioritize and keep track of all security incidents. The solution lets you define a set of actions to be triggered based on the type of security incident when an alert is raised. You can also automate responsive actions, like shutting down compromised devices or disabling USB ports.
Collect, analyze, and spot suspicious security threats throughout your network logs based on the indicators of compromise.
Learn MoreLog360's extensive threat analytics capability helps you easily find malicious activity and threat patterns in your network.
Learn MoreGet notified about security violations, and identify anomalous privileged user activities like user logons, user logoffs, and failed logons.
Learn MoreAutomatically generate predefined reports, and comply with regulatory mandates such as HIPAA, SOX, PCI DSS, and the GDPR.
Learn MoreSecure your AWS, Azure, Salesforce, and Google Cloud infrastructure with log alerting and incident management.
Learn MorePhishing is a social engineering attack vector that leverages deceptive email or messaging tactics to deceive unsuspecting victims into divulging sensitive information or visiting malicious websites, ultimately compromising their cybersecurity posture.
Here's an example: An attacker creates a fake website which appears to be legitimate, impersonating a well-known company. They run an email campaign to lure victims into clicking a malicious link, which redirects to the website. Upon entering the website, users are prompted to enter their login credentials, which the attackers steal and use for malicious purposes.
Once an attacker gains valid credentials to log in, they bypass the network's security systems and propagate within the network to exploit business-critical resources.
With Log360, you can identify if a user logs in with credentials they obtained from a malicious source, deviates from normal user behaviors, escalates privileges, or accesses or modifies any sensitive resources.
Log360 notifies you in real time when a malicious source attempts to infiltrate your network. By giving information such as the domain's age, geography, and reputation score, the solution aids in further analysis and investigation. ManageEngine Log360 is a comprehensive SIEM solution that enables you to proactively mitigate phishing attacks with its ML-driven UEBA module.