While the constantly evolving technology landscape has become a sign of progress and has bolstered businesses, it has also brought with it numerous vulnerabilities and advanced network security threats that pose risks to organizations' cybersecurity postures.
When it comes to detecting such sophisticated cyberattacks, traditional security measures and responses may not suffice. This is why organizations need to move towards user and entity behavior analytics (UEBA) for advanced threat detection and response.
Resolving threats using Log360's UEBA console
Log360 collects and analyzes logs from different sources, such as firewalls, database servers, mail servers, and endpoints, to understand the regular usage patterns exhibited by users. Using this data, a baseline is established. A risk score is then calculated based on comparisons between observed activities and the baseline. Anomalous behavior generates a risk score depending on its severity and subsequently triggers an alert so that necessary action can be taken to mitigate the threat. Anomalies are identified as time-based, count-based, and pattern-based.
Key threat detection capabilities of Log360's UEBA console
Spotting insider threats
Insider threats refer to the risks posed by users in an organization's network. This includes malicious threat actors who intend to cause damage to the organization by stealing sensitive information for financial or personal gain. Insider threats can also be negligent users who, by their careless actions, inadvertently expose the network to attacks.
Some signs of insider threats:
- Abnormal file permission changes
- New or unusual system access attempts
- Unusual access times
- Application allow listing
- Excessive authentication failures
Log360 closely monitors such events, spots abnormal behavior, and alerts IT administrators of a possible attack. With Log360, you can go a step further in mitigating threats by using its incident management console.
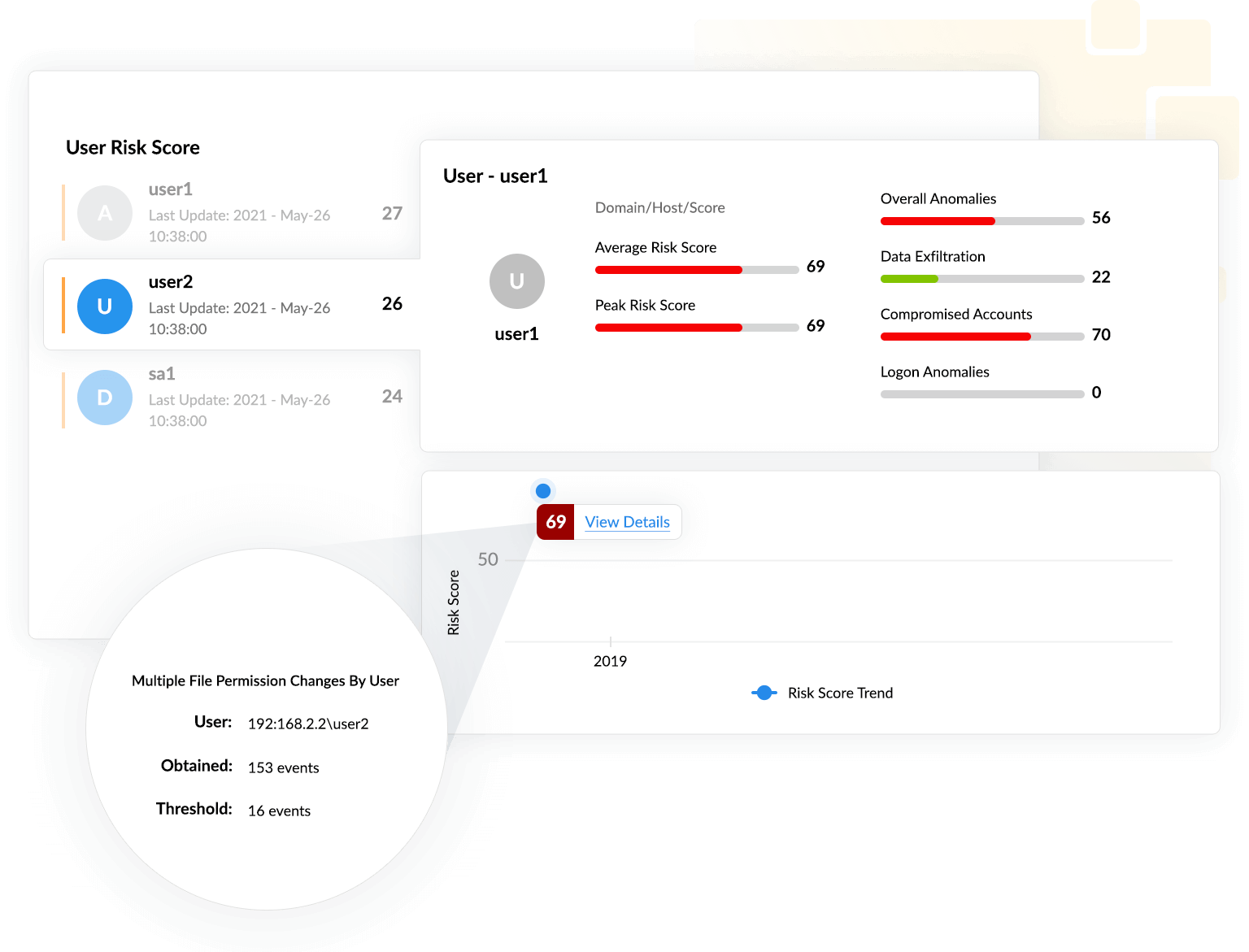
In this scenario, it can be observed that a user attempted 153 file permission changes within a short interval of time, and that value is higher than the established baseline value of 16. Thus, this triggers a count anomaly and is flagged as a high risk.
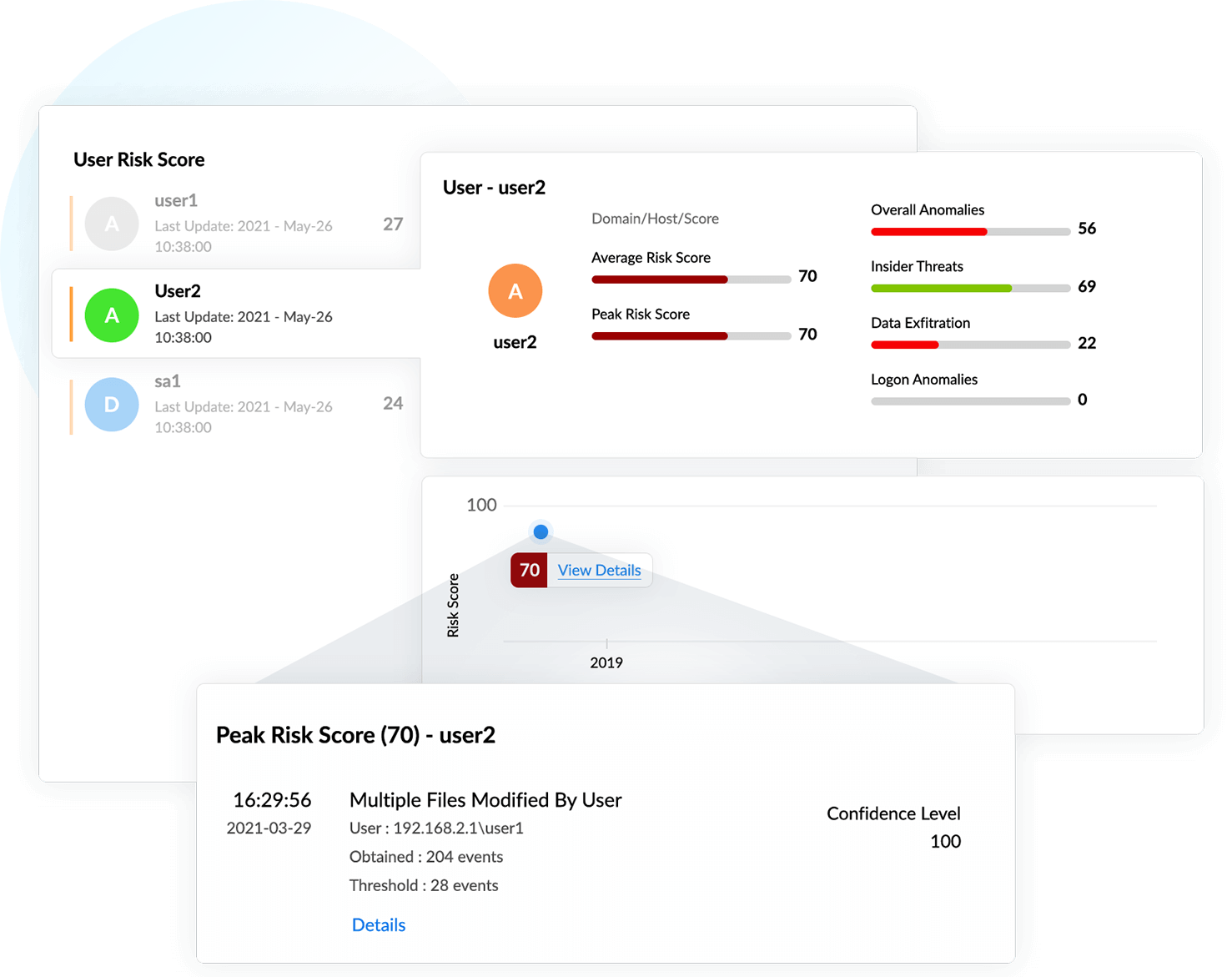
In this example, a user has a risk score of 70, and Log360 has detected a possible account compromise scenario due to multiple indicators. For instance, the user made modifications to 204 files in a set interval of time, which is higher than the user's normal number of modification instances (28).
Identifying account compromise
If an attacker gains access to a legitimate user account, the account can be leveraged to perform detrimental activities, such as malicious software installations, that can lead to further compromise. There are several ways user accounts can be compromised, including phishing, brute-force attacks, users accessing unsecured networks, and weak password policies.
Some common indicators of account compromise:
- Malicious software installations
- Anomalous login activity
- Clearing event logs
- Successive login failures
Detecting data exfiltration
Data exfiltration is one of the most common end goals for the majority of cyberattacks. In simple terms, data exfiltration is the unauthorized movement of data from within an organization to outside of it. This affects an organization in multiple ways, including financial losses, compliance violations, and damage to its reputation.
Some common signs of data exfiltration:
- Attempts to access sensitive files and folders
- Plugging in removable storage devices
- Unusual file download patterns
- Unusual access times
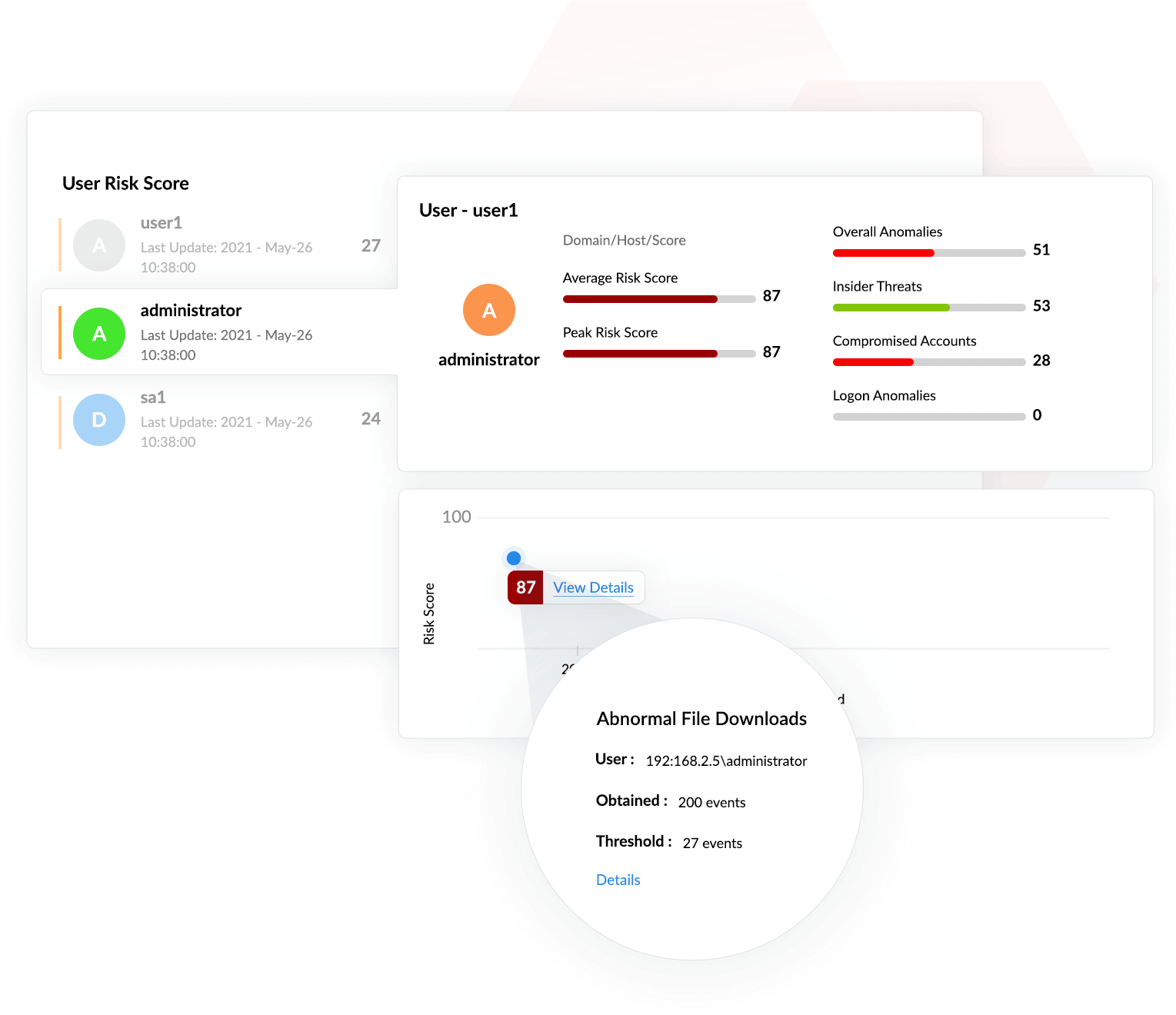
In this scenario, the user's risk score is calculated to be 87. This score is a consequence of several events, including abnormal file downloads, an abnormal user login count, and numerous login failures.
Why is Log360 the best fit for your UEBA needs?
- Log360 identifies, qualifies, and investigates threats that might otherwise go unnoticed by extracting more information from the logs collected by its SIEM component to provide better context.
- It offers greater visibility into threats with its score-based risk assessment for users and entities through its dashboard. This approach helps you determine which threats actually merit investigation.
- Log360 provides more context to the risk scoring process by using dynamic peer grouping. It monitors user activities and calculates a risk score based on each user's peer group. If a user exhibits behavior that is abnormal for their virtual peer group (resulting in a high risk score), an alert is raised.
- It customizes risk scoring by assigning different weightage to different factors. In this way, you can make sure Log360 is optimized for maximum performance, resulting in enhanced threat detection.
By combining all these capabilities, Log360's UEBA module helps you secure your organization's network and defend against unusual cyberthreats with ease. Read on to learn more about the other key capabilities of Log360.
Download now

