Traditional signature-based antivirus solutions fail against zero-day and polymorphic malware. Malware Protection Plus leverages deep learning and anomaly detection to analyze process behaviours, system interactions, and execution patterns in real time.
Threat detection with Malware Protection Plus
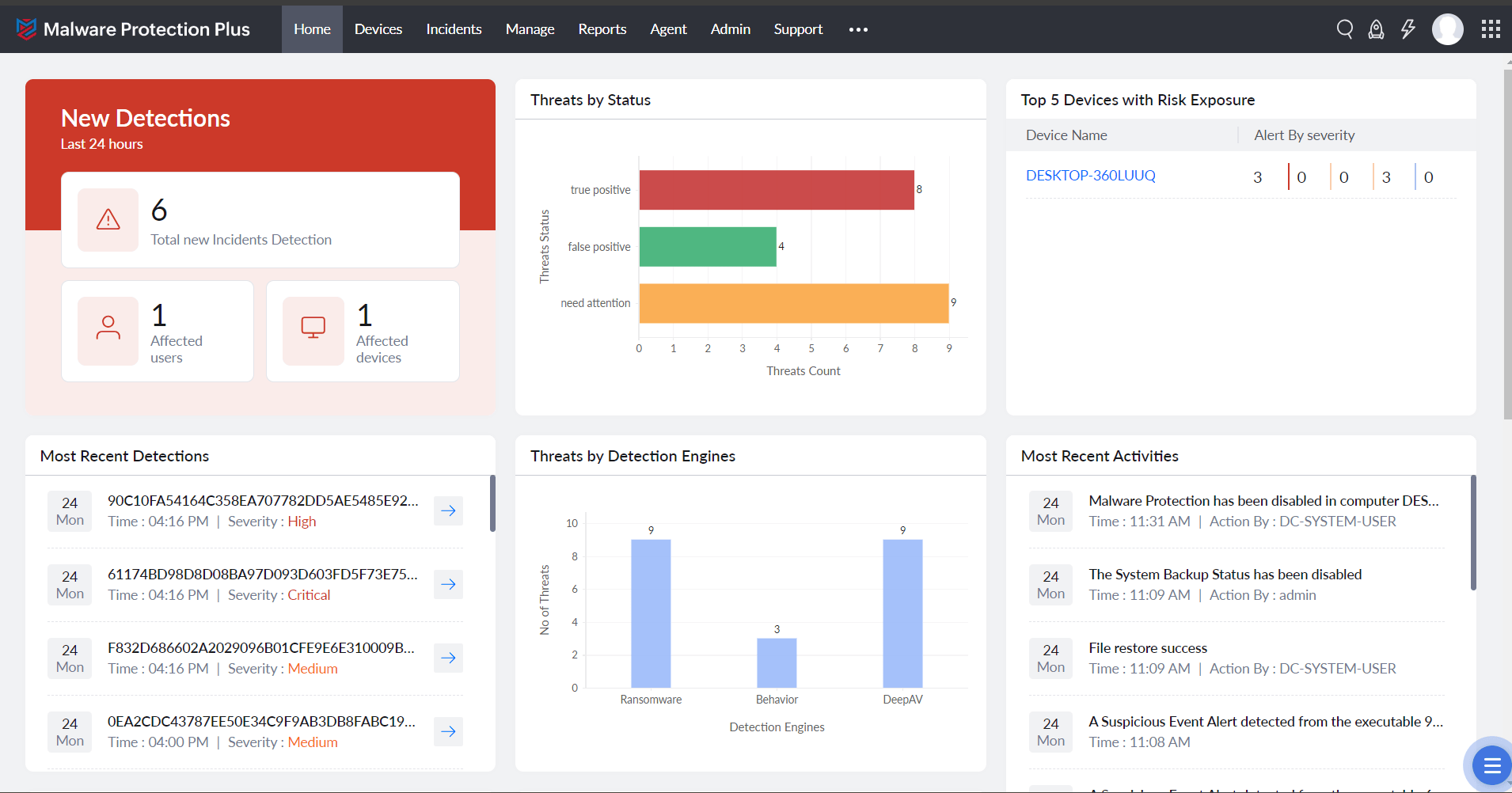
Why is real-time threat detection important for your business?
In the event of a cyberattack, how you respond to the first few minutes can make or break everything. The stakes are higher if you're running a business. The difference between catching an intruder at the door versus dealing with a complete security meltdown often comes down to how quickly you spot the threat. Traditional detection methods rely heavily on signature-based approaches, which can fall short against unknown malware, zero-day threats, and fileless attacks. AI-assisted threat intelligence can flag suspicious activity as it happens. That's where real-time threat detection becomes crucial to your cyber hygiene. This proactive approach helps IT teams:
- Cut down dwell time and fasten incident response.
- Prevent lateral spread and contain the damage caused by malware.
- Maintain compliance with evolving data protection mandates.
- Strengthen trust with customers, partners, and stakeholders.
How real-time threat detection works?
Modern cyberattacks are no longer predictable or easy to detect using traditional methods. Attackers now use stealthy techniques, fileless malware, and rapidly evolving threats to bypass signature-based defenses. To counter this, Malware Protection Plus adopts a multi-layered detection strategy that combines machine learning, behavior analysis, and deep learning to deliver comprehensive, real-time protection.
Multiple detection layers: Malware protection Plus integrates both behavior-based analysis and deep learning techniques. This enhances accuracy and broadens the scope of detection across diverse threat vectors.
ML-Assisted behavior analysis: Malware Protection Plus looks out for anomalies such as unexpected file modifications, suspicious process executions, or abnormal access patterns.
Deep learning algorithms: Advanced deep-learning models provide an additional layer of protection, recognizing patterns linked to malware, even those previously unknown. This ensures both online and offline protection.
Proactive threat detection: By not relying solely on static signatures, this dynamic approach identifies zero-day threats and emerging malware proactively, before they can cause damage.
Continuous learning: The antivirus engine adapts over time, learning from new attack patterns and threat intelligence. This reduces reliance on frequent updates while keeping protection up-to-date.
Balance between detection and performance: Apart from real-time detection, Malware Protection Plus also carefully manages system performance. The detection logic is optimized to minimize false positives and avoid disrupting day-to-day operations.
What are the types of real-time threat detection?
AI-assisted behavioural Detection
Distinguish between the ordinary and the suspicious by closely monitoring API calls, process injections, and lateral movements. Malware Protection Plus establishes a benchmark for normal activity, allowing AI to spot deviations that might suggest malicious intent, whether from familiar malware or entirely new threats.
Fileless malware detection
Traditional antivirus solutions miss fileless attacks (e.g., PowerShell scripts, WMI abuse, in-memory execution), which cleverly bypass detection by leaving no trace on the disk. Malware Protection Plus keeps a vigilant eye on memory processes like DLL injections and intercepts malicious "living-off-the-land" binaries (LOLBins).
Ransomware blocking
Malware Protection Plus detects unusual file encryption and modification patterns early on, isolating affected endpoints to stop any further spread. It also swiftly rolls back ransomware changes using secure backups ensuring your data remains safe and sound.
Memory exploit prevention
Attackers are constantly on the lookout for vulnerabilities to exploit, particularly in system memory (like buffer overflows and ROP chains) to execute harmful code. Malware Protection Plus tackles these sophisticated threats with powerful runtime memory protection and identifying memory injection attempts.
Deep memory scanning for stealth threats
Advanced malware hides in memory to evade detection. Our solution lets you perform a full memory scan on-demand or on-write to uncover shellcode and payloads scanning for hidden malicious artifacts.
Credential hardening & LSASS protection
LSASS is a prime target for credential theft (via Mimikatz-styled attacks). Malware Protection Plus prevents LSASS memory dumping, detects suspicious credential access.
Living-Off-The-Land attack prevention
Attackers abuse trusted tools ( like PowerShell, WMI) for stealthy execution. Detect anomalous script execution (such as encoded PowerShell commands) and monitor lateral movement via RDP, SMB, and WMI abuse.
Intent-Based Detection (Indicators of Attack)
Instead of just focusing on malware signatures, Malware Protection Plus delves into the methodologies and intent behind the malicious behaviour, enabling us to identify the attack chain, from the first breach to data exfiltration, and intervene to block exploitation attempts.
Command & Control (C2) detection
Persistent malware relies on communication with attacker-controlled servers to receive instructions and deliver payloads. Malware Protection Plus stops shellcode execution in its tracks ensuring that C2-based attacks are thwarted before they can even begin, keeping your systems safe and secure.
What are the key features to look for in a real-time threat detection tool?
It’s not simply about spotting malware; it’s about catching it early, catching it accurately, and doing so without drowning your IT team in endless alerts. If you’re evaluating your options, here’s what really matters:
- Behavioral analysis and anomaly detection
A solid detection tool should do more than compare files to a list of known threats. You want technology that pays attention to how things actually behave, in real time. Can it pick up on unusual patterns—like a sudden burst of files being encrypted? These subtle signs can be the first hints of ransomware or other advanced threats.
- Machine Learning & AI-powered insights
Tools that leverage AI and machine learning can recognize new, never-before-seen attack methods (zero-days) and adapt on the fly. This results in fewer missed threats, fewer false alarms, and a security posture that actually keeps pace with the bad guys.
- Real-time alerts
Speed is everything when it comes to detection. Your tool needs to let you know the moment something suspicious pops up, so your team can react before a minor incident turns into a major crisis.
- Lightweight, endpoint-first approach
Threats usually start at the endpoint, so that’s where your detection should happen. The solution should be able monitor for threats locally, right on the device, without relying on constant cloud checks. That way, you get rapid decisions and protection that doesn’t bog down performance (or stop working when the internet’s down).
- Automated response actions
Spotting an attack is only half the battle, you need to stop it, too. The tool should have a self-healing mechanism that automatically take action: kill a rogue process or even roll back unwanted changes with minimal manual intervention.
- Deep visibility & forensic analysis
When something goes wrong, you need answers, not just alerts. The right tool gives you a clear timeline of what happened, which files or users were involved, and how the threat got in. This helps you clean up quickly, learn from incidents, and make your defenses smarter and stronger.
- Scalability & integration
Whether you’re protecting a handful of laptops or a global network, your solution should grow with you. It also needs to play nicely with the rest of your security stack, be it integrating with SIEMs, SOARs, or your endpoint management tools, so you get a holistic, unified defense.
In short, the best real-time threat detection tools are proactive, intelligent, and easy to fit into your existing workflow—helping you stay one step ahead, no matter how the threat landscape evolves.
Why choose Malware Protection Plus?
~1%
System bandwidth used by our agent, minimizing resource footprint.
3 Million
Endpoints currently under continuous 24/7 protection
>99%
Ransomware detection accuracy with patented behavior analytics engine
FAQs about Real-Time Threat Detection
What is real-time threat detection?
+-Real-time detection is the continuous monitoring of endpoint and system activity to instantly identify and respond to threats as they occur. Unlike periodic scans, it uses behavior analysis and machine learning to detect anomalies, such as unauthorized file changes, privilege escalations, or lateral movement, often catching zero-day and fileless attacks that signature-based tools miss.
Read moreWhat are the benefits of real-time threat detection?
+-Real-time threat detection enables faster identification and containment of threats before they cause damage. It helps detect advanced threats like zero-day exploits, ransomware, and fileless malware in their early stages. This reduces incident response time, limits lateral spread, and minimizes business disruption. It also improves threat visibility, supports compliance, and strengthens overall security posture.
Read moreWhat is the difference between traditional antivirus and NextGen antivirus?
+-Traditional antivirus solely utilizes signature-based detection, scanning files for known malware patterns. Next-Gen Antivirus (NGAV) on the other hand use AI/ML-driven behavioral analysis to detect unknown threats, including zero-day attacks, fileless malware, and ransomware.
Read moreHow much impact does the solution have on the system performance?
+-Malware Protection Plus is designed to be lightweight, running efficiently in the background without consuming excessive resources. It minimizes system impact by leveraging cloud-based processing and utilizing edge scanning (local scanning) to ensure continuous protection without affecting user experience.
Read moreHow does Malware Protection Plus detect threats?
+-Malware Protection Plus employs a combination of AI/ML algorithms, behavioural detection and real-time threat analysis. These mechanisms enable the detection of unknown threats and fileless attacks without patient zero.
Read moreIs Anti-ransomware included in Malware Protection Plus?
+-Yes, anti-ransomware features are typically a subset of NGAV, focusing specifically on detecting and mitigating ransomware attacks. Malware Protection Plus offers protection coverage for all threats, including ransomware attacks.
Read more