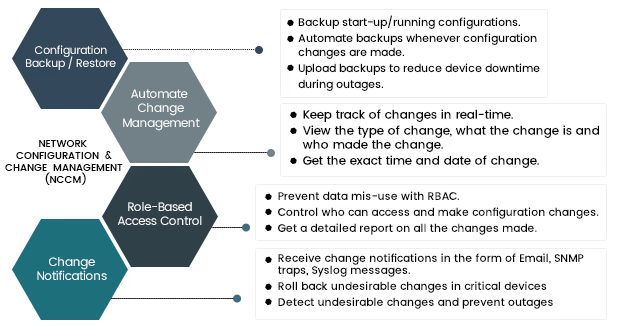
The essential components of network configuration and change management (NCCM)
Effective Network configuration and change management (NCCM) involves several key components that help maintain a secure, efficient, and compliant network. Here are the essential elements:
Configuration backup and restore
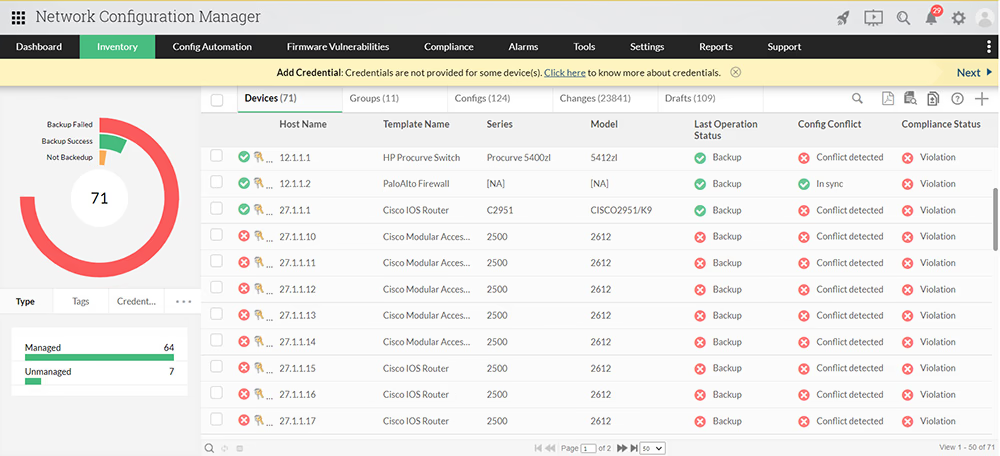
Backups are the foundation of network stability. Without regular configuration backups, recovering from a misconfiguration, device failure, or cyberattack can be a time-consuming and costly process. NCCM solutions automate configuration backups, ensuring that the latest versions are stored securely. In case of a failure, administrators can quickly restore a known working configuration, minimizing downtime and reducing operational risk.
Automating change management
Manually handling configuration changes across multiple network devices is not only tedious but also prone to human error. Automating change management streamlines the process by enabling bulk updates, scheduled deployments, and pre-configured templates. This ensures that changes are implemented consistently across all devices while reducing the likelihood of misconfigurations. Additionally, automation helps enforce compliance by allowing only authorized changes to take place.
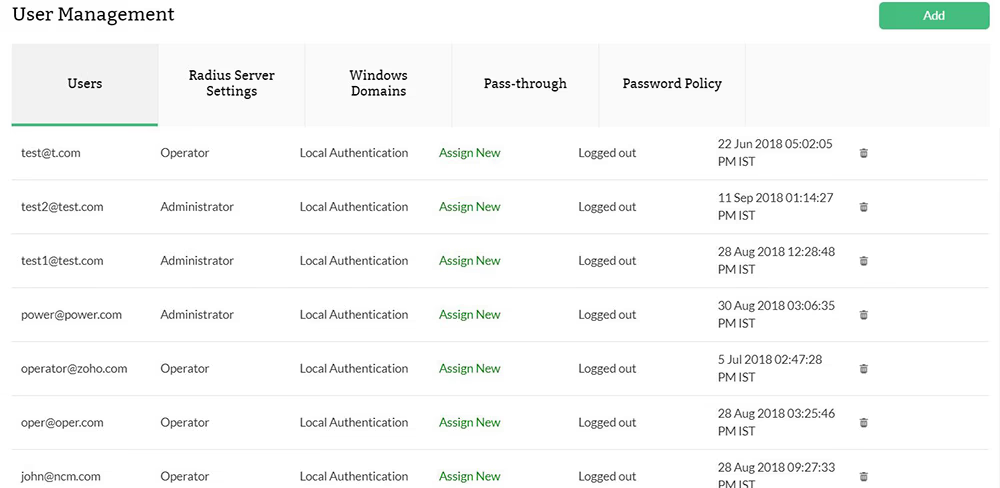
Role-based access control (RBAC)
Unrestricted access to network configurations increases the risk of accidental or unauthorized changes. Role-Based Access Control (RBAC) ensures that only specific users or teams can modify configurations based on predefined permissions. For example, junior administrators may have read-only access, while senior engineers can approve and apply configuration changes. This prevents unauthorized modifications and enhances security by restricting access to critical network settings.
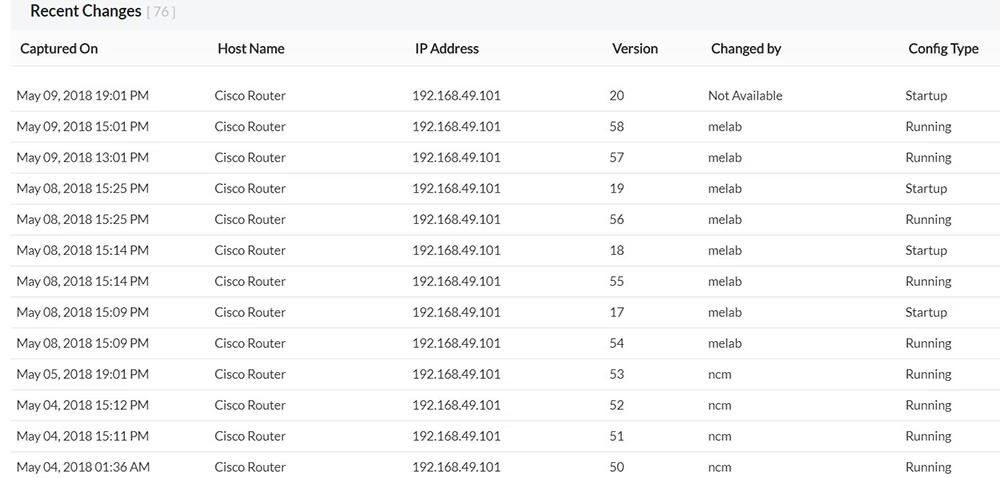
Real-time change notifications
Even with strict policies in place, unauthorized or unexpected changes can occur. NCCM solutions provide real-time change notifications to alert network administrators whenever a configuration is modified. These alerts help in quick incident response, allowing admins to investigate and take corrective actions before issues escalate. Notifications can be integrated with IT service management (ITSM) tools, enabling seamless tracking of changes and compliance reporting.
By incorporating these essential components, NCCM not only simplifies network operations but also strengthens security, improves compliance, and minimizes downtime.