-
Restrict the use of unsafe web apps
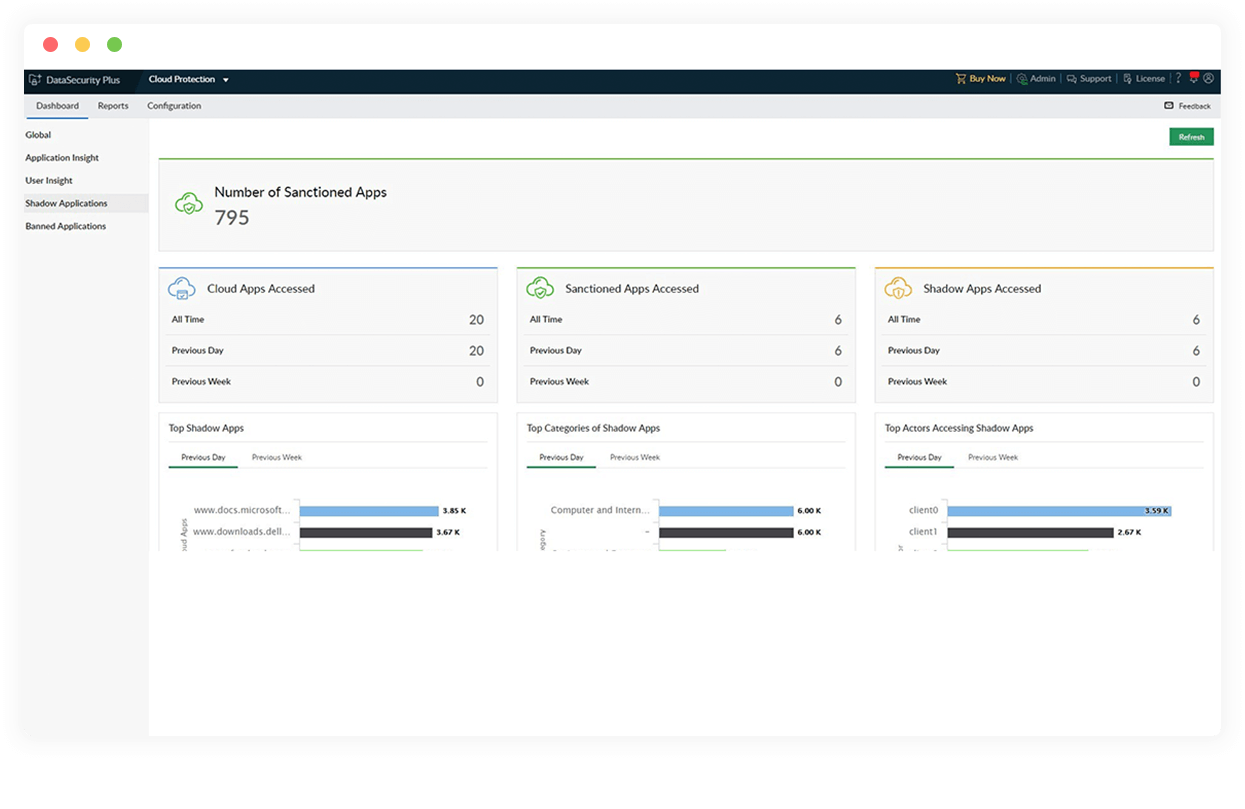
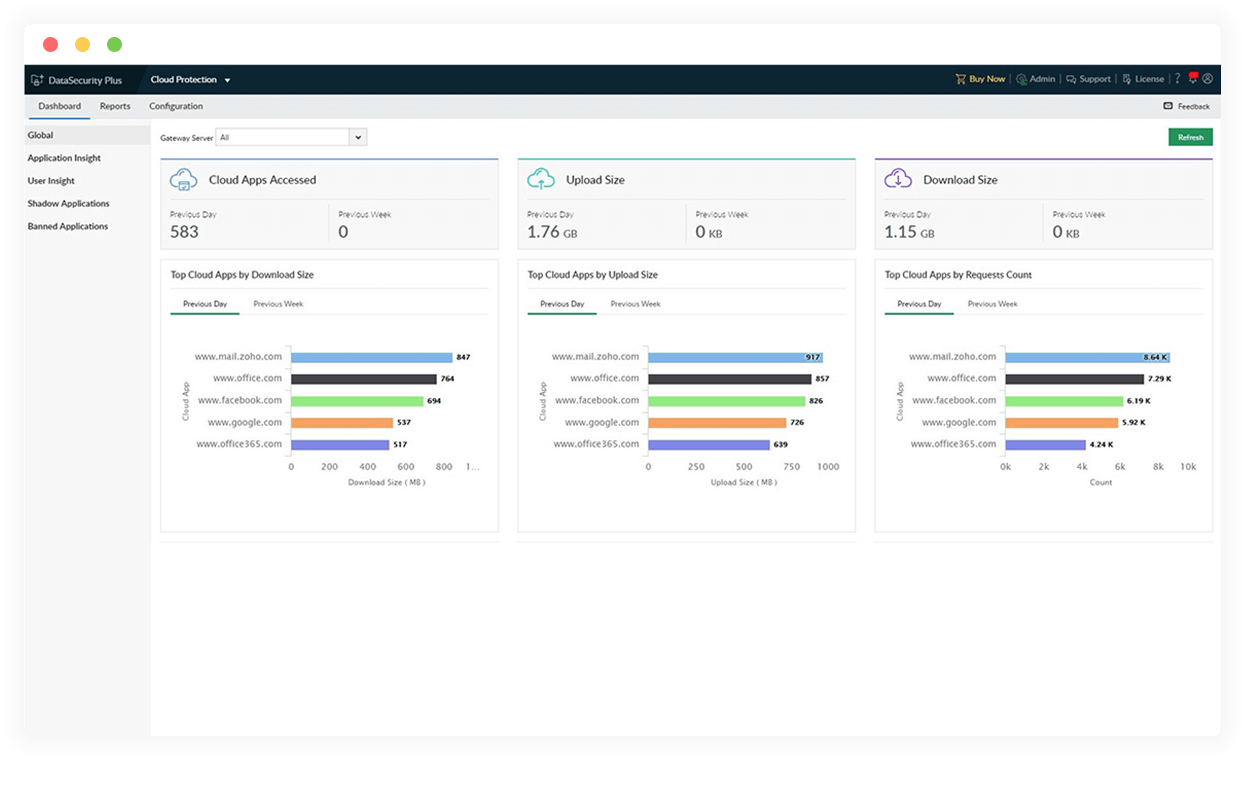
Track low reputation cloud apps used in your organization to analyze the risk they pose, and add these apps to your block list to deny access to them.
-
Reduce cloud attack surface
To strengthen your organizations' cloud security posture, periodically review and block known domains that host exploit kits, deliver malicious payloads, and more.
-
Ensure safe web experience
Enforce the use of only safe cloud applications, i.e. those with adequate encryption levels and trustworthy third-party certificates.
-
Block irrelevant web applications
Scrutinize the websites accessed most often, and block those deemed unproductive and harmful to your workforce.
Monitor cloud app use and effortlessly block malicious cloud applications with our cloud protection software.