-
USB management tool
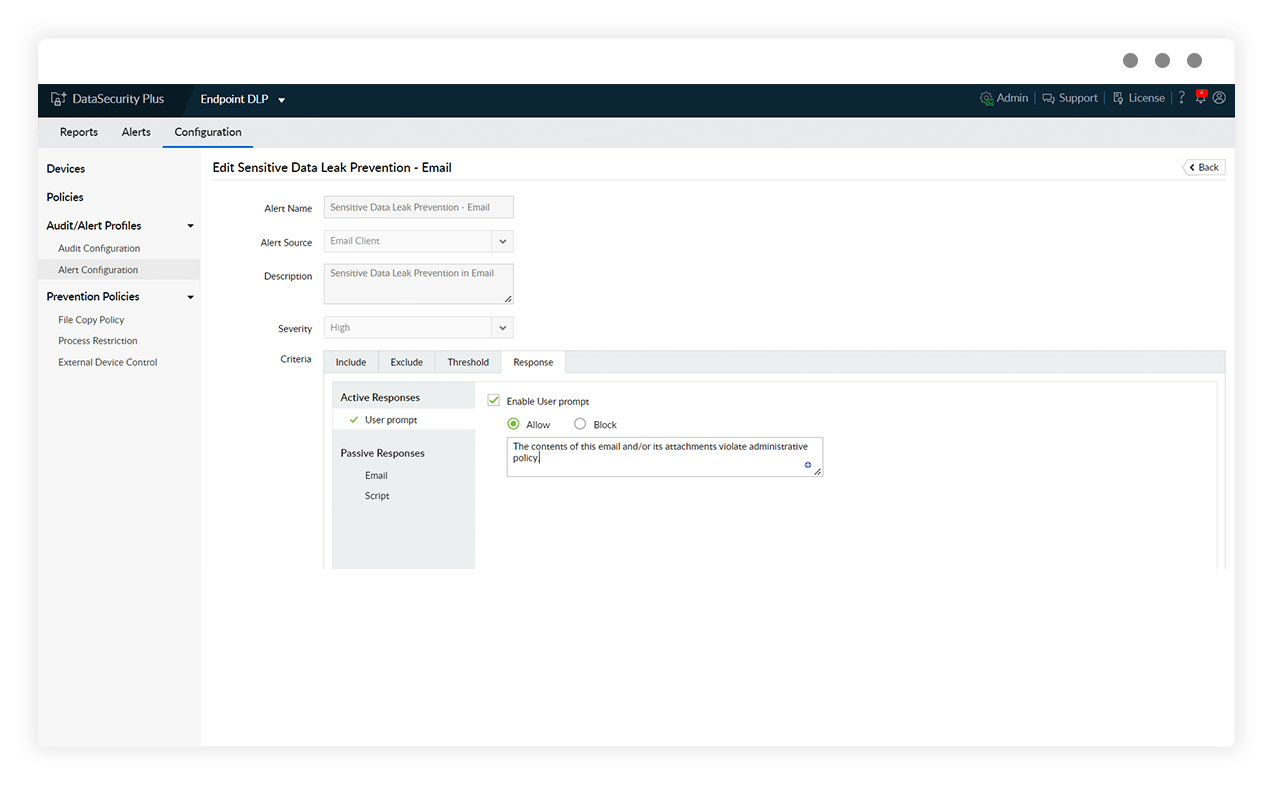
Enforce a strict protocol that tracks and stops the movement of files classified as highly sensitive. Generate instant emails to your stakeholders with relevant details on USB usage.
-
Prevent USB data theft
Make USBs read only or restrict the use of clipboards to prevent file copy actions across local devices to minimize the risk of data theft via USBs.
-
Block suspicious USB devices
Create detailed blocklists containing unvetted and suspicious USBs. These devices will be blocked outright and users will be unable to carry out any activities using them.
-
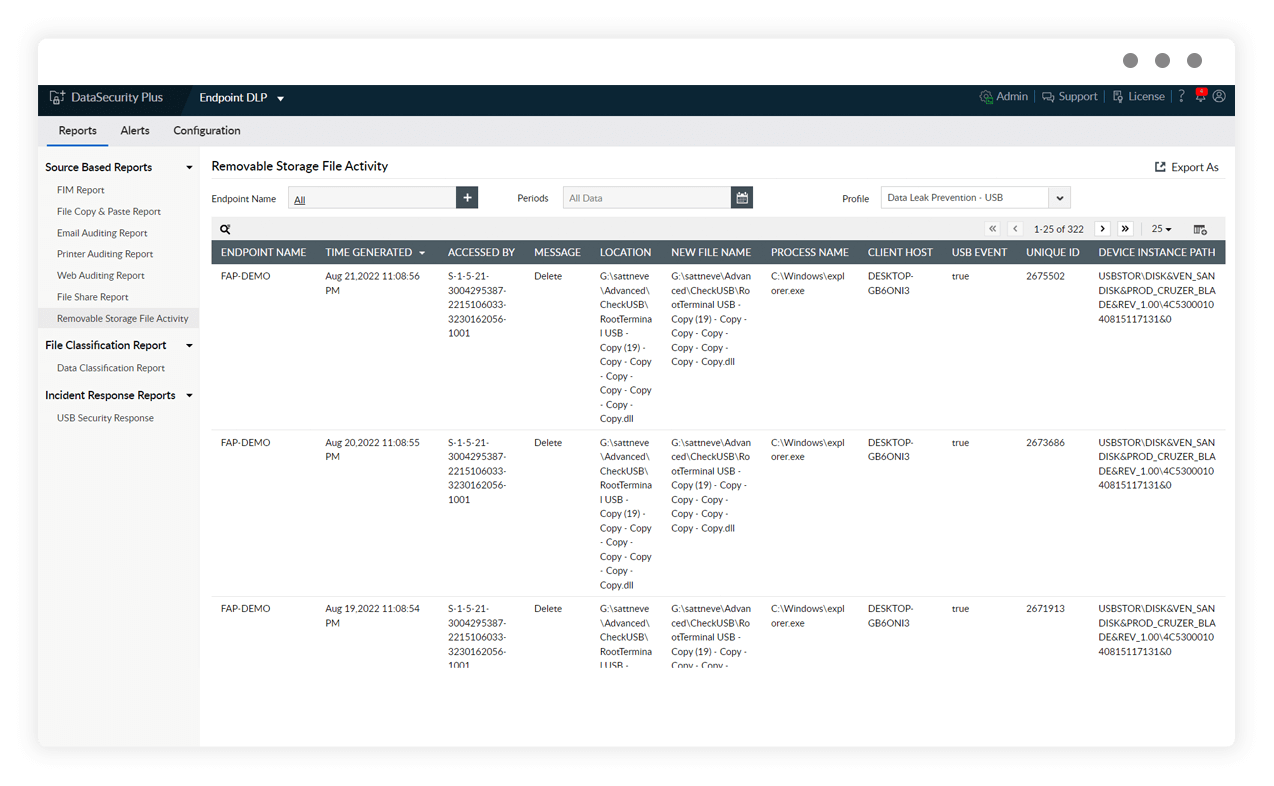
Audit removable device usage
Track move, rename, delete, modify, copy, and paste activities across USBs with details on device instance paths, when modifications were made, who made them, etc.
Centralize the management of USB devices using our data leak prevention software.