-
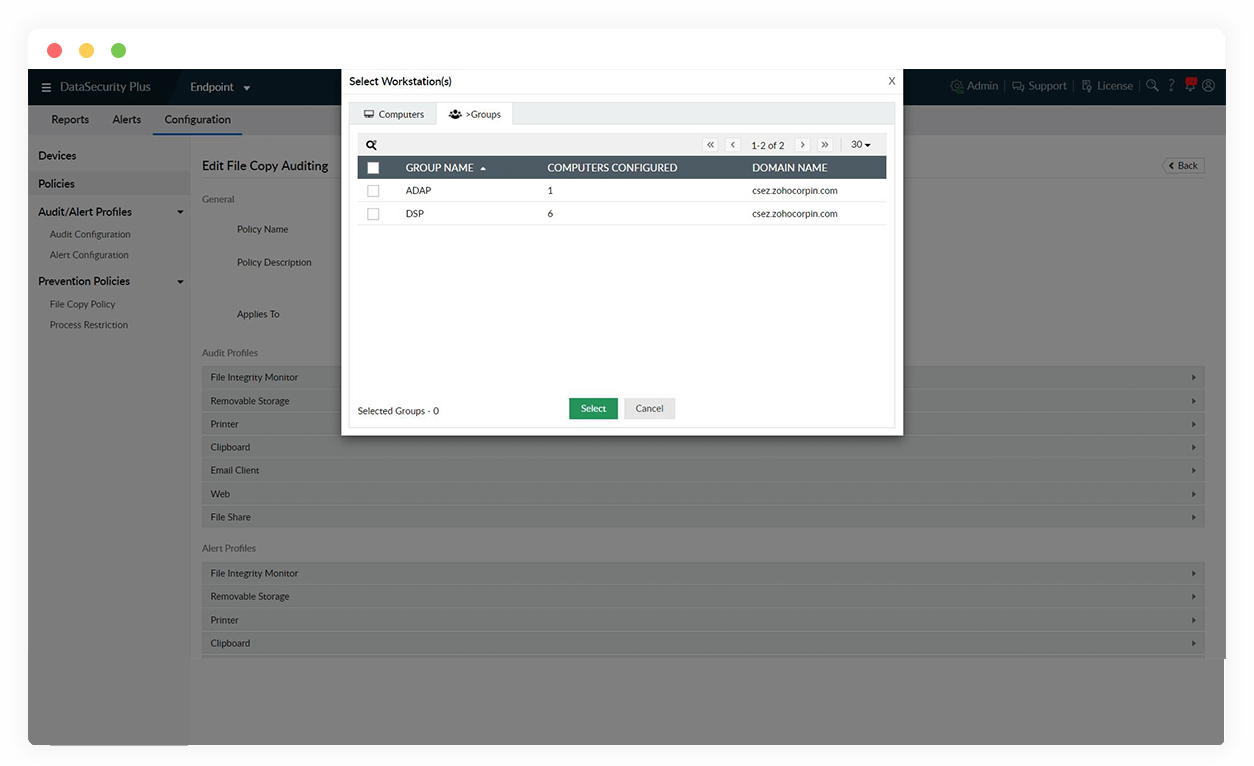
Anti-file-copy software
Monitor files copied in real time, and prevent the unwarranted transfer of critical data across local and network shares.
-
USB data copy protection
Prevent the unauthorized sharing and transfer of your organization's critical data across multiple devices including mobile phones, USBs, etc.
-
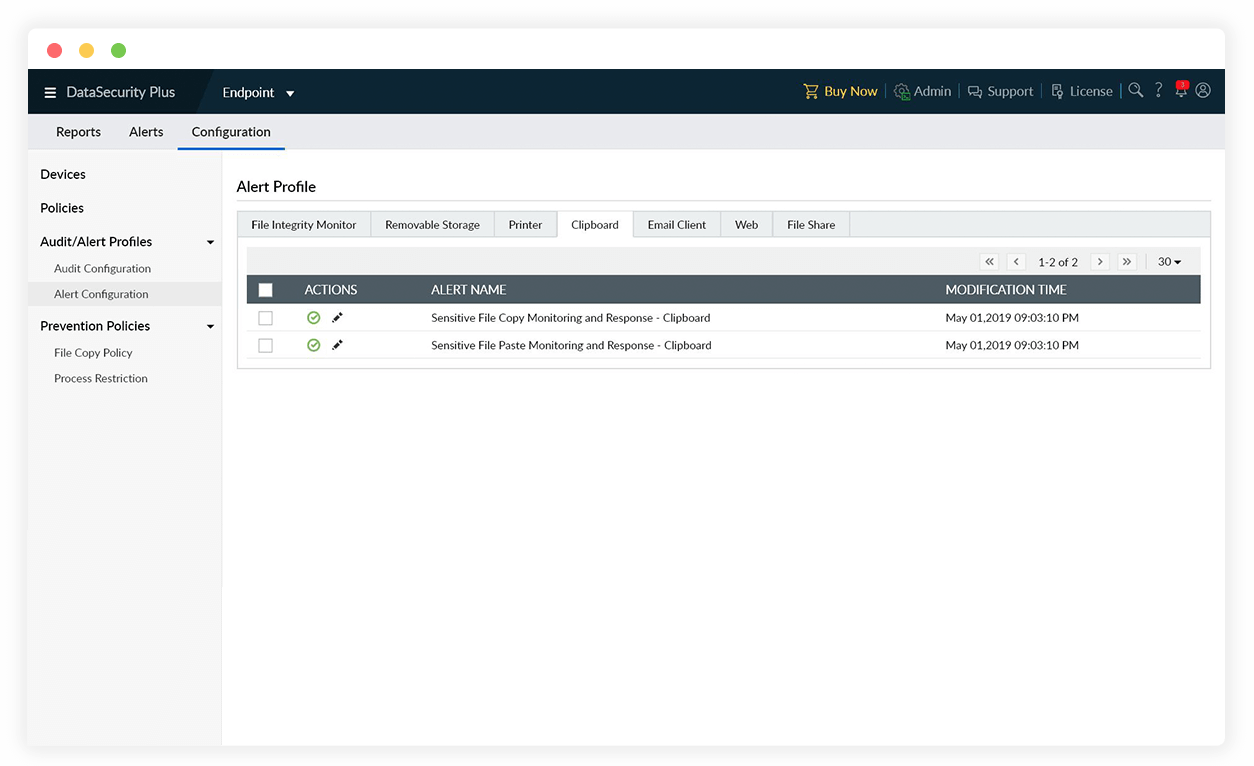
Automated system response
Use quick and interactive system prompts to warn users of policy violations when they attempt to copy critical files.
-
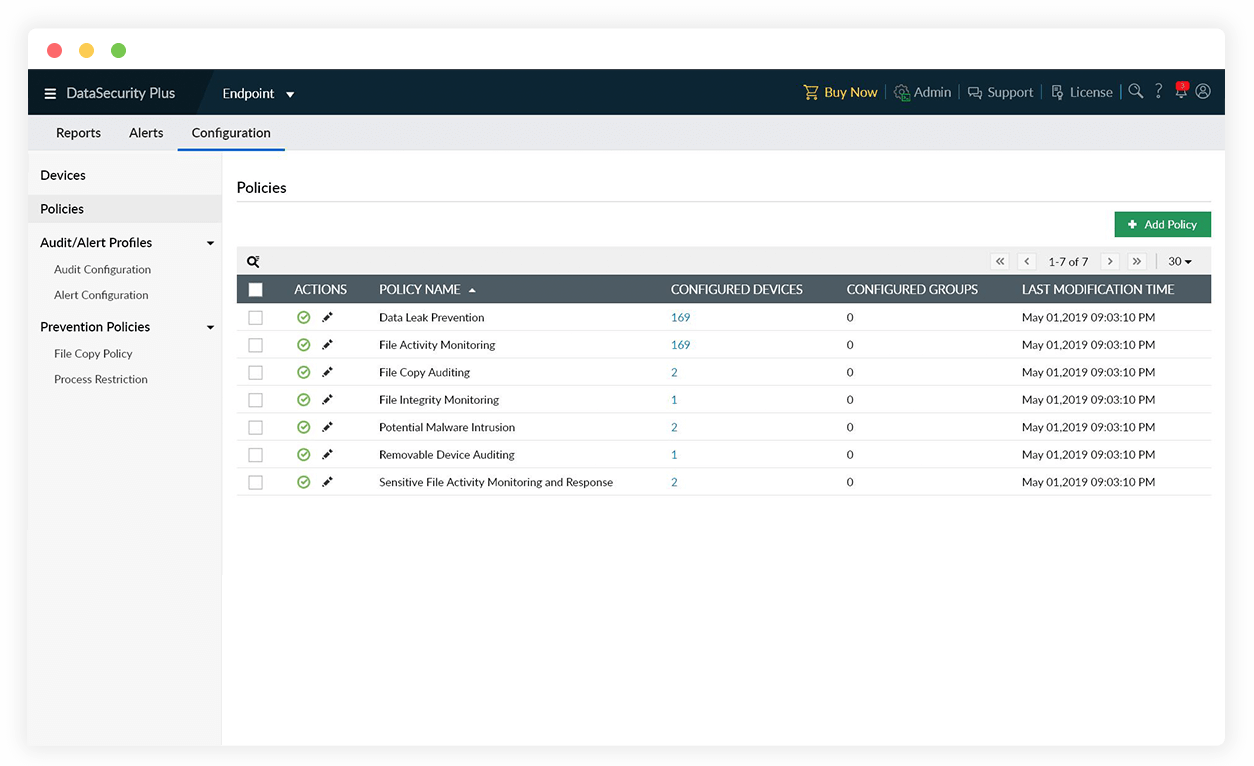
Audit file copy events
Track and analyze all attempts made by your employees to copy files, including failed ones using our copy protection software.
Detect and prevent sensitive data leaks via USB devices, email, and more using our data leak prevention tool