-
Track data access
Perform real-time file access auditing across Windows file servers and failover clusters with in-depth details on who accessed what, when, and from where.
-
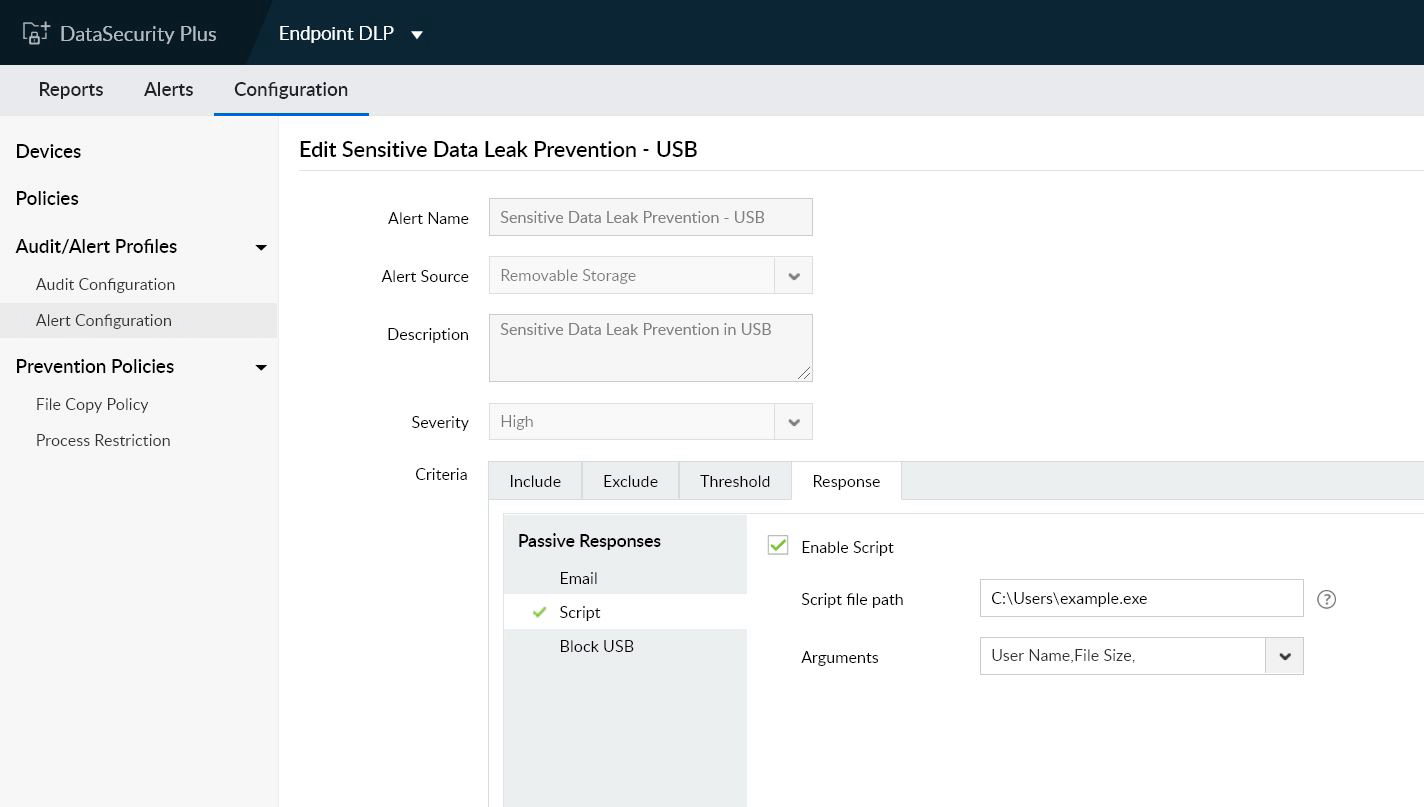
Detect access anomalies
Spot, notify about, and respond to sudden spikes in high-risk file actions such as deletion, permission change, and copy paste, as they could indicate privilege abuse.
-
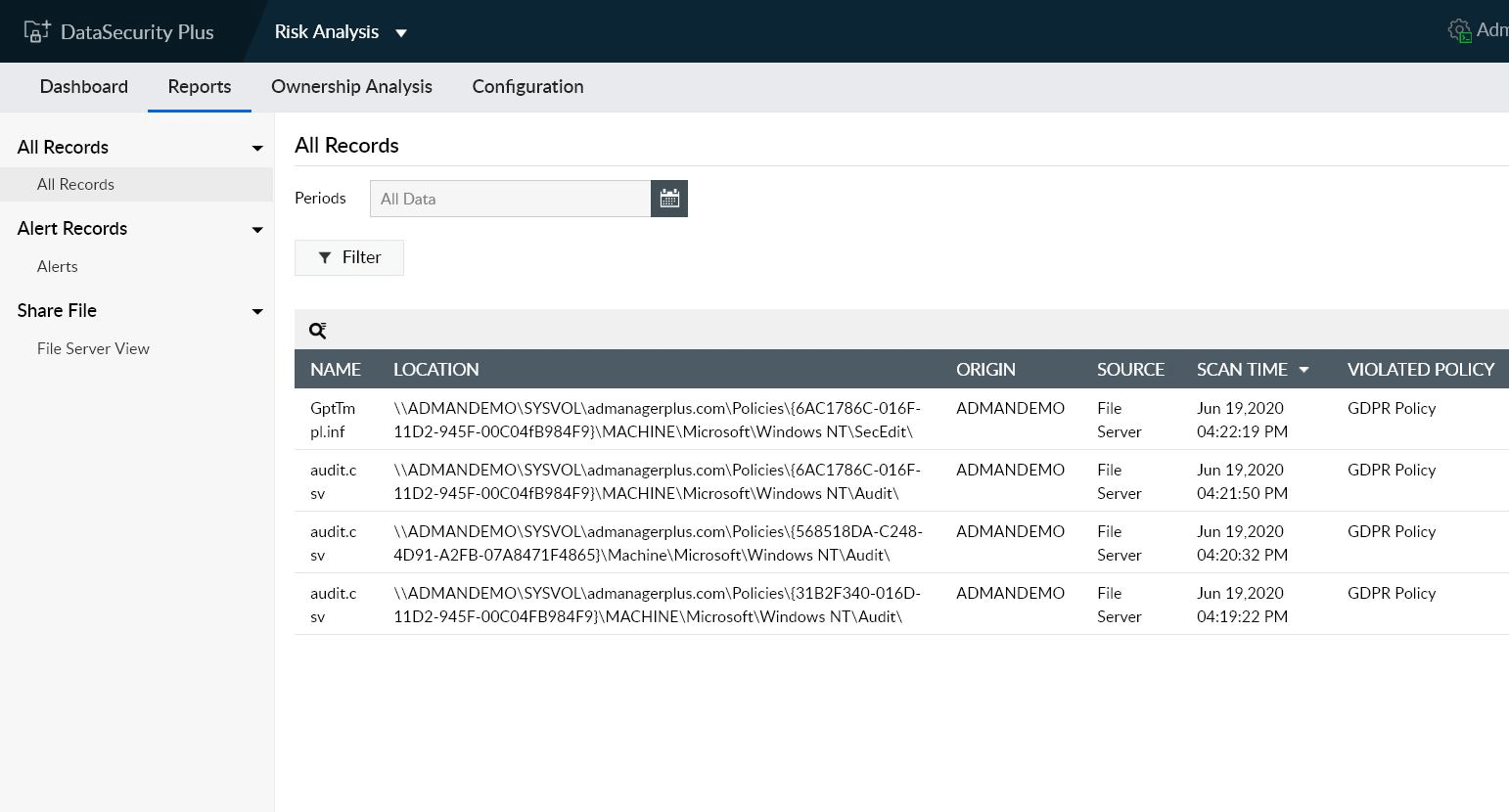
Monitor file integrity
Maintain a complete audit trail of changes made to your critical data, and maintain the necessary security, compliance, and operational standards.
-
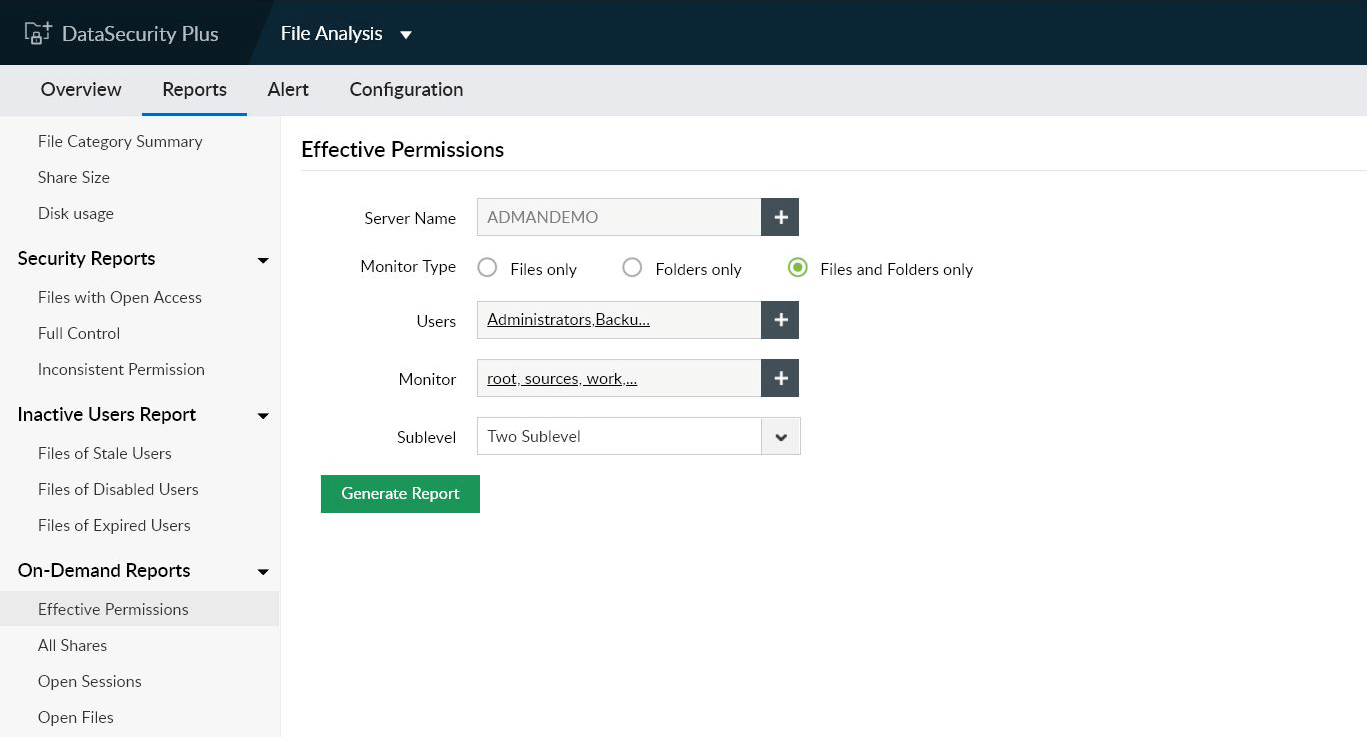
Perform risk assessments
Find corporate data that's the most vulnerable to security attacks such as files with open access, with inconsistent permissions, or owned by stale users.
Experience advanced data security and visibility with DataSecurity Plus.