-
Stop data theft via email
Spot and instantaneously block emails (Outlook) that contain highly confidential files and folders as attachments.
-
Detect insider activities
Track indicators of malicious insiders like unexplained spikes in failed file accesses, permission change activities, and more.
-
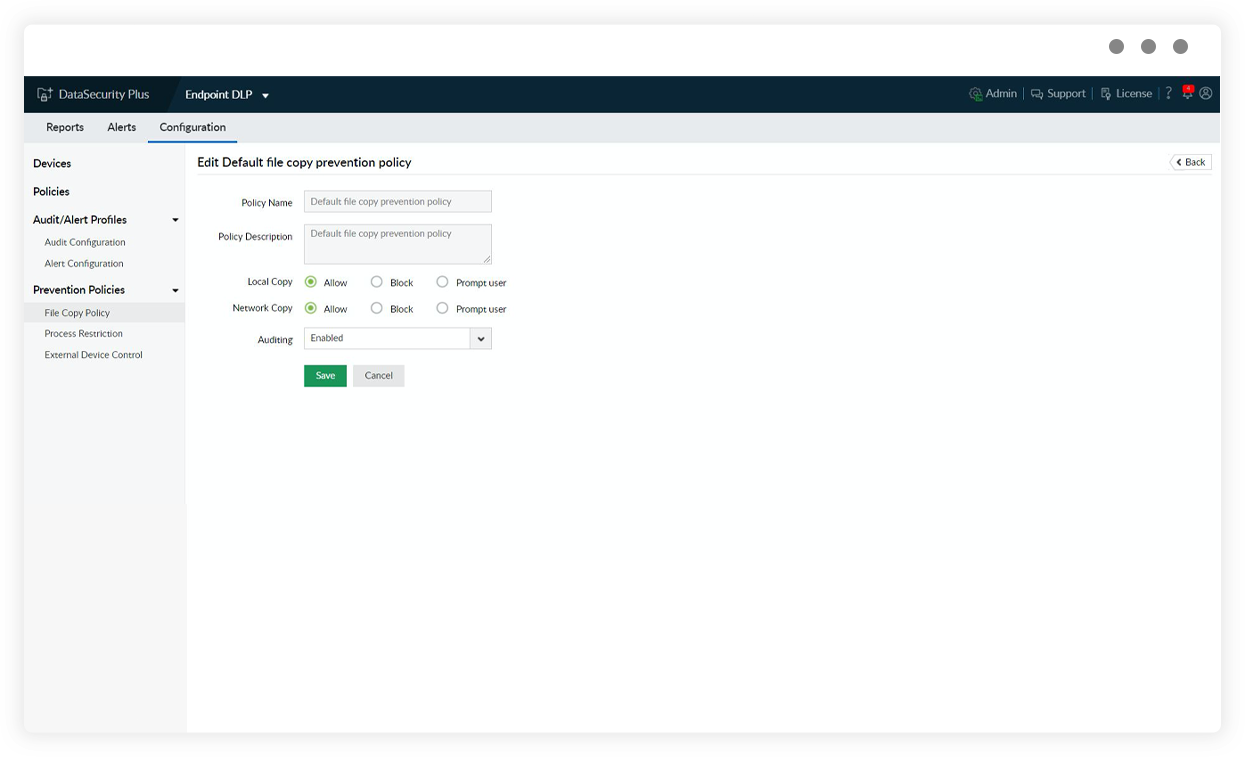
Proactive data theft prevention
Defend against data leaks by blocklisting suspicious USB devices, denying write access to USBs, blocking emails with sensitive files in attachments, and more.
-
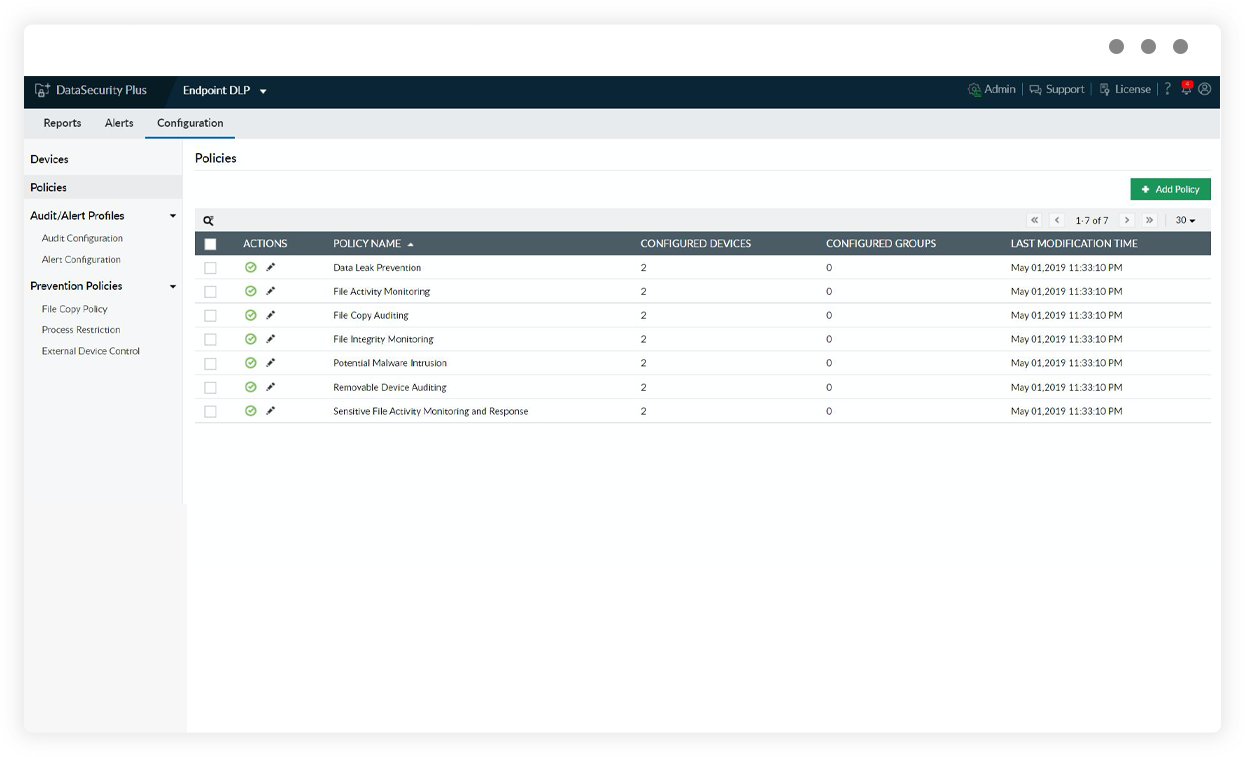
Employ an integrated DLP solution
Detect threats to your sensitive data quickly using integrated DLP software that can discover and classify PII and ePHI, monitor file integrity, enforce content-aware protection, and more.
Ensure the integrity and security of your organization's data using our DLP software.