-
Prevent data theft via USBs
Block certain capabilities like write and execute access in removable storage devices to prevent unauthorized data theft attempts by malicious insiders.
-
Enable content-aware protection
Track and block the movement of confidential data as attachments in email clients (Outlook). Also, employ user prompts to warn employees regarding data loss prevention (DLP) policy violations.
-
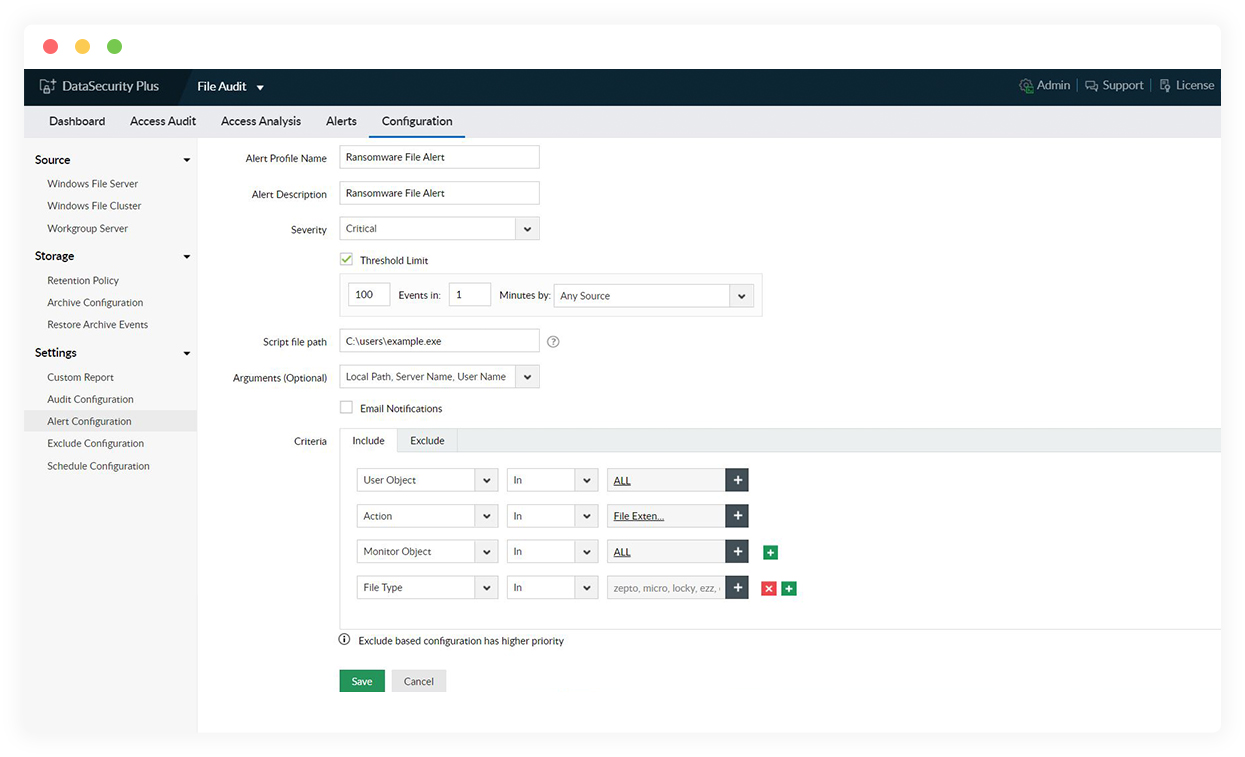
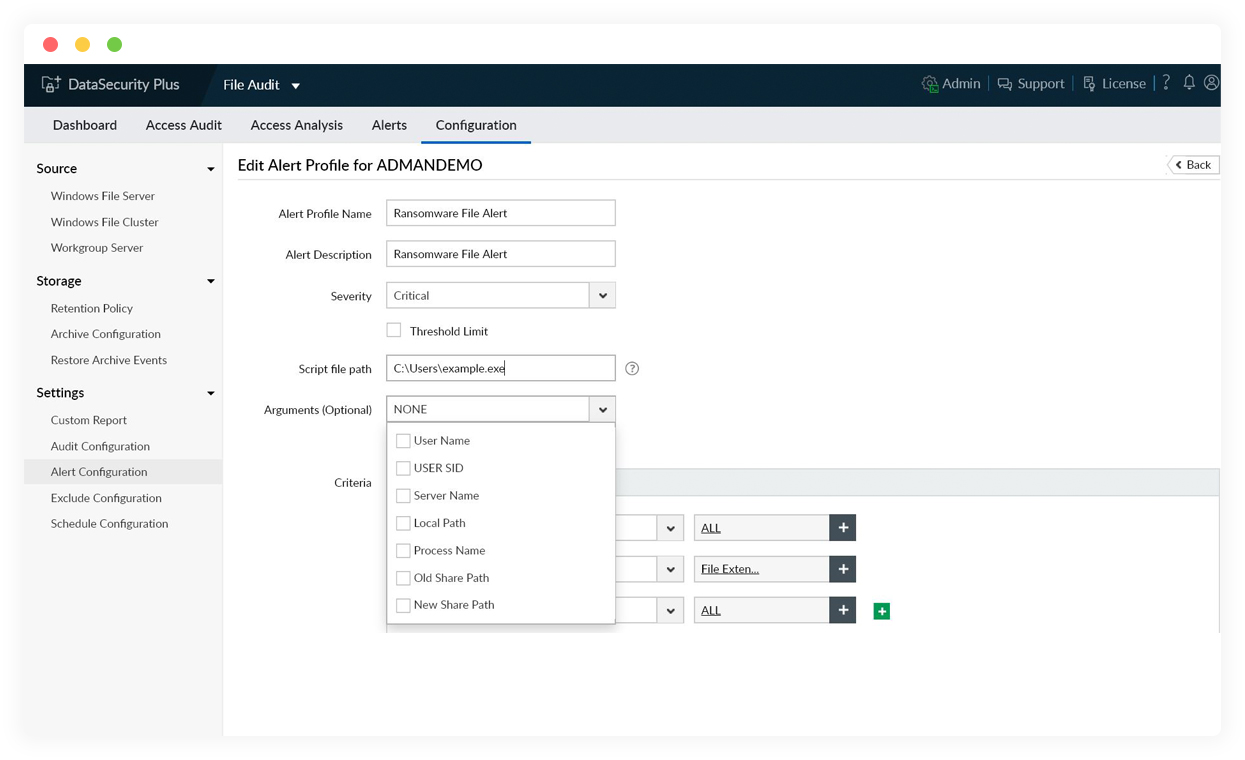
Use predefined DLP policies
Apply the various built-in data leak prevention policies to monitor file integrity, detect possible malware intrusions, track the movement of sensitive data, and more.
-
Enable file copy protection
Audit both Ctrl+C and right-click file copy activities. Block unwarranted file copy actions across local and shared folders.
Detect and protect sensitive personal data with our data leak prevention solution.