-
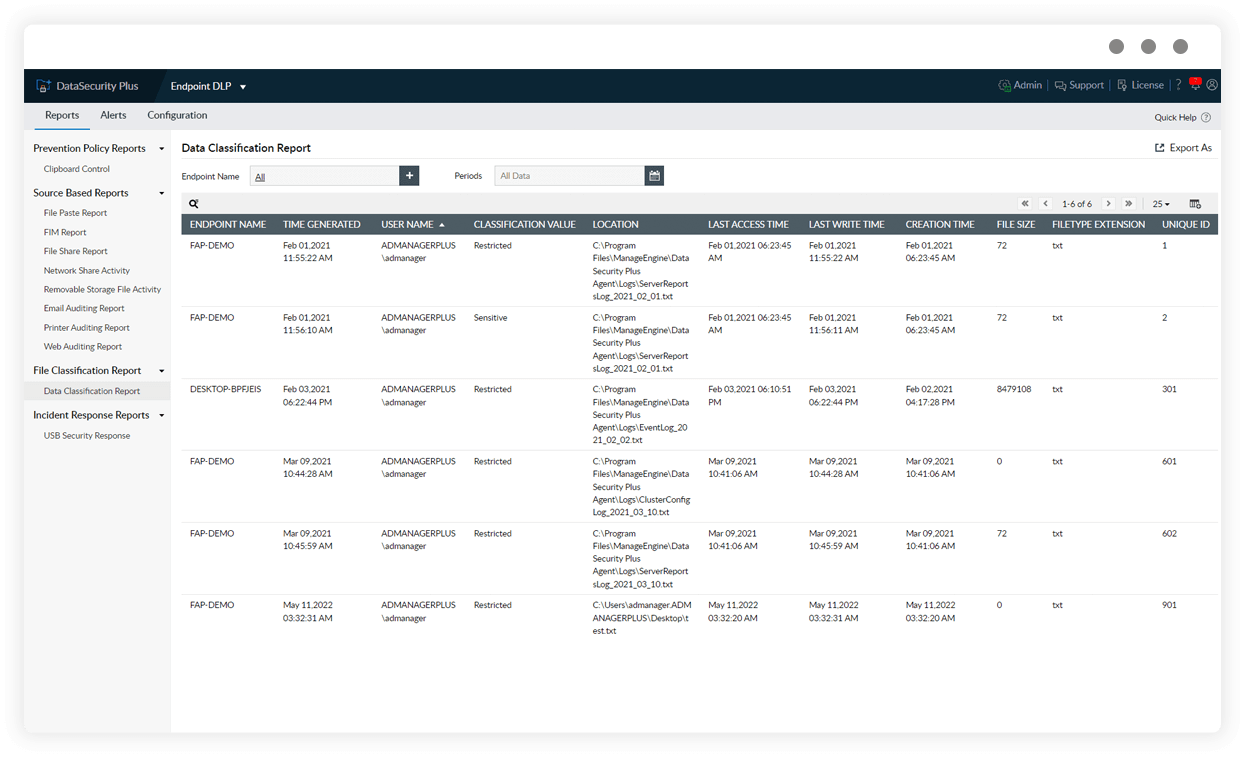
Classify files based on sensitivity
Classify files into various categories, such as Public, Internal, Sensitive, and Restricted, and know where your organization's critical data is located.
-
Surveil sensitive data
Spot anomalies in permissions and unauthorized modifications to sensitive data with our file integrity monitoring tool and track the movement of sensitive files with file copy monitoring.
-
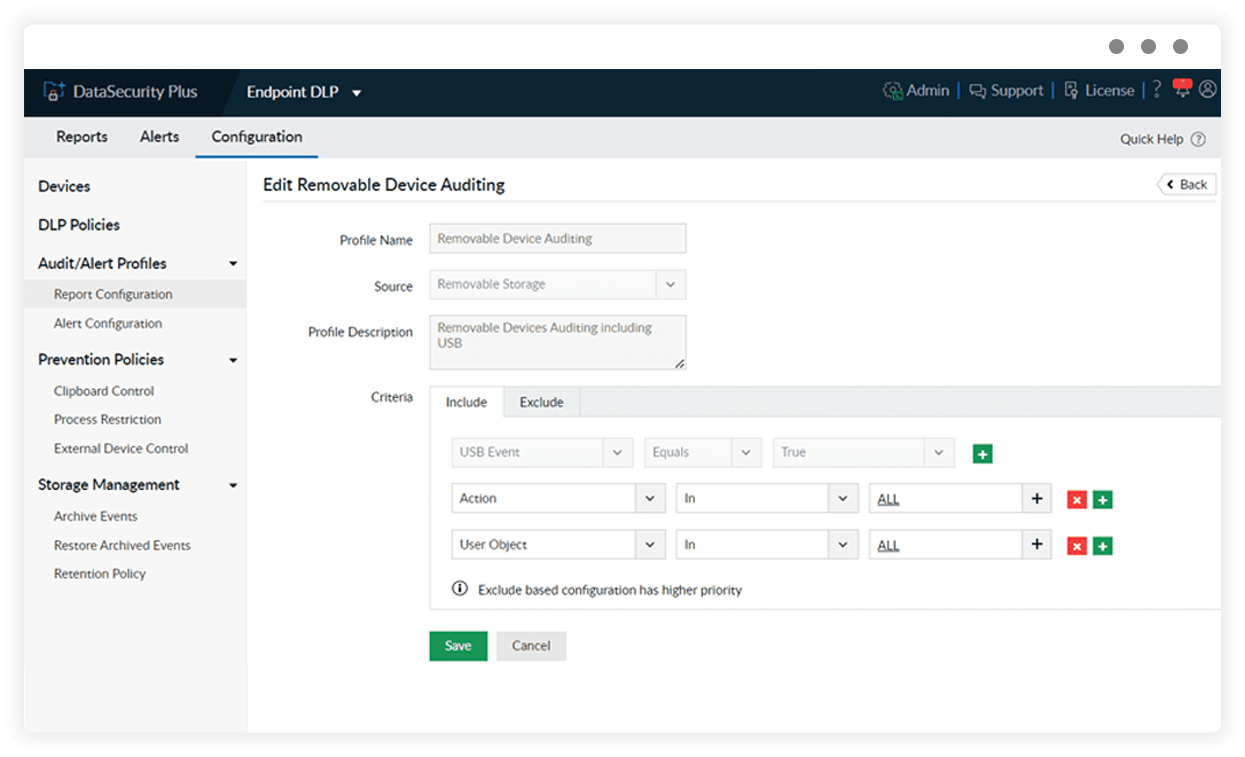
Audit removable storage
Track the transfer of sensitive and restricted data to and from USBs, cameras, printers, and other removable storage devices with our data leak detection tool's audit profiles.
-
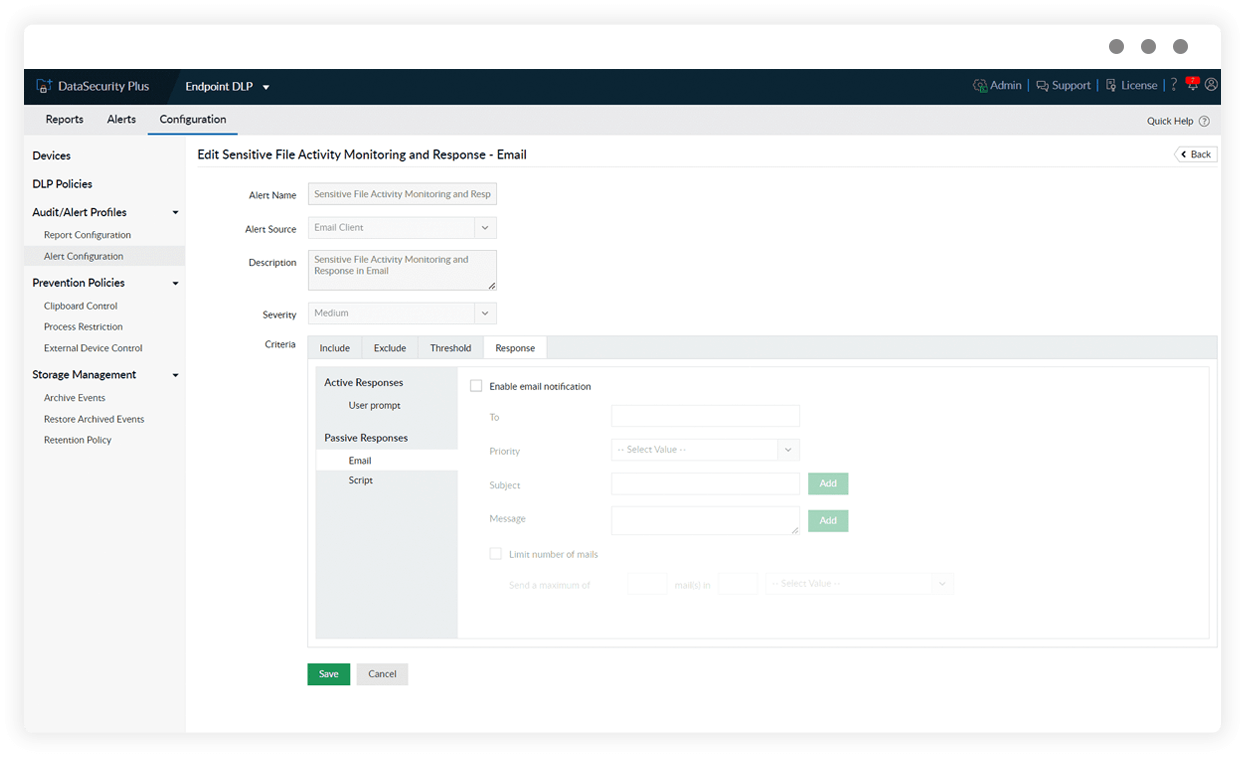
Respond to data leaks instantly
Configure alerts to get notified about potential data leaks and respond by restricting external devices, preventing file copying, employing user prompts, and implementing a myriad of other response actions with our DLP tool.
Detect data leaks instantly and don't let the sand drip through with data leak prevention software.