-
Predefined DLP policies:
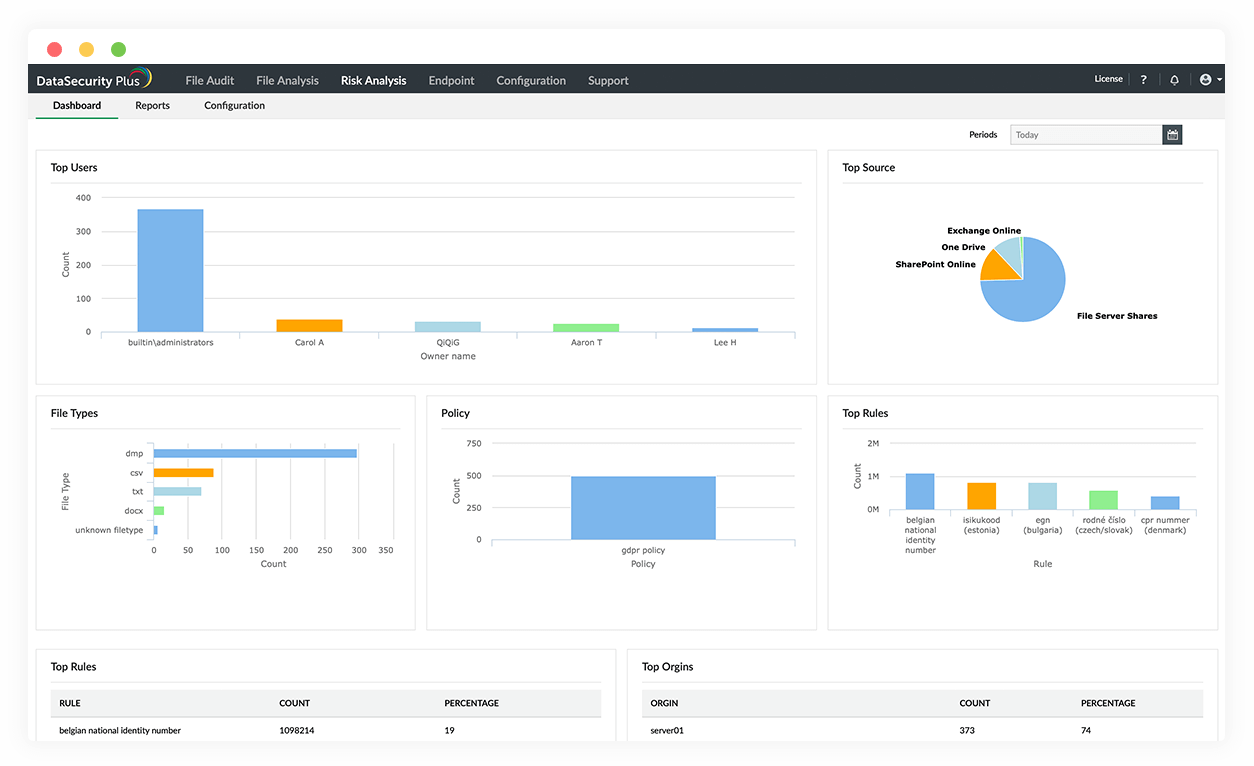
Set up and start securing your data easily with the data loss prevention tool's built-in alerting and response policies.
-
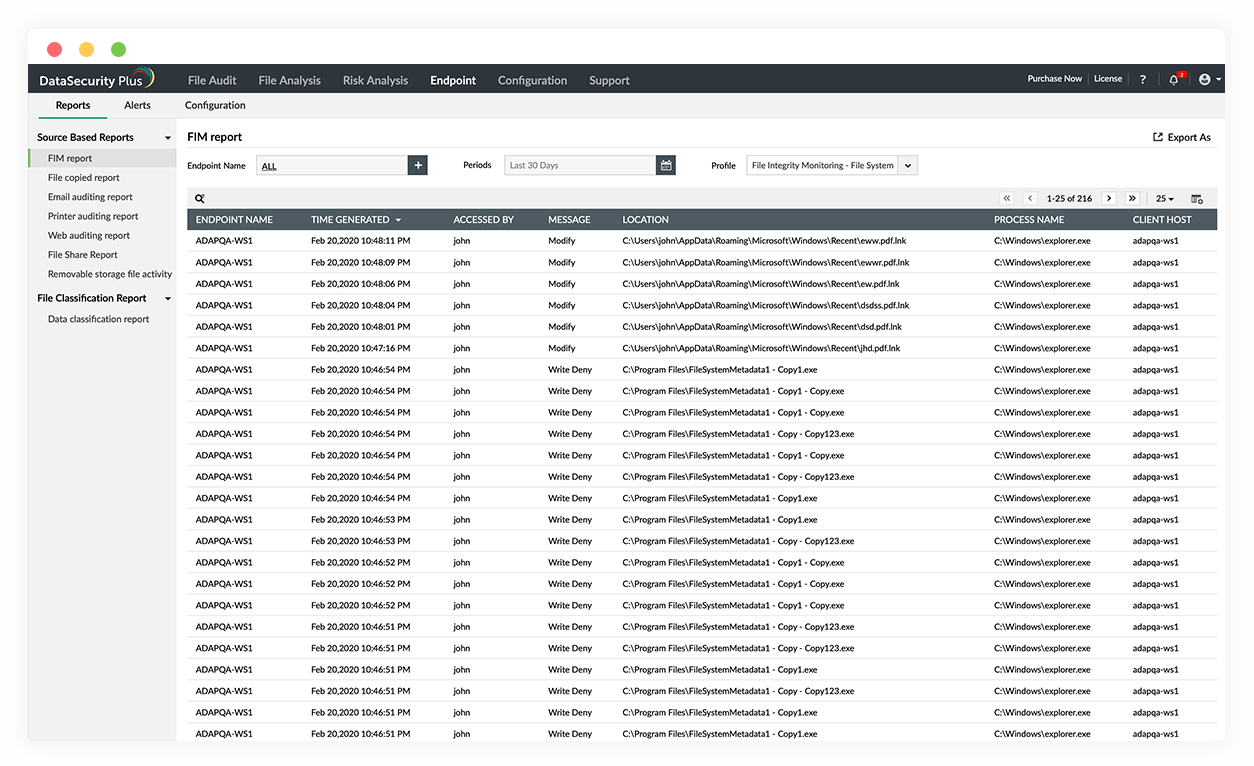
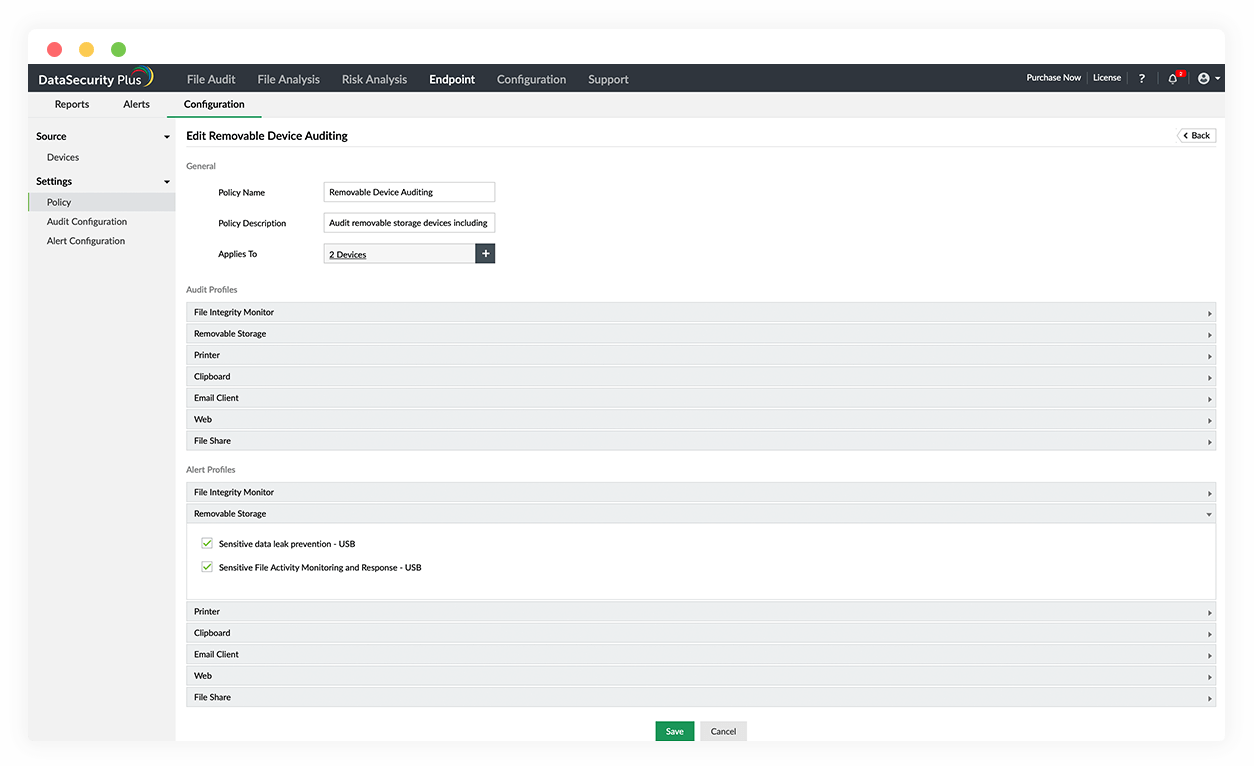
USB DLP:
Track USBs when they're plugged in, monitor file activity in removable storage media, and disrupt sensitive data transfers to USB drives.
-
Email DLP:
Monitor Outlook, and block users from performing unauthorized actions like attaching critical business data to emails.
-
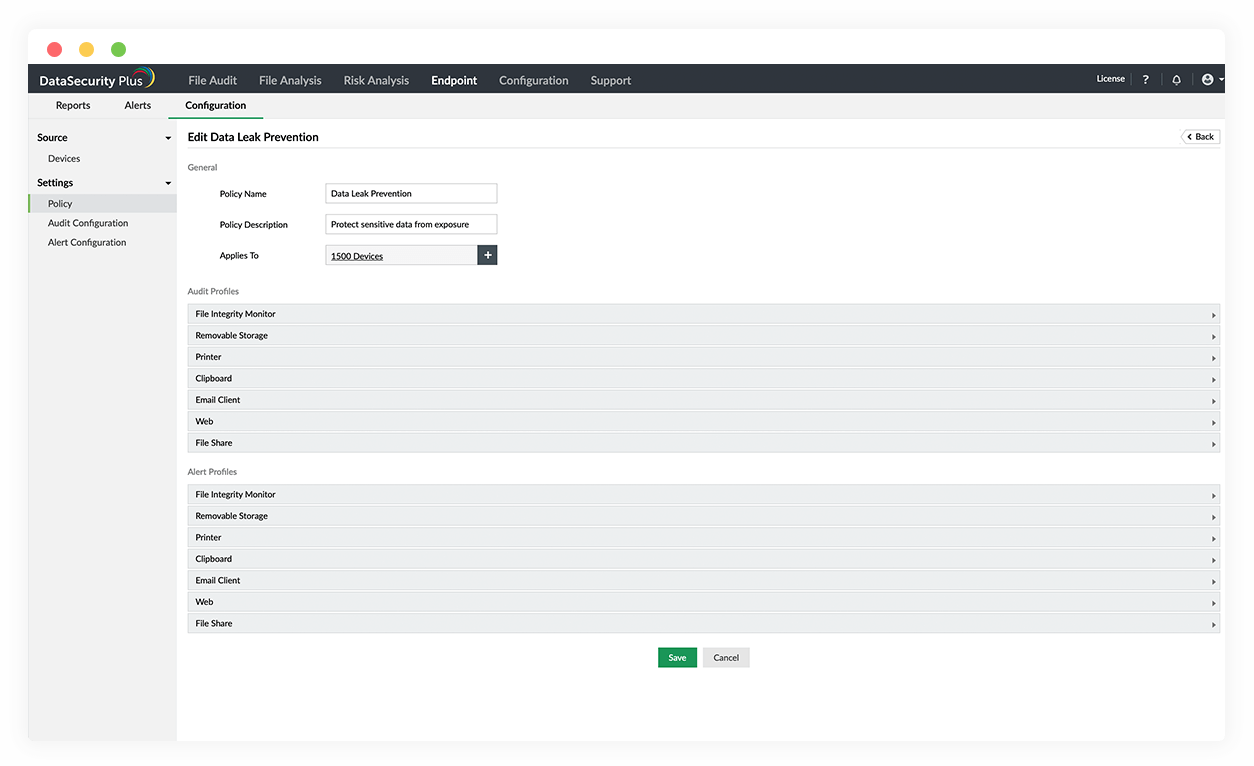
Automated incident response:
Create custom alerts and automate responses to potential security issues such as suspicious file copy events and ransomware infections.
Detect and respond to data exfiltration via endpoints with Data leak prevention software