-
Cohesive data protection software
Get a bird's-eye view of sensitive data across enterprise file storage, identify file access anomalies, and automate responses to security incidents.
-
Protect critical data
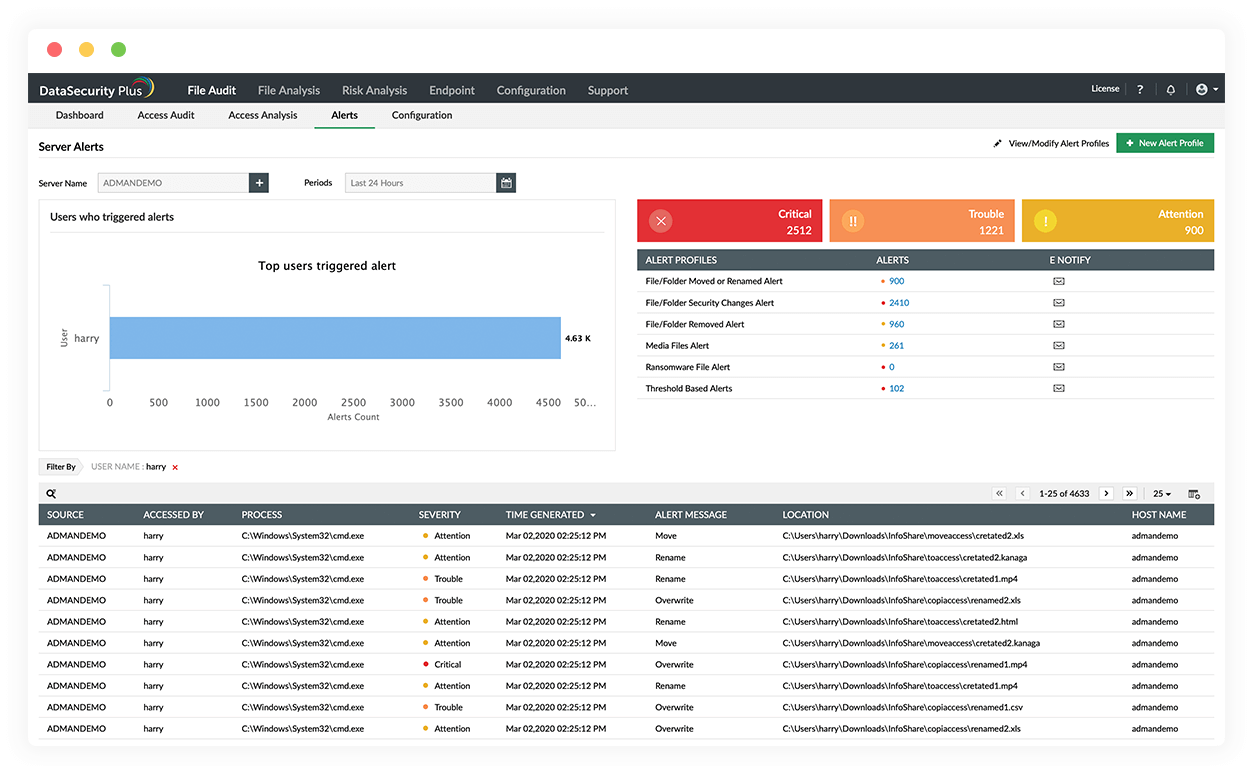
Classify data that requires the most stringent security—such as PII and ePHI—and set up the data protection tool to notify admins about any unauthorized use of this data.
-
Policy-based security
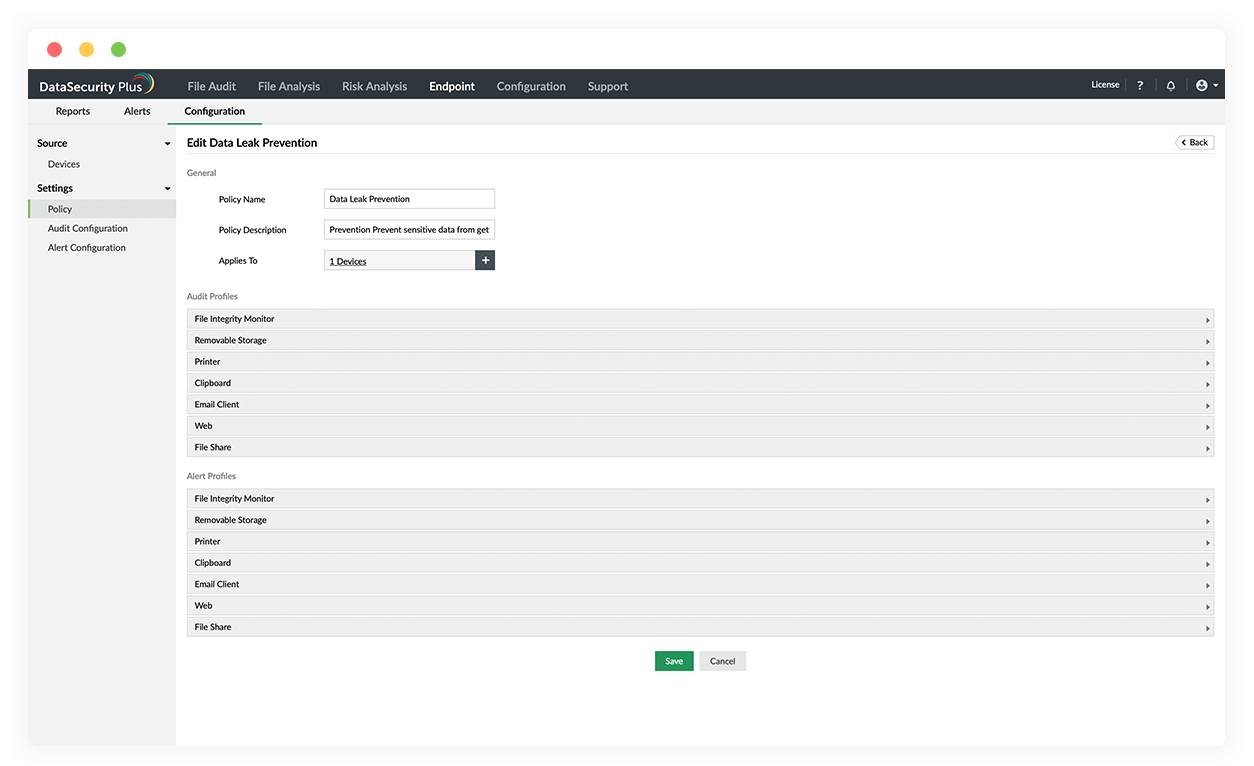
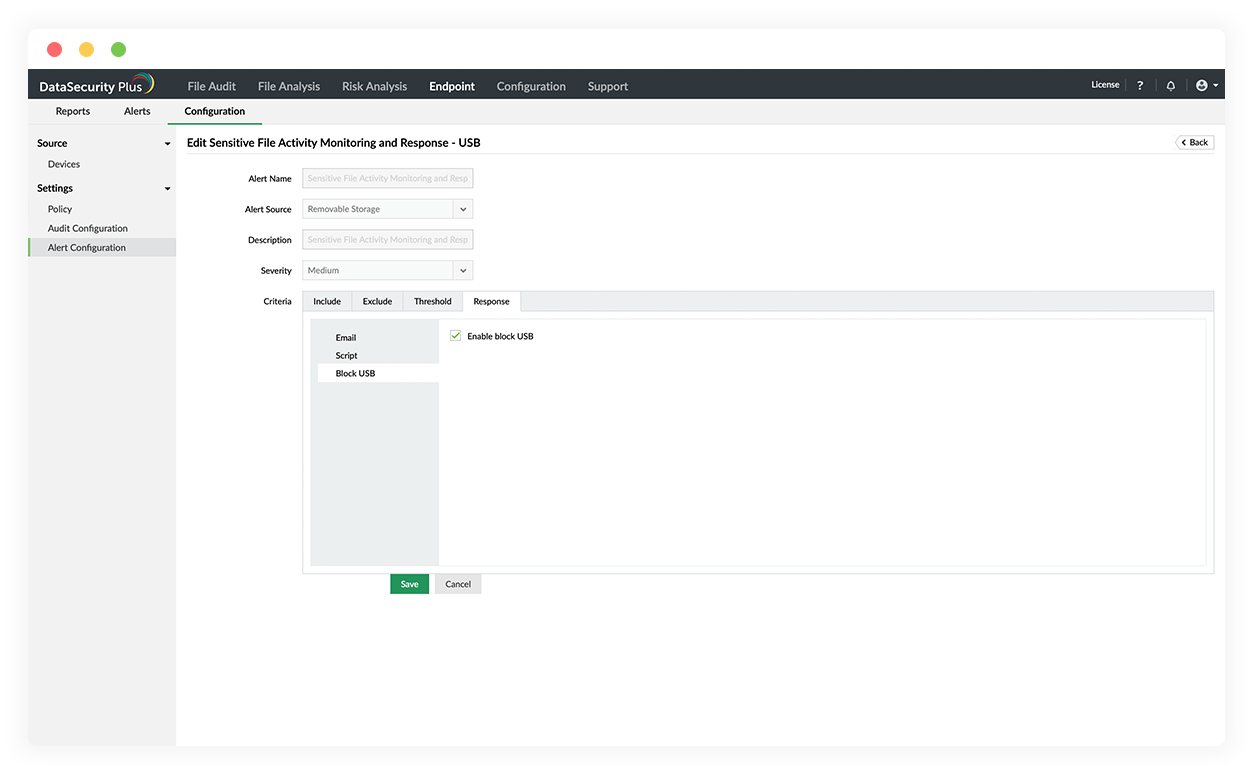
Deploy data protection policies to safeguard sensitive data from accidental or malicious leakage via removable storage devices and email attachments.
-
Check permission hygiene
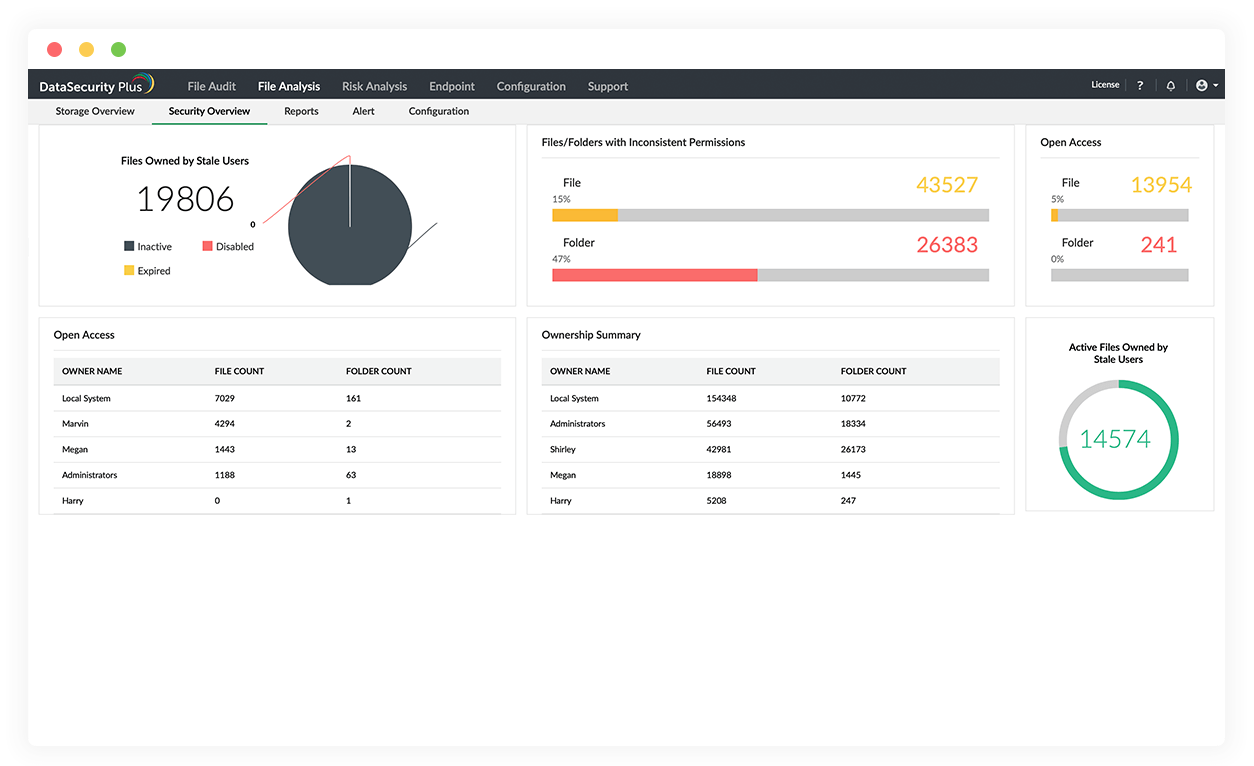
Analyze users' access rights to enterprise data, list effective permissions, and identify security vulnerabilities like files owned by inactive users.
Detect and respond to data exfiltration via endpoints with Data leak prevention software