-
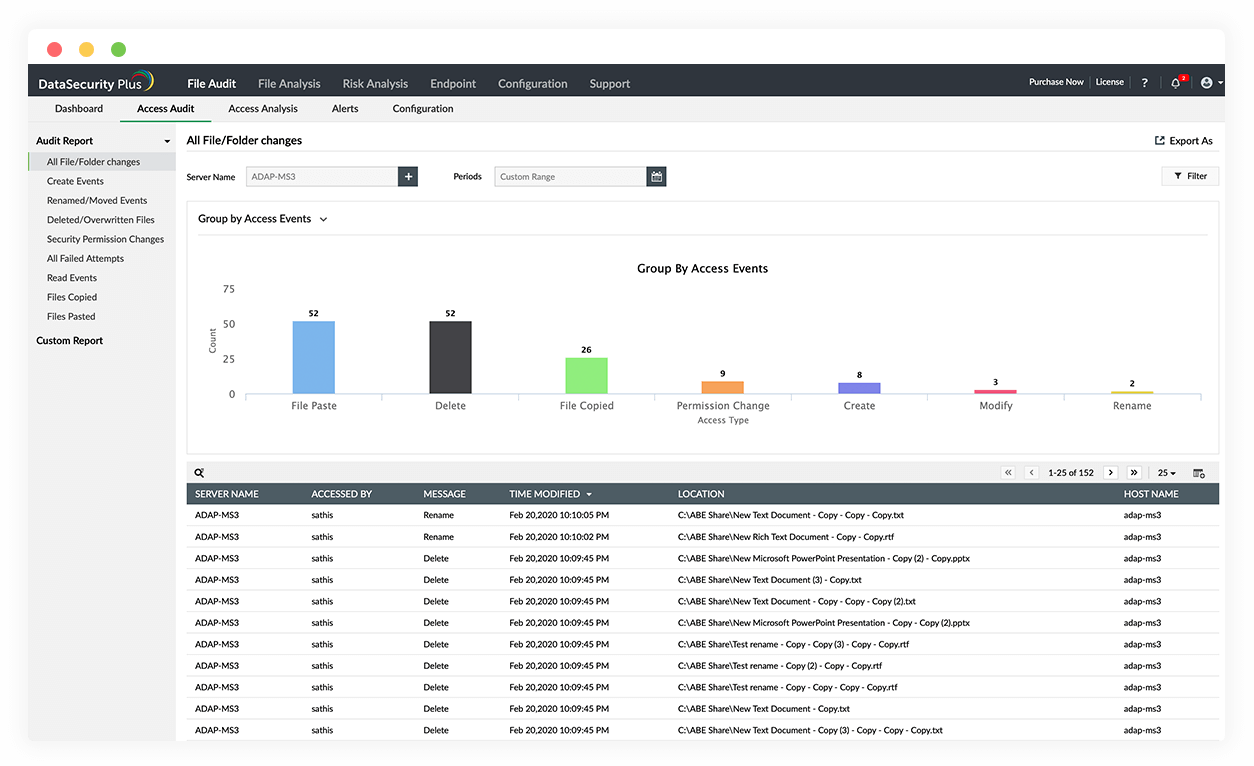
Monitor critical files
Ensure file server security by tracking file changes, analyzing file access trends, and verifying the integrity of critical files.
-
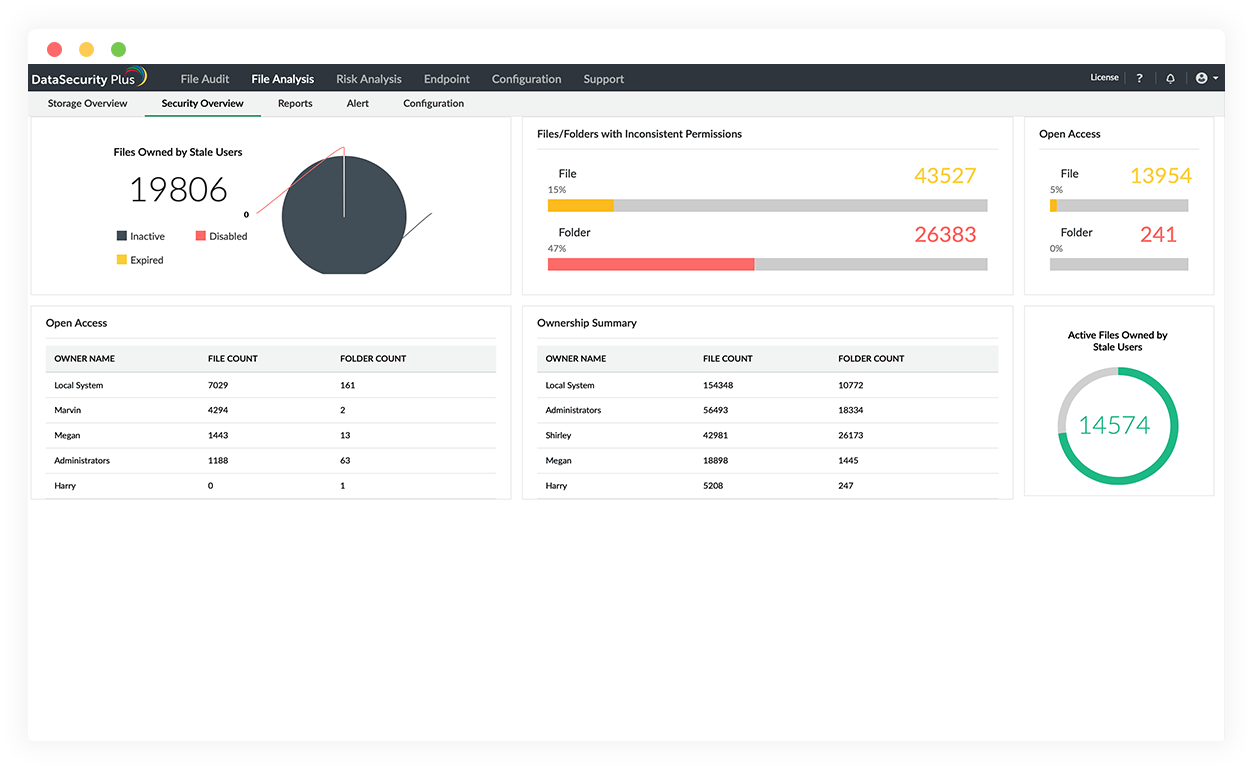
Storage and permission analysis
Analyze file metadata, permissions, and storage practices to check permission hygiene and optimize disk usage.
-
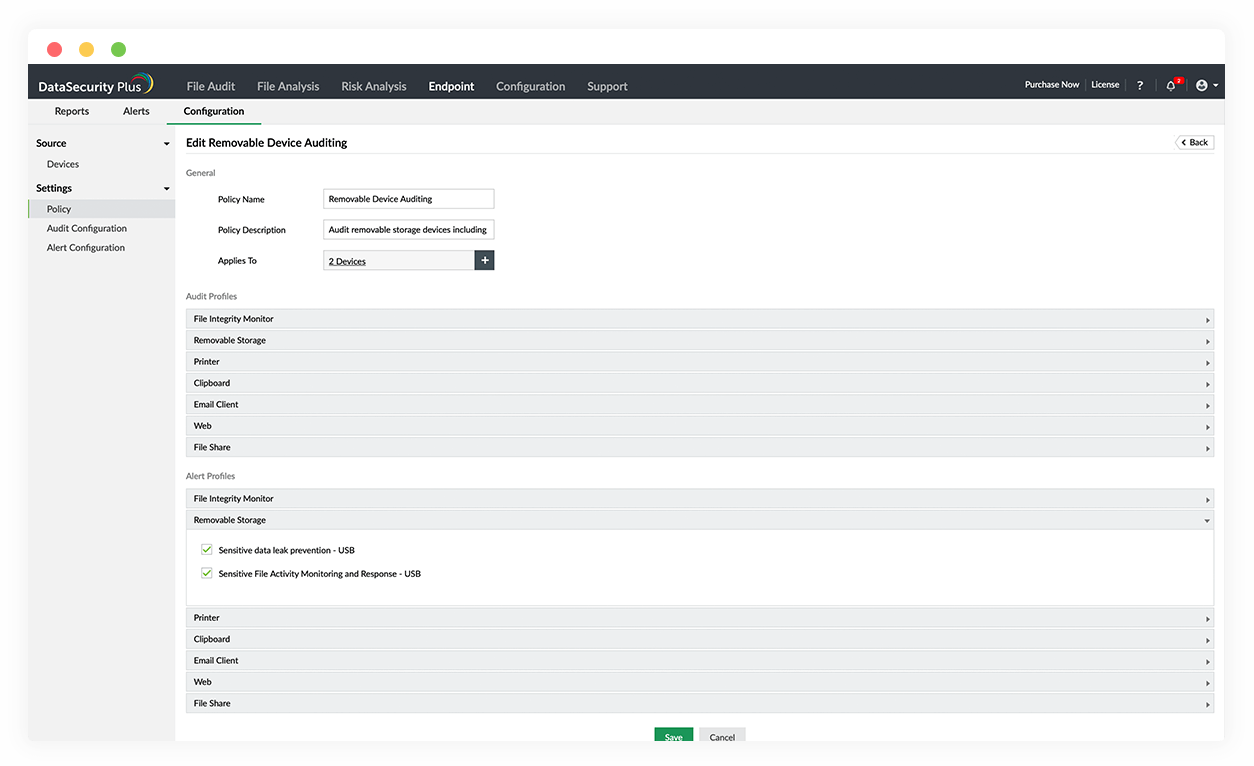
Data security tool
Secure sensitive data and prevent it from leaving your network via endpoints such as USBs, email, printers, and more.
-
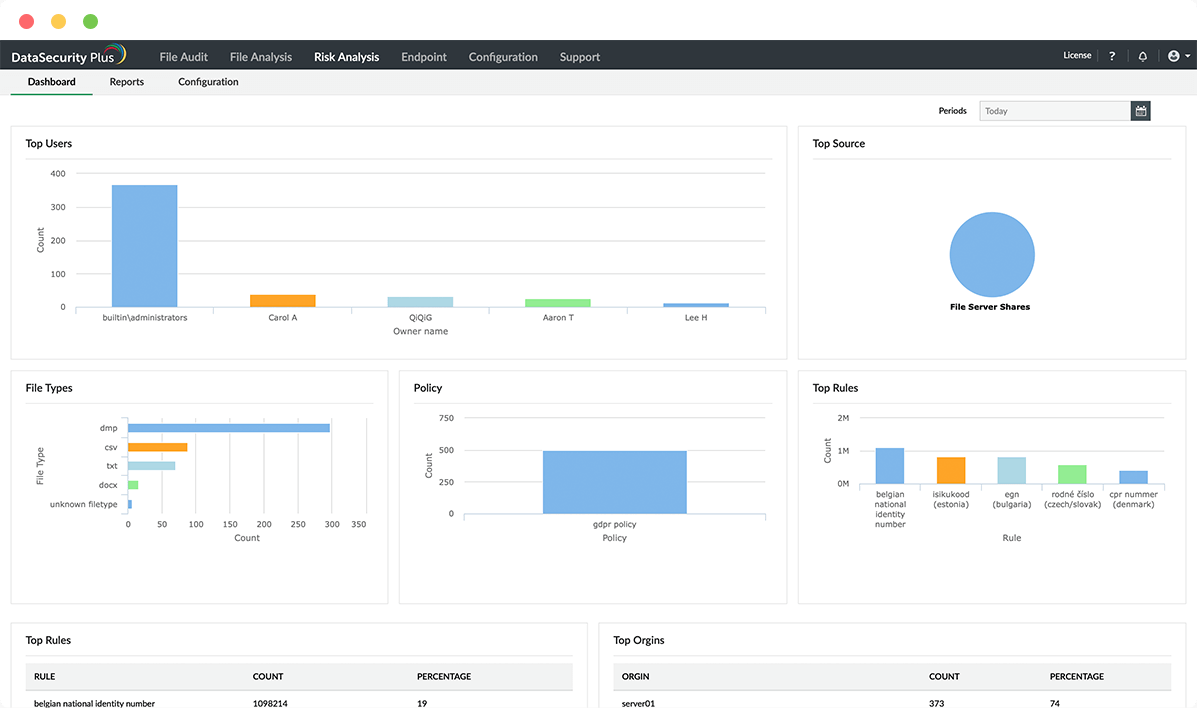
Ensure least privilege
Identify files that require the most stringent data security measures, and verify that their permissions are suitably restrictive.
Safeguard enterprise data from unauthorized use and exfiltration with data leak prevention software.