Locate all sensitive data in your data storage and classify it based on its sensitivity to implement adequate security measures for high-risk files.
Monitor abnormal file activity and prevent unauthorized file transfers across your on-premises storage, cloud storage, and endpoint devices.
Detect and respond to external and internal threats using automated security incident response systems.
Utilize regular expressions and keyword matching rules to discover PII, ePHI, PCI data, etc., hiding in your files.
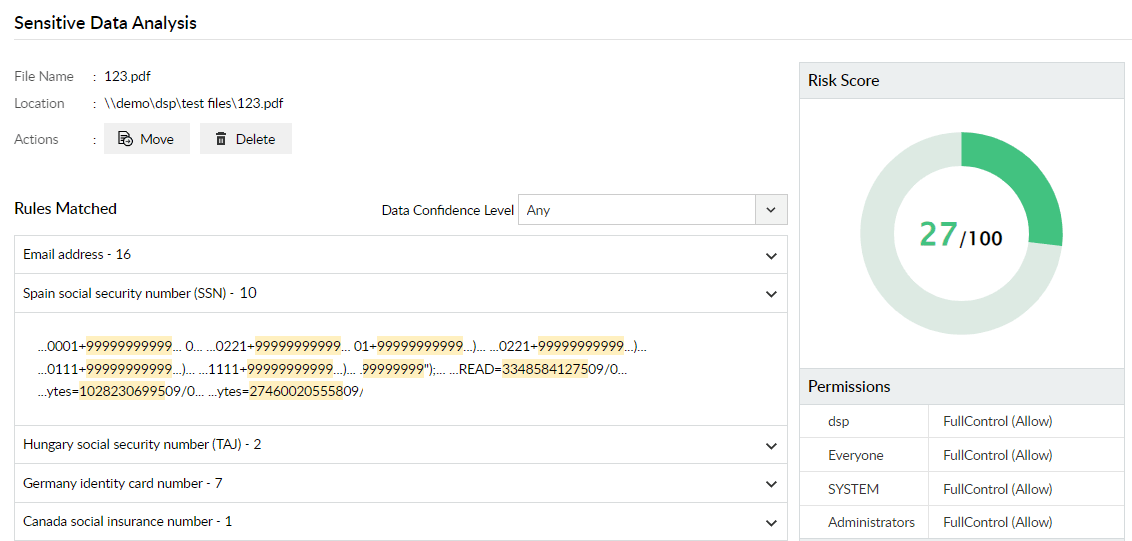
View risk scores assigned to files based on the volume of sensitive data they contain and their access permissions, and choose if you want to move or delete them.
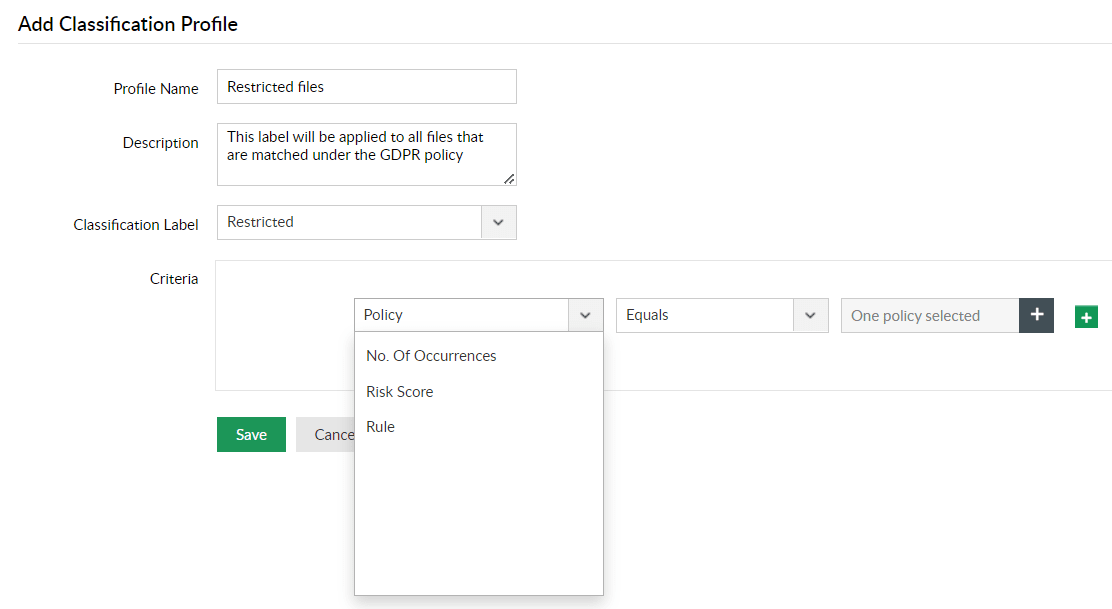
Instantly apply custom classification labels to all sensitive data based on custom policies, volume of sensitive data, matched rules, and risk scores.
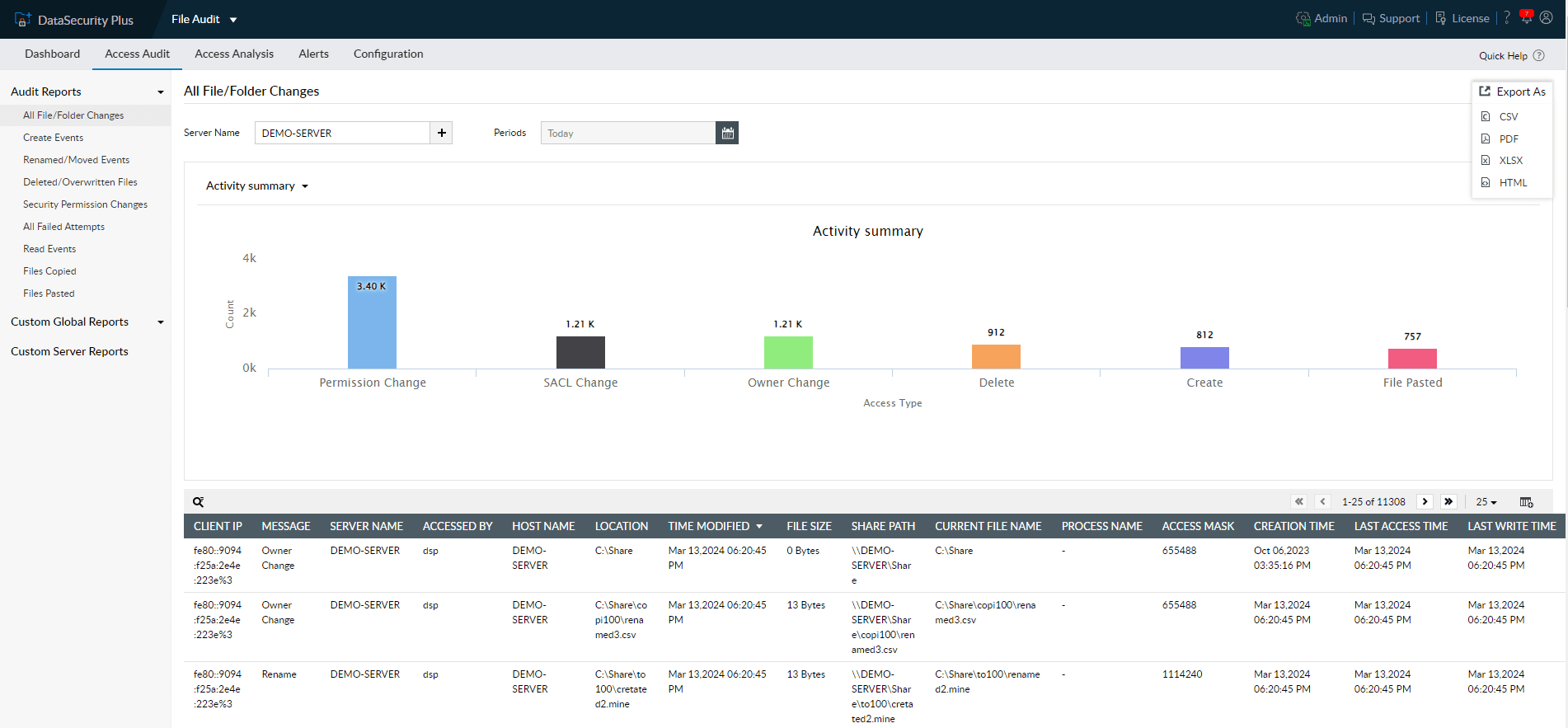
Audit all file activities with details on who accessed what, when, and from where, and detect high-risk file modifications with instant alerts.
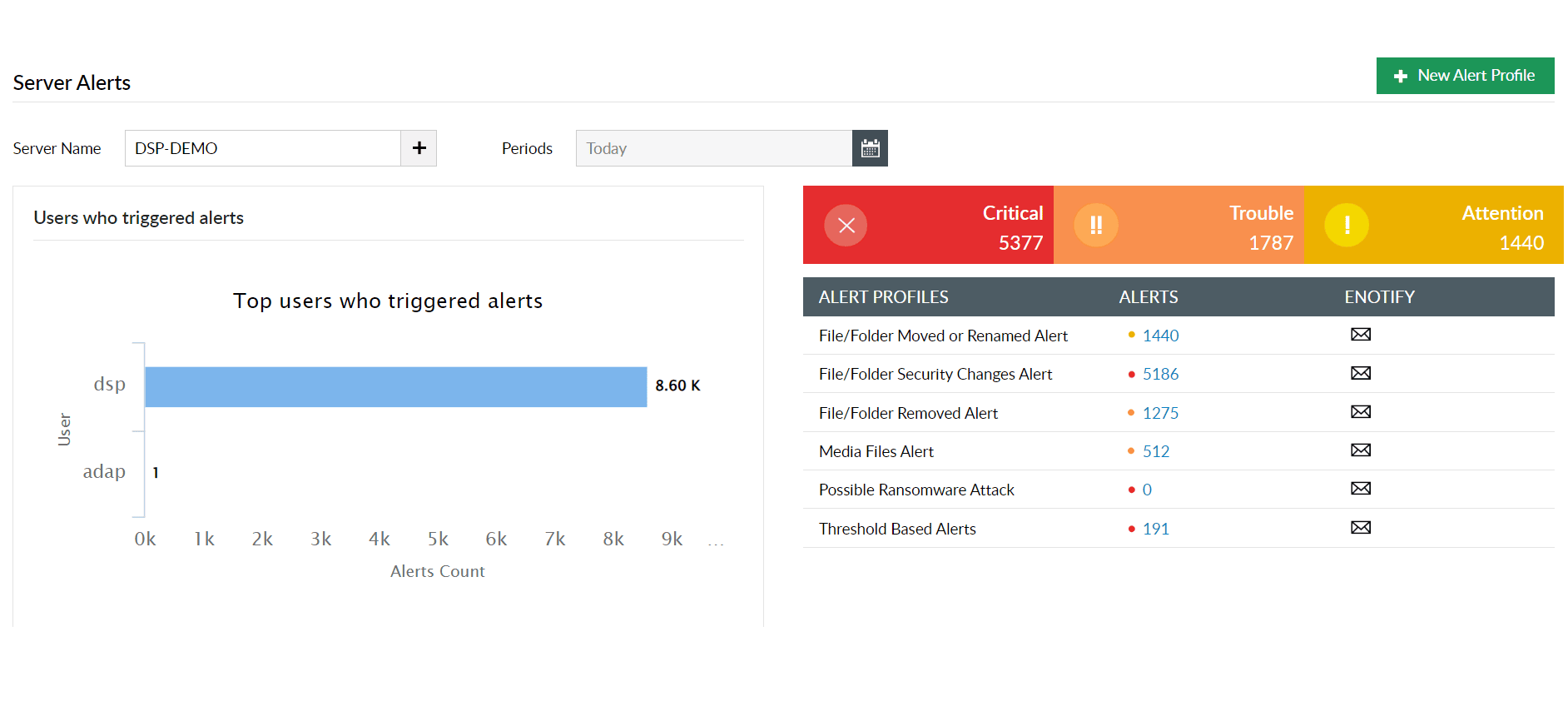
Generate instant alerts for tell-tale signs of ransomware attacks, such as file create, rename, and extension changes.
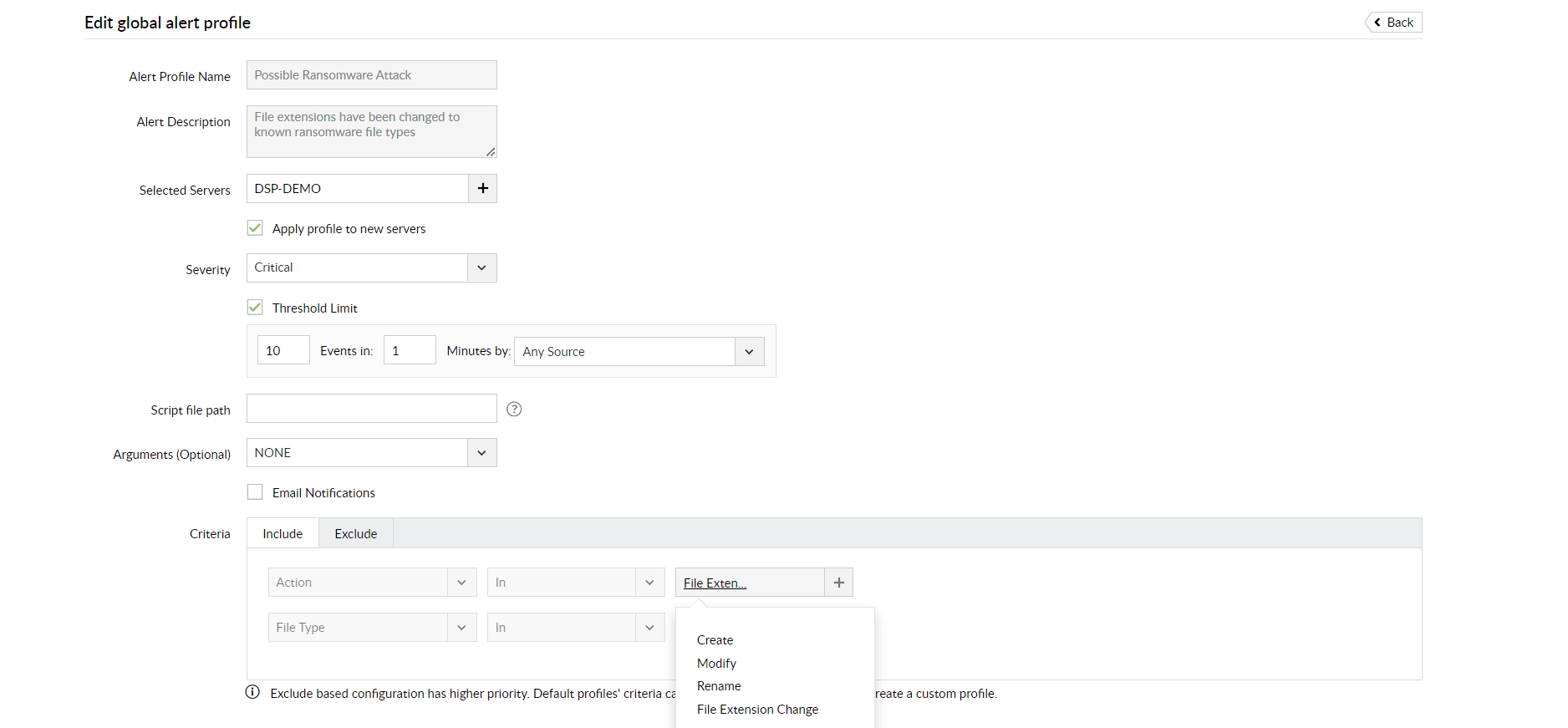
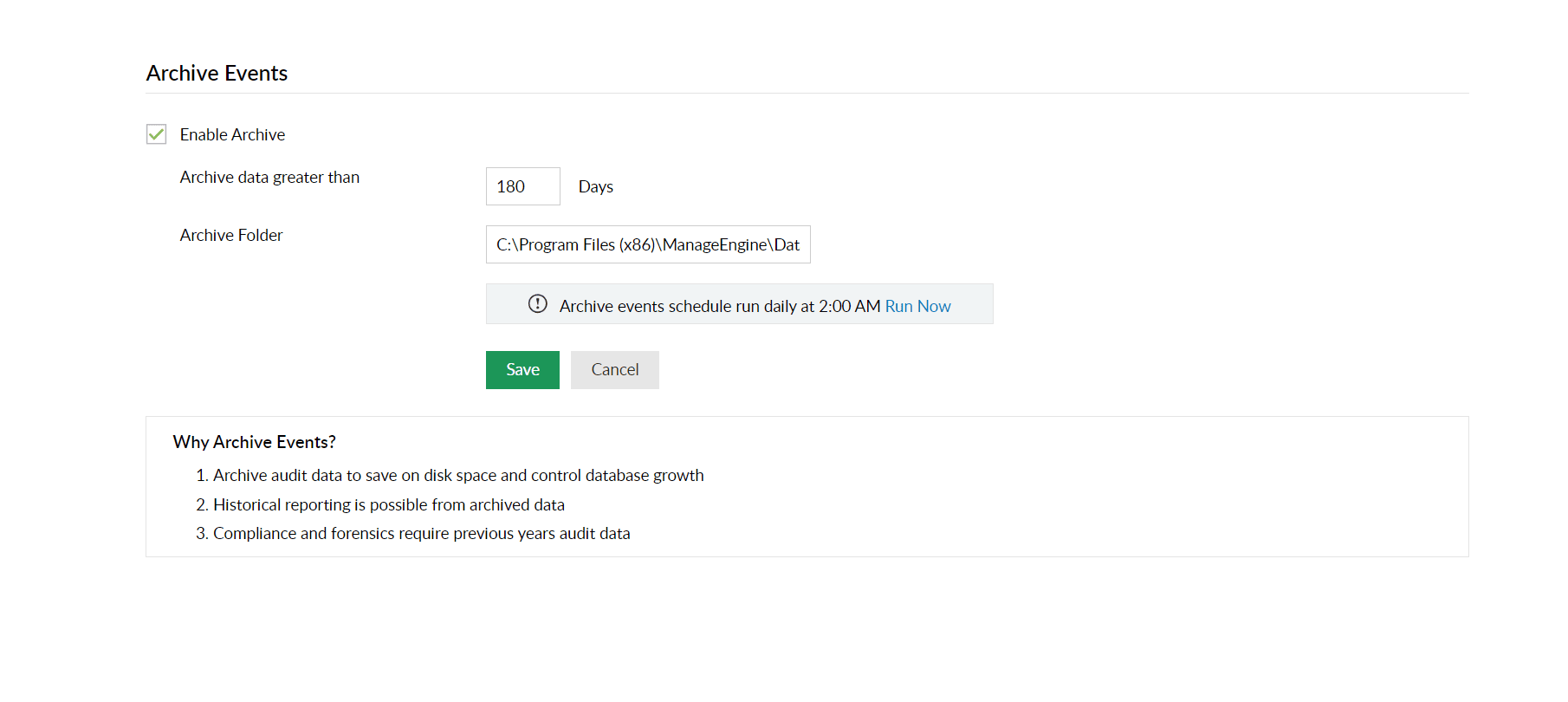
Maintain complete audit trails and keep all reports ready to address critical requirements of regulatory mandates like the GDPR, PCI DSS, and HIPAA.
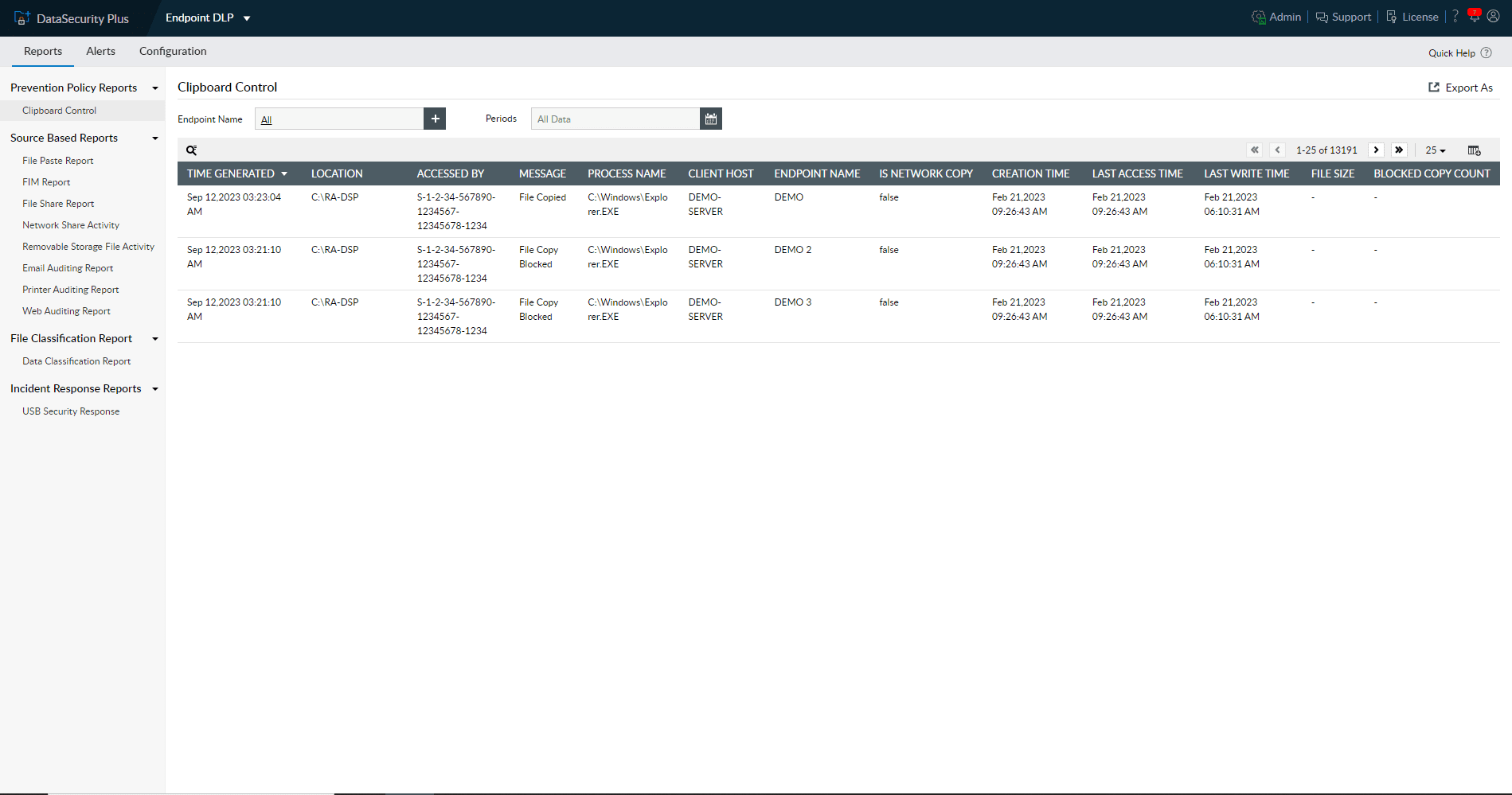
Audit all user clipboard actions across your servers and endpoints, and choose whether to allow or block them.
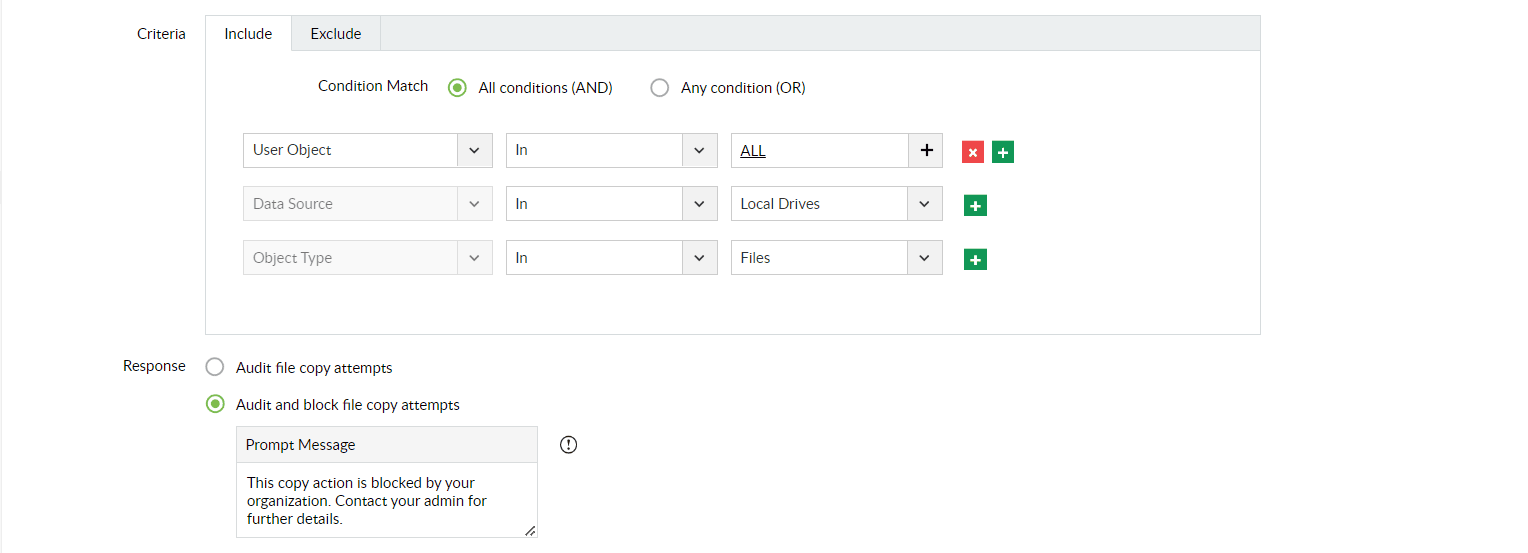
Use default or custom DLP policies to track and prevent data transfer activities across shared folders, USB devices, printers, bluetooth, WiFi, and more.
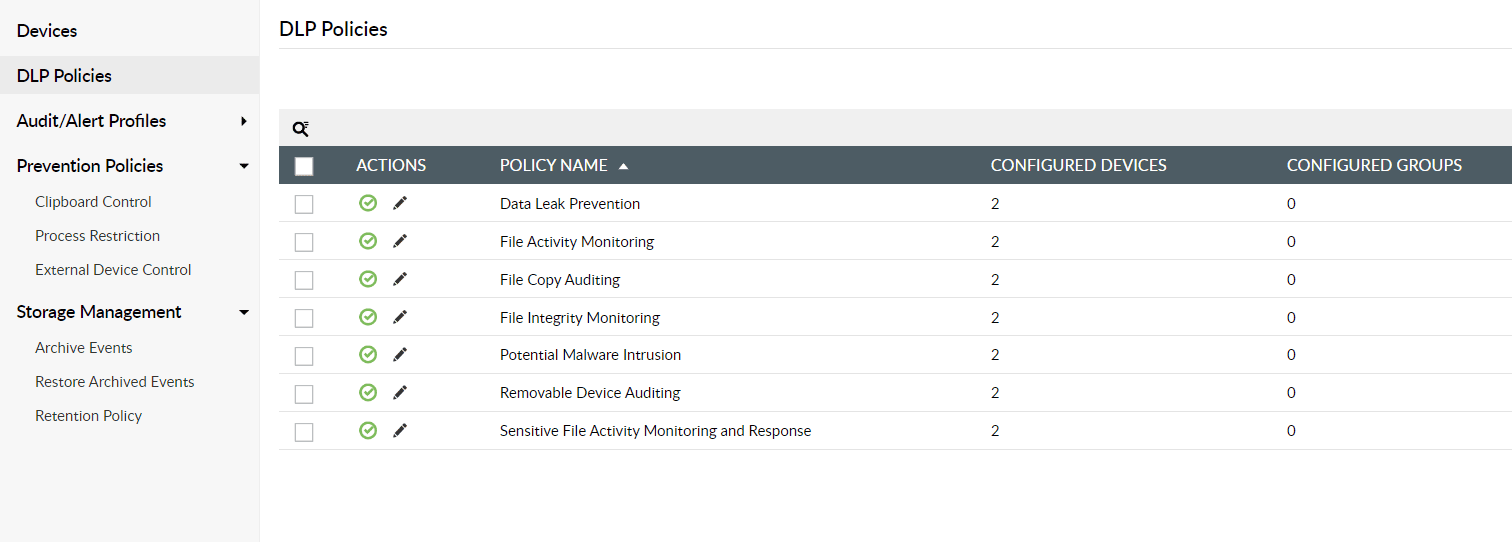
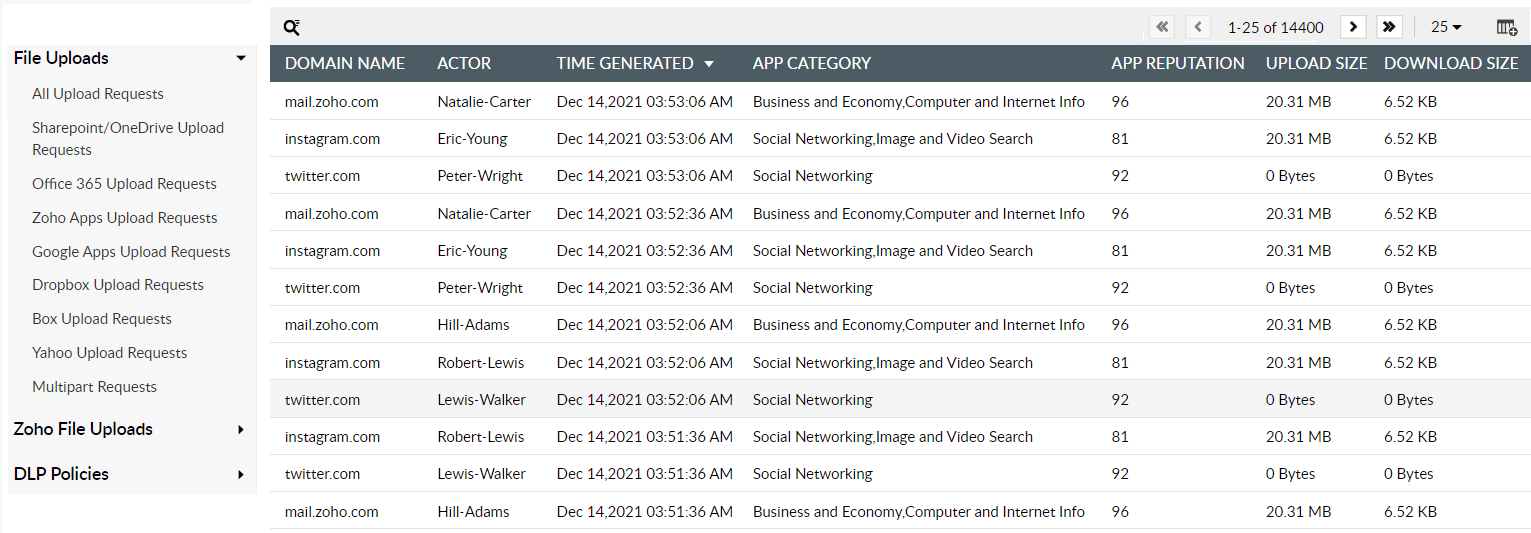
Scan outbound emails and attachments to track unauthorized file transfers. Block possible file uploads and downloads through various cloud applications.
Intuitive UI
Easy deployment
Cost-effective
Easy-to-use
dashboards
No productivity
downtime
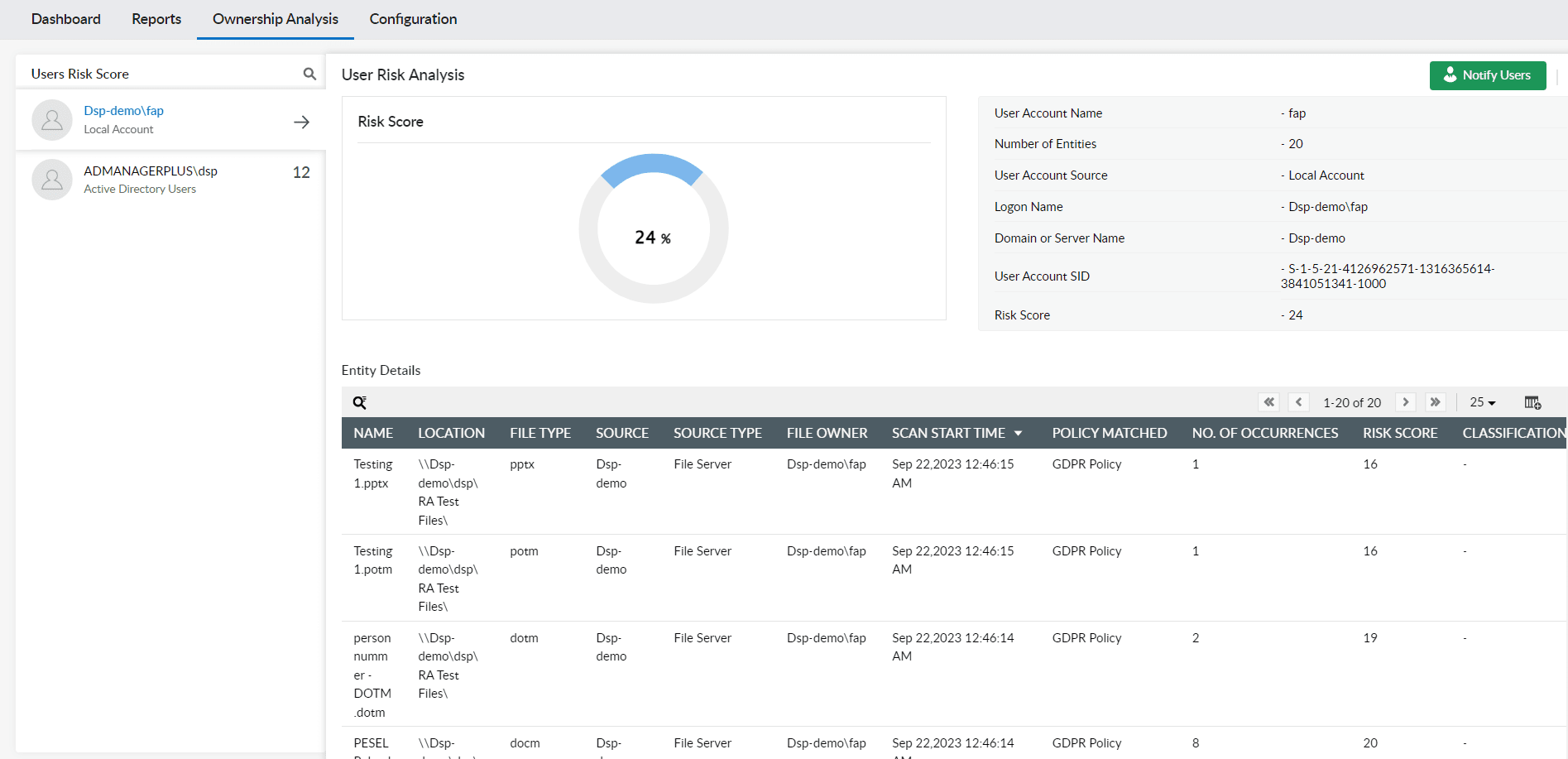
See how many sensitive files are owned by different users and identify high-risk users, alarming data trends, and more.
Gain a better understanding of privileged users and overexposed files using user risk scores.
Ask high-risk users to re-evaluate their access permissions and revoke them if needed.

Receive detailed information on each audited event, such as name, server, user, location, and more.
Add/remove report columns, filter based on server or time range, and export them in multiple formats such as CSV, PDF, etc.

Choose from a wide range of reports, each addressing different endpoint vulnerabilities.
Get all the information you need to track, monitor, and generate reports about actions carried out on endpoint devices.
