-
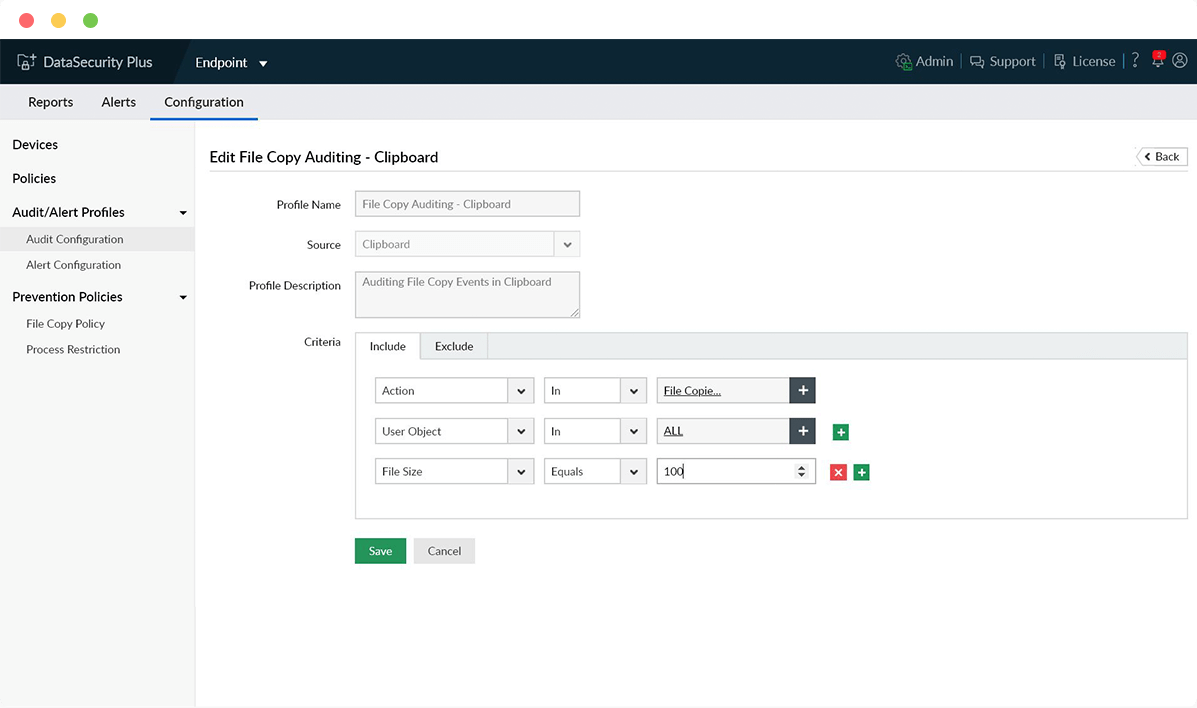
Audit removable storage
Track and analyze the usage of USB drives in your organization along with details on who accessed each device for what, when, and from where.
-
Detect USB usage anomalies
Trigger instant email notifications and block USB ports in response to high-risk events such as a sudden spike in files transfers to external storage devices.
-
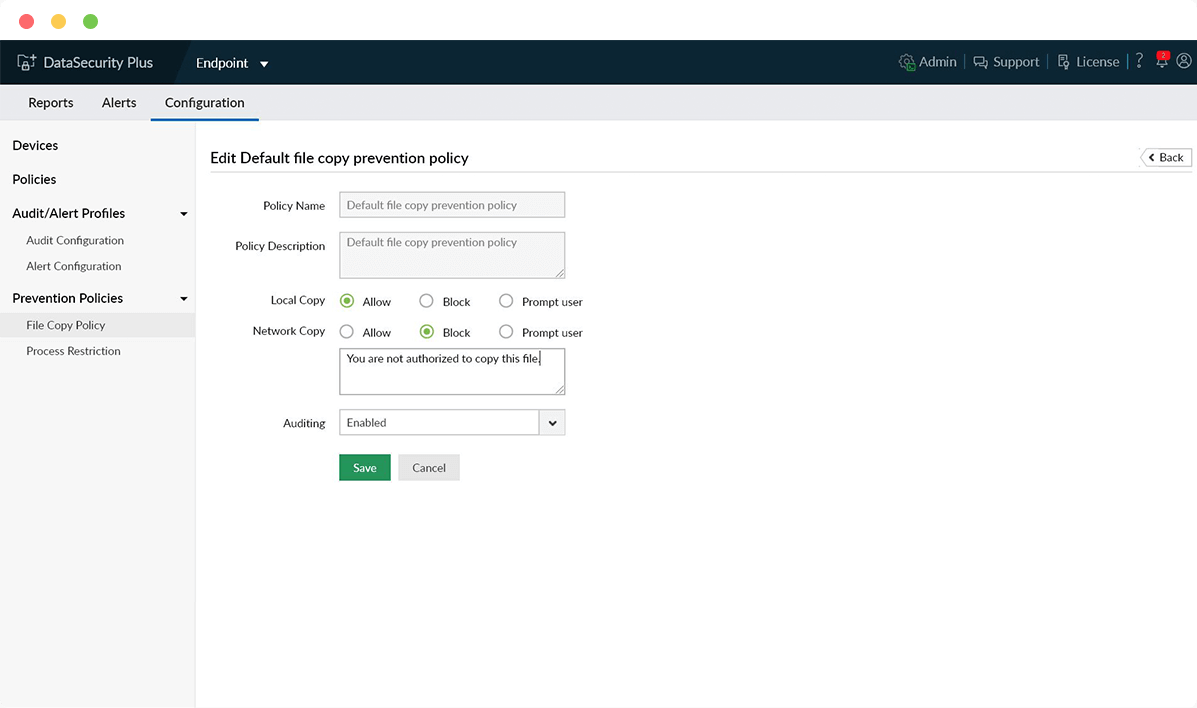
Stop data theft via USB
Restrict users from moving business-critical data to USB devices by blocking file copy actions to limit the possibility of a data leak.
-
Educate end users
Warn users against the dangers of needless file copy actions to USB drives with the use of automated system prompts.
Prevent malicious or accidental exposure of sensitive data with data leak prevention software