-
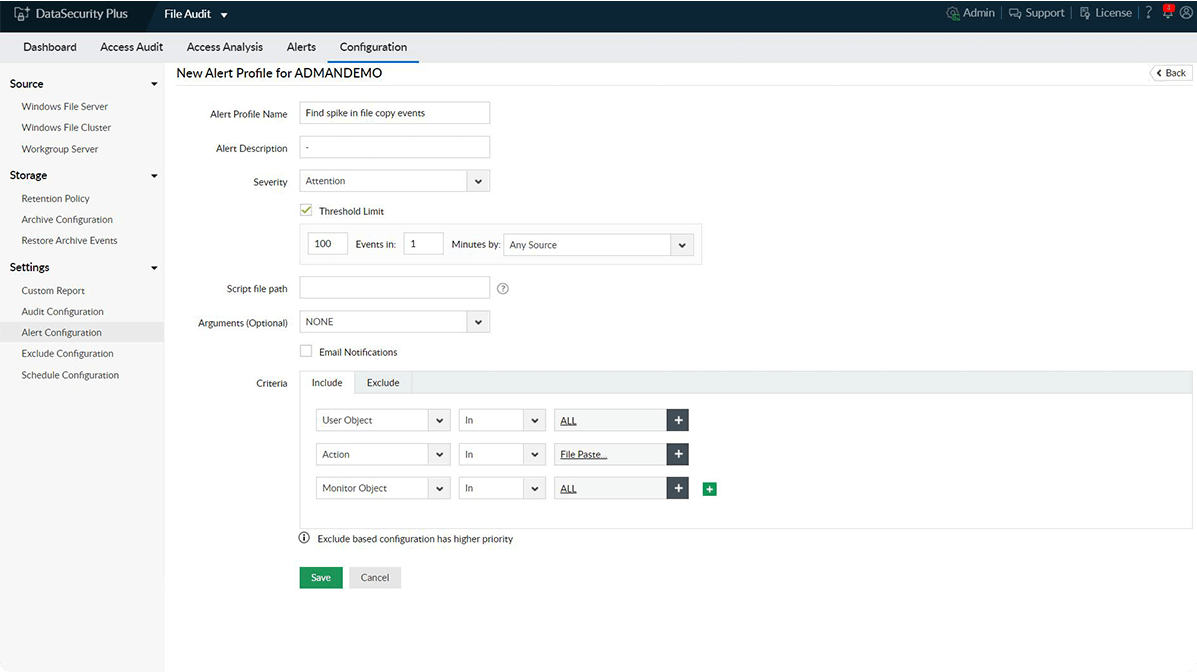
Audit file copy activities
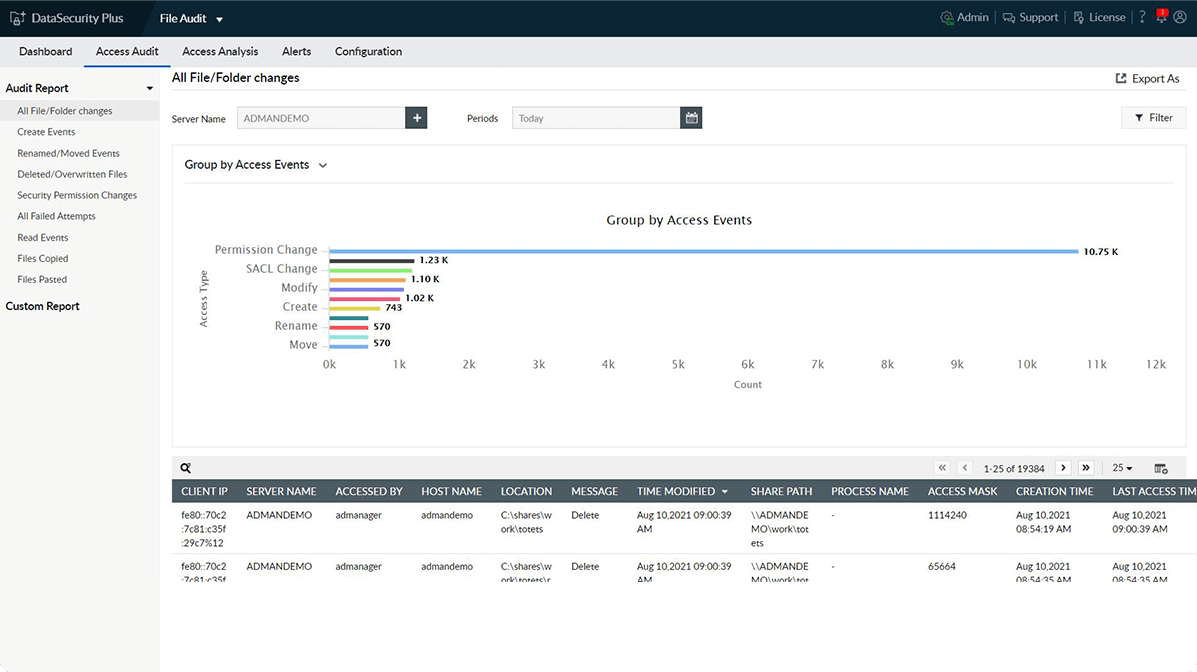
In addition to monitoring file accesses and modifications, keep track of file transfers with details on which file was copied, by whom, when, and from where.
-
Track email attachments
Analyze email attachments for confidential and restricted files and prevent their movement as per your organization's data security policy.
-
Stop data leaks via USB
Granularly limit the various capabilities of USBs like restricting users from running executables on USBs, making USBs read-only, or denying all USB accesses.
-
Record file movements
Maintain a detailed record of all file and folder transfers to ensure accountability and help with forensic investigations.
Restrict unauthorized file copies with the help of our data leak prevention software.