-
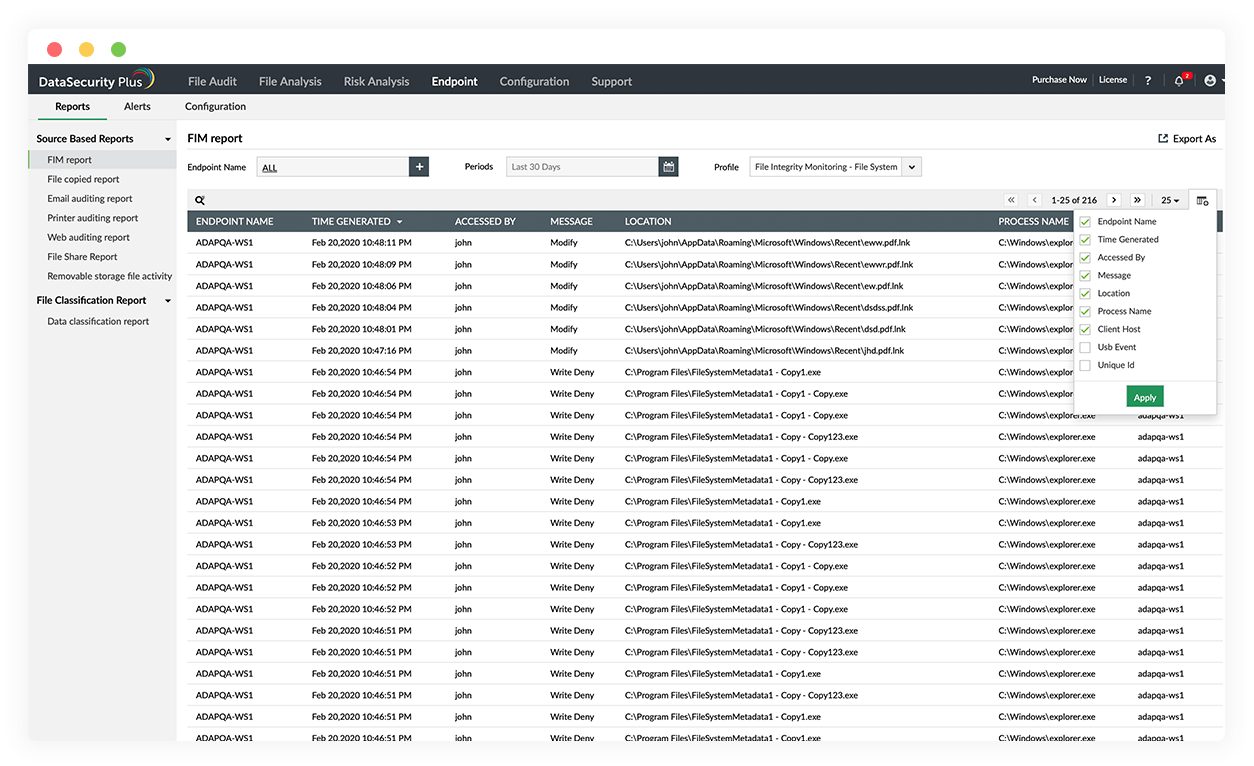
Investigate suspicious user actions
Instantly detect abnormal user behavior such as excessive permission changes, failed access attempts, and more.
-
Enable content-aware protection
Locate and tag files containing sensitive personal information such as PII, ePHI, or PCI, and enforce strong data protection strategies to safeguard it.
-
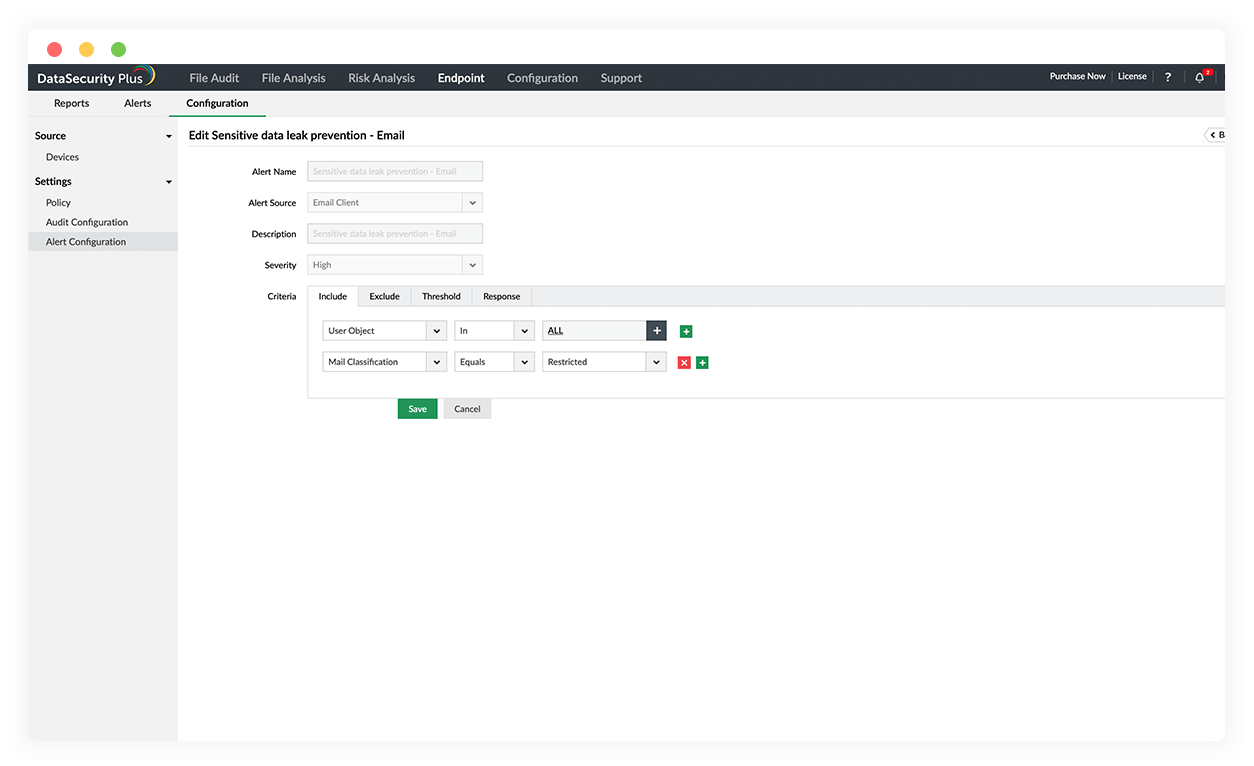
Stop unintended data leaks
Flag and respond to suspicious user actions such as large web uploads and sensitive data leaks via USB or email.
-
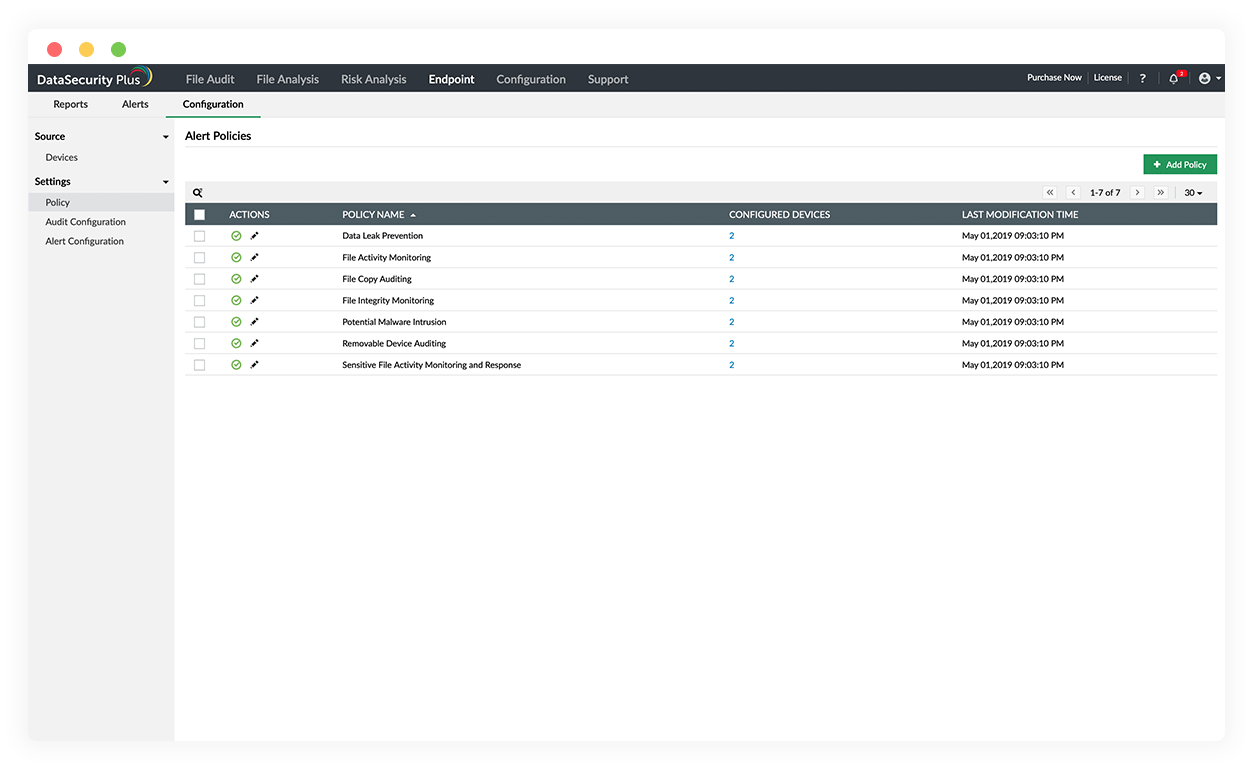
Boost end-user accountability
Use file auditing capabilities to log user actions in real time, and spot misuse of permissions, multiple failed access attempts, and more.
Track malicious user behavior and stop data exfiltration using our data leak prevention tool.