-
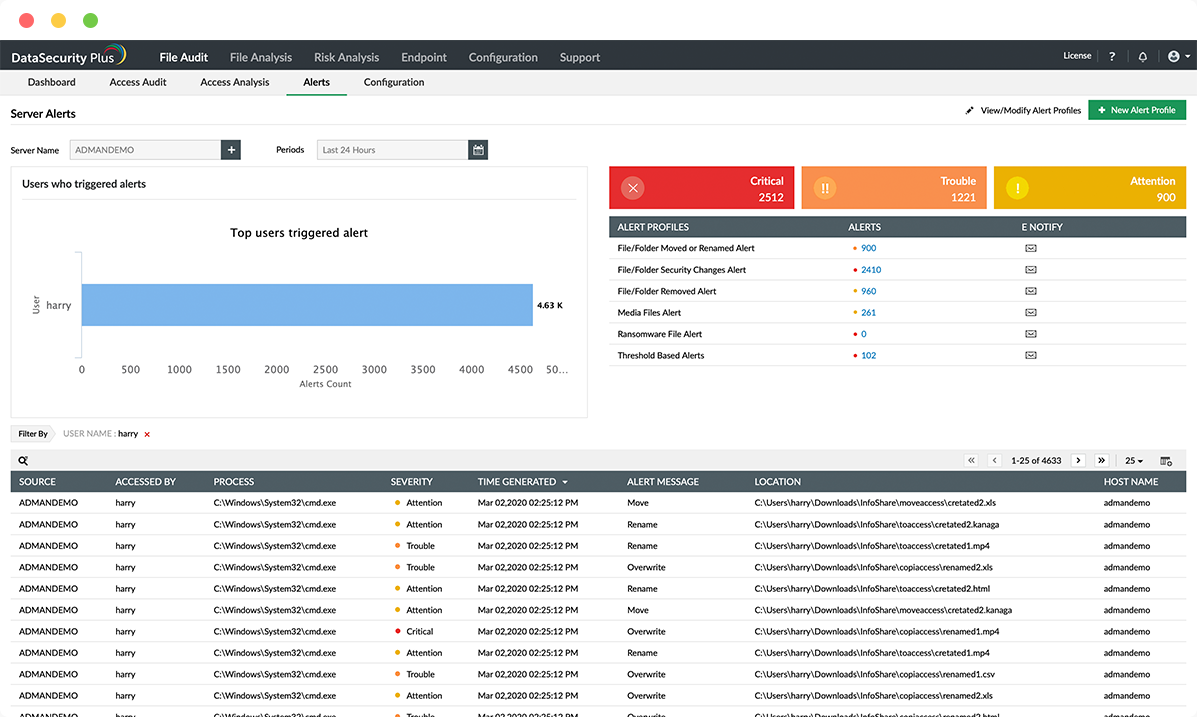
Environment-specific alerts
Customize alerts based on a specific user, file, event source, etc. to identify anomalous or suspicious activity unique to your environment.
-
Spots indicators of compromise
Detect user activity anomalies like file changes carried out during non-business hours, or a sudden surge in file deletions.
-
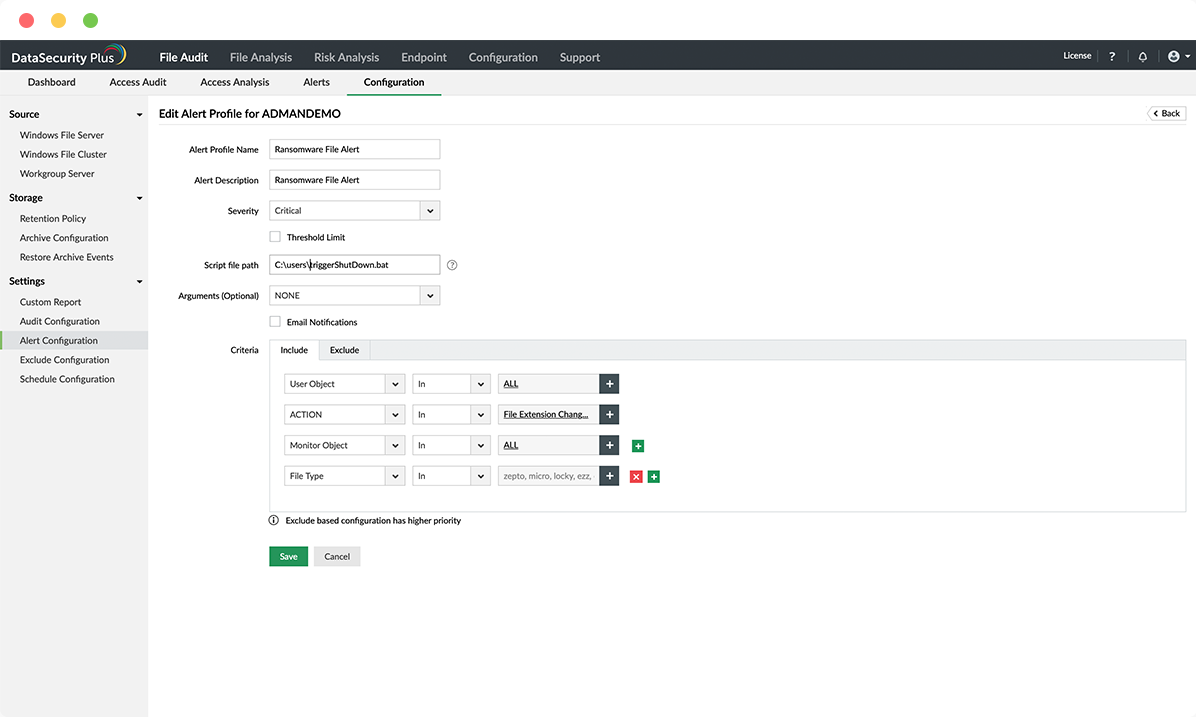
Security incident handling
Detect ransomware attacks, and prevent them from spreading by executing scripts to shut down infected servers and isolate corrupted machines.
-
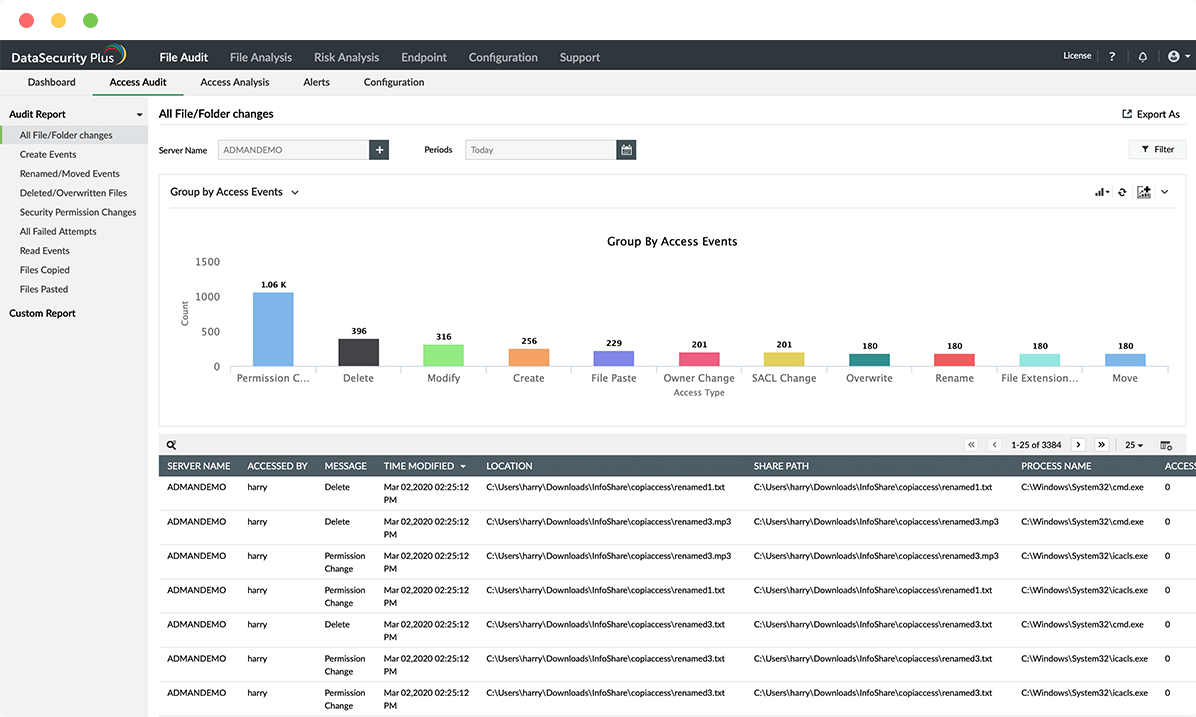
DLP incident response
Thwart attempts to exfiltrate sensitive data via USBs and email with the security incident response tool's effective, predefined responses.
Detect and prevent sensitive data leaks via USB devices, email, and more using our data leak prevention tool