-
Detect data theft attempts
Identify and block the actions of malicious insiders who try to steal files containing business-critical data via USB sticks or email (Outlook) attachments.
-
Spot indicators of compromise
Catch high-risk behavior, such as running suspicious executables, trying to access restricted web applications, and using unauthorized personal devices, and trigger instant email alerts.
-
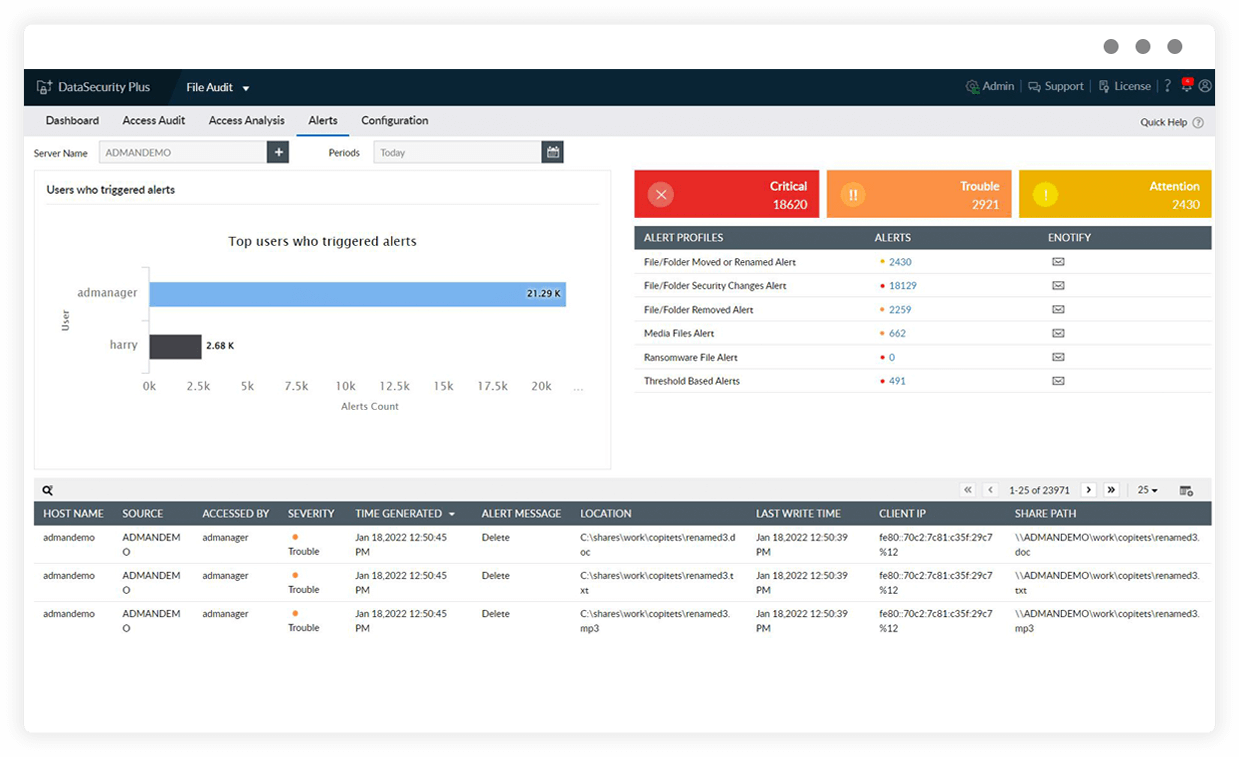
Instant threat detection and response
Use our automated threat response mechanism to shut down infected systems, disconnect corrupted users' sessions, quarantine files and folders, disable suspicious user accounts, and more.
-
Locate security vulnerabilities
Discover gaps in your cybersecurity framework such as files owned by stale, disabled, and expired users; files with open access; or those with permission hygiene issues.
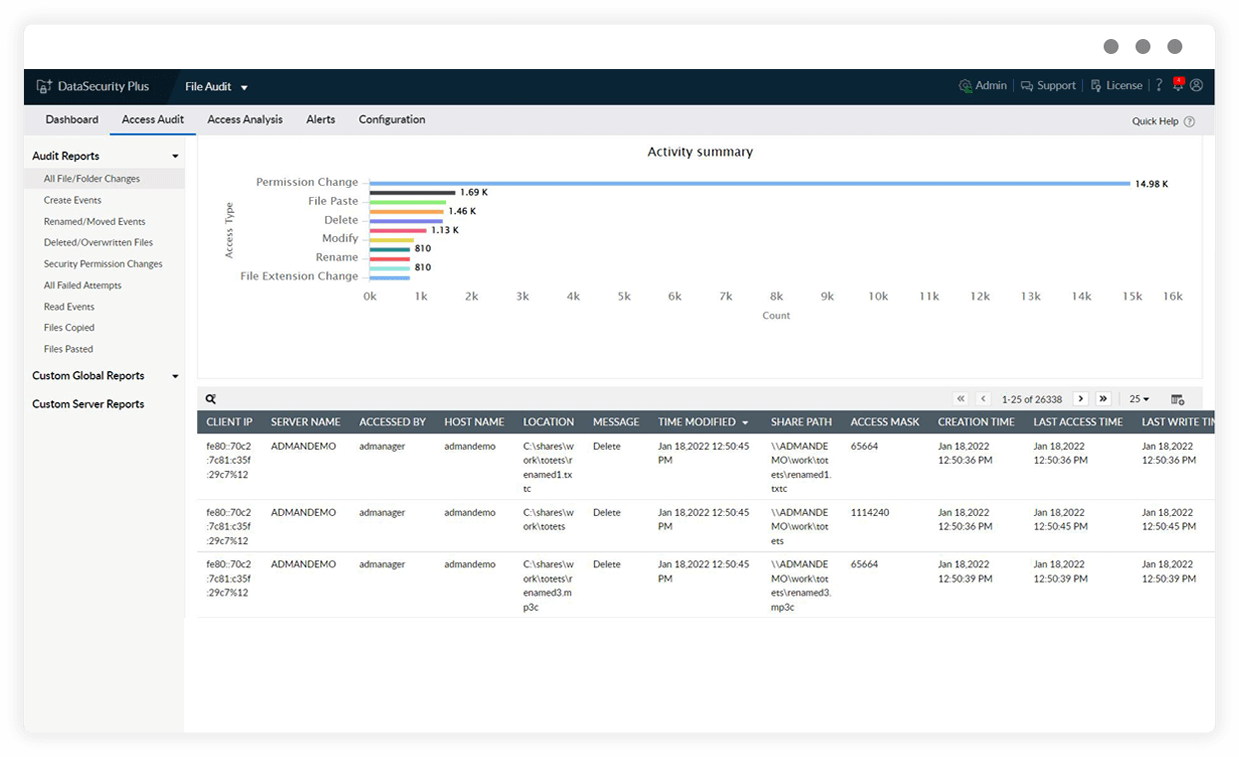
Facilitate quick threat detection and response using our data leak prevention software.