-
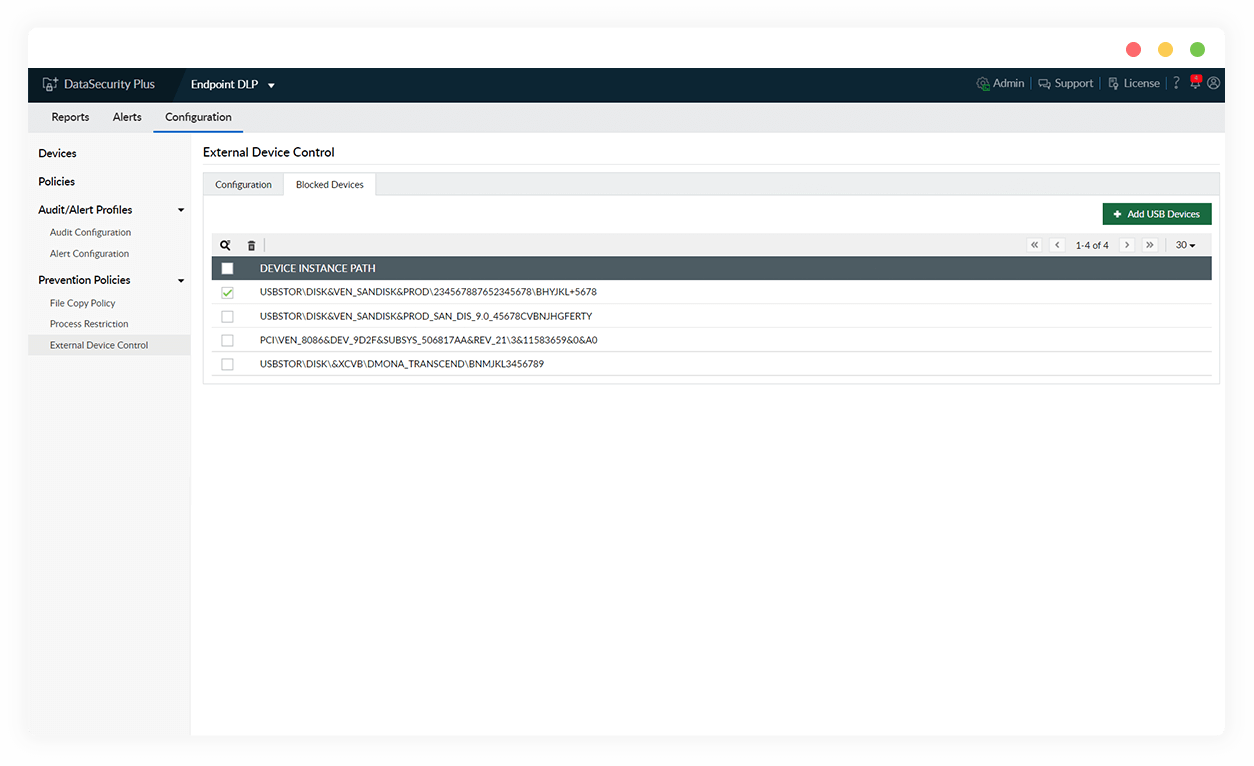
Allow only authorized flash drives
Add the device instance paths of flash drives to a blocklist to prevent attacks from potentially harmful drives. Block USBs when any user action is initiated to prevent foul play by insiders.
-
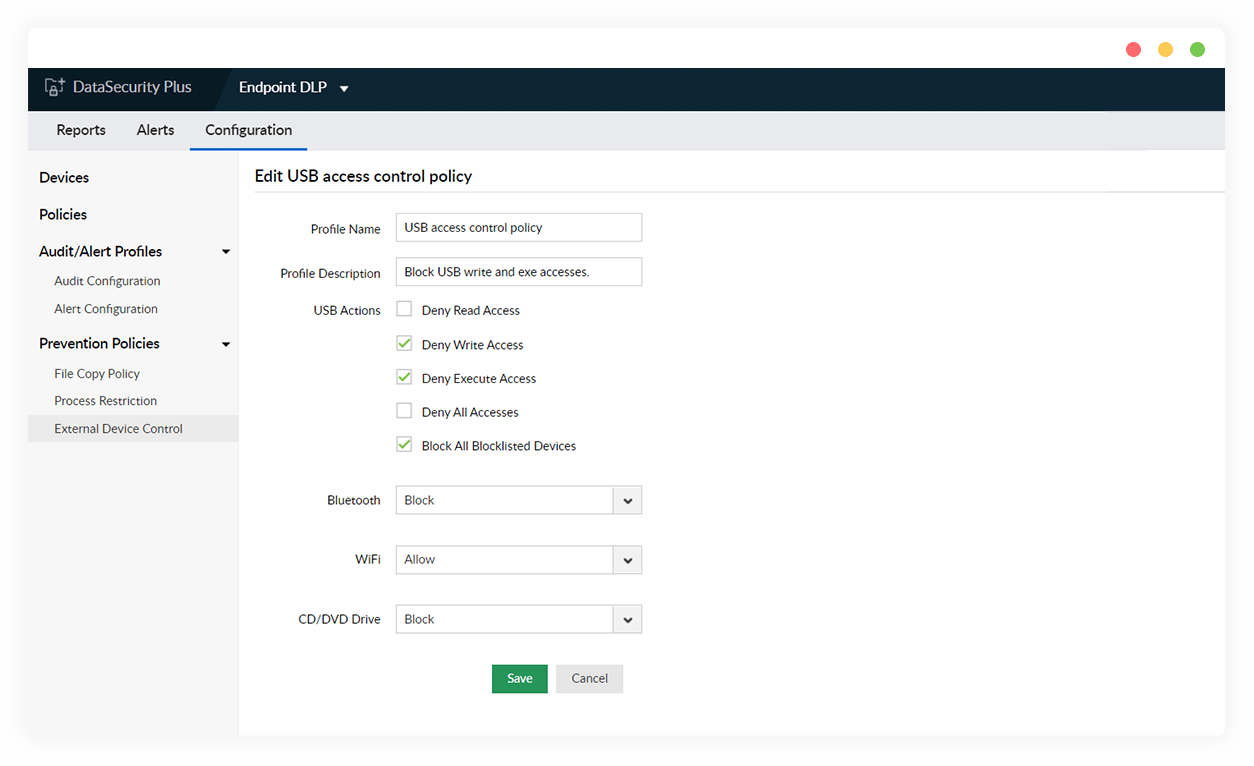
Prohibit specific USB drive actions
Decline select user actions made in removable storage drives. For instance, enable read access to files within a drive but disable modify rights to prevent user-made changes.
-
Prevent application execution in USBs
Restrict application executables within flash drives being run by all users. Allow users access to USB actions by applying the external device policy to only authorized endpoints.
-
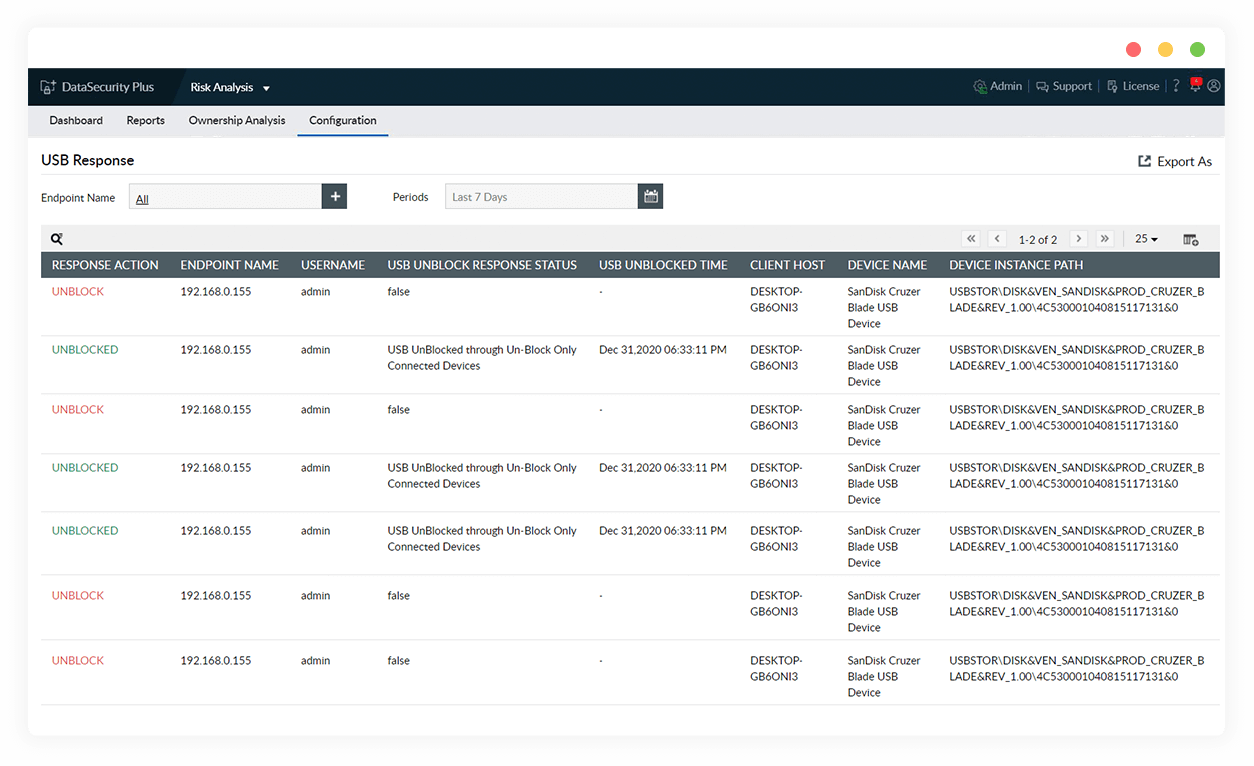
Monitor sensitive file activity in USBs
Track USB actions on restricted files and be notified by email. Further, define a built-in response to block the removable drive to curb unauthorized activity.
Regulate user actions made in USB drives and other removable media with our data leak prevention software.