-
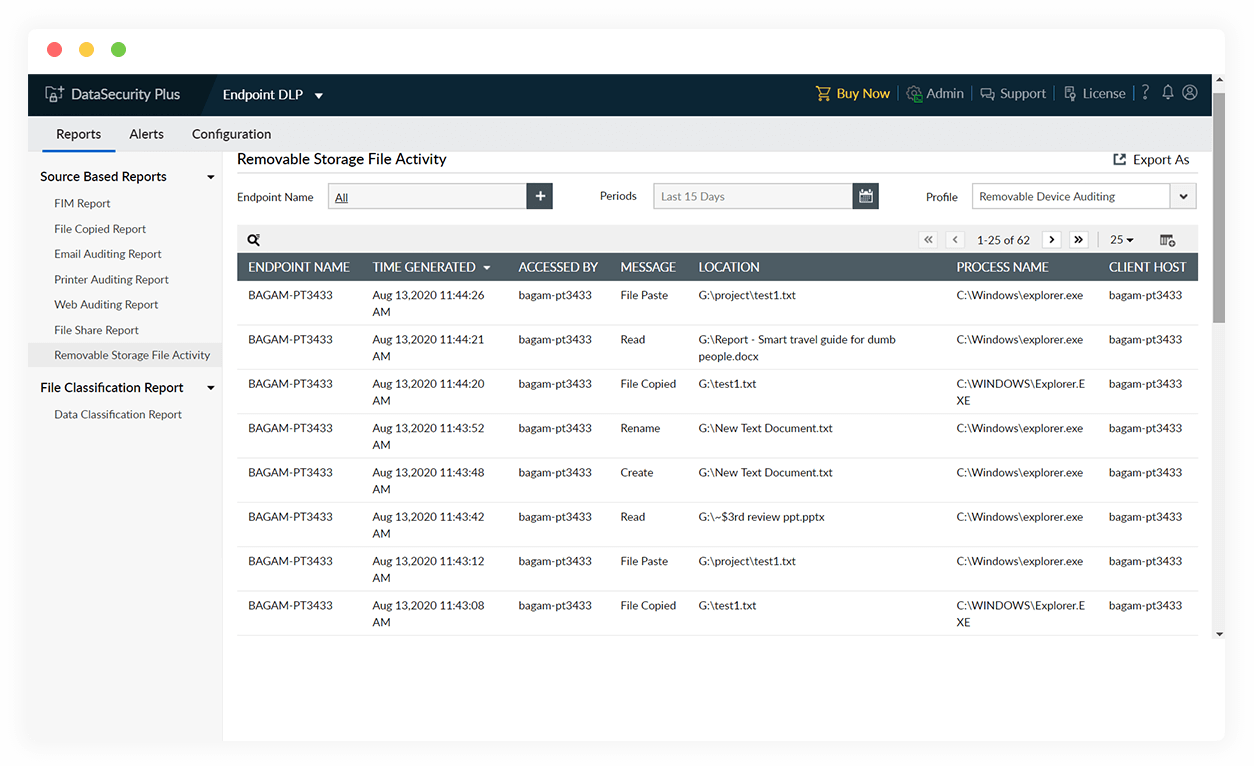
Monitor removable storage device usage
Audit the use of removable storage devices in your organization, and maintain a detailed record all files transferred to and from devices, including details on time, location, user, etc.
-
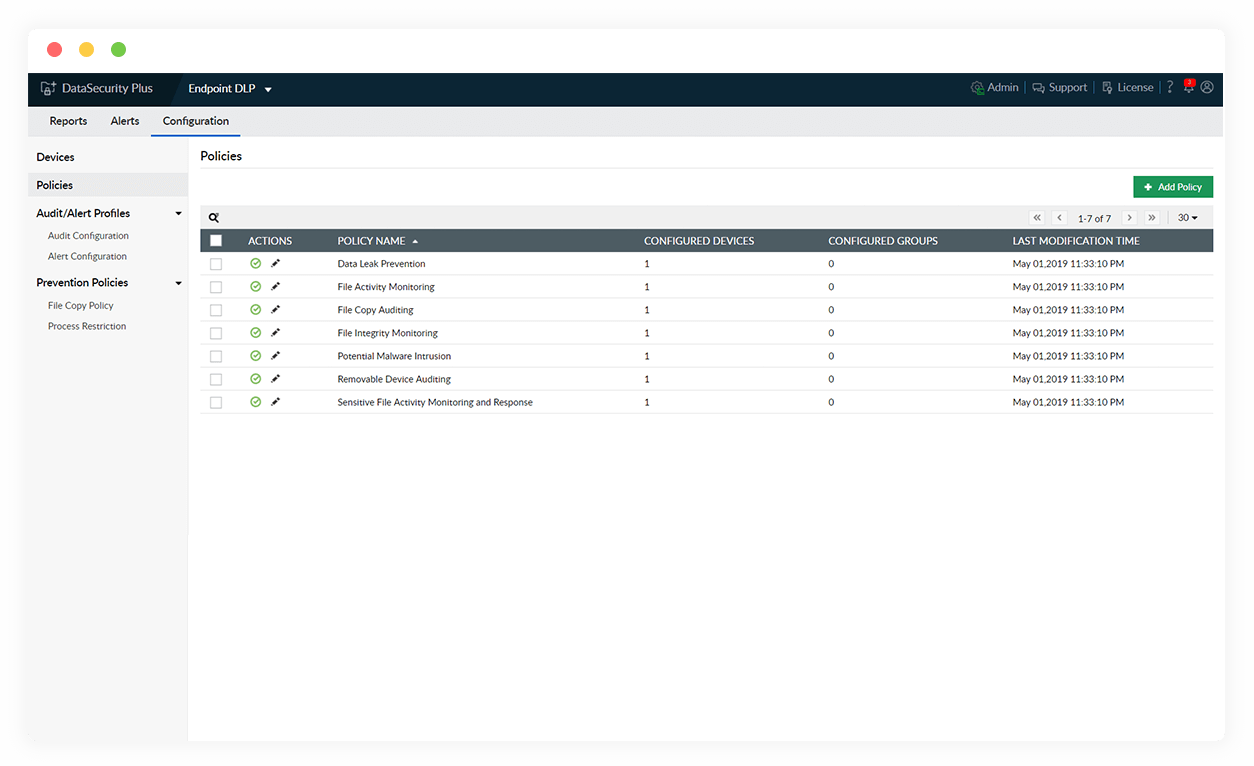
Identify anomalous file transfers
Keep yourself informed of all unwarranted file transfers that take place across USB devices by triggering instant email alerts.
-
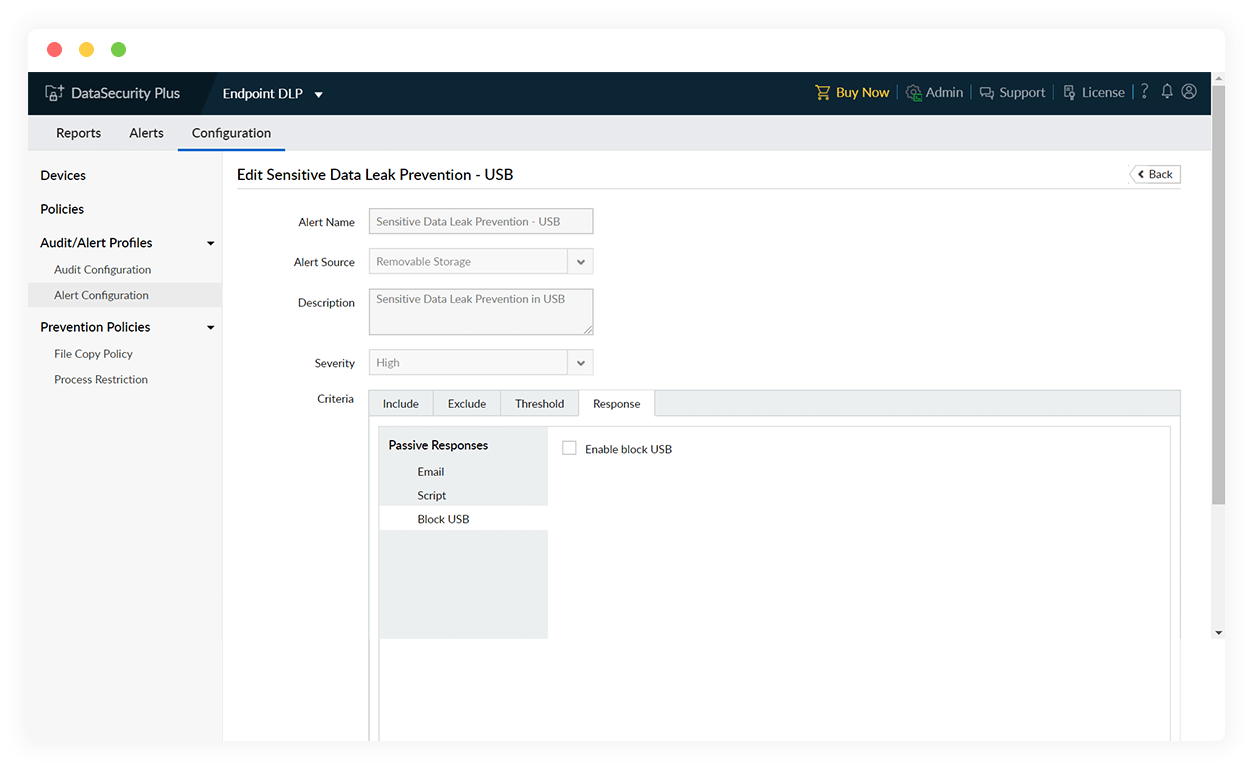
Respond to high-risk events
Lock down USB ports as a response to data exfiltration attempts, and ensure no further leak occurs by restricting files from being copied to USB devices.
-
Write protect USB devices
Prevent files on your USB devices from getting modified by restricting file actions, and blocklist suspicious devices using USB port control.
Ensure no data is lost via USB and other removable storage devices using our data leak prevention tool.