-
Track removable device use
Gain insights into USB device use in your organization with details such as what action was attempted, when it was performed, by whom, and more.
-
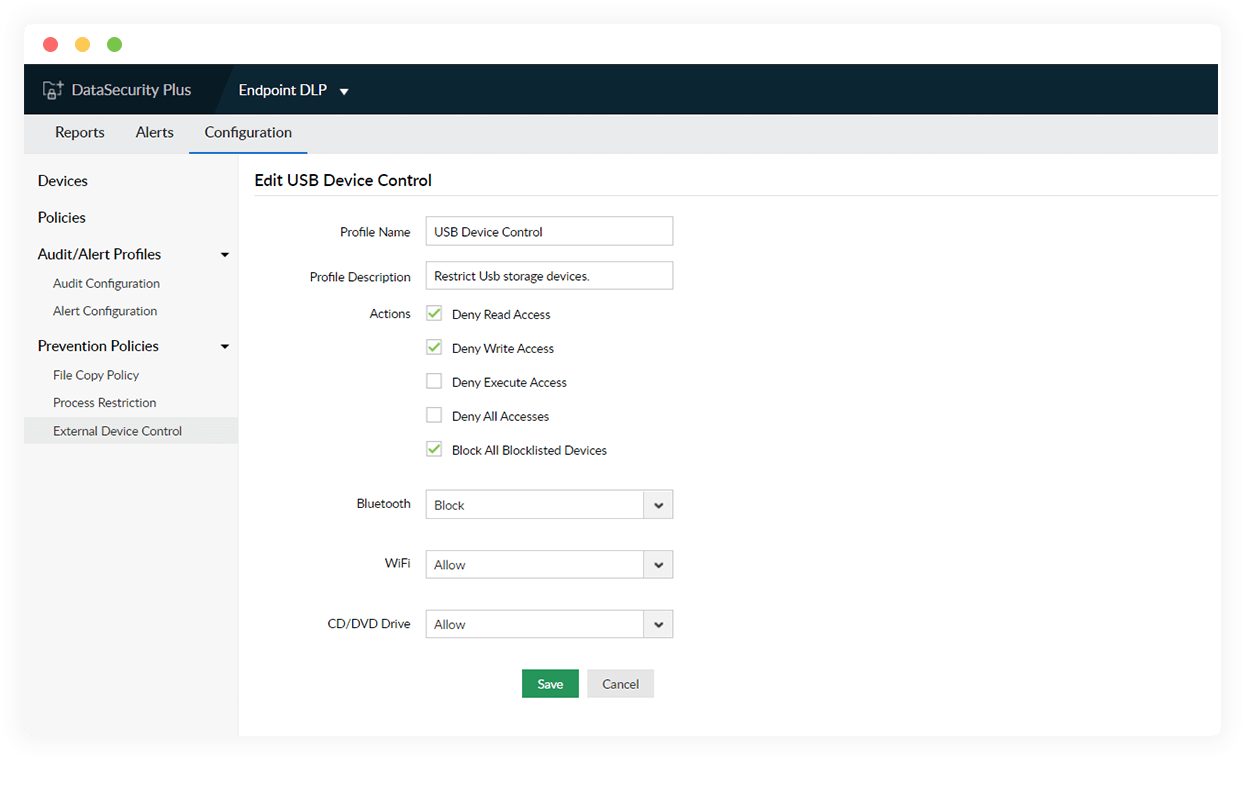
Control USB file activities
Restrict exclusive file actions such as read, write, and execute action on USBs—either individually or all together—to hinder malware infiltration and prevent data leaks.
-
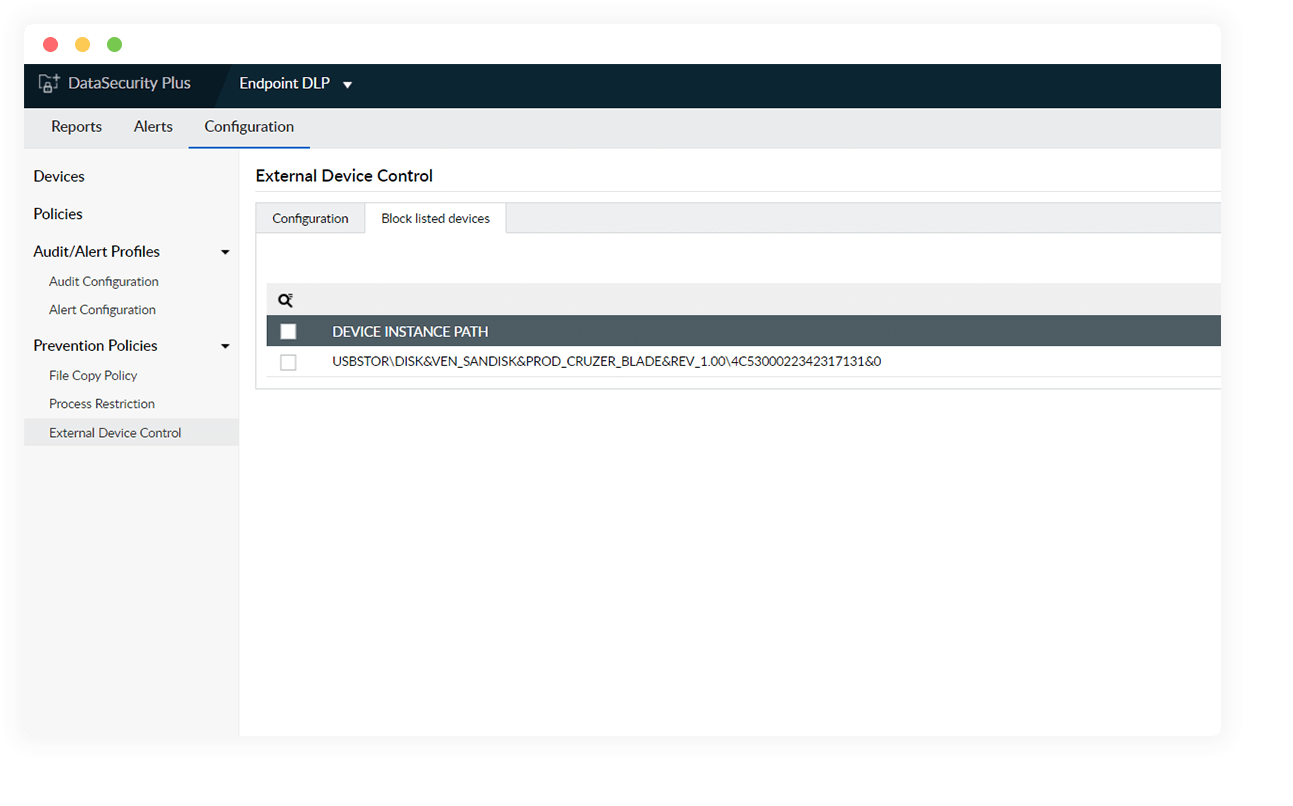
Blocklist USB devices
Create a list of all removable storage devices that need to be banned using their device instance paths, and block them using suitable policies.
-
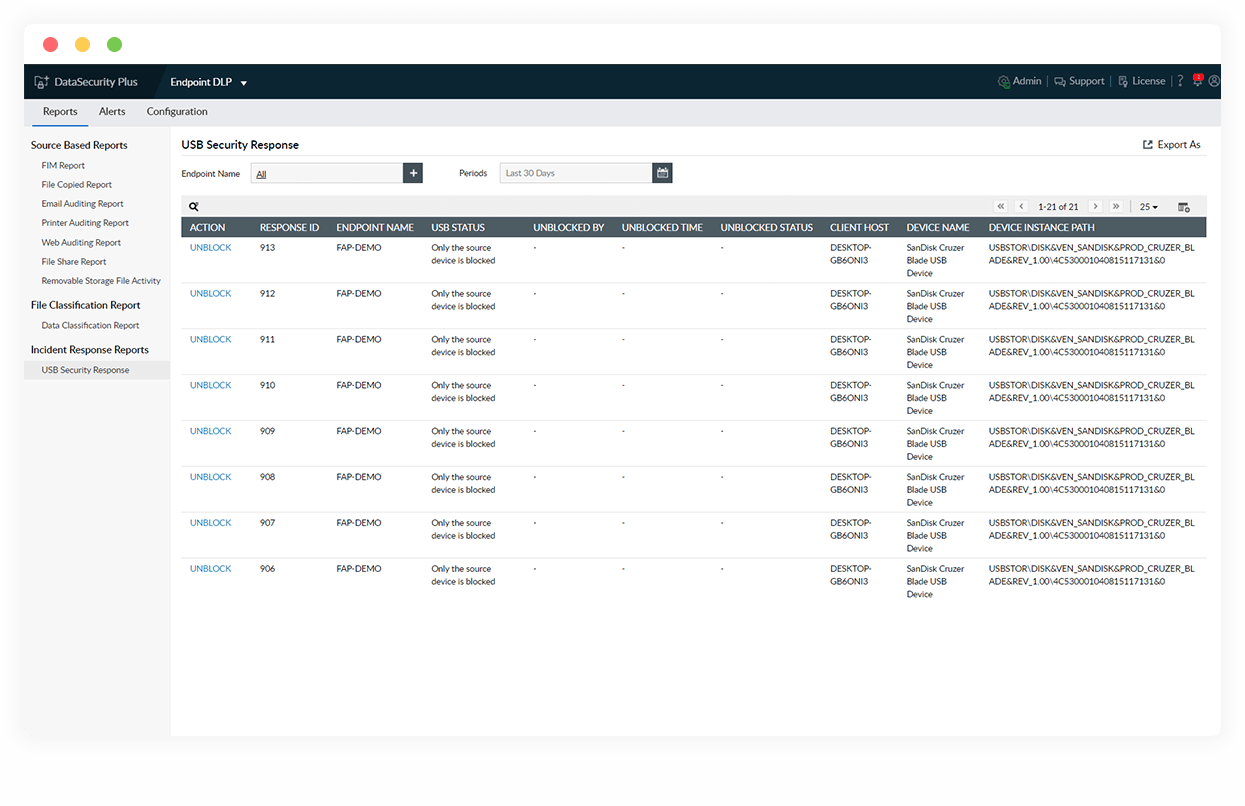
Block and unblock USB ports
Block USB ports as a response to unauthorized devices using them for data transfer attempts, and unblock them easily from the reports.
Stop unauthorized USB transfers by monitoring USB device use and blocking USB ports using our USB monitoring tool