-
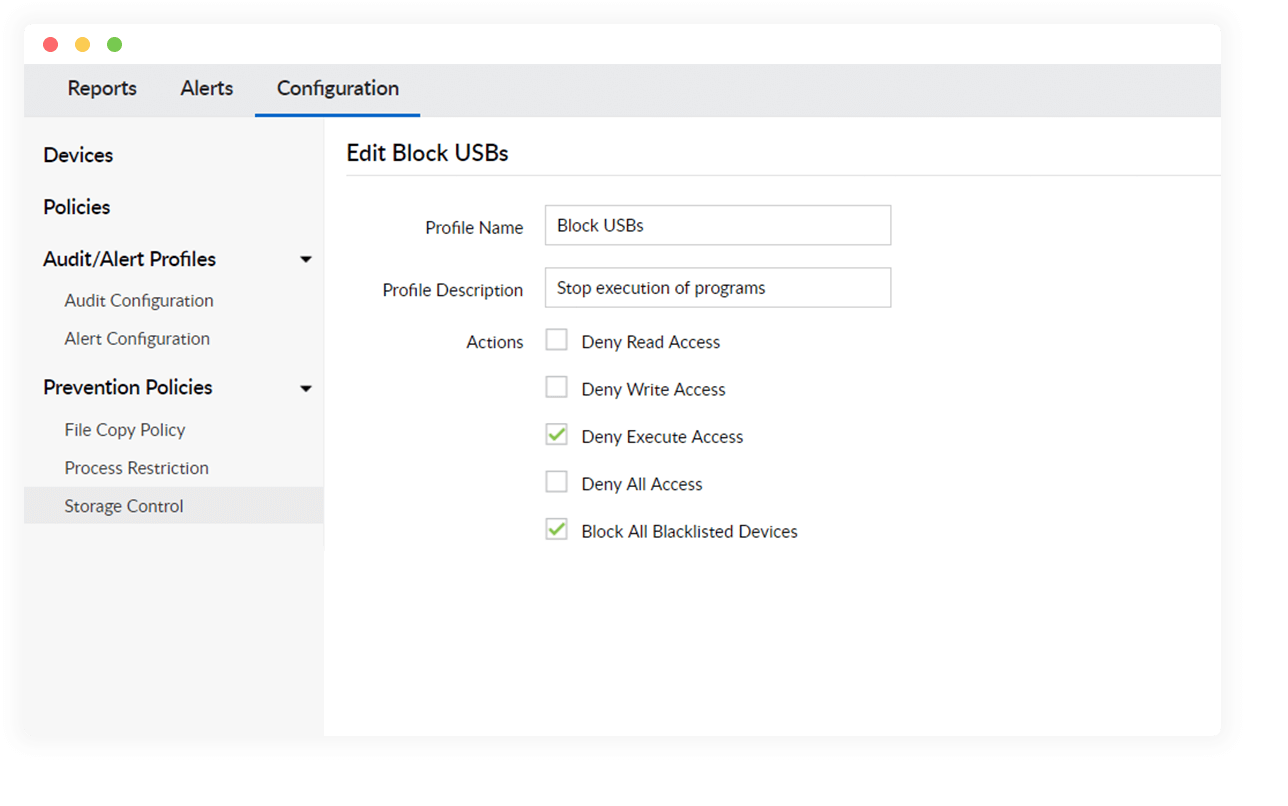
Deny high-risk USB actions
Invalidate removable drives use to stop files in USBs being opened or modified, and to block unknown application executables from being run.
-
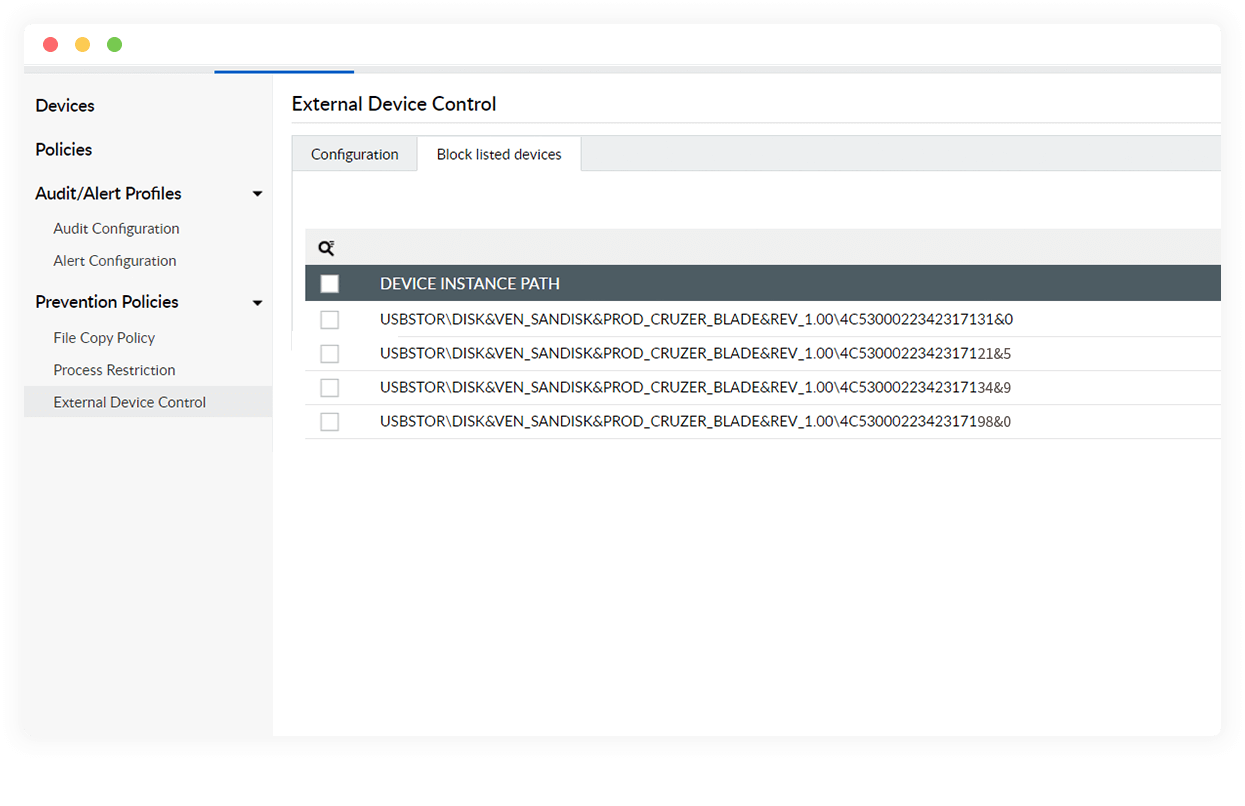
Authorize safe devices only
Enable employees to use only the secure USB drives authorized by you. Effectively block unauthorized devices specified by you in the block-list configuration.
-
Block all peripheral devices
Control which peripheral devices can be used within your organization. Allow or stop bluetooth devices, Wi-Fi routers, and more.
-
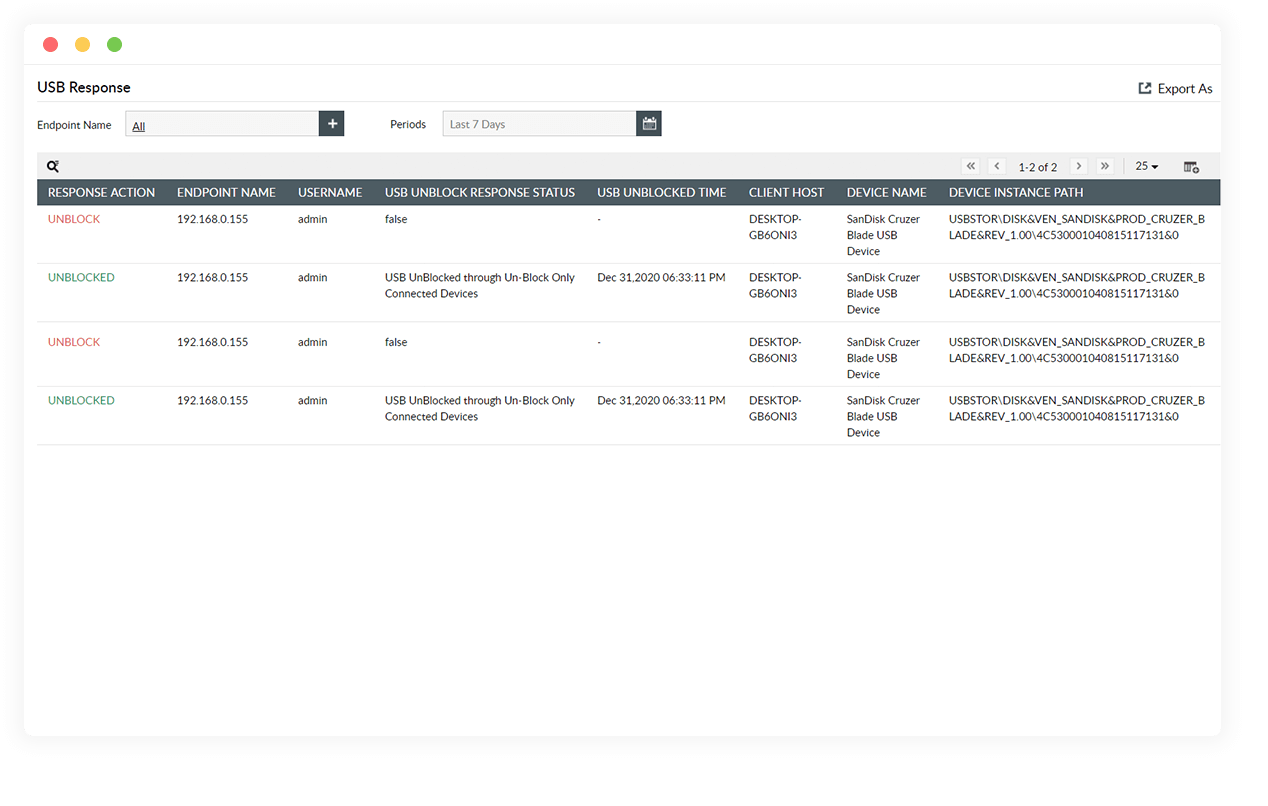
Grant read-only access to users
Control the use of USB drives by granting users only minimum access to reading files on the drives. Block write access to USB drives, preventing data transfers to the drives.
Enforce use of authorized USB drives and ensure safe data exchange with our data leak prevention software.