-
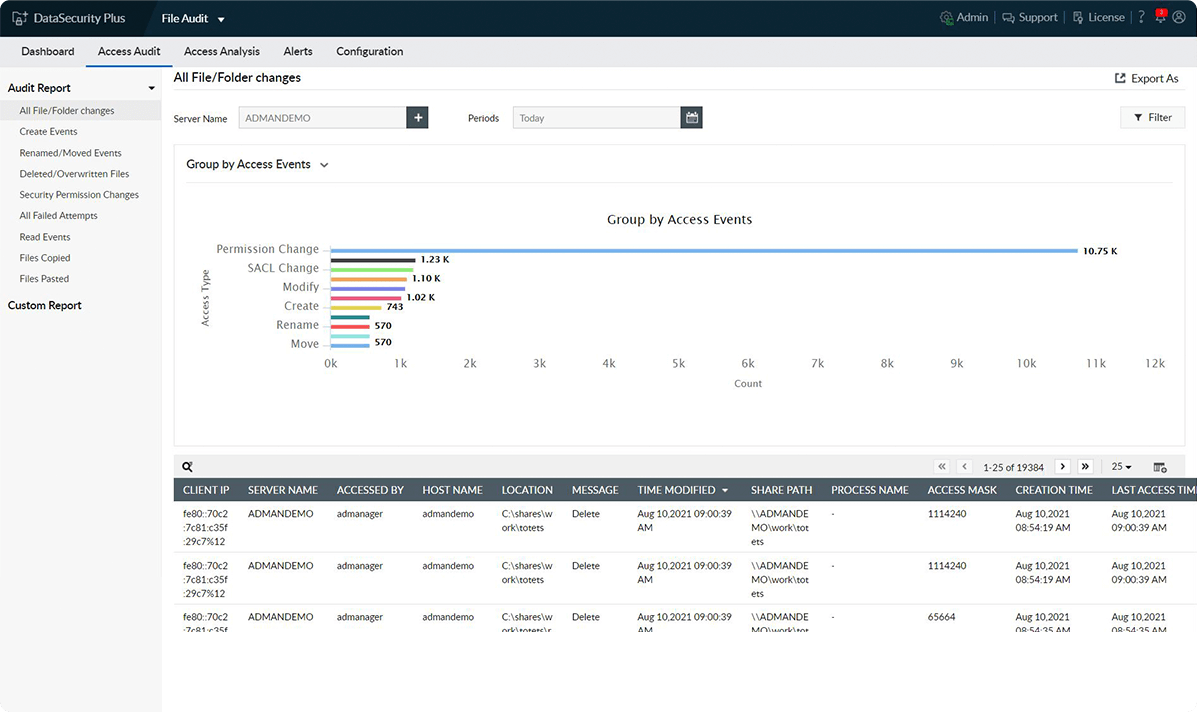
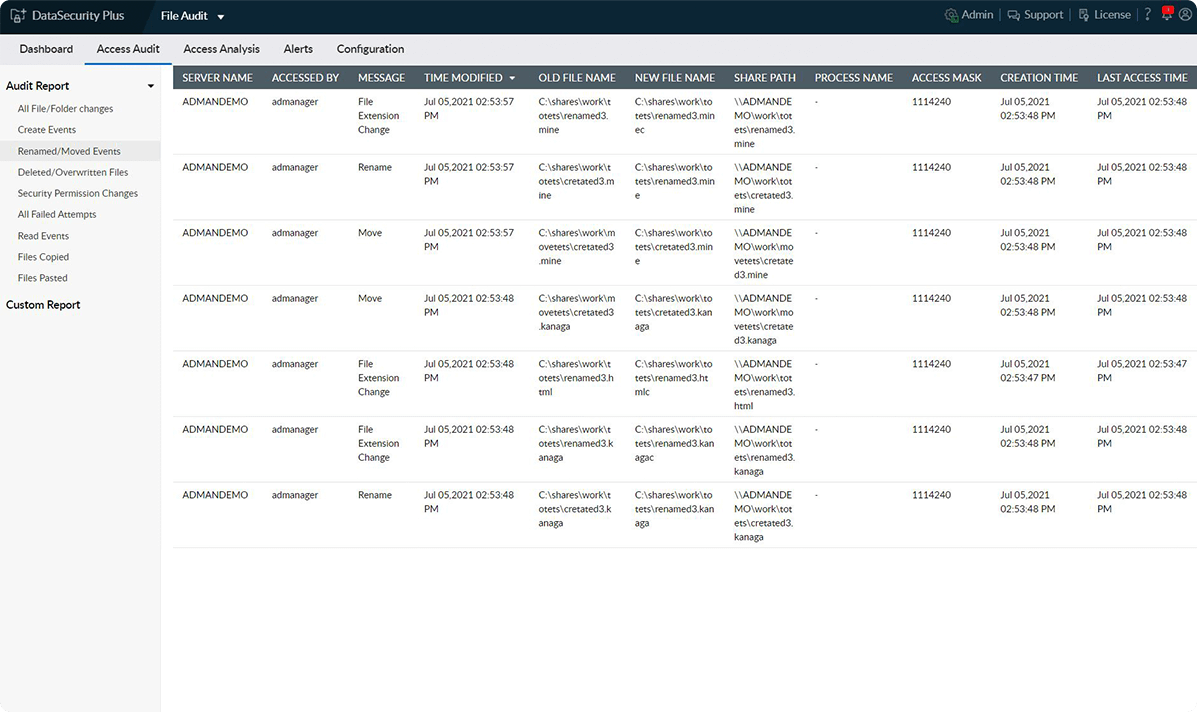
Detect all file change activities
Maintain a daily log on a wide range of failed and successful file modifications, such as creating, renaming, overwriting, moving, deleting, copying, and pasting.
-
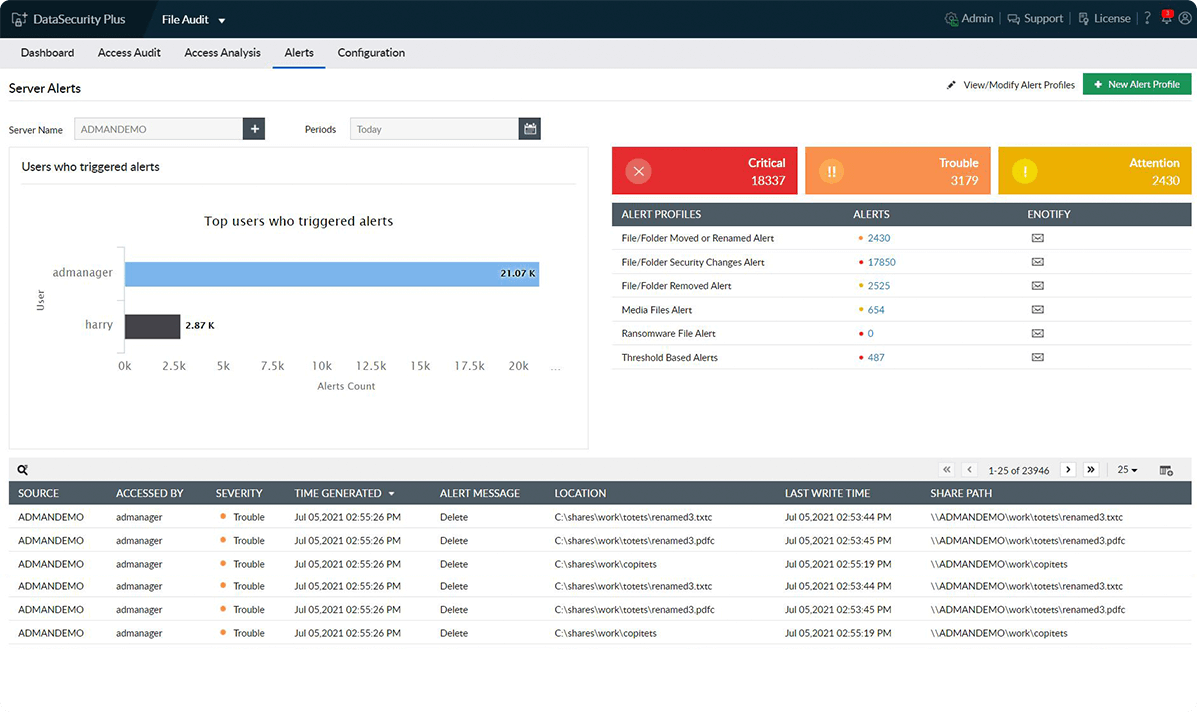
Scrutinize high-risk file changes
Employ instant email alerts to notify admins when a permission, owner, or SACL value for a business-critical file is modified during nonbusiness hours.
-
Track file access patterns
Use graphs to find the most active users, the file activity summary, the most modified files, and more. The offered filters, like the last access time, host details, and file name, help you drill down further.
-
Ensure file integrity monitoring
Ensure easy compliance with regulations, such as the PCI DSS, HIPAA, and the GDPR, that mandate around the clock monitoring of vital files for detecting any unauthorized changes.
Gain pervasive visibility into all file activities with the help of our file server auditing software.