-
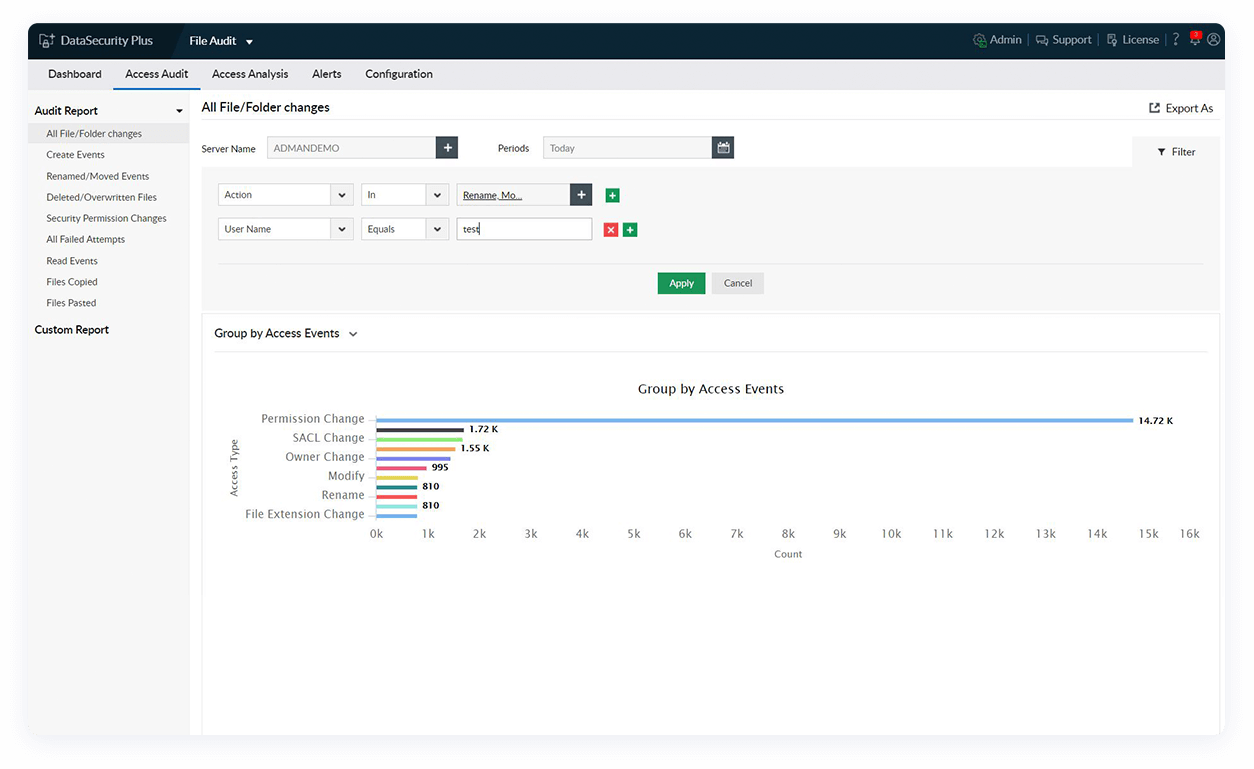
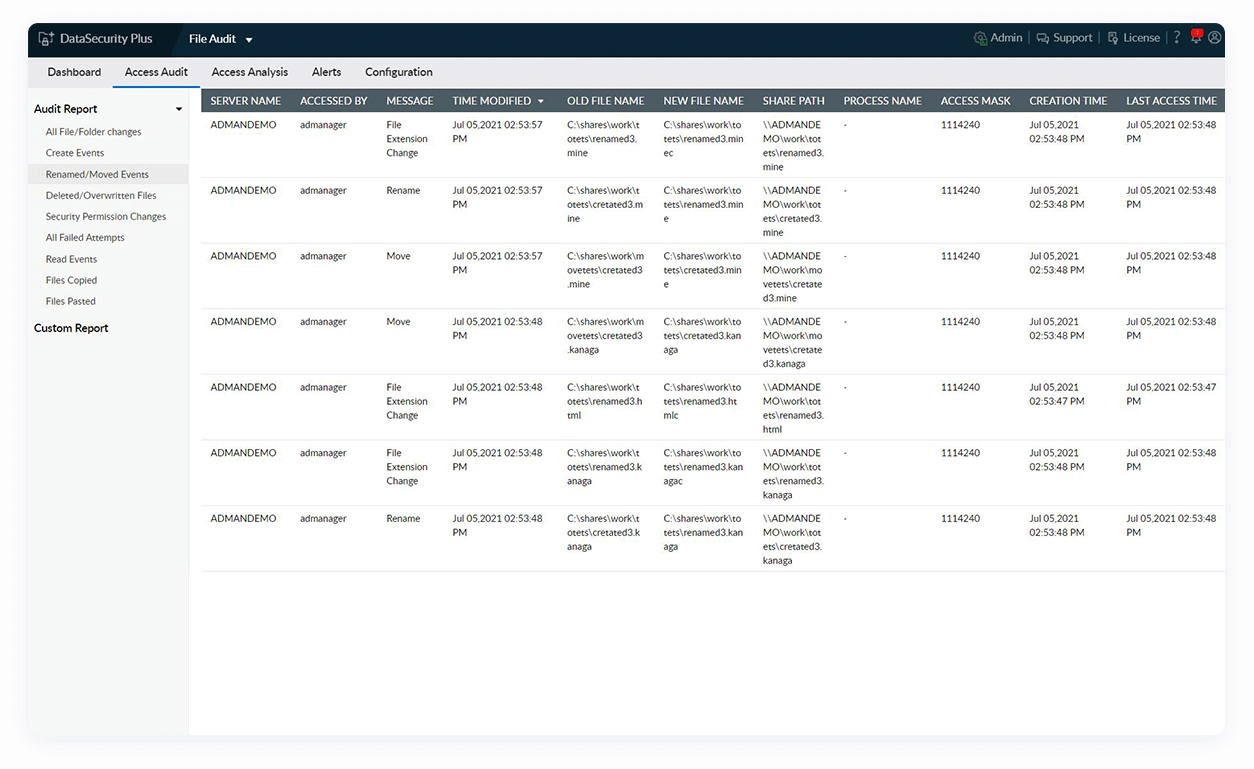
Audit file accesses
Track all file changes, including create, delete, rename, overwrite, move, permission, and SACL changes, with details on who modified which file, when, and from where.
-
Detect ransomware attacks
Minimize the threat to your data stores by quickly spotting indicators of a ransomware attack, shutting down infected devices, and quarantining corrupted devices from the network.
-
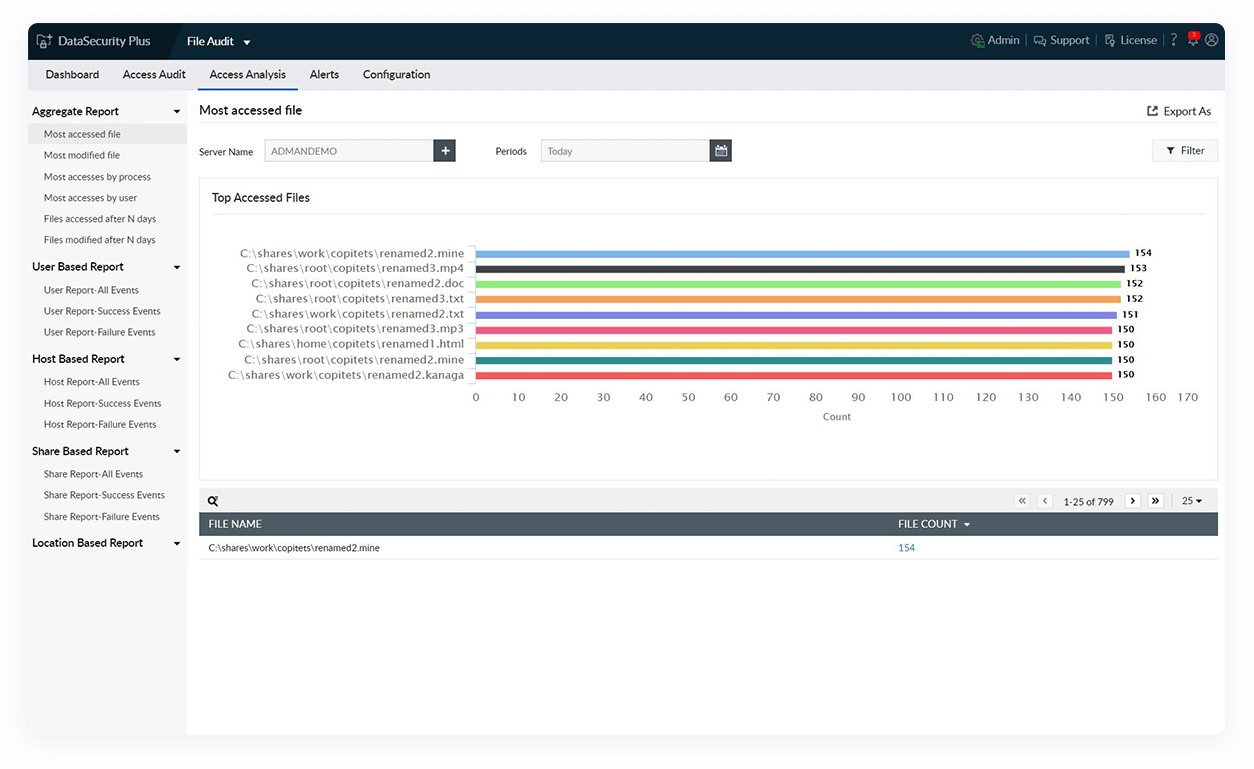
Spot anomalous changes
Monitor file integrity by reviewing sudden spikes in critical file modifications and changes made during non-business hours.
-
Focus on high-risk users
Customize and schedule periodic reports to selectively track the file modifications made by high-privileged users and groups.
Ensure no unwarranted changes are made to your files with our file integrity monitoring software.