-
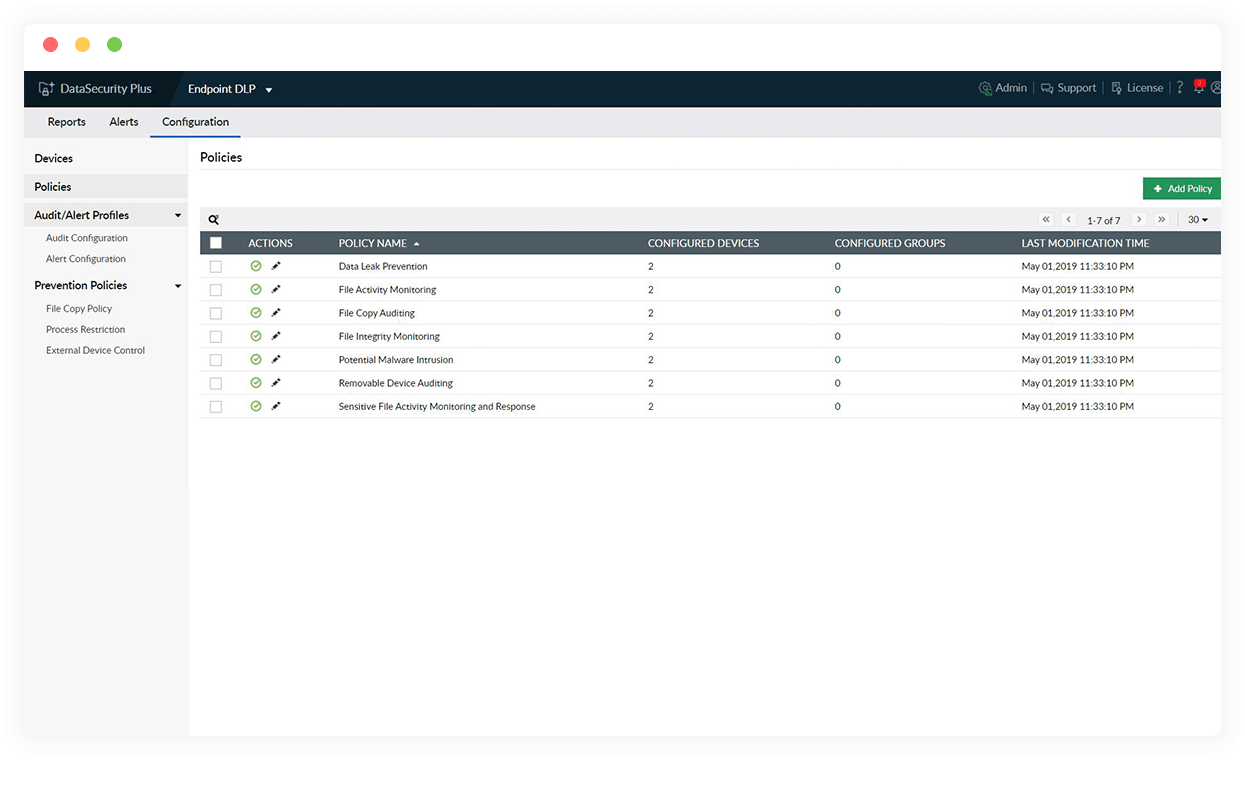
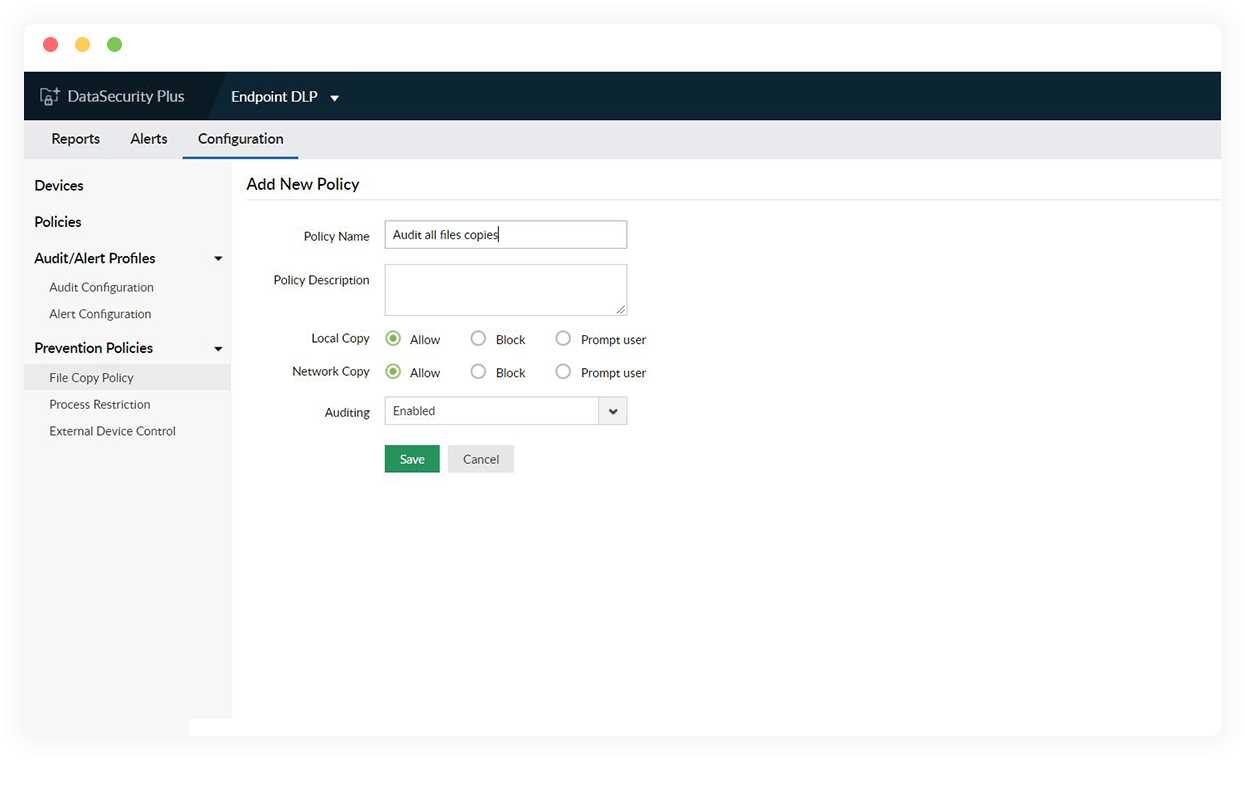
Copy protection software for USBs
Stop the movement of business-critical files to unauthorized locations by restricting both local and network copy functionalities.
-
Stop data leaks via USBs
Block write access to external storage devices and prevent rogue insiders from making unwanted copies of important files to USBs.
-
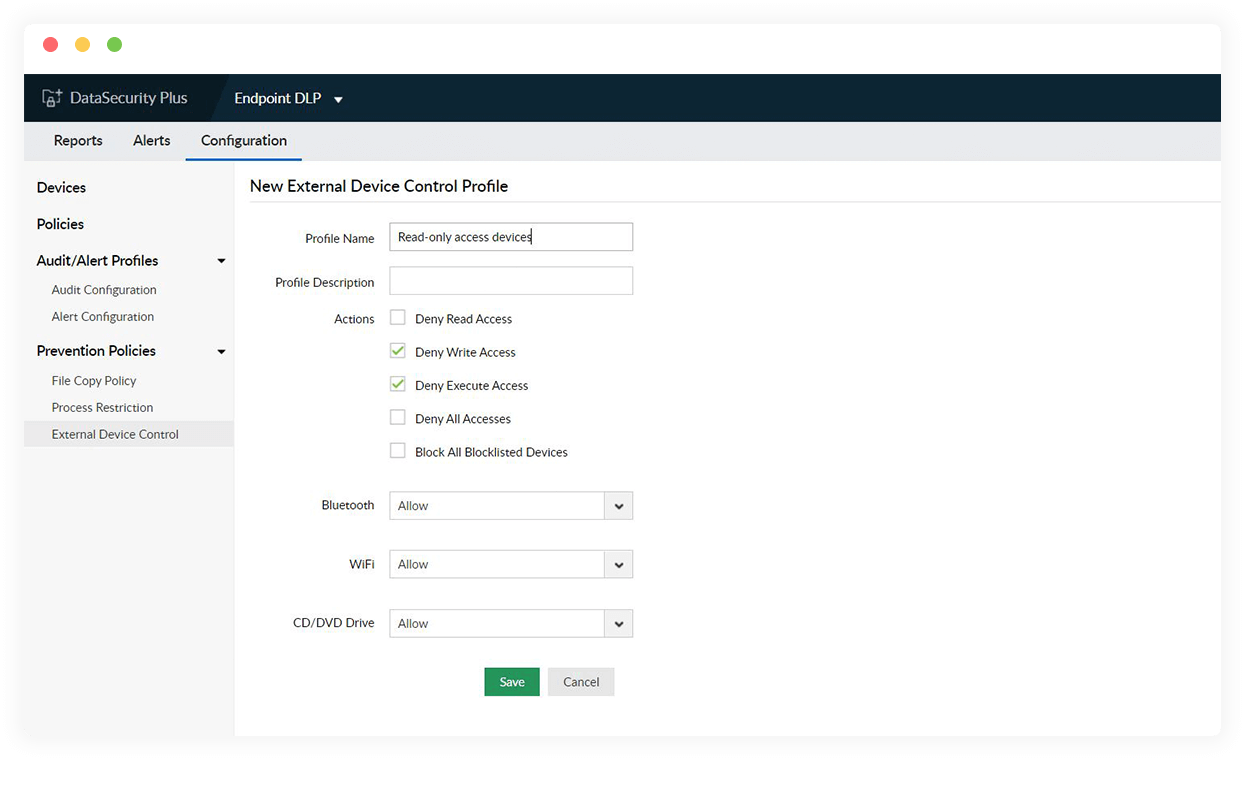
Enforce removable storage control
Limit the use of USBs by denying read rights, execute access, and more. Also, use blocklisting capabilities to restrict the use of high-risk external devices.
-
Automate your threat response
Detect sudden spikes in sensitive files copied to external storage devices and initiate automated responses that block the use of these devices instantly.
Minimize the risk of data loss with our homegrown data leak prevention (DLP) solution.