-
Spot ransomware-corrupted files
Run periodic scans across your entire file system to identify ransomware-infected files lying dormant and reduce the risk to your business-critical data.
-
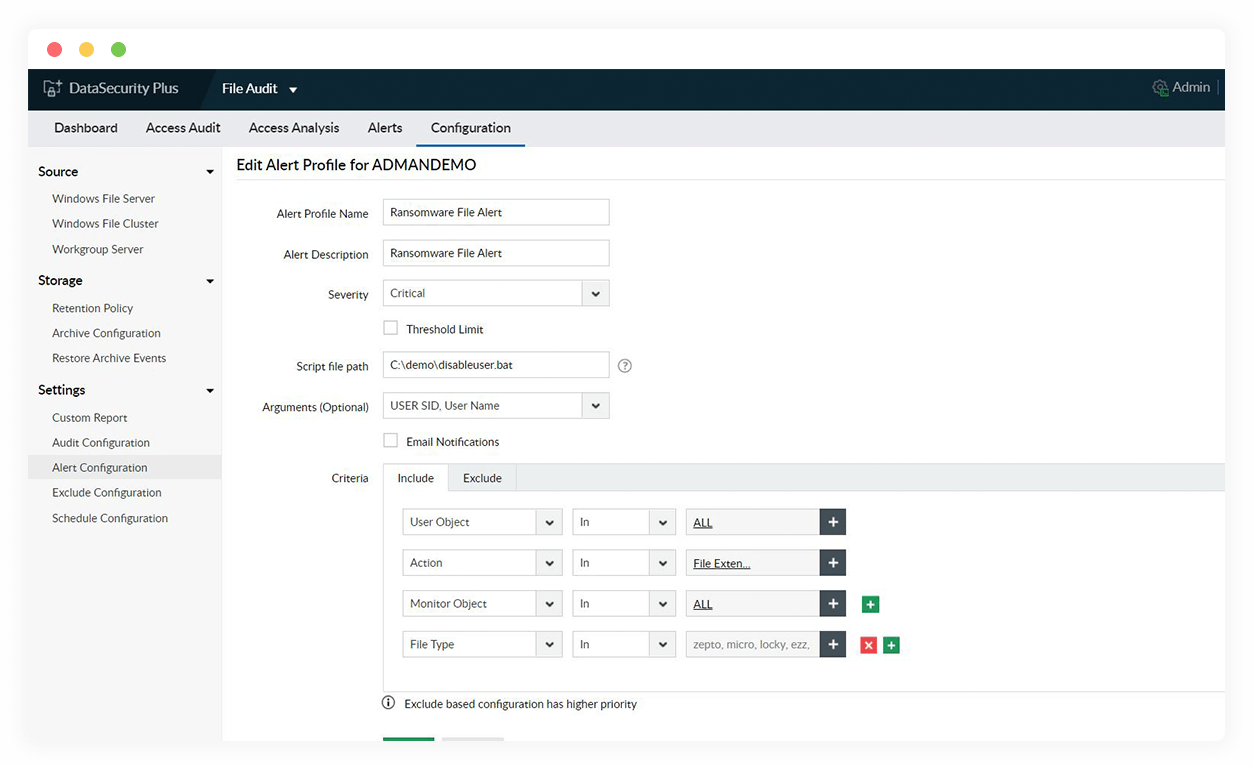
Detect ransomware attacks
Identify ransomware attacks the moment they begin by scrutinizing bulk changes to file extensions, permissions, and ownership in real time.
-
Speed up your security response
Locate and disconnect the ransomware-infected device, revoke the affected user's access to file shares, and minimize the damage using automated threat responses.
-
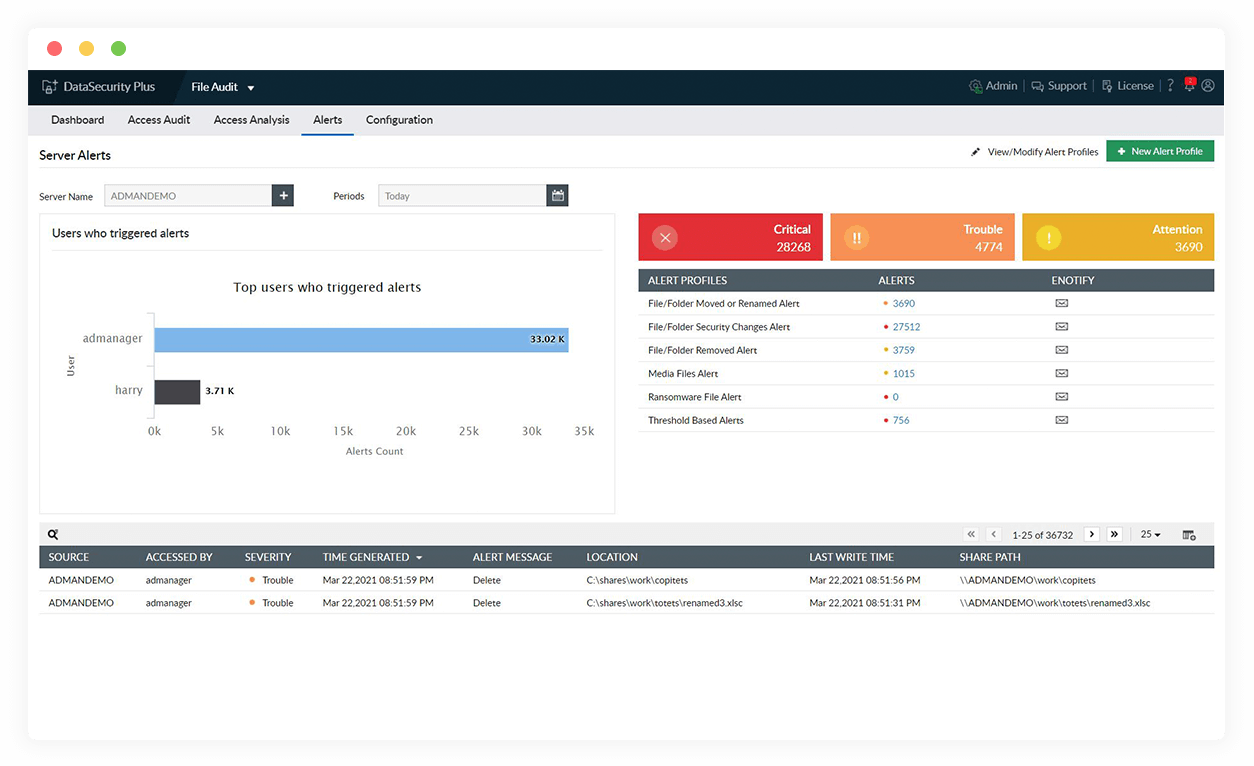
Expedite forensic analysis
Find patient zero of the ransomware attack, i.e. the first infected system, with a deep dive into a detailed audit trail of all file activities.
Mitigate the risk ransomware poses using our ransomware detection software