-
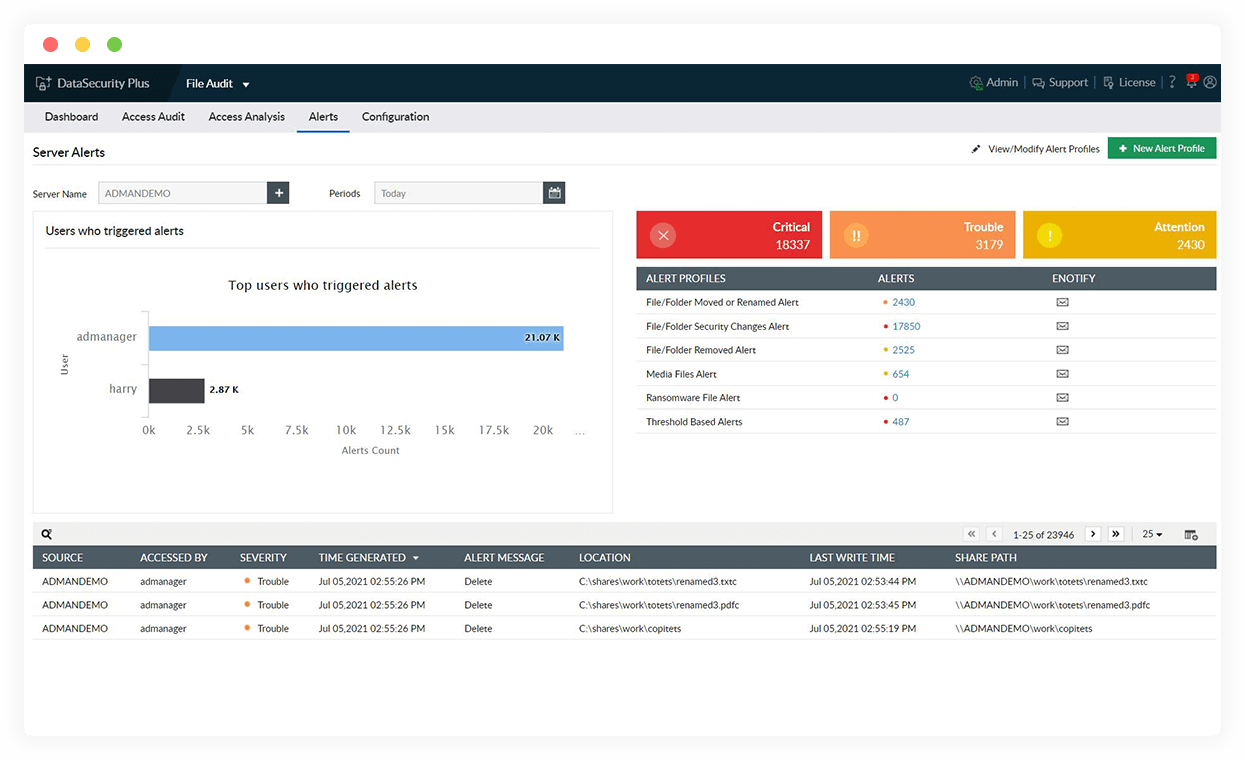
Spot ransomware indicators
Detect sudden, enormous spikes in file rename, deletion, and permission change activities, which are sure signs of possible ransomware infection spreading.
-
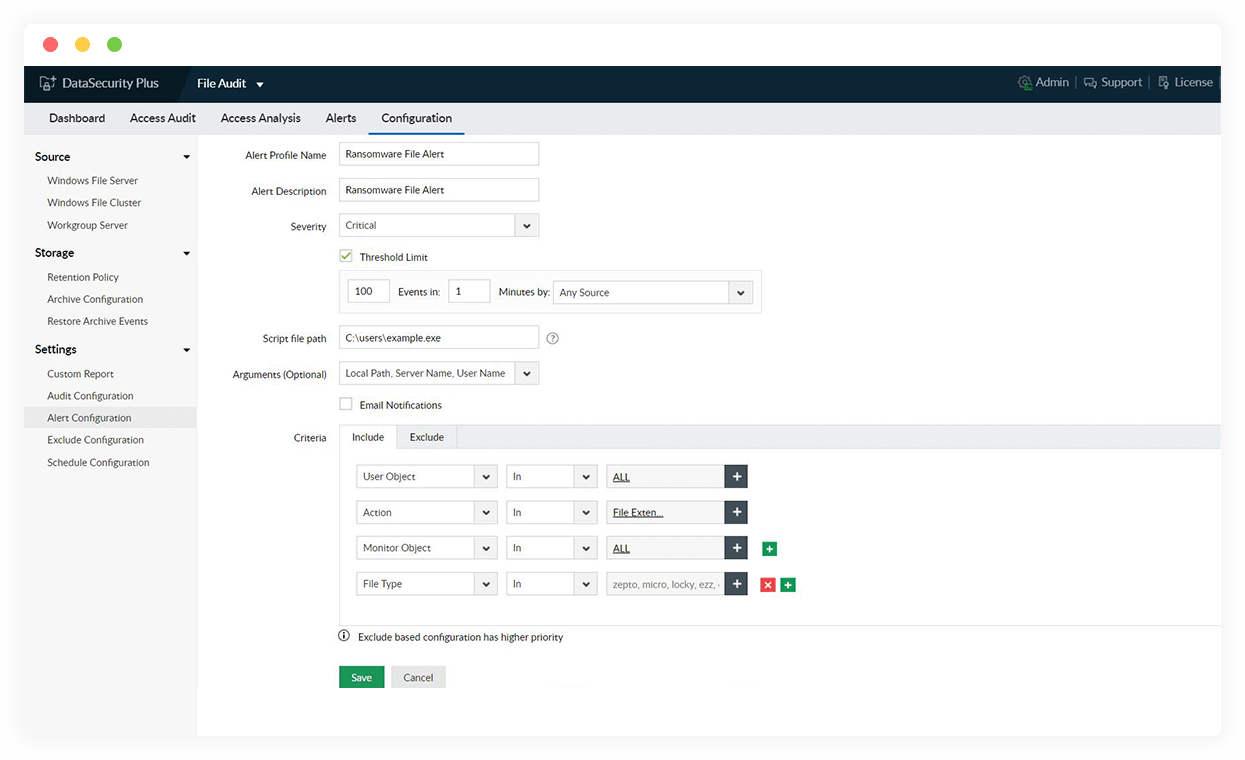
Quarantine ransomware infection
Use automated threat responses to stop ransomware attacks by isolating and shutting down the infected devices or disconnecting the user account taken over by malware.
-
Locate ransomware-infected data
Receive instant notifications on detecting ransomware-corrupted files across your file storage. Use the up-to-date, pre-built library of known ransomware file types to aid in detection.
-
Investigate ransomware attacks
Use our in-depth audit trail on all file and folder activities to quickly identify where the incident originated, when, and how.
Combat ransomware attacks quickly with the help of our file server auditing software.