-
Enable quick incident detection
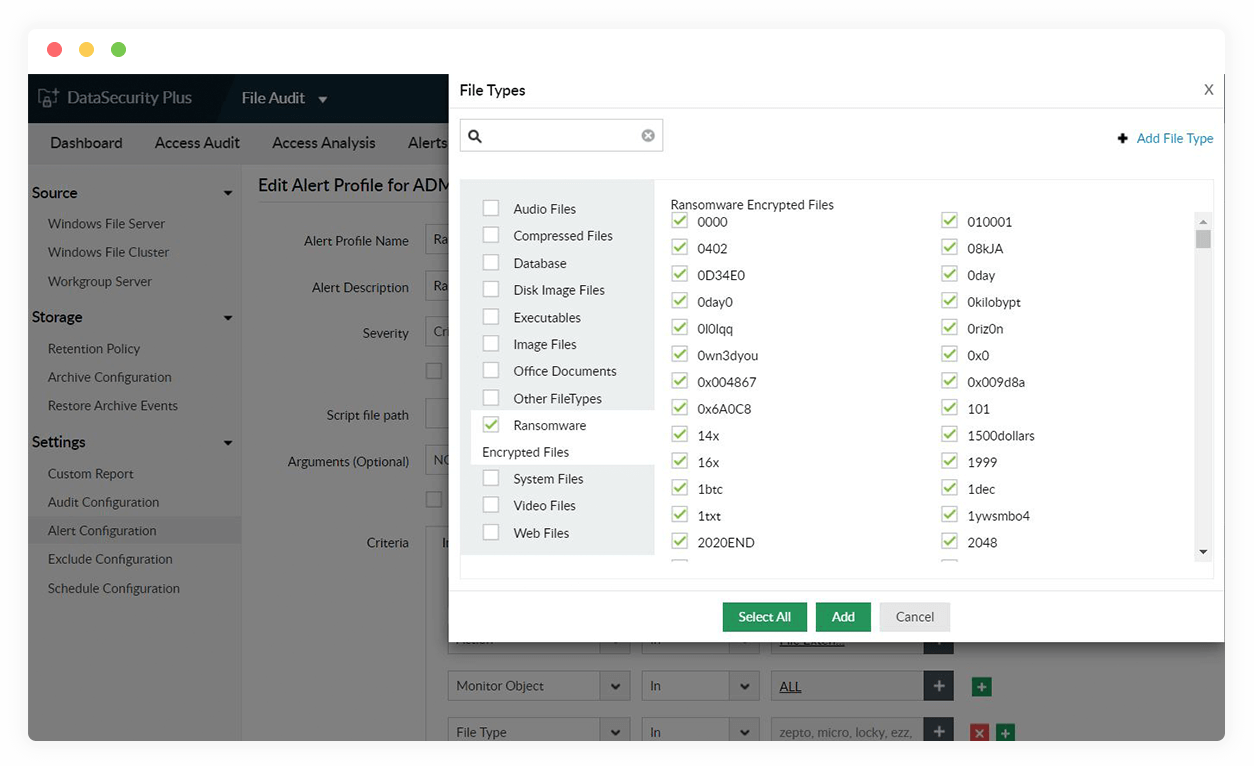
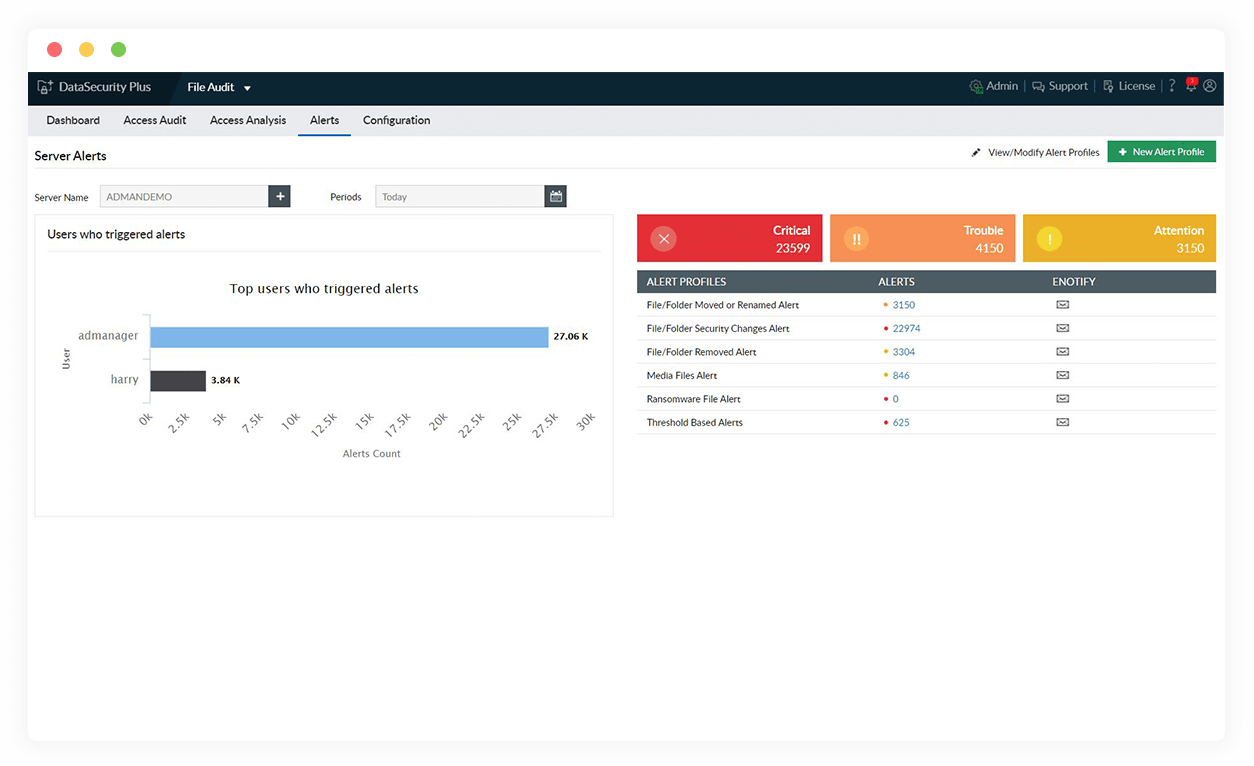
Quickly spot ransomware attacks to facilitate instant responses by tracking sudden, unexplained spikes in file rename and permission change activities.
-
Isolate infected devices
Cut off the ransomware infection instantly upon detection by shutting down the host machine and disconnecting the infected systems from the network.
-
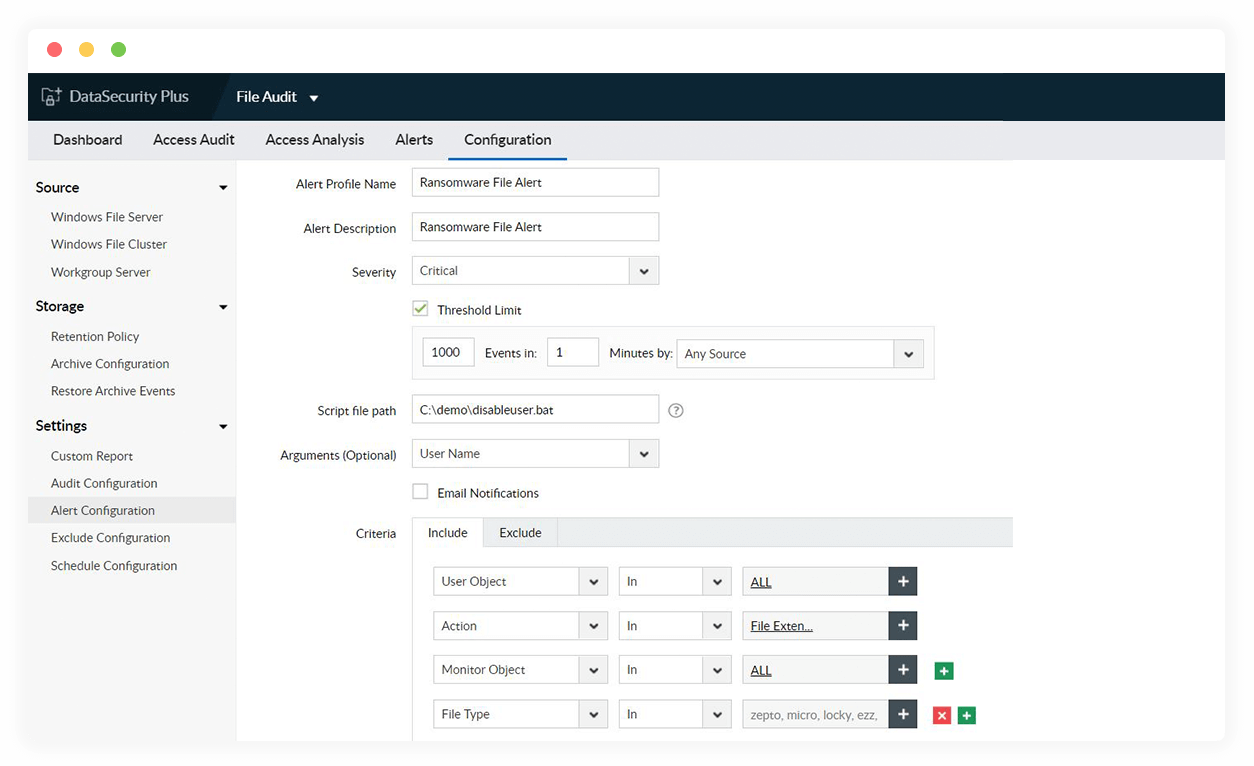
Disable hijacked user accounts
Deactivate user accounts commandeered by ransomware by executing scripts tailored to your organization's requirements.
-
Enforce Zero Trust system
Analyze and identify folders and shares with excessive privileges and ensure only bare minimum rights are provided to lower your risk of ransomware quickly spreading.
Secure your organization's business-critical data from loss, theft, and exposure using our DLP software