-
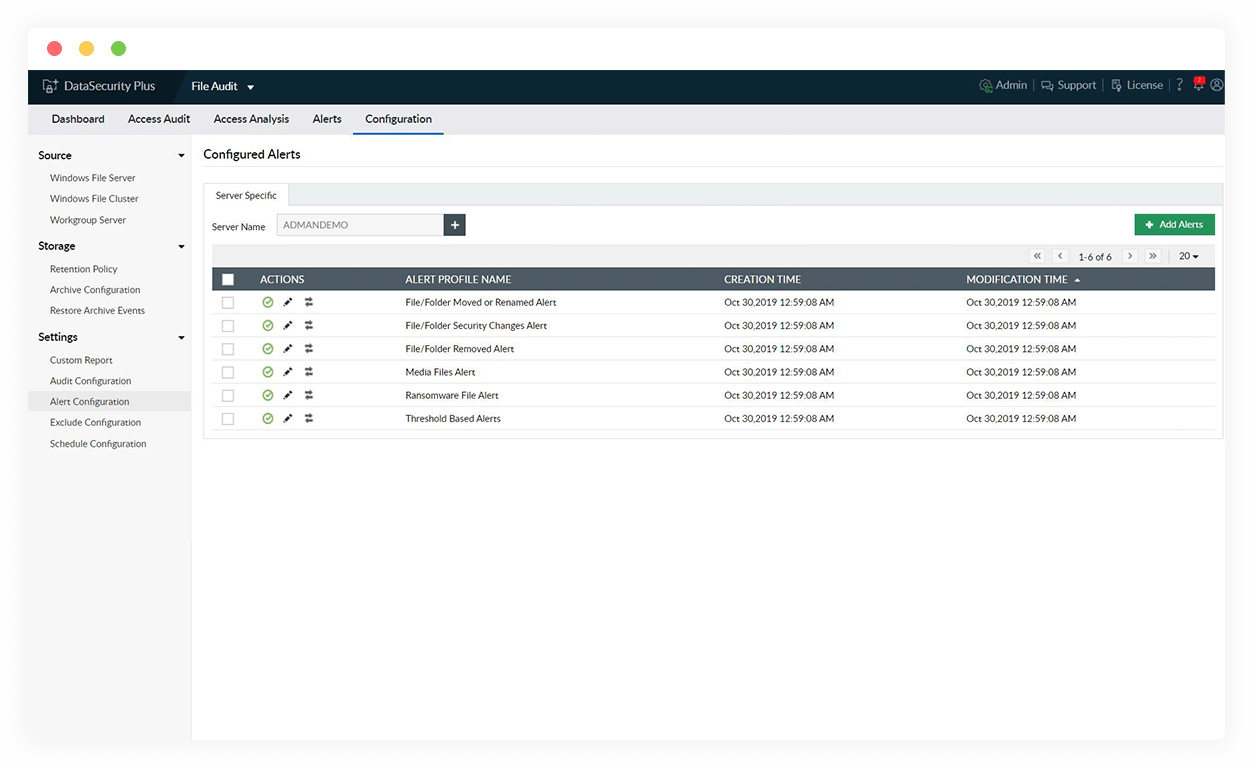
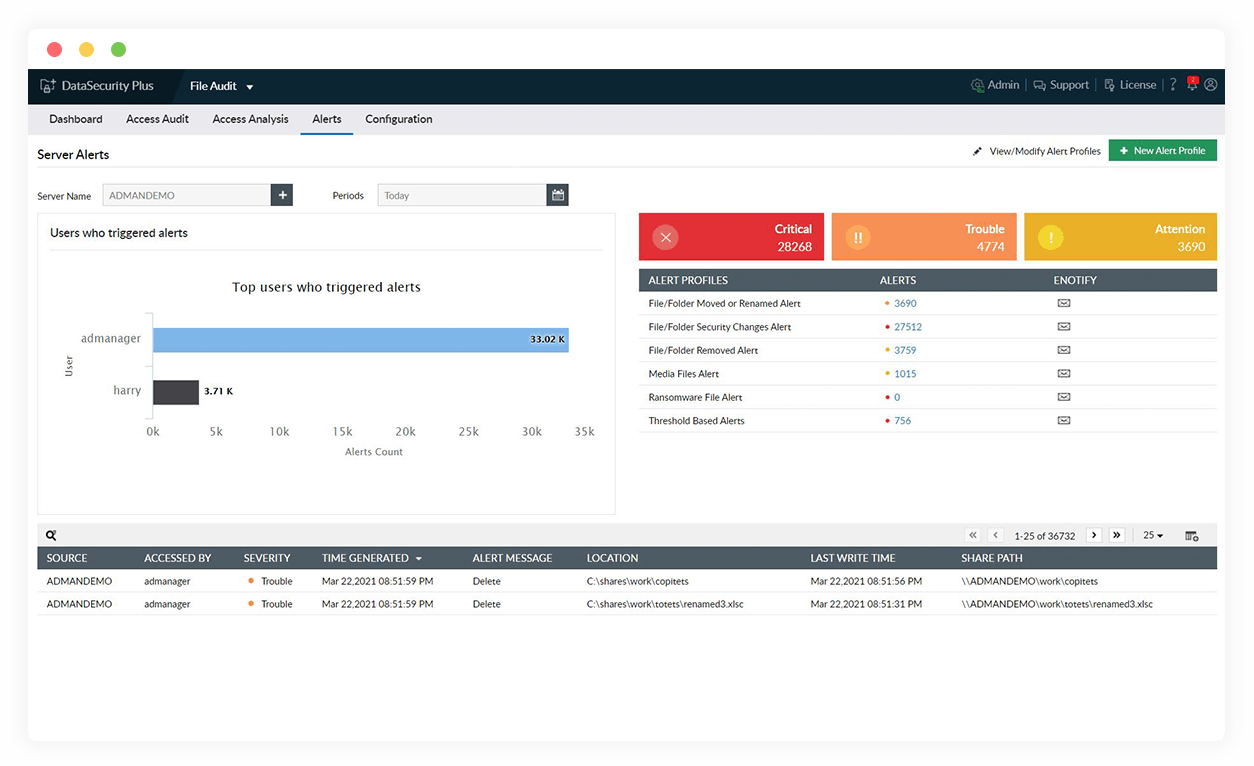
Detect ransomware attacks instantly
Accurately spot the excessive file modifications that usually accompany a ransomware attack, and quickly notify admins and other stakeholders.
-
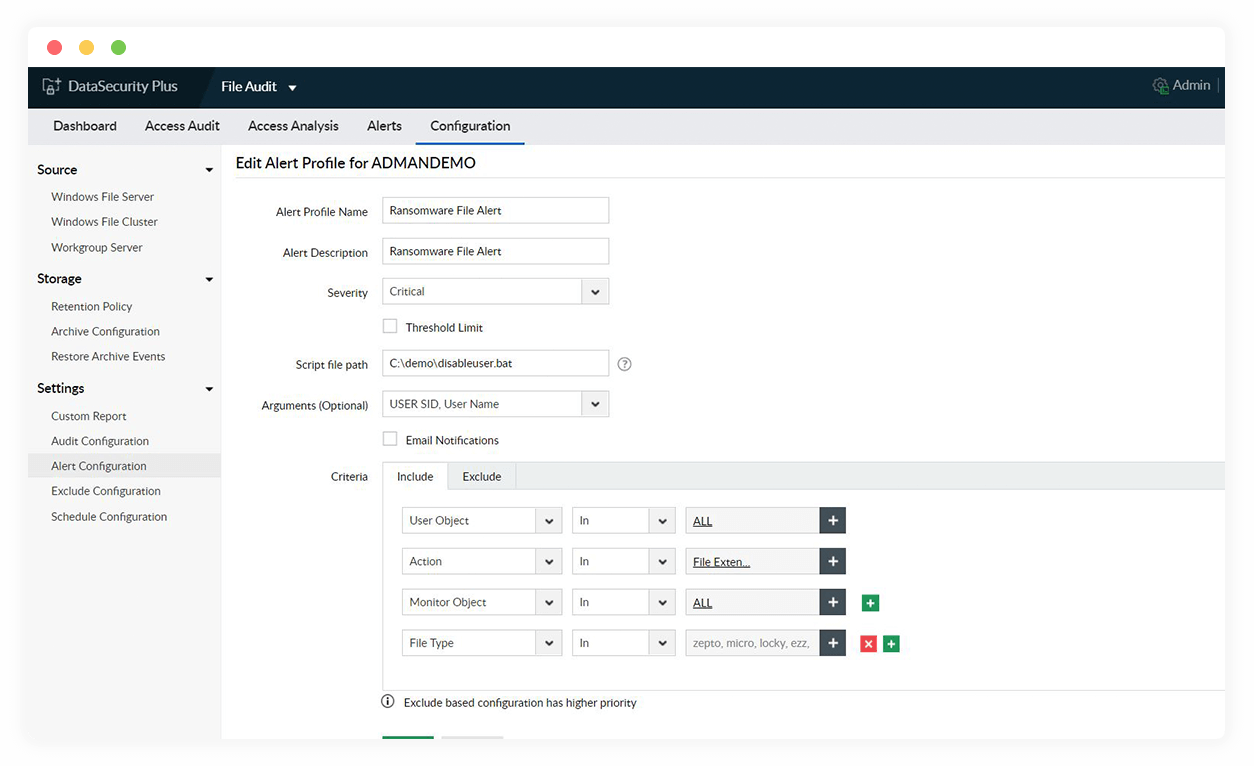
Automate your ransomware response
Execute custom scripts to shut down the infected system, disconnect corrupted devices from the network, and quarantine ransomware-infected machines using a myriad of available options.
-
Reduce the risk of a ransomware attack
Lower the risk of a ransomware attack by locating overexposed files, preventing suspicious applications from running, blocking the use of malicious web applications, and more.
-
Find ransomware-corrupted files
Track all files infected with known ransomware variants such as Petya, Wannacry, Locky, and more using our pre-built, up-to-date library.
Detect and prevent sensitive data leaks via USB devices, email, and more using our data leak prevention tool