-
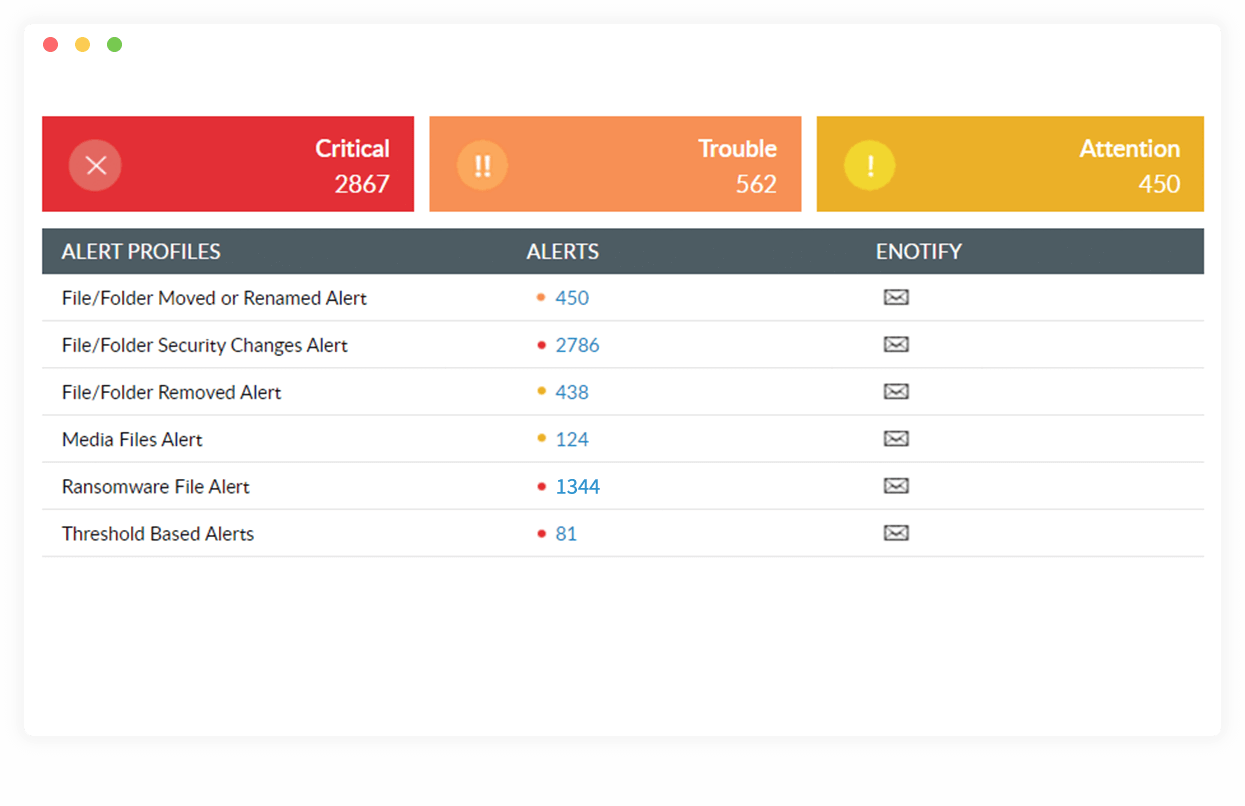
Spot ransomware attacks
Get immediately notified of sudden spikes in suspicious file events indicative of ransomware intrusion. Always be on the alert for signs of ransomware with real-time reports and email notifications generated right when an attack is triggered.
-
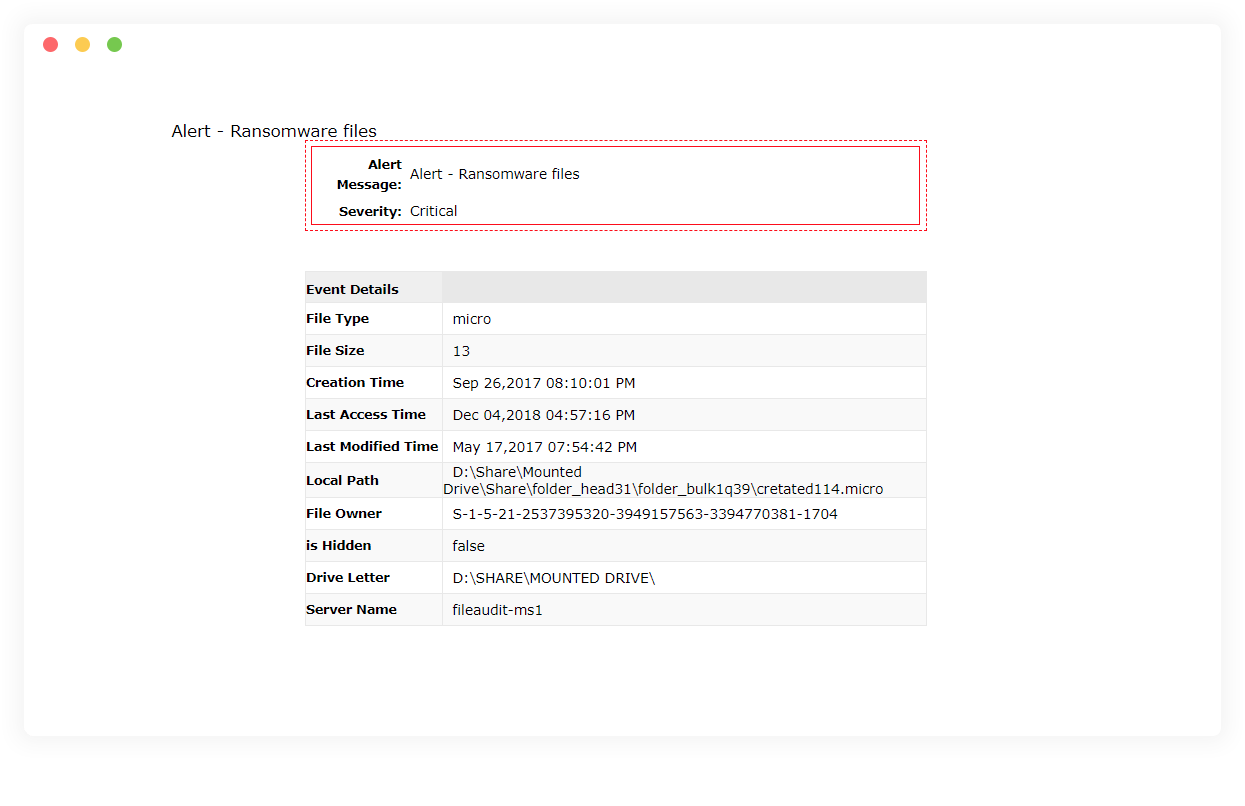
Locate ransomware-infected files
Find all instances of files corrupted with known ransomware variants like Petya, WannaCry, or Locky. Monitor data stores using our library of over 50 ransomware variants for prompt identification.
-
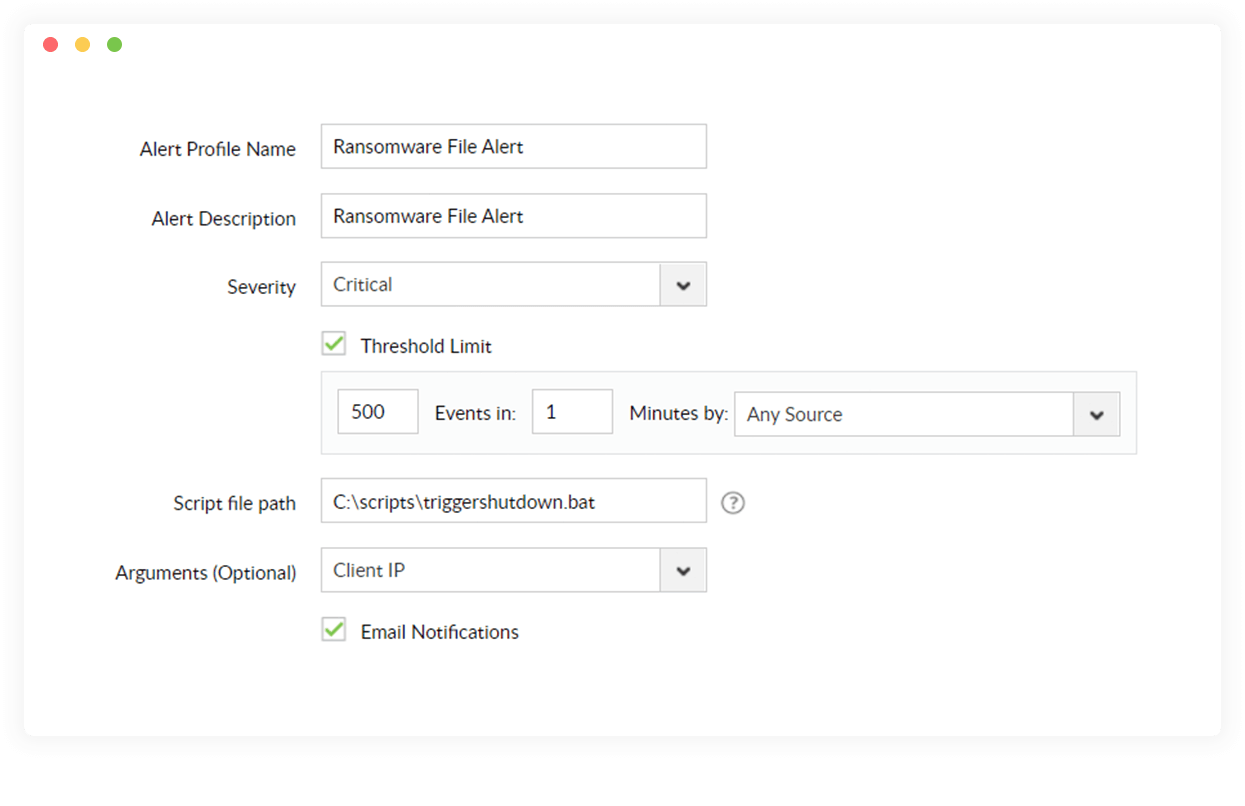
Define systematic alert-responses
Set up alerts with high severity to spot ransomware indicators instantaneously and be notified straight away. Further, use customizable scripts to automate threat response.
-
Contain ransomware spread
Define mitigation efforts to be implemented immediately after an attack has been identified in your network. Confine ransomware at the source by cutting off compromised endpoints.
Stop a ransomware attack from snowballing into a full-fledged invasion with our ransomware detection software.